2017-04-19 - ZEUS PANDA BANKER, KOVTER AND MIUREF INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-19-Zeus-Panda-Banker-and-Kovter-and-Miuref-infection-traffic-2-pcaps.zip 11.7 MB (11,746,543 bytes)
- 2017-04-19-USPS-themed-malspam-tracker.csv.zip 3.3 kB (3,260 bytes)
- 2017-04-19-USPS-themed-emails-and-associated-malware.zip 754.3 kB (754,332 bytes)
NOTES:
USPS-themed malspam continues. Today, the emails have links that go directly to fake Word Online sites. These fake Word Online sites distribute zipped .js files disguised as Office plugins. The end result is the same as yesterday, with the campaign pushing Zeus Panda Banker, Kovter, and Miuref/Boaxxe.
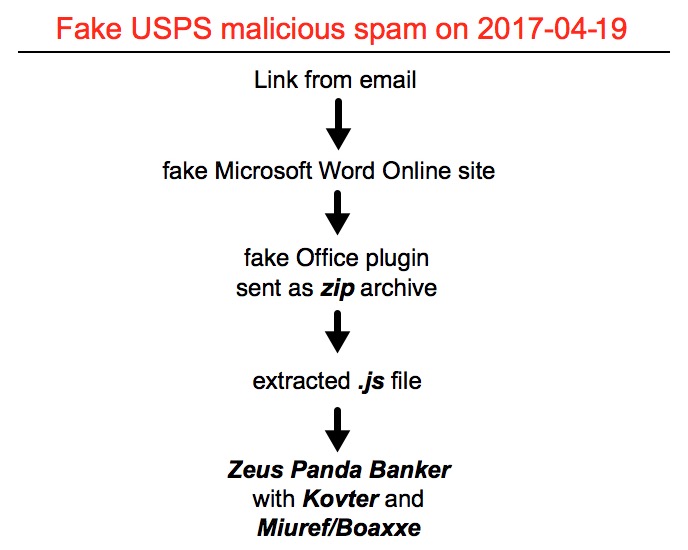
Shown above: Flowchart for this infection traffic.
EMAILS
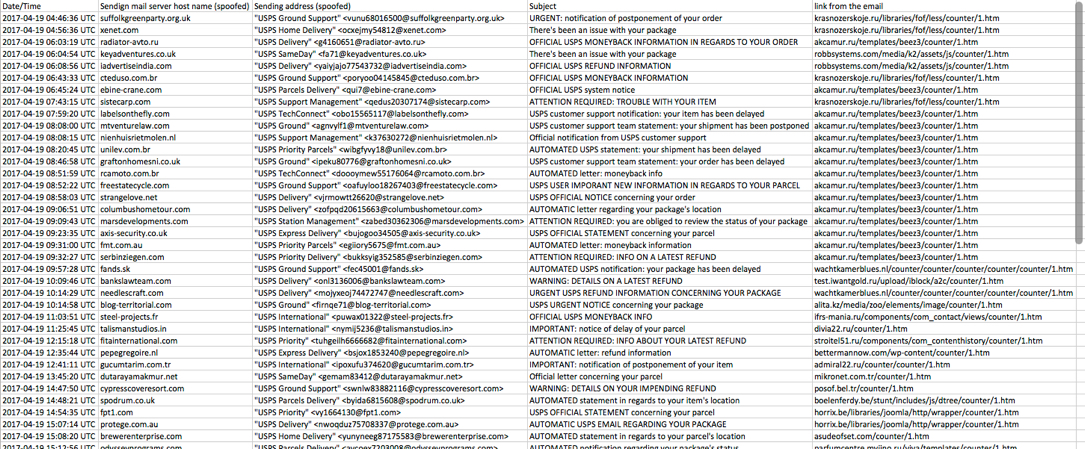
Shown above: Screen shot of the spreadsheet tracker.
