2017-04-19 - DRIDEX INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-19-Dridex-infection-traffic.pcap.zip 1.4 MB (1,432,787 bytes)
- 2017-04-19-Dridex-malspam-tracker.csv.zip 1.6 kB (1,572 bytes)
- 2017-04-19-Dridex-emails-and-malware.zip 3.8 MB (3,807,431 bytes)
BACKGROUND ON THIS CAMPAIGN:
- After a 6-month hiatus, malspam pushing Dridex came back in January 2017 (link), but I hadn't personally run across any Dridex until 2017-03-30.
- Since that time, mass-distribution Dridex has been on again/off again, with some malspam runs featuring a former Microsoft zero-day exploit for CVE-2017-0199 (link).
- Unfortunately, I haven't seen any of those emails with exploits based on CVE-2017-0199.
- I've only occasionally seen today's sort of malspam, with PDF attachments having embedded Word documents.
- You must enable macros on those embedded Word documents before an infection can occur.
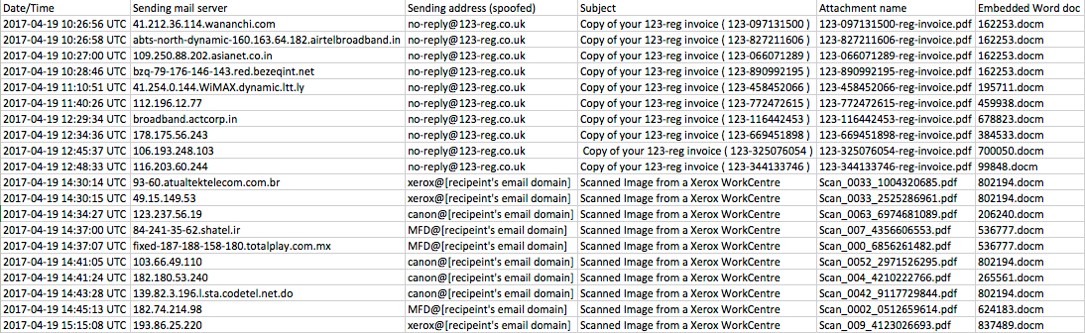
Shown above: Screenshot of today's Dridex malspam tracker.
EMAILS
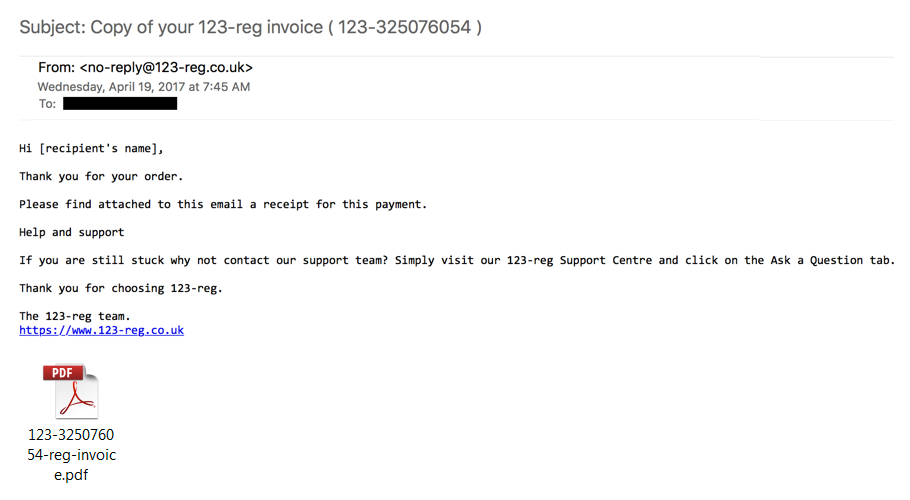
Shown above: Example of an email from the 1st wave of Dridex malspam.
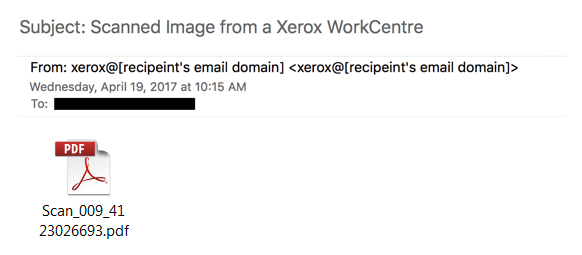
Shown above: Example of an email from the 2nd wave of Dridex malspam.
