2017-04-20 - "BLANK SLATE" CAMPAIGN STILL PUSHING CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-20-Cerber-ransomware-from-badwerkad_top.pcap.zip 302.6 kB (302,604 bytes)
- 2017-04-20-Blank-Slate-malspam-tracker.csv.zip 0.9 kB (940 bytes)
- 2017-04-20-Blank-Slate-emails-and-Cerber-ransomware.zip 336.3 kB (336,341 bytes)
BACKGROUND:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
OTHER NOTES:
- Just the normal round of Blank Slate emails seen today.
- Normal Blank Slate emails only consist of zip attachments containing .js files designed to download and install ransomware (today, Cerber ransomware).
- I didn't find any fake Microsoft emails linking to fake Google Chrome pages today.
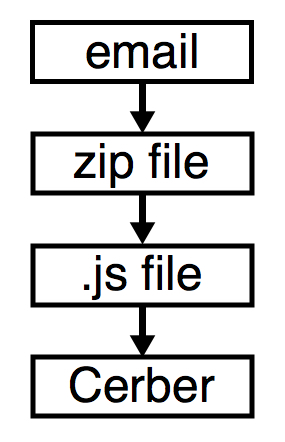
Shown above: Flow chart for these emails.
Shown above: Didn't see any malspam for them, even if those fake Google Chrome pages are still active.
EMAILS
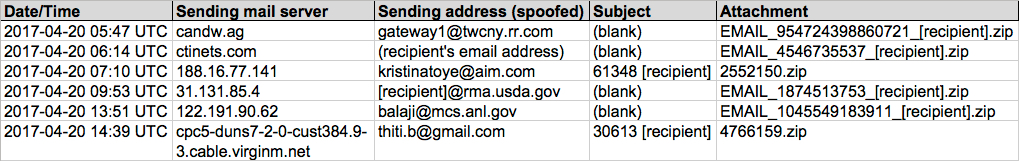
Shown above: Data from the spreadsheet tracker (image 1 of 3).
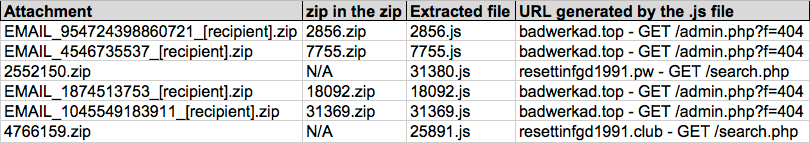
Shown above: Data from the spreadsheet tracker (image 2 of 3).
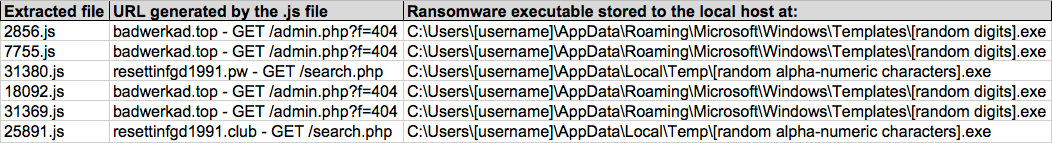
Shown above: Data from the spreadsheet tracker (image 3 of 3).
(READ: Date/Time -- Sending mail server -- Sending address (spoofed) -- Subject -- Attachment name)
- 2017-04-20 05:47 UTC -- candw[.]ag -- gateway1@twcny.rr[.]com -- (blank) -- EMAIL_954724398860721_[recipient].zip
- 2017-04-20 06:14 UTC -- ctinets[.]com -- (recipient's email address) -- (blank) -- EMAIL_4546735537_[recipient].zip
- 2017-04-20 07:10 UTC -- 188.16.77[.]141 -- kristinatoye@aim[.]com -- 61348 [recipient] -- 2552150.zip
- 2017-04-20 09:53 UTC -- 31.131.85[.]4 -- [recipient]@rma.usda[.]gov -- (blank) -- EMAIL_1874513753_[recipient].zip
- 2017-04-20 13:51 UTC -- 122.191.90[.]62 -- balaji@mcs.anl[.]gov -- (blank) -- EMAIL_1045549183911_[recipient].zip
- 2017-04-20 14:39 UTC -- cpc5-duns7-2-0-cust384.9-3.cable.virginm[.]net -- thiti.b@gmail[.]com -- 30613 [recipient] -- 4766159.zip
TRAFFIC
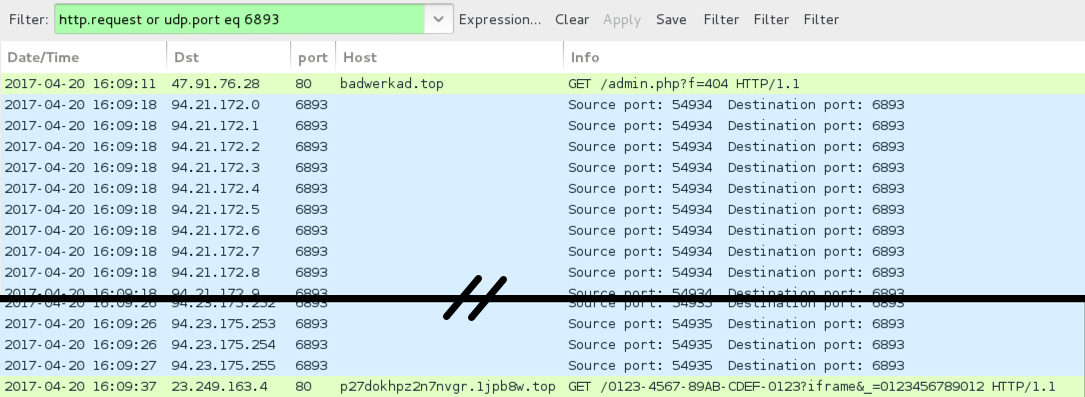
Shown above: Traffic from the infection filtered in Wireshark.