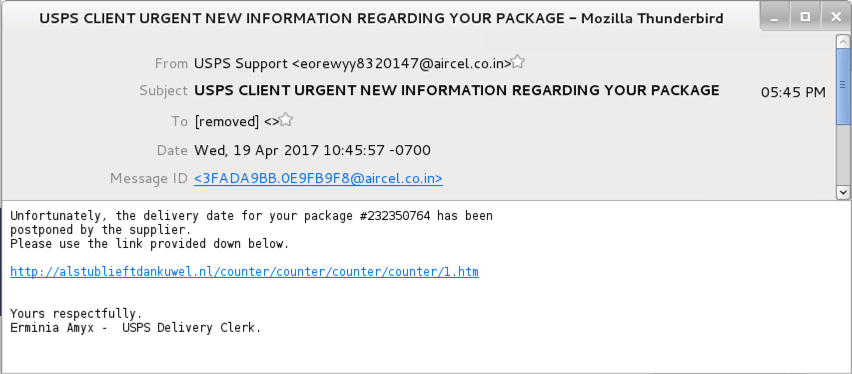
Shown above: Example of one of these emails.
DATES/TIMES:
- Tuesday Wednesday 2017-04-19 as early as 04:46 UTC through at least 17:46 UTC
EXAMPLES OF SENDING ADDRESSES (ALL SPOOFED):
- "USPS Delivery" <g4160651@radiator-avto[.]ru>
- "USPS Delivery" <mojyxeoj74472747@needlescraft[.]com>
- "USPS Delivery" <nwoqduz75708337@protege[.]com[.]au>
- "USPS Delivery" <onl3136006@bankslawteam[.]com>
- "USPS Delivery" <vjrmowtt26620@strangelove[.]net>
- "USPS Delivery" <yaiyjajo77543732@iadvertiseindia[.]com>
- "USPS Delivery" <ynxkkeyo03233040@hopechennai[.]com>
- "USPS Delivery" <zofpqd20615663@columbushometour[.]com>
- "USPS Express Delivery" <bsjox1853240@pepegregoire[.]nl>
- "USPS Express Delivery" <bujogoo34505@axis-security[.]co[.]uk>
- "USPS Ground Support" <fec45001@fands[.]sk>
- "USPS Ground Support" <jwidiyt62054011@netidev[.]com>
- "USPS Ground Support" <oafuyloo18267403@freestatecycle[.]com>
- "USPS Ground Support" <poryoo04145845@cteduso[.]com[.]br>
- "USPS Ground Support" <swnlw83882116@cypresscoveresort[.]com>
- "USPS Ground Support" <vunu68016500@suffolkgreenparty[.]org[.]uk>
- "USPS Ground" <agnvylf1@mtventurelaw[.]com>
- "USPS Ground" <firnqe71@blog-territorial[.]com>
- "USPS Ground" <ipeku80776@graftonhomesni[.]co[.]uk>
- "USPS Home Delivery" <ocxejmy54812@xenet[.]com>
- "USPS Home Delivery" <weqixgo74057530@realladrilhos[.]com[.]br>
- "USPS Home Delivery" <yunyneeg87175583@brewerenterprise[.]com>
- "USPS International" <ipoxufu374620@gucumtarim[.]com[.]tr>
- "USPS International" <nymij5236@talismanstudios[.]in>
- "USPS International" <puwax01322@steel-projects[.]fr>
- "USPS International" <vyebouig5081867@gabrielparra[.]net>
- "USPS Parcels Delivery" <avcoex7203008@odysseyprograms[.]com>
- "USPS Parcels Delivery" <byida6815608@spodrum[.]co[.]uk>
- "USPS Parcels Delivery" <ioorwi48205672@rejoicetea[.]com>
- "USPS Parcels Delivery" <iteurzid82466787@axiom3[.]com>
- "USPS Parcels Delivery" <kemydje45521@earj[.]com[.]br>
- "USPS Parcels Delivery" <qui7@ebine-crane[.]com>
- "USPS Priority Delivery" <bukksyig352585@serbinziegen[.]com>
- "USPS Priority Delivery" <ozacireb8@puzzle-my-picture[.]com>
- "USPS Priority Parcels" <egiiory5675@fmt[.]com[.]au>
- "USPS Priority Parcels" <wibgfyvy18@unilev[.]com[.]br>
- "USPS Priority" <tuhgeilh6666682@fitainternational[.]com>
- "USPS Priority" <vy1664130@fpt1[.]com>
- "USPS SameDay" <fa71@keyadventures[.]co[.]uk>
- "USPS SameDay" <gemam83412@dutarayamakmur[.]net>
- "USPS Station Management" <ci3046188@premiumdoener[.]eu>
- "USPS Station Management" <pokqyyy86821746@bolideco[.]com>
- "USPS Station Management" <zabed30362306@marsdevelopments[.]com>
- "USPS Station Management" <zijahyno6766657@dwglesson[.]ru>
- "USPS Support Management" <k37630272@nienhuisrietmolen[.]nl>