FIRST WAVE:
- Date/Time: Wednesday 2017-04-19 as early as 10:26 UTC through at least 12:49 UTC
- From: no-reply@123-reg[.]co[.]uk
- Subject: Copy of your 123-reg invoice ( 123-456789012 ) [number changes for each message]
- Attachment name: 123-456789012-reg-invoice.pdf [number matches subject line]
SECOND WAVE:
- Date/Time: Wednesday 2017-04-19 as early as 14:30 UTC through at least 15:16 UTC
- From: canon@[recipeint's email domain]
- From: MFD@[recipeint's email domain]
- From: xerox@[recipeint's email domain]
- Subject: Scanned Image from a Xerox WorkCentre
- Attachment name: Scan_[3 to 4 digits]_[10 digits].pdf
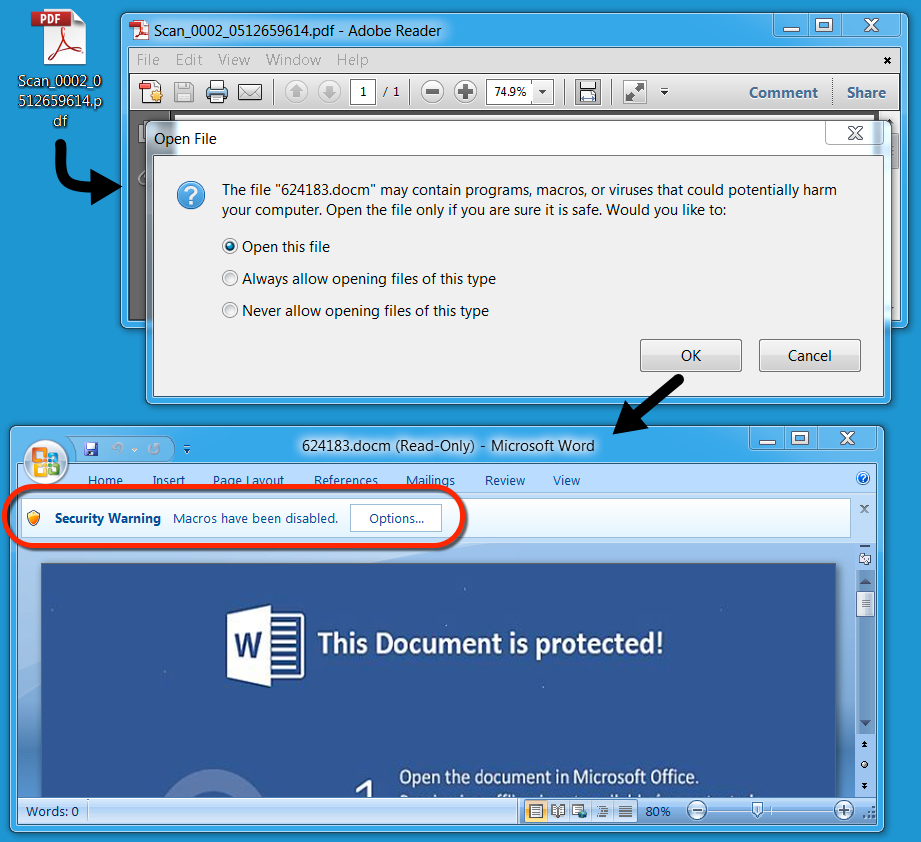
Shown above: How attachments from both waves of malspam behave.
TRAFFIC
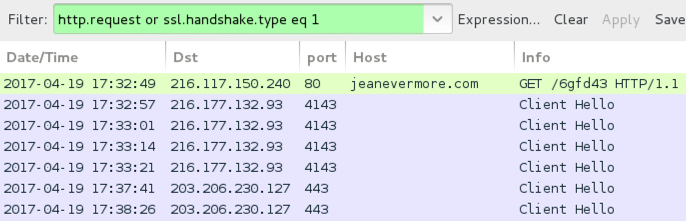
Shown above: Traffic from an infection filtered in Wireshark.