URLS GENERATED BY THE EXTRACTED .JS FILES:
- 47.91.76[.]28 port 80 - badwerkad[.]top - GET/admin.php?f=404
- [Domain did not resolve] - resettinfgd1991[.]pw - GET/search.php
- [Domain did not resolve] - resettinfgd1991[.]club - GET/search.php
CERBER POST-INFECTION TRAFFIC:
- 94.21.172[.]0 - 94.21.172.31 (94.21.172[.]0/27) UDP port 6893
- 94.22.172[.]0 - 94.22.172.31 (94.22.172[.]0/27) UDP port 6893
- 94.23.172[.]0 - 94.23.175.255 (94.23.172[.]0/22) UDP port 6893
- 193.169.135[.]155 port 80 - p27dokhpz2n7nvgr.1jpb8w[.]top
SHA256 HASHES
EMAIL ATTACHMENTS:
- 95a5d63799245f364ffca436db6db1f6ef8b3a737bbe69db0773580b4f62c8e9 - 2552150.zip
- ab77f2127019eb940328598fcdd0610131a1a15ee159a58a6cb4f01ce20359a8 - 4766159.zip
- 984c467750c0bdf6666a19bb58ba977f438abe3f96f2f807c62919ddc05119ea - EMAIL_1874513753_[recipient].zip
- fb190e7e7fa8b1edae1b7aa881b7433fa9a02e0038a9cacc555db6f9c4ee85ad - EMAIL_4546735537_[recipient].zip
- 8ad6aadd2cf5412293df5088d965ee60642cb9e32172874a50021a5969d1fa3c - EMAIL_1045549183911_[recipient].zip