- "USPS Support Management" <qedus20307174@sistecarp[.]com>
- "USPS Support Management" <sxozi7570@skift[.]com>
- "USPS Support" <eorewyy8320147@aircel[.]co[.]in>
- "USPS TechConnect" <doooymew55176064@rcamoto[.]com[.]br>
- "USPS TechConnect" <obo15565117@labelsonthefly[.]com>
EXAMPLES OF SUBJECT LINES:
- ATTENTION REQUIRED: INFO ABOUT YOUR LATEST REFUND
- ATTENTION REQUIRED: INFO ON A LATEST REFUND
- ATTENTION REQUIRED: TROUBLE WITH YOUR ITEM
- ATTENTION REQUIRED: you are obliged to review the status of your package
- AUTOMATED letter: moneyback info
- AUTOMATED letter: moneyback information
- AUTOMATED notification concerning your shipment's status
- AUTOMATED notification regarding your package's status
- AUTOMATED notification: moneyback info
- AUTOMATED statement in regards to your item's location
- AUTOMATED statement in regards to your parcel's location
- AUTOMATED USPS notification: your package has been delayed
- AUTOMATED USPS statement: your shipment has been delayed
- AUTOMATIC letter regarding your package's location
- AUTOMATIC letter: refund information
- AUTOMATIC USPS EMAIL REGARDING YOUR PACKAGE
- IMPORTANT USPS REFUND INFORMATION IN REGARDS TO YOUR SHIPMENT
- IMPORTANT: notice of delay of your parcel
- IMPORTANT: notification of postponement of your item
- Major problems reported to the USPS
- Official letter concerning your parcel
- Official notification from USPS customer support
- OFFICIAL USPS MONEYBACK INFO
- OFFICIAL USPS MONEYBACK INFORMATION
- OFFICIAL USPS MONEYBACK INFORMATION IN REGARDS TO YOUR ORDER
- OFFICIAL USPS REFUND INFORMATION
- OFFICIAL USPS system notice
- There's been an issue with your package
- URGENT USPS REFUND INFORMATION CONCERNING YOUR PACKAGE
- URGENT: notification of postponement of your order
- USPS CLIENT URGENT NEW INFORMATION REGARDING YOUR PACKAGE
- USPS customer support notification: your item has been delayed
- USPS customer support team statement: your order has been delayed
- USPS customer support team statement: your shipment has been postponed
- USPS OFFICIAL NOTICE concerning your order
- USPS official notice: major issues with your shipment
- USPS OFFICIAL STATEMENT concerning your parcel
- USPS support statement: your item has been delayed
- USPS URGENT LETTER in regards to your item
- USPS URGENT NOTICE concerning your package
- USPS USER IMPORANT NEW INFORMATION IN REGARDS TO YOUR PARCEL
- USPS USER URGENT NEW INFO REGARDING YOUR ORDER
- WARNING: DETAILS ON A LATEST REFUND
- WARNING: DETAILS ON YOUR IMPENDING REFUND
- WARNING: you're legally obliged to review the status of your item
- WARNING: you're required to check the status of your shipment
TRAFFIC
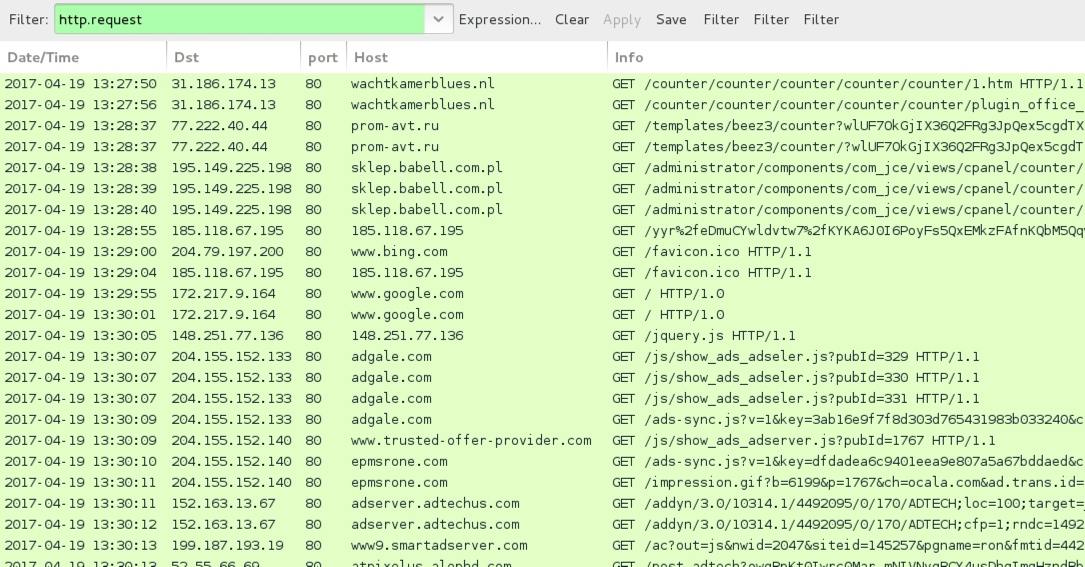
Shown above: Traffic from an infection filtered in Wireshark.
