2017-04-21 - ZEUS PANDA BANKER, KOVTER AND SMOKE LOADER FROM FAKE PARKING SERVICE WEBSITE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-21-malware-download-from-fake-Parking-Service-website-2-pcaps.zip 1.7 MB (1,673,601 bytes)
- 2017-04-21-Parking-Service-themed-malspam-tracker.csv.zip 0.9 kB (913 bytes)
- 2017-04-21-Parking-Service-themed-emails-and-associated-malware.zip 1.3 MB (1,274,686 bytes)
NOTES:
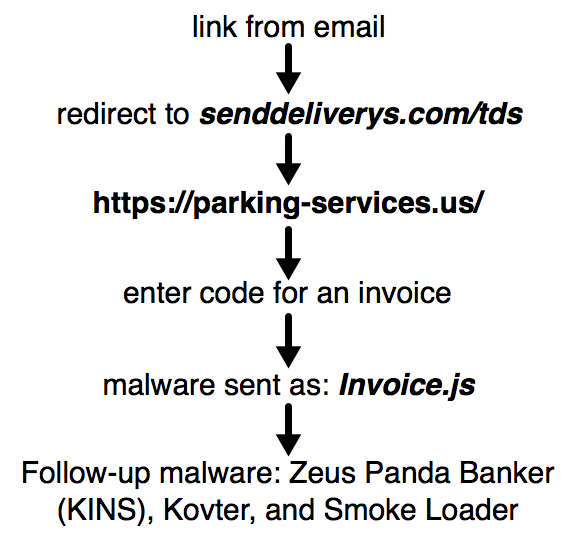
- On 2017-04-21, malware distributed through USPS-themed malspam that I've been tracking changed from USPS to Parking Service-themed malspam.
- Today, this campaign pushed Zeus Panda Banker (KINS), Kovter and Smoke Loader.
IMAGES
EMAILS
DATE/TIME: Friday 2017-04-21 as early as 14:49 UTC through at least 17:55 UTC
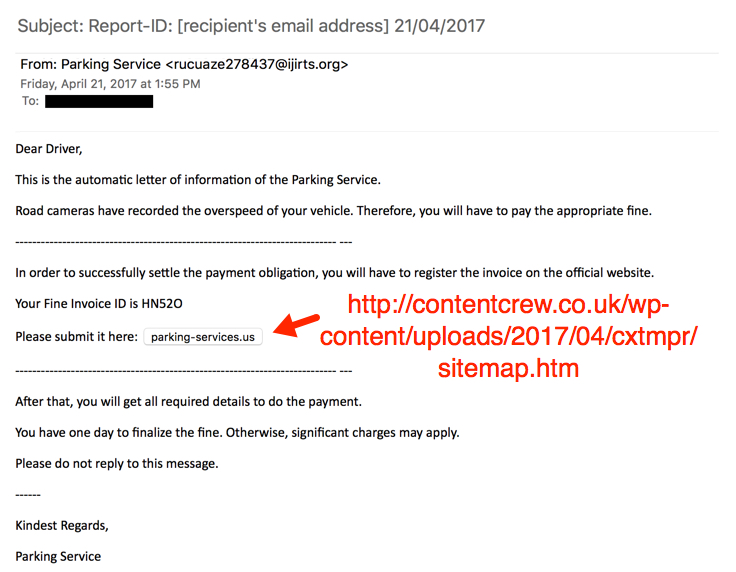
SUBJECT: Report-ID: [recipient's email address] 21/04/2017
SENDING EMAIL EXAMPLES (ALL SPOOFED):
- "Parking Service" <iwudumsf850@olgroupltd[.]com>
- "Parking Service" <luboqyje50@rhoentaxi[.]de>
- "Parking Service" <mykijep06577@rotarysamui[.]org>
- "Parking Service" <rucuaze278437@ijirts[.]org>
- "Parking Service" <rwuyhe03505@sakshichemsciences[.]com>
- "Parking Service" <suhyxud40532787@nexusbrandconsulting[.]co[.]za>
