2017-04-13 - "BLANK SLATE" CAMPAIGN STILL PUSHING CERBER RANSOMWARE, STILL USING FAKE CHROME PAGE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-13-Cerber-ransomware-infection-traffic.pcap.zip 385.2 kB (385,212 bytes)
- 2017-04-13-Cerber-ransomware-infection-traffic.pcap (536,245 bytes)
- 2017-04-13-Blank-Slate-emails-and-Cerber-ransomware.zip 366.8 kB (366,829 bytes)
- 2017-04-13-Cerber-ransomware-from-testgojale_com.exe (334,506 bytes)
- 2017-04-13-blank-slate-malspam-1005-UTC.eml (4,245 bytes)
- 2017-04-13-blank-slate-malspam-1330-UTC.eml (4,170 bytes)
- 48.js (8,502 bytes)
- _READ_THI$_FILE_2DKNJ_.hta (77,078 bytes)
- _READ_THI$_FILE_JUTNOHS_.txt (1,378 bytes)
- chrome_update.zip (3,940 bytes)
BACKGROUND:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
OTHER NOTES:
- This blog post documents a slight variation on the fake Microsoft emails leading to a fake Google Chrome page sent from this campaign.
- Of course, the vast majority of Blank Slate malspam is still blank emails only consisting of attachments that are zip archives containing .js files.
- I just haven't had time lately to document the normal Blank Slate emails.
FAKE CHROME PAGE
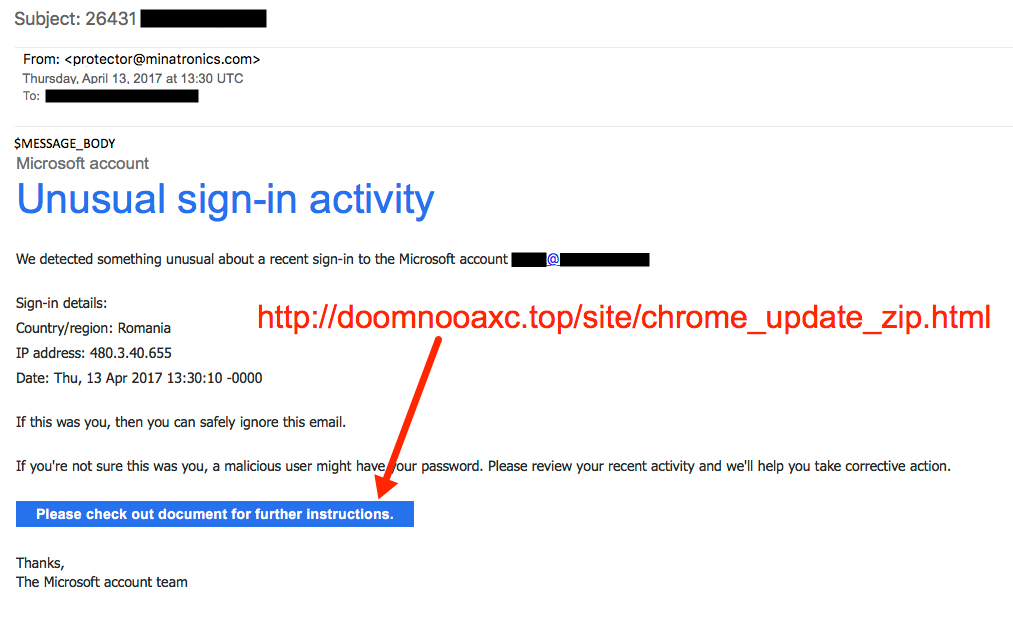
Shown above: Screen shot from the fake Microsoft email.