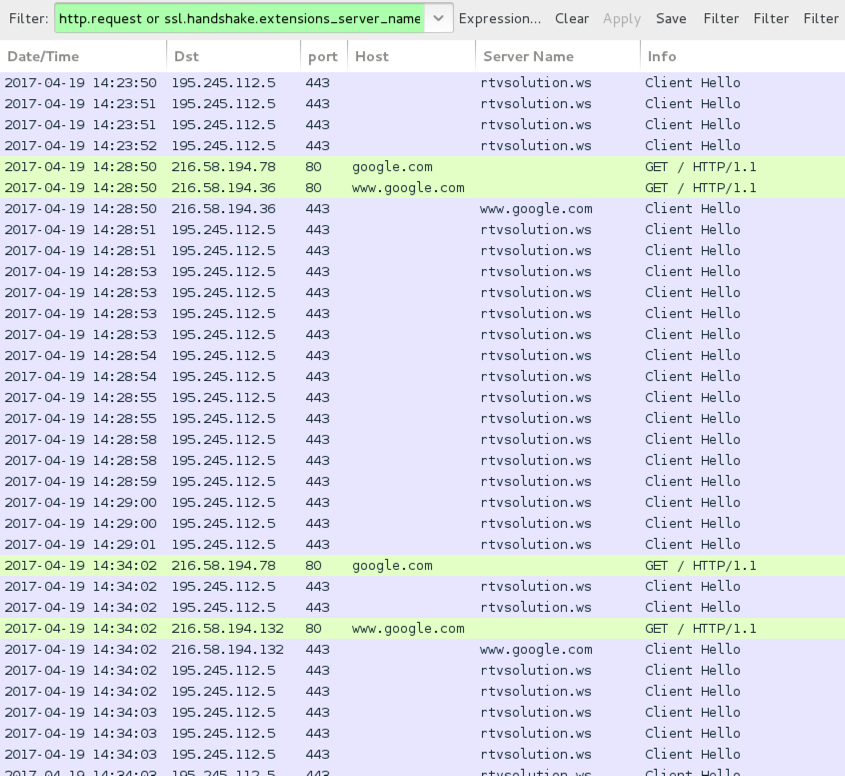
Shown above: Post-infection traffic from the Zeus Panda Banker (exe1.exe) separated from the other traffic.
NOTES: The Zeus Panda Banker didn't create any traffic right away. My sample waited about 5 minutes or so before generating any post-infection network activity. If I included it in the regular pcap, that pcap would be well over 100 MB in size (due to all the other post-infection traffic). So I infected another host with only the Zeus Panda Banker to show that traffic.
