2017-03-31 - "BLANK SLATE" CAMPAIGN STILL PUSHING CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-31-Blank-Slate-activity-14-pcaps.zip 4.5 MB (4,532,118 bytes)
- 2017-03-31-Blank-Slate-malspam-tracker.csv.zip 2.9 kB (2,896 bytes)
- 2017-03-31-Blank-Slate-emails-and-Cerber-ransomware.zip 3.6 MB (3,605,659 bytes)
BACKGROUND:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
EMAILS
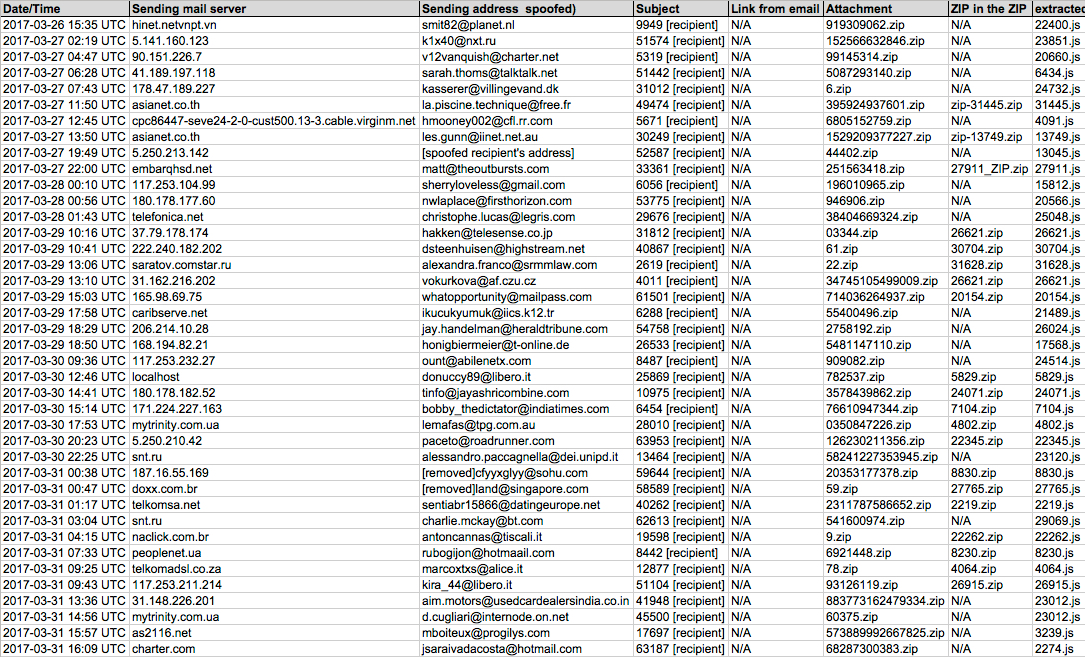
Shown above: Screen shot from the spreadsheet tracker. Review that document for more details.
TRAFFIC
HTTP TRAFFIC FOR THE RANSOMWARE:
- 35.166.163[.]174 port 80 - truemityunituistep[.]top - GET /search.php
- 35.166.163[.]174 port 80 - truemityunituistep[.]top - GET /__files__/1
- 47.90.205[.]113 port 80 - www.chromefastl[.]top - GET /user.php?f=2.gif
- 47.90.205[.]113 port 80 - www.chromehakc[.]top - GET /user.php?f=2.gif
- 47.90.205[.]113 port 80 - www.fffgooaldq[.]top - GET /user.php?f=2.gif
- 47.90.205[.]113 port 80 - www.ffjoleedas[.]top - GET /user.php?f=2.gif
- 47.90.205[.]113 port 80 - www.hoopcinezc[.]top - GET /user.php?f=2.gif
- 47.90.205[.]113 port 80 - www.newsectorbs[.]top - GET /user.php?f=2.gif
- 54.149.101[.]37 port 80 - jhdgh[.]trade - GET /search.php
- 54.149.101[.]37 port 80 - jhdgh[.]site - GET /search.php
- 54.149.101[.]37 port 80 - polkiuj[.]bid - GET /search.php
HTTP TRAFFIC FOR RANSOMWARE DOWNLOAD FROM FAKE CHROME INSTALL PAGE:
- 47.90.205[.]113 port 80 - www.chromefastl[.]top - GET /site/chrome_update.html
- 47.90.205[.]113 port 80 - www.chromefastl[.]top - GET /site/download.php
- 47.90.205[.]113 port 80 - www.chromehakc[.]top - GET /site/chrome_update.html
- 47.90.205[.]113 port 80 - www.chromehakc[.]top - GET /site/download.php
- 47.90.205[.]113 port 80 - www.fffgooaldq[.]top - GET /site/chrome_update.html
- 47.90.205[.]113 port 80 - www.fffgooaldq[.]top - GET /site/download.php