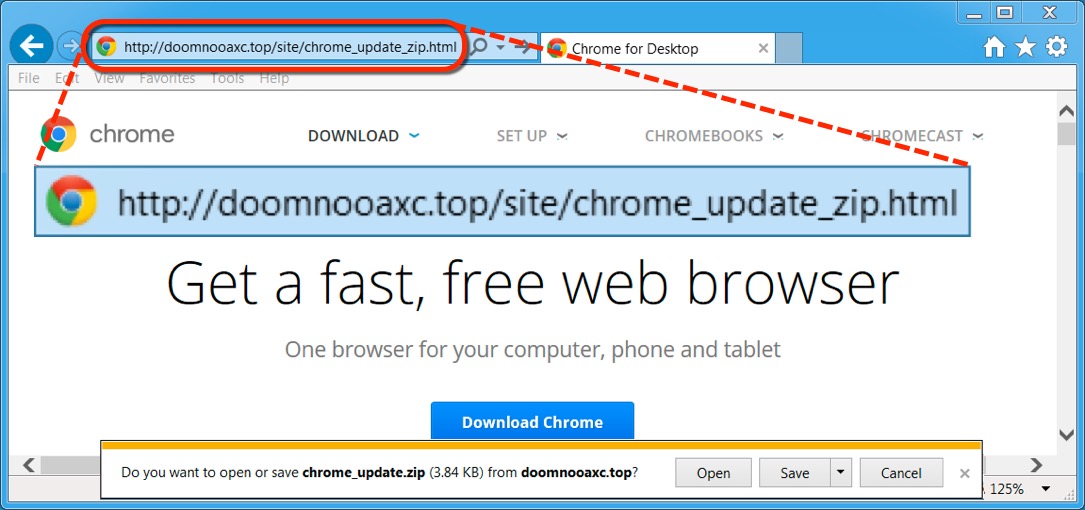
Shown above: Letting the fake Chrome page send a fake Chrome update as a zip archive.
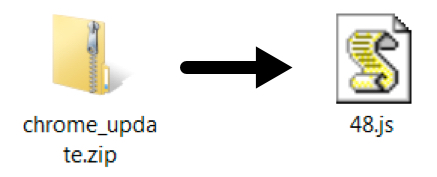
Shown above: Zip acrhive sent by the fake Chrome page.
TRAFFIC
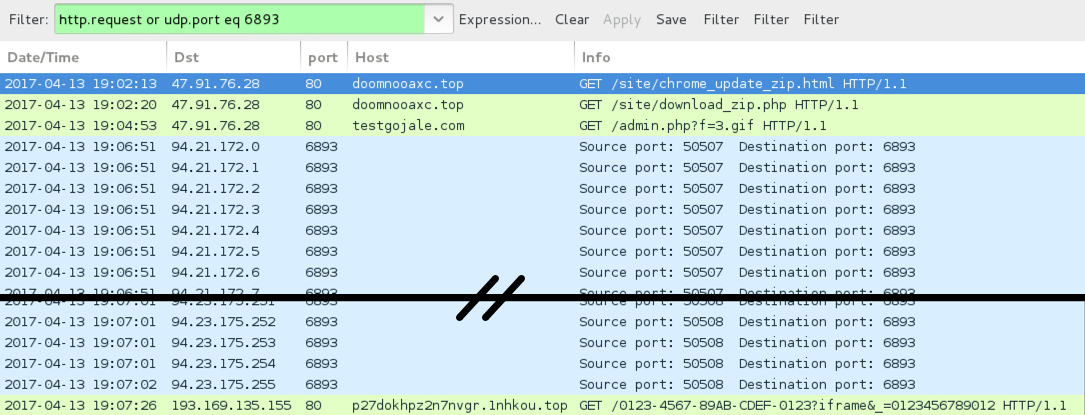
Shown above: Traffic from the infection filtered in Wireshark.
