2017-04-03 - HANCITOR INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-03-Hancitor-infection-traffic.pcap.zip 485.1 kB (485,079 bytes)
- 2017-04-03-Hancitor-infection-traffic.pcap (630,633 bytes)
- 2017-04-03-Hancitor-malspam-3-examples.zip 3.1 kB (3,084 bytes)
- 2017-04-03-Hancitor-malspam-1535-UTC.eml (1,129 bytes)
- 2017-04-03-Hancitor-malspam-1537-UTC.eml (1,105 bytes)
- 2017-04-03-Hancitor-malspam-1554-UTC.eml (1,125 bytes)
- 2017-04-03-malware-from-Hancitor-infection.zip 357.8 kB (357,848 bytes)
- 46353.exe (197,632 bytes)
- BN692D.tmp (158,720 bytes)
- Ringcentral_renya.glendayle.doc (241,152 bytes)
NOTES:
- The DELoader/ZLoader malware crashed on the host I infected, so I didn't get the follow-up Tor traffic that I usually see.
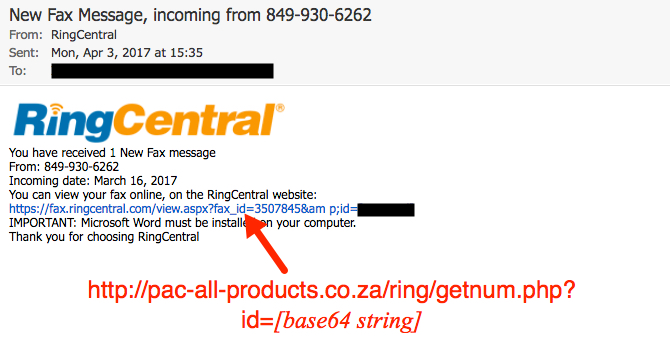
Shown above: Screen shot of the email.
EMAIL HEADERS:
- Date/Time: Monday 2017-04-03 as early as 15:35 UTC
- From: (spoofed) "RingCentral" <message@faxcentral[.]com>
- Subject: New Fax Message, incoming from 849-930-xxxx
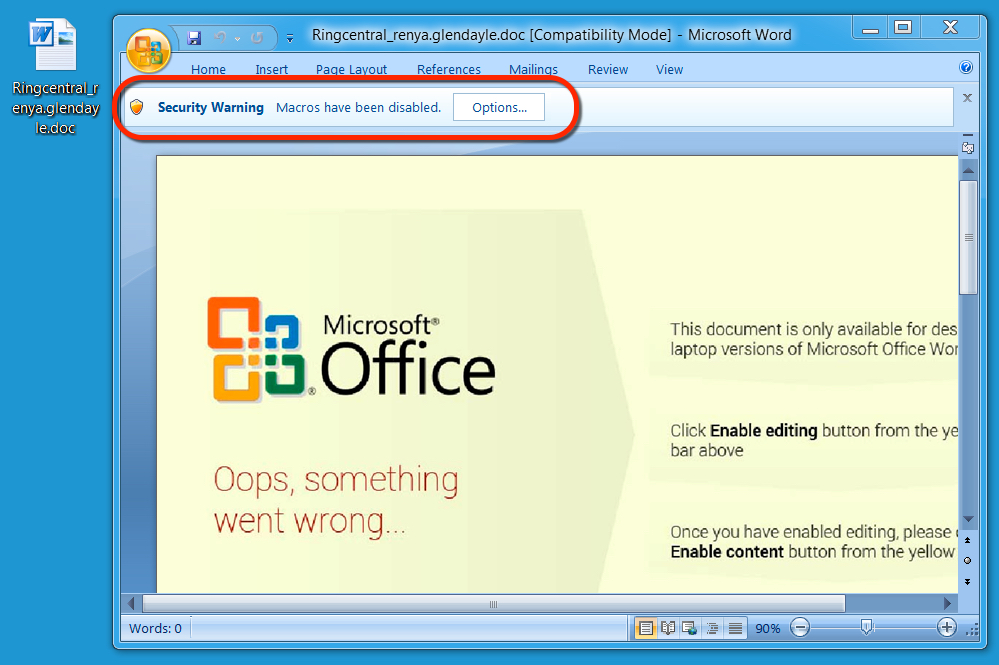
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
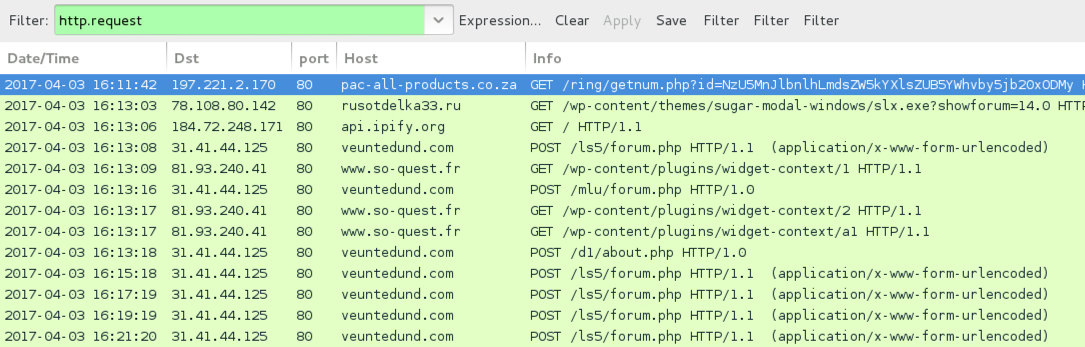
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUEST FOR THE INITIAL DOCUMENT:
- 197.221.2[.]170 port 80 - pac-all-products[.]co[.]za - GET /ring/getnum.php?id=[base64 string]
POST-INFECTION TRAFFIC:
- 78.108.80[.]142 port 80 - rusotdelka33[.]ru - GET /wp-content/themes/sugar-modal-windows/slx.exe?showforum=14.0
- 81.93.240[.]41 port 80 - www.so-quest[.]fr - GET /wp-content/plugins/widget-context/1
- 81.93.240[.]41 port 80 - www.so-quest[.]fr - GET /wp-content/plugins/widget-context/2
- 81.93.240[.]41 port 80 - www.so-quest[.]fr - GET /wp-content/plugins/widget-context/a1
- 31.41.44[.]125 port 80 - veuntedund[.]com - POST /ls5/forum.php
- 31.41.44[.]125 port 80 - veuntedund[.]com - POST /d1/about.php
- 31.41.44[.]125 port 80 - veuntedund[.]com - POST /mlu/forum.php
- api.ipify[.]org - GET /
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 14b45db836ff1c0d7e283d0ff824013d7a48c59d3805c20cf9a4c61106256fe4
File location: Ringcentral_renya.glendayle.doc
File description: Hancitor maldoc
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: fc8e08d0c0039b9fad3a1d0138dafe9428f06fbdc6096292edeae123a9fb7c65
File location: C:\Users\[username]\AppData\Local\Temp\46353.exe
File description: Hancitor binary
- SHA256 hash: 0a6b1ac5472a554e6d72bee875b7b7cdf85c9c1c8765b4f395c8847f47cc5043
File location: C:\Users\[username]\AppData\Local\Temp\BN692D.tmp
File description: DELoader/ZLoader
Click here to return to the main page.