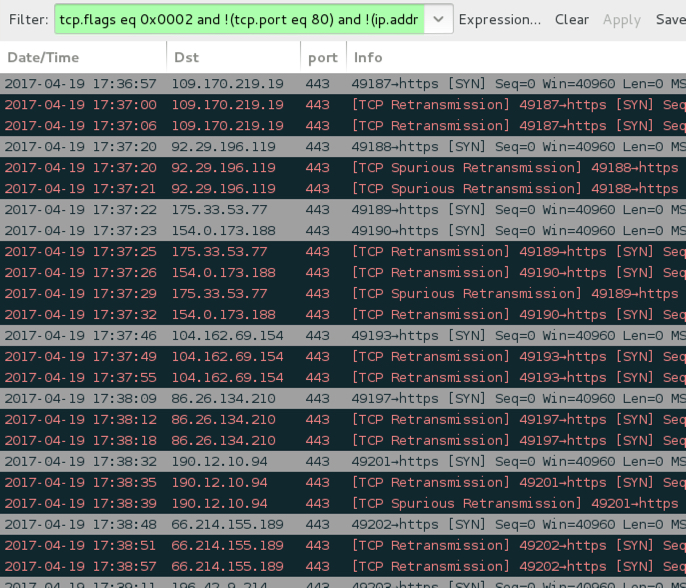
Shown above: More Wireshark filtering shows attempted TCP connections by the infected host.
URLS TO RETRIEVE DRIDEX FROM THE WORD DOCUMENT MACROS:
- barkave.comcastbiz[.]net - GET /6gfd43
- barrets[.]com[.]br - GET /6gfd43
- carterfabricationsinc.comcastbiz[.]net - GET /6gfd43
- cleck.comcastbiz[.]net - GET /6gfd43
- dbrose[.]com - GET /6gfd43
- drsketchy[.]ph - GET /6gfd43
- explorer.comcastbiz[.]net - GET /6gfd43
- gth[.]co[.]uk - GET /6gfd43
- hammis[.]com - GET /6gfd43
- hawgshackcycles.comcastbiz[.]net - GET /6gfd43
- integritycomputers[.]biz - GET /6gfd43
- jeanevermore[.]com - GET /6gfd43
- jure[.]cl - GET /6gfd43
- keane-hypnotherapy[.]com - GET /6gfd43
- mayod[.]net - GET /6gfd43
- michaelflood.comcastbiz[.]net - GET /6gfd43
- murrellswaterproofing[.]com - GET /6gfd43
- narucom[.]com - GET /6gfd43
- ormagraphica[.]it - GET /6gfd43
- pierreleroy[.]net - GET /6gfd43
- steve-b[.]com - GET /6gfd43
- thefatdude[.]co[.]uk - GET /6gfd43
- twotime.comcastbiz[.]net - GET /6gfd43
- webrus[.]net - GET /6gfd43
INFECTING A WINDOWS HOST BY ENABLING MACROS ON THE EMBEDDED WORD DOCUMENT:
- 216.117.150[.]240 port 80 - jeanevermore[.]com GET - GET /6gfd43
- 216.177.132[.]93 port 4143 - HTTPS/SSL/TLS traffic with Dridex-associated certifcate
- 203.206.230[.]127 port 443 - HTTPS/SSL/TLS traffic with Dridex-associated certifcate
OTHER ATTEMPTED TCP CONNECTIONS FROM THE INFECTED HOST:
- 2.220.229[.]217 port 443
- 66.214.155[.]189 port 443
- 86.26.134[.]210 port 443
- 92.29.196[.]119 port 443
- 104.162.69[.]154 port 443
- 109.170.219[.]19 port 443
- 154.0.173[.]188 port 443
- 175.33.53[.]77 port 443
- 190.12.10[.]94 port 443
- 196.42.9[.]214 port 443
MALWARE
SHA256 HASHES FOR THE ATTACHED PDF FILES:
- 05dd48c95e4e1b81786f9a3f4fcb7a41cc311f55ea8ecddd7f6e859df636e3ca
- 2e9c00a2068a594bef50ac27c0f90e4640689fb6ef1173641220f57b09c47e18
- 37b7487ca7cb16b973e35b3afc63202035bb53d04d15b2150fb5754cb334492e
- 44a7a6e85201a73a35b63c7d0e36320b52dd9023cdea50f8c551687398244c37
- 48c3d56e55697eae003c953f1830e76412241d147aa7ac2231eb39c9f3a266fc
- 4bd1cdd02acc8bd849617120e526c412acd026b92e63438c58a637122eddb634
- 6af64a4869c248ad84d07f0effd7a192d6d63844b5841869ffa9fb993d96482b
- 73a89bcbf9b8176f4acafc2b4b4ad5d145d00c30c436eabf996a640accb15789
- 7460aedf462c05480f036c4d7f5958254208a8cb3db6b1028edb0100717ebc73
