2017-04-05 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-05-Hancitor-infection-with-ZLoader.pcap.zip 13.8 MB (13,778,275 bytes)
- 2017-04-05-Hancitor-infection-with-ZLoader.pcap (14,582,657 bytes)
- 2017-04-05-Hancitor-malspam-3-examples.zip 2.6 kB (2,628 bytes)
- 2017-04-05-Hancitor-malspam-1512-UTC.eml (763 bytes)
- 2017-04-05-Hancitor-malspam-1526-UTC.eml (737 bytes)
- 2017-04-05-Hancitor-malspam-1733-UTC.eml (789 bytes)
- 2017-04-05-malware-from-Hancitor-infection.zip 189.8 kB (189,773 bytes)
- BN4E.tmp (165,888 bytes)
- d657.exe (156,672 bytes)
- March_invoice_nathaniel.clark.js (33,004 bytes)
NOTES:
- On Wednesday 2017-04-05, links from Hancitor malspam pointed to a .js file instead of a .doc file as we've seen previously.
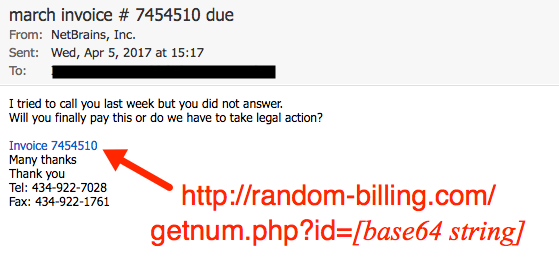
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2017-04-05 as early as 15:12 UTC
- From: (spoofed) "NetBrains, Inc." <billing@netbrain[.]com>
- Subject: march invoice # 1437146 due
- Subject: march invoice # 7454510 due
- Subject: march invoice # 8781758 due
Shown above: Malicious .js file from link in the malspam.
TRAFFIC
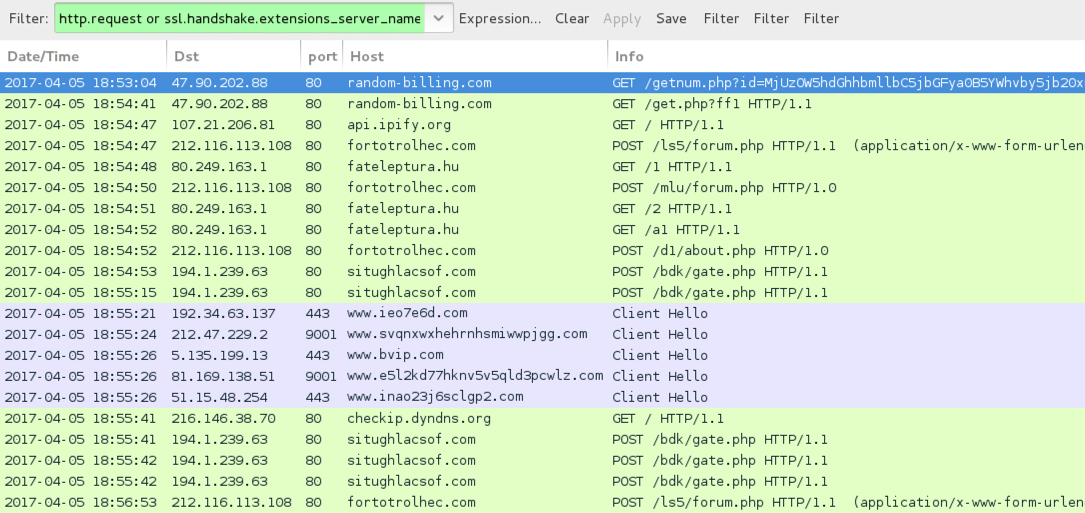
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUEST FOR THE .JS FILE:
- 47.90.202[.]88 port 80 - random-billing[.]com - GET /getnum.php?id=[base64 string]
POST-INFECTION TRAFFIC:
- 47.90.202[.]88 port 80 - random-billing[.]com - GET /get.php?ff1
- 80.249.163[.]1 port 80 - fateleptura[.]hu - GET /1
- 80.249.163[.]1 port 80 - fateleptura[.]hu - GET /2
- 80.249.163[.]1 port 80 - fateleptura[.]hu - GET /a1
- 212.116.113[.]108 port 80 - fortotrolhec[.]com - POST /ls5/forum.php
- 212.116.113[.]108 port 80 - fortotrolhec[.]com - POST /mlu/forum.php
- 212.116.113[.]108 port 80 - fortotrolhec[.]com - POST /d1/about.php
- 194.1.239[.]63 port 80 - situghlacsof[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
.JS FILE FROM LINK IN THE EMAIL:
- SHA256 hash: a882be2a0b1f13b7cf60ed50237344049962bb53e82dbcfb44c33c936895c685
File location: March_invoice_nathaniel.clark.js
File description: Hancitor .js file
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: 1f860dfa7ab0d7cd0d38b5f8e90f68ee9d8b9ce81c1b55fd35c999c445b4349c
File location: C:\Users\[username]\AppData\Local\Temp\d657.exe
File description: Hancitor binary
- SHA256 hash: b2d4609580c64295b5c233bba1205e58e6e0be4b128bc772ace76b65ef9dd902
File location: C:\Users\[username]\AppData\Local\Temp\BN4E.tmp
File description: DELoader/ZLoader
Click here to return to the main page.
