2017-03-29 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-29-Hancitor-infection-with-ZLoader.pcap.zip 14.0 MB (14,008,392 bytes)
- 2017-03-29-Hancitor-malspam-15-examples.zip 21.4 kB (21,416 bytes)
- 2017-03-29-malware-from-Hancitor-infection.zip 299.6 kB (299,574 bytes)
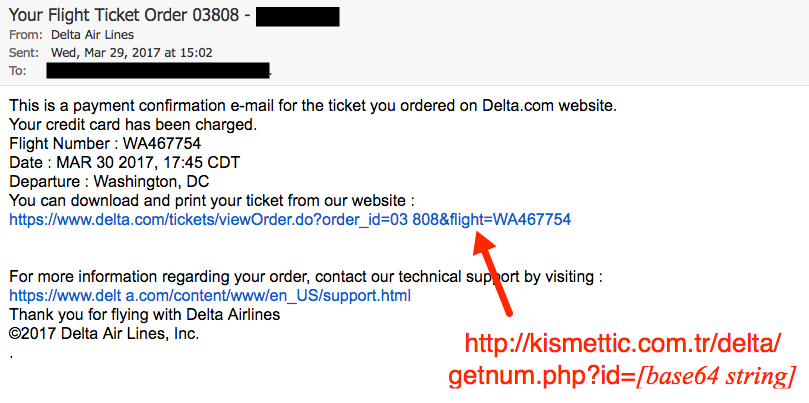
Shown above: Screen shot of the email.
EMAIL HEADERS:
- Date: Monday 2017-03-27
- From: (spoofed) "Amazon[.]com" <ship-confirm@amazon-delivery[.]com>
- Subject: Your Amazon[.]com order has shipped (#123-12345678-1234567890)
- Date: Tuesday 2017-03-28
- From: (spoofed) "ADP Billing" <adp@adp-usa[.]com>
- Subject: Your invoice 123456 is available for review!
- Date: Wednesday 2017-03-29
- From: (spoofed) "Delta Air Lines" <order@delta-tickets[.]com>
- Subject: Your Flight Ticket Order 12345 - [recipient]

Shown above: Malicious Word document (Hancitor) from link in the malspam.
TRAFFIC
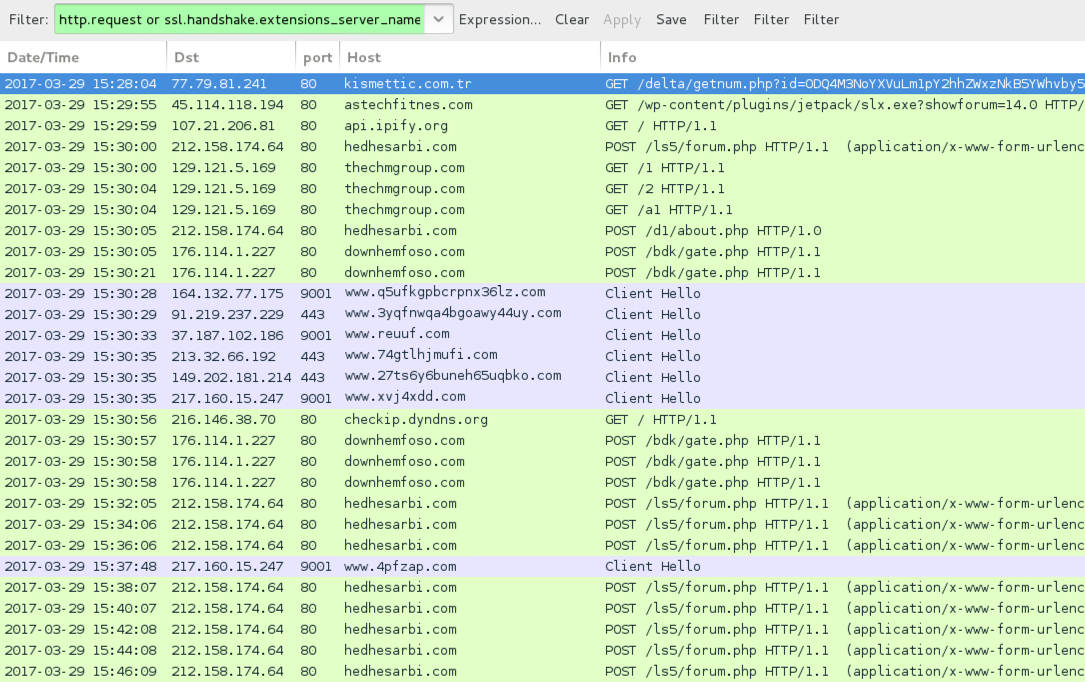
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE INITIAL DOCUMENT:
- 2017-03-28 - www.oceanprosperity[.]com[.]hk - GET /stat/getnum.php?id=[base64 string]
- 2017-03-27 - www.bluedot[.]co[.]za - GET /l5afva/getnum.php?id=[base64 string]
- Today - 77.79.81[.]241 port 80 - kismettic[.]com[.]tr - GET /delta/getnum.php?id=[base64 string]
- Today - 52.77.44[.]7 port 80 - ieducate[.]sg - GET /delta/getnum.php?id=[base64 string]
POST-INFECTION TRAFFIC:
- 45.114.118[.]194 port 80 - astechfitnes[.]com - GET /wp-content/plugins/jetpack/slx.exe?showforum=14.0
- 212.158.174[.]64 port 80 - hedhesarbi[.]com - POST /ls5/forum.php
- 212.158.174[.]64 port 80 - hedhesarbi[.]com - POST /d1/about.php
- 129.121.5[.]169 port 80 - thechmgroup[.]com - GET /1
- 129.121.5[.]169 port 80 - thechmgroup[.]com - GET /2
- 129.121.5[.]169 port 80 - thechmgroup[.]com - GET /a1
- 176.114.1[.]227 port 80 - downhemfoso[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses, various ports - Tor traffic
SOME ARTIFACTS ON THE INFECTED WINDOWS HOST:
- C:\Users\[username]\AppData\Local\Temp\42239.exe (100 kB)
- C:\Users\[username]\AppData\Local\Temp\BN53F9.tmp (180 kB)
- C:\Users\[username]\AppData\Local\Temp\beqyve.crt (2 kB)
- C:\Users\[username]\AppData\Roaming\Dueh\ymax.ute (0 kB)
- C:\Users\[username]\AppData\Roaming\Dueh\zmax.ute (0 kB)
- C:\Users\[username]\AppData\Roaming\Nyyml\ruyt.oze (21,603 kB)
- C:\Users\[username]\AppData\Roaming\tor\cached-certs (19 kB)
- C:\Users\[username]\AppData\Roaming\tor\cached-microdescs-consensus (2,194 kB)
- C:\Users\[username]\AppData\Roaming\tor\cached-microdescs.new (3,673 kB)
- C:\Users\[username]\AppData\Roaming\tor\lock (0 kB)
- C:\Users\[username]\AppData\Roaming\tor\state (2 kB)
- C:\Users\[username]\AppData\Roaming\Xeukys\epposi.php (4 kB)
- C:\Users\[username]\AppData\Roaming\Xeukys\php.exe (29 kB)
- C:\Users\[username]\AppData\Roaming\Xeukys\php5ts.dll (5,589 kB)
- C:\Users\[username]\AppData\Roaming\Zyku\acho.myu (180 kB)
- C:\Users\[username]\AppData\Roaming\libeay32.dll (1,944 kB)
- C:\Users\[username]\AppData\Roaming\libevent-2-0-5.dll (703 kB)
- C:\Users\[username]\AppData\Roaming\libgcc_s_sjlj-1.dll (511 kB)
- C:\Users\[username]\AppData\Roaming\libssp-0.dll (91 kB)
- C:\Users\[username]\AppData\Roaming\ssleay32.dll (391 kB)
- C:\Users\[username]\AppData\Roaming\tor.exe (2,898 kB)
- C:\Users\[username]\AppData\Roaming\zlib1.dll (105 kB)
FILE HASHES
FROM LINK IN THE EMAIL:
- SHA256 hash: 9041418337322cbdf1f6105d4ade74110b25675f00c72b0728f66faa56a73f05
File location: Ticket_shaun.michaels6.doc
File description: Hancitor maldoc
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: 63733fe624b6e2ca7941a30e33f2e664a973d91c5a28abe6204aab4a0062d917
File location: C:\Users[username]\AppData\Local\Temp\42239.exe
File description: Hancitor EXE
- SHA256 hash: 7e059267c64b5740672872c4f860f685a9eafbc605319dbb65b45eea7359d338
File location: C:\Users[username]\AppData\Local\Temp\BN53F9.tmp
File description: ZLoader (DELoader) EXE
Click here to return to the main page.