- 47.90.205[.]113 port 80 - www.ffjoleedas[.]top - GET /site/chrome_update.html
- 47.90.205[.]113 port 80 - www.ffjoleedas[.]top - GET /site/download.php
- 47.90.205[.]113 port 80 - www.newsectorbs[.]top - GET /site/chrome_update.html
- 47.90.205[.]113 port 80 - www.newsectorbs[.]top - GET /site/download.php
MALWARE
SHA256 HASHES FOR RANSOMWARE SAMPLES:
- 66fc3e7027cabc29c6ef9bcd40eb92e36530175a89c33dfb4a210ef868af13e0 - Cerber ransomware from chromefastl[.]top on 2017-03-27
- 66fc3e7027cabc29c6ef9bcd40eb92e36530175a89c33dfb4a210ef868af13e0 - Cerber ransomware from chromehakc[.]top on 2017-03-27
- 59118ff55d6c20a08c6d4422972f9741de8b77755695cef9bc95126d46fb0026 - Cerber ransomware from hoopcinezc[.]top on 2017-03-27
- d4dbc24e07aca11e53f1bb733852e4416a8fc7db1c0c947994ec271895fdb0a4 - Cerber ransomware from truemityunituistep[.]top on 2017-03-27
- 8ea494bd84bea2617922a9ed488db44937199b3764ab6cb9f64e49d7e6945a3b - Cerber ransomware from truemityunituistep[.]top on 2017-03-28
- 07be83b0e9ed748c11d16afbd42b5582f192539706f3996a6debebdb575ad259 - Cerber ransomware from newsectorbs[.]top on 2017-03-29
- b0e6d0e366494f94fd05756ec4b6245c74eee8f1c0ea65b21ba5e5f1c79d69c8 - Cerber ransomware from polkiuj[.]bid on 2017-03-29
- 2e3652afd5d79020dd5aa1d95a61fa6c8e67271f16ccb15aacf11accdd9cc790 - Cerber ransomware from fffgooaldq[.]top on 2017-03-31
- 434d95079877a99fc7cf9c01faabe37c185656bd5ffebe627a756641e41e1f5b - Cerber ransomware from ffjoleedas[.]top on 2017-03-31
- 5bcb16e6dd8a023f7daef3cf2193ec4d8b911e3af677be3ebfbe58dbaf6e6d41 - Cerber ransomware from jhdgh[.]site on 2017-03-31
- 0a7786e86d3df2548e12176b5d8aa6db0de9e556450a90f7c36fdbab1392b48f - Cerber ransomware from jhdgh[.]trade on 2017-03-31
IMAGES
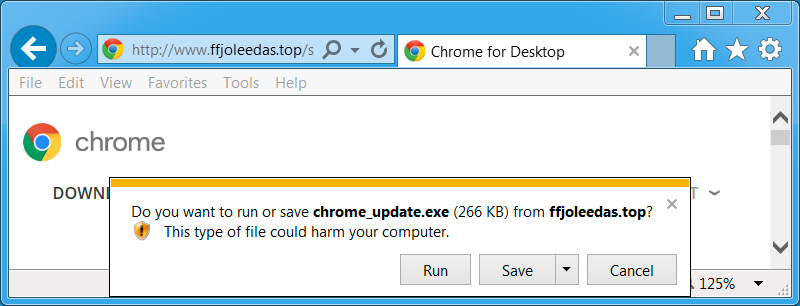
Shown above: No more emails seen, but these fake Chrome install pages are still a thing.
Click here to return to the main page.