- "Parking Service" <sype02065717@counterdepthrefrigerators[.]us>
- "Parking Service" <w133444@chimneyhill[.]com>
- "Parking Service" <xdyn573536@theelitemarketingalliance[.]com>
- "Parking Service" <yzuuyif7050056@emckliniek[.]nl>
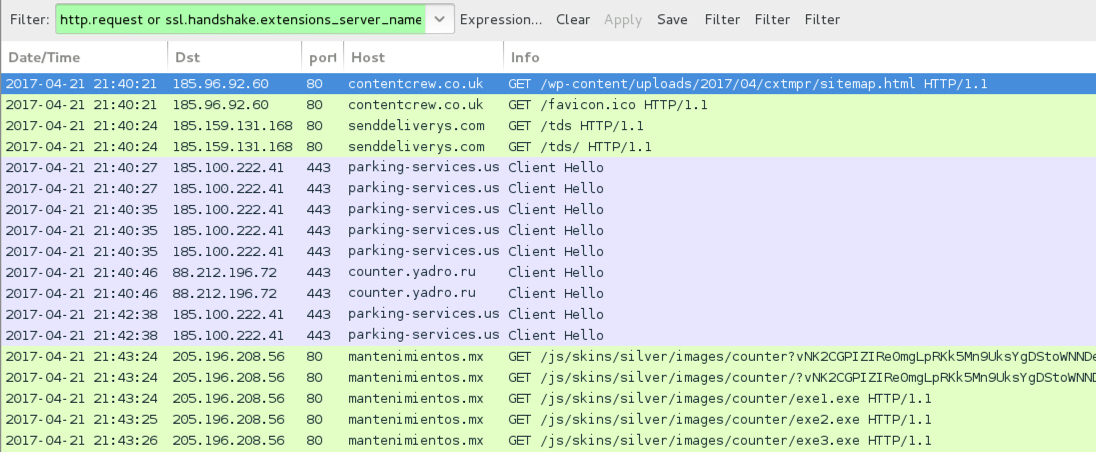
TRAFFIC
EXAMPLES OF LINKS FROM THE EMAILS:
- contentcrew[.]co[.]uk - GET /wp-content/uploads/2017/04/cxtmpr/sitemap.html
- gfkam[.]ru - GET /media/editors/tinymce/plugins/template/sitemap.html
- gigpig[.]co[.]uk - GET /wsssepc/sitemap.html
- katydrake[.]co[.]uk - GET /tmknm/sitemap.html
- komfortservices[.]co[.]uk - GET /rhvlqxfmd/sitemap.html
- midlandaerospace[.]com - GET /jsfm/sitemap.html
REDIRECT FROM THE EMAIL LINKS:
- senddeliverys[.]com - GET /tds
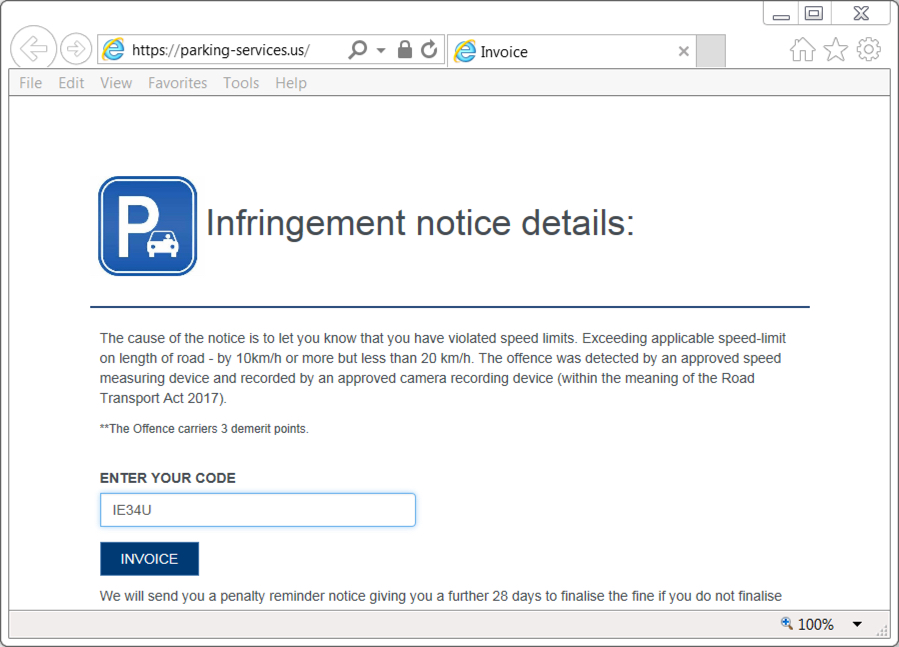
FAKE PARKING SERVICES SITE:
- parking-services[.]us (HTTPS)
PARTIAL URLS FROM THE EXTRACTED .JS FILES FOR FOLLOWUP MALWARE:
- antenimientos[.]mx - GET /js/skins/silver/images/counter
- cangas[.]ro - GET /old/libraries/cms/version/counter
- js-electronics[.]be - GET /administrator/components/com_installer/models/counter
- mantenimientos[.]mx - GET /js/skins/silver/images/counter
- petitions[.]ie - GET /FULL_ROOT_FILES_30Nov16/media/com_petitions_sign/js/counter