LINKS FROM THE EMAILS:
- admiral22[.]ru - GET /counter/counter/1.htm
- akcamur[.]ru - GET /templates/beez3/counter/1.htm
- alita.kz - GET /media/zoo/elements/image/counter/1.htm
- alstublieftdankuwel[.]nl - GET /counter/counter/counter/counter/1.htm
- asudeofset[.]com - GET /counter/1.htm
- belturhotel[.]com - GET /wp-includes/js/plupload/counter/1.htm
- bettermannow[.]com - GET /wp-content/counter/1.htm
- boelenferdy.be - GET /stunt/includes/js/dtree/counter/1.htm
- divia22[.]ru - GET /counter/1.htm
- emsp[.]ru - GET /counter/1.htm
- freetreeopenair[.]at - GET /libraries/joomla/feed/parser/counter/1.htm
- horrix.be - GET /libraries/joomla/http/wrapper/counter/1.htm
- ifrs-mania[.]ru - GET /components/com_contact/views/counter/1.htm
- jerzynowak[.]com[.]pl - GET /libraries/joomla/cache/counter/1.htm
- krasnozerskoje[.]ru - GET /libraries/fof/less/counter/1.htm
- mikronet[.]com[.]tr - GET /counter/1.htm
- myxpert[.]ch - GET /templates/beez3/html/com_newsfeeds/counter/1.htm
- parfumcentre.myjino[.]ru - GET /viva/templates/counter/1.htm
- posof.bel[.]tr - GET /counter/1.htm
- prom-avt[.]ru - GET /templates/beez3/counter/1.htm
- robbsystems[.]com - GET /media/k2/assets/js/counter/1.htm
- sistematn[.]ru - GET /fobp/vol/counter/1.htm
- stroitel51[.]ru - GET /components/com_contenthistory/counter/1.htm
- sulfor-workshop[.]org - GET /counter/1.htm
- test.iwantgold[.]ru - GET /upload/iblock/a2c/counter/1.htm
- wachtkamerblues[.]nl - GET /counter/counter/counter/counter/counter/1.htm
PARTIALS URLS FROM THE .JS FILES FOR ADDITIONAL MALWARE:
- chateaudesbourines[.]com - GET /libraries/fof/download/adapter/counter
- hotelesencarnaciondediaz[.]com - GET /libraries/joomla/cache/controller/counter
- myxpert[.]ch - GET /templates/beez3/html/com_newsfeeds/counter
- prom-avt[.]ru - GET /templates/beez3/counter
- test.iwantgold[.]ru - GET /upload/iblock/a2c/counter
MALWARE
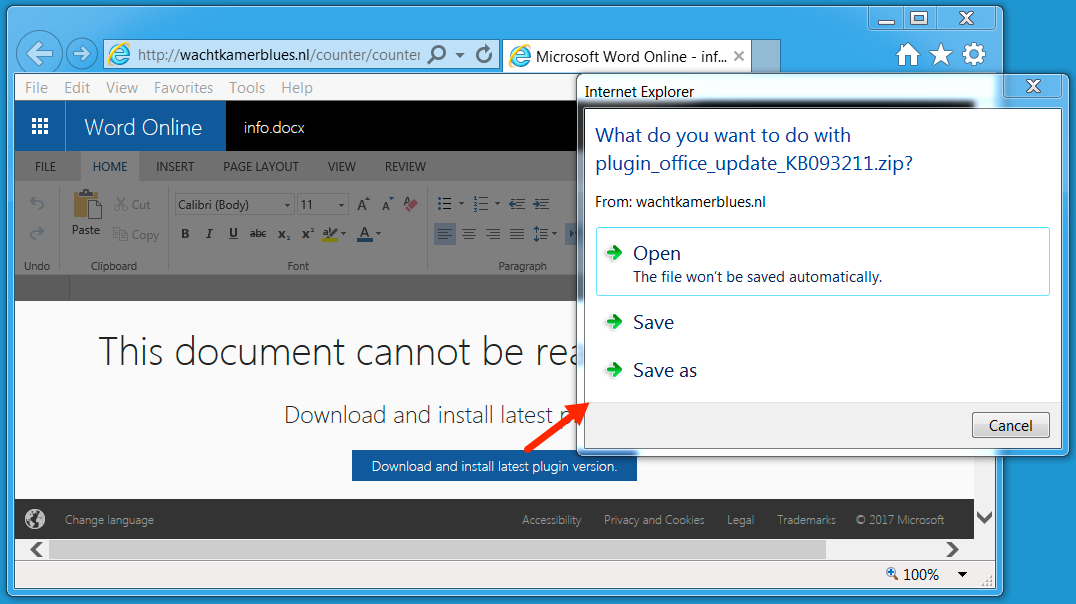
Shown above: Zip archive disguised as an Office plugin downloaded from a fake Word Online page.