FAKE GOOGLE CHROME PAGE AND ZIP DOWNLOAD:
- 47.91.76[.]28 port 80 - doomnooaxc[.]top - GET /site/chrome_update_zip.html
- 47.91.76[.]28 port 80 - doomnooaxc[.]top - GET /site/download_zip.php
EXTRACTED .JS FILE GRABBING CERBER RANSOMWARE:
- 47.91.76[.]28 port 80 - testgojale[.]com - GET /admin.php?f=3.gif
CERBER RANSOMWARE POST-INFECTION TRAFFIC:
- 94.21.172[.]0 - 94.21.172[.]31 (94.21.172[.]0/27) UDP port 6893
- 94.22.172[.]0 - 94.22.172[.]31 (94.22.172[.]0/27) UDP port 6893
- 94.23.172[.]0 - 94.23.175[.]255 (94.23.172[.]0/22) UDP port 6893
- 193.169.135[.]155 port 80 - p27dokhpz2n7nvgr.1nhkou[.]top
MALWARE
SHA256 HASHES:
- SHA256 hash: 3de3fd9cda91e91b24c5569e4d2874ed5a8105e28c43dae911ab2b86e87e7505
File name: chrome_update.zip
File description: Downloaded from fake Google Chrome page at doomnooaxc[.]top on 2017-04-13
- SHA256 hash: cdd6286df651a213d2e13253ea67602db628fb1a8625ca4e308a0766866373ec
File name: 48.js
File description: Malicious .js file extracted from chrome_update.zip
- SHA256 hash: 5d947667bb754a1e1716bec2f86fb82ed5cc8dc5bf8d5c34d15ef232f8f6feb4
File description: Cerber ransomware downloaded by 48.js from testgojale.com on 2017-04-13
IMAGES
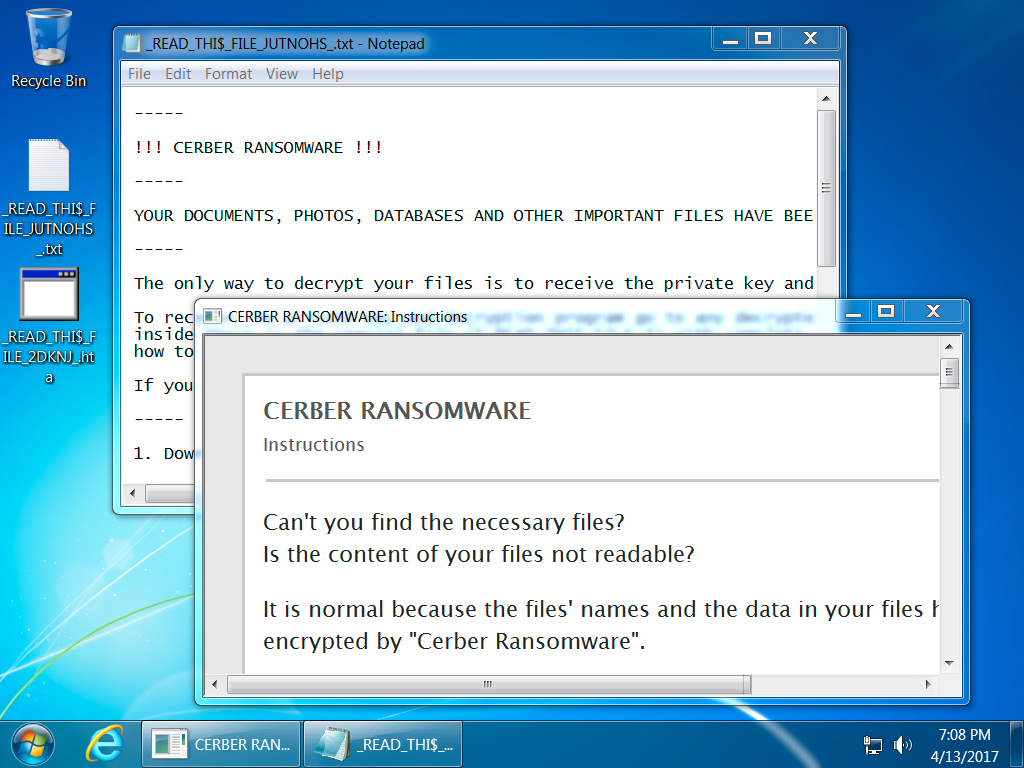
Shown above: Desktop of an infected Windows host. Still using dollar signs in _READ_THI$_FILE_ for file names. No more images with the instructions, though.
Click here to return to the main page.