- 8b37015b6b2d0cf72cd6eb4dce34888235e16f3ffc67a5bdca743588936edc23 - EMAIL_954724398860721_[recipient].zip
EXTRACTED .JS FILES:
- 70e6d68813fd3de20c9a606b66af2829d24ae398e16d22a70e7d4dc28ee12f35 - 2856.js
- ed3d344d3b3977c53607d8168acd020e33749e0f34e7e27424a5a6a5814f5bb3 - 7755.js
- 5d02f1a90802b1e04fe2aca7806903aa98b575380a225b5cf5e3f7dea14bd772 - 18092.js
- b7c277ed5b60020818f657ca4319b807086550bf1d160b552caaac379347deee - 25891.js
- a6a0c883159cd43852ac041f43f8b0629a3afce930c986f25d821b370be3bd06 - 31369.js
- 911a21e84ba7fb5f1d579caa5a1e0dc54032b80020fda344cf7ea77df7c9d41c - 31380.js
CERBER RANSOMWARE:
- SHA256 hash: 44674a537e498f64aeb16b5d304da93f0d91fcce644b7917a0f8fd4302f4a4b0
File description: Cerber ransomware downloaded from badwerkad[.]top on 2017-04-20
IMAGES
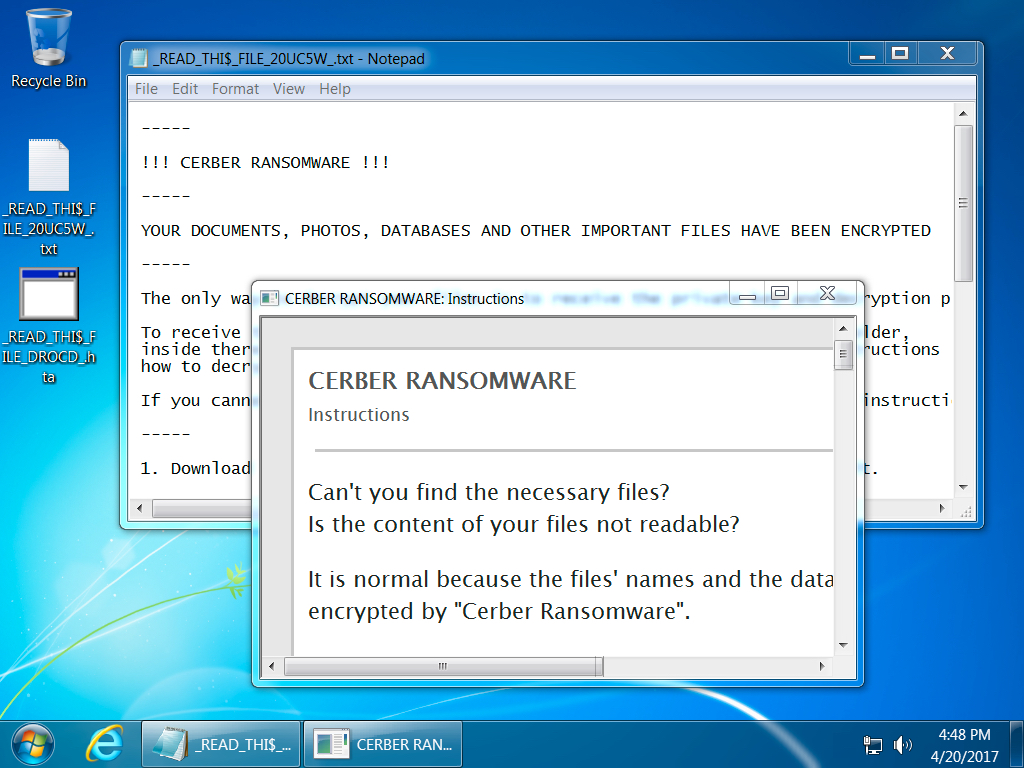
Shown above: Desktop of an infected Windows host.
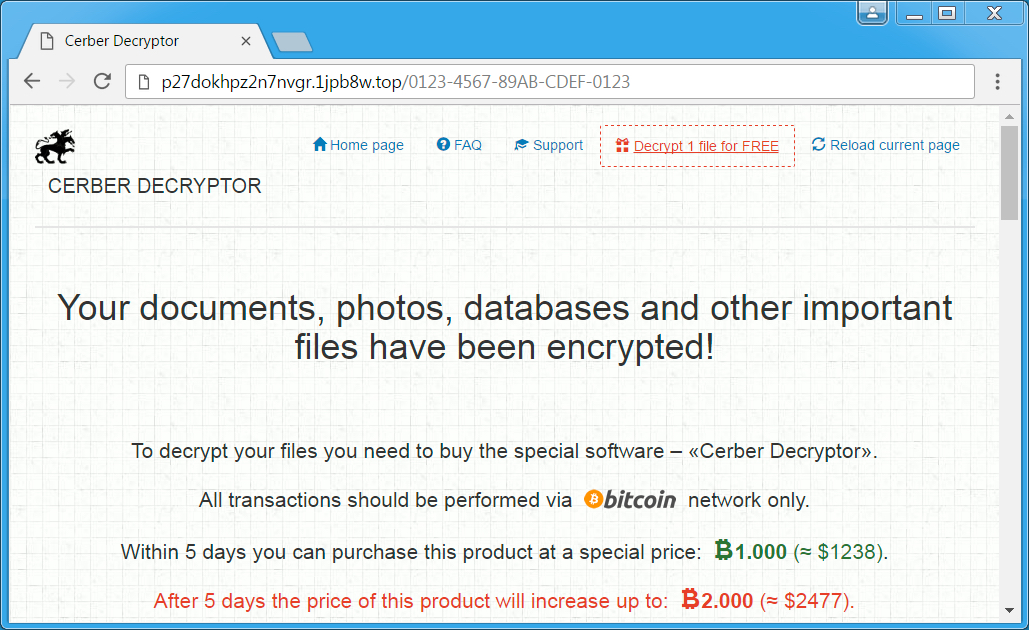
Shown above: The ransom price when I checked was 1 Bitcoin.
Click here to return to the main page.