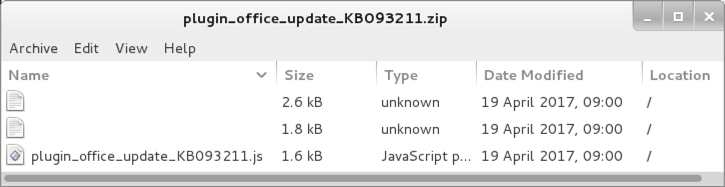
Shown above: Contents of the downloaded zip archive.
EXAMPLE OF ZIP ARCHIVE FROM FAKE WORD ONLINE SITE:
- SHA256 hash: a2585201421ddc107b4de5690caccdf4adeae9554af95d5ab470191d38173e32
File size: 4,526 bytes (contains a .js file and two other garbage files)
File name: plugin_office_update_KB093211.zip
.JS FILE EXTRACTED FROM THE DOWNLOADED ZIP ARCHIVE:
- SHA256 hash: 7659654b930ed572f3528a03ef135c90c319defeb48c8b8396e19df22660f3a3
File size: 1,602 bytes
File name: plugin_office_update_KB093211.js
EXAMPLES OF MALWARE DOWNLOADED BY THE EXTRACTED .JS FILE:
- SHA256 hash: c781a2dc4de1d1a6f01dd6b93b20b2d3ab9d56dea2110f9b84db6c47ad0877f2
File size: 323,584 bytes
File name: exe1.exe
File description: Zeus Panda Banker
- SHA256 hash: f8b38728dcb83fd6aeecda6bb787473f054a5af9dd1e592b43405ae6ddcbac56
File size: 415,798 bytes
File name: exe2.exe
File description: Kovter
- SHA256 hash: fac09ff77baf7c744bcc2aa952ec84428f4942e02530bcca14b40825eaf9f7e2
File size: 112,560 bytes
File name: exe3.exe
File description: Miuref/Boaxxe
ARTIFACT LOCATIONS
SOME ARTIFACT LOCATIONS ON THE INFECTED WINDOWS HOST:
- C:\Users\[username]\AppData\Local\6b59565b\26aed7bb.bat
- C:\Users\[username]\AppData\Local\6b59565b\e1c6dce7.6036e91bf
- C:\Users\[username]\AppData\Local\Oznics\pffpubjp.2
- C:\Users\[username]\AppData\Local\Oznics\pffpubjp.dll
- C:\Users\[username]\AppData\Local\Upmqmedia\{583452A8-C4CC-8262-7E22-E606977AAB64}
- C:\Users\[username]\AppData\Local\Upmqmedia\exe3.exe
- C:\Users\[username]\AppData\Local\Upmqmedia\mdwkecqb.2
- C:\Users\[username]\AppData\Local\Upmqmedia\mdwkecqb.dll
- C:\Users\[username]\AppData\Local\Temp\diminuendos.dll
- C:\Users\[username]\AppData\Local\Temp\exe1.exe
- C:\Users\[username]\AppData\Local\Temp\exe2.exe
- C:\Users\[username]\AppData\Local\Temp\exe3.exe
- C:\Users\[username]\AppData\Local\Temp\nswF0C5.tmp\System.dll
- C:\Users\[username]\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\TranscodedWallpaper.exe
- C:\Users\[username]\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\desktop.osy
- C:\Users\[username]\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\Ease of Access.aqa
- C:\Users\[username]\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol
- C:\Users\[username]\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\TranscodedWallpaper.hup
Registry key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: Omxics
- Value name: C:\Windows\SysWOW64\regsvr32.exe C:\Users\[username]\AppData\Local\Upmqmedia\mdwkecqb.dll
- Value name: Oznics
- Value name: regsvr32.exe C:\Users\[username]\AppData\Local\Oznics\pffpubjp.dll
- Value name: TranscodedWallpaper.exe
- Value name: "C:\Users\[username]\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\TranscodedWallpaper.exe"
- Value name: Upmqmedia
- Value name: C:\Users\[username]\AppData\Local\Upmqmedia\exe3.exe
Click here to return to the main page.