- spiritlifestyle[.]org - GET /.well-known/acme-challenge/counter/counter/counter
FILE HASHES
FAKE INVOICES:
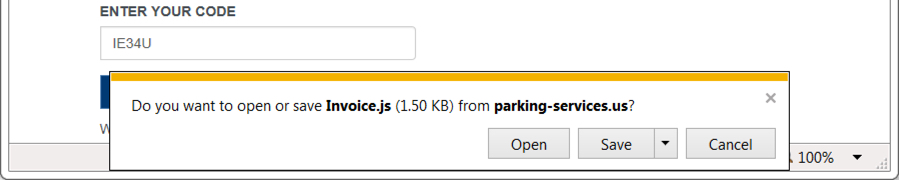
SHA256 hash: 20e6c812f7d8688c9ccb24cc4e9c0fa2b71f1770f38b5571a60043043d4b4ac5
File name: Invoice.js (1st run)
SHA256 hash: 6ad0e26e0423838df19f00e178e47a1b65395b2b68055ecb07a99613208cc684
File name: Invoice.js (2nd run)
FOLLOW-UP MALWARE:
SHA256 hash: 545e3817ddeafd7b8406c1de57d6ea794629bf615f22c0ed18bf88c16e2d292d
File name: exe1.exe (1st run)
File description: Zeus Panda Banker (KINS)
SHA256 hash: 03974017388c6085175f111ee26c3833448b0551acf11063a13a916a75844321
File name: exe2.exe (1st run)
File description: Kovter
SHA256 hash: 1a7fbc76c3881cd9dcf292db25790a9aba6bf677308f9ea1b8f252657bc9c16c
File name: exe3.exe (1st run)
File description: Smoke Loader
SHA256 hash: a4916151059e5f4065f1fb230f06205d1c9cddc5c779984b108e77a22e7c32e9
File name: exe1.exe (2nd run)
File description: Zeus Panda Banker (KINS)
SHA256 hash: b1da6f66bf8049e58f17862ea5ca30bf27054ebb132e6360a68083bab640b70f
File name: exe2.exe (2nd run)
File description: Kovter
SHA256 hash: 08c462be614f6ac81cf78a59f254737beabb5c2abddc5b4bf6436e7d105c204a
File name: exe3.exe (2nd run)
File description: Smoke Loader
Click here to return to the main page.