- 77afe8ea7a346f93d226245df36907d414052896fdd1a7f03f58621239991859
- 9e1f83c6d7957302282f35d3188c82631d27bab8614120d8fc1a5a75121b69c5
- bedcb0aaf08b9730fd758f8fc803e2d44530eb03e41a68552bcdaf9965915ed1
- c7788d23647fa3a7f488a66d0ecd0263432e2d528939db1cdbe67865feec220f
SHA256 HASHES FOR WORD DOCUMENTS EMBEDDED IN THOSE PDF FILES:
- 2b69fd2f9c8752487979c4dceb167a6fca47c462304ec3ca4f2892959fd66b7f
- 5376e3d22a581353cd6edfc9cc27746c558e8749cec5734e93b22ff5e7e5854d
- 61a97941f79d6de863f3f539f64d15b6dfa97e27450e41df03c569c43e0dcbf4
- 710068bcc78b498cde513b3aec41532ffb1bd0587f05e3cdac05e3256ffd5d24
- 864fae08d1db98f1b85df2a5e5523253f1f00eb2d576b38c7591c1985e9b8e63
- 92dd9711f6c6d213df7cfe1b0b1302b685c893e57c246f39bc99aec8db91c0e0
- 9a0f58b63e18003b3e6248115ee1eced2fd4d6a746902eb47ab16ea41ddcec94
- 9f62445b29957ebce2adeca845f412a1c1c67f14eb65a43c7a90e15fc5877e7b
- a1f8cee16dc73af43164f2997ddfb2939c7e928fd85899d4d784d9c7a283f677
- b01e1a7d9949b90eccbfc5c2b757739f5f03dc0884af5675956d3a3b95df8bd4
- d4a36a990b6a82c8c924177ba6c79ba6c3ce1bc9ad2f191aa206ed0e9b9f2b0e
- f74c197bc0a4d3e8c7e477b35b1a2596160722d506969b7322a7326c6c5e8c70
- fa96716253d79a8a2b77dbaad32632e613f2b5dff494c37bb1cc22eeab629299
ARTIFACTS FROM AN INFECTED WINDOWS HOST:
- C:\Users\[removed]\AppData\Local\Temp\cAgE.cmd [Windows command shell script]
- C:\Users\[removed]\AppData\Local\Temp\ferbys2 [encrypted Dridex binary]
- C:\Users\[removed]\AppData\Local\Temp\redchip2.exe [decrypted Dridex binary]
- C:\Users\[removed]\AppData\Roaming\GmB8Yb\OLEACC.dll [other artifact found on the infected host]
- C:\Users\[removed]\AppData\Roaming\GmB8Yb\SnippingTool.exe [copy of legitimate Windows Snipping Tool executable]
DRIDEX EXECUTABLE:
- SHA256 hash: 760390f07cefafadece0638a643d69964433041abeab09b65bfcdb922c047872
File size: 151,552 bytes
File location: C:\Users\[removed]\AppData\Local\Temp\redchip2.exe
OTHER ARTIFACTS FROM THE INFECTED HOST:
- SHA256 hash: 2c9e1e1ed5743d4ab67e1902ab3dbd3c577bb7cdaed3d47619455314700377c3
File size: 442,368 bytes
File location: C:\Users\[removed]\AppData\Roaming\GmB8Yb\OLEACC.dll
- SHA256 hash: 890884c7fe7d037e6debd21d1877e9c9c5e7790cdba007ddb219ae6a55667f78
File size: 431,104 bytes
File location: C:\Users\[removed]\AppData\Roaming\GmB8Yb\SnippingTool.exe
File description: A legitimate executable (Windows Snipping Tool) copied to this directory... Not actual malware.
Click here to return to the main page.
