2017-04-24 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-24-Hancitor-infection-with-ZLoader.pcap.zip 12.6 MB (12,582,831 bytes)
- 2017-04-24-Hancitor-infection-with-ZLoader.pcap (13,312,274 bytes)
- Z2017-04-24-Hancitor-malspam-4-examples.zip 5.3 kB (5,314 bytes)
- 2017-04-24-Hancitor-malspam-155034-UTC.eml (2,403 bytes)
- 2017-04-24-Hancitor-malspam-161335-UTC.eml (2,408 bytes)
- 2017-04-24-Hancitor-malspam-161400-UTC.eml (2,405 bytes)
- 2017-04-24-Hancitor-malspam-161408-UTC.eml (2,404 bytes)
- Z2017-04-24-malware-from-Hancitor-infections.zip 208.2 kB (208,217 bytes)
- 123.xls (15,766 bytes)
- BNC476.tmp (169,984 bytes)
- TestWordDoc.doc (19,456 bytes)
- invoice_wartell.zueber.doc (6,059 bytes)
- putty.exe (150,016 bytes)
NOTES:
- Sometime last week, links from Hancitor malspam started pointing to RTF documents with a .doc extension that utilize an exploit for CVE-2017-0199.
- If a Windows host is still vulnerable, users only need to open the document in an outdated version of Microsoft office to get infected (no macros involved).
- Mandiant has a nice write-up here about how it works.
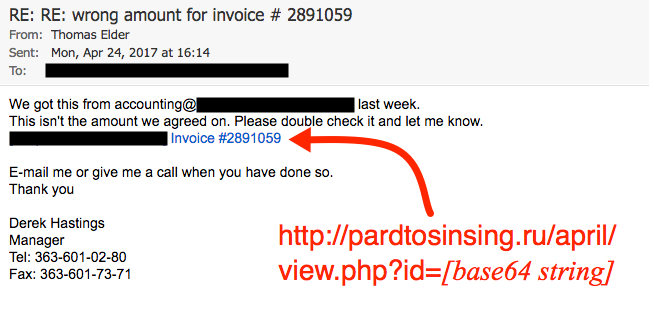
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date/Time: Monday 2017-04-24 as early as 15:50 UTC
- From: (spoofed) "Dalton Peters" <sayaka_iwato@ibiden[.]com>
- From: (spoofed) "Lara Whitt" <sayaka_iwato@ibiden[.]com>
- From: (spoofed) "Rosalinda Fountain" <sayaka_iwato@ibiden[.]com>
- From: (spoofed) "Thomas Elder" <sayaka_iwato@ibiden[.]com>
- Subject: RE: RE: wrong amount for invoice # 2154712
- Subject: RE: RE: wrong amount for invoice # 2891059
- Subject: RE: RE: wrong amount for invoice # 7219828
- Subject: RE: RE: wrong amount for invoice # 8296239
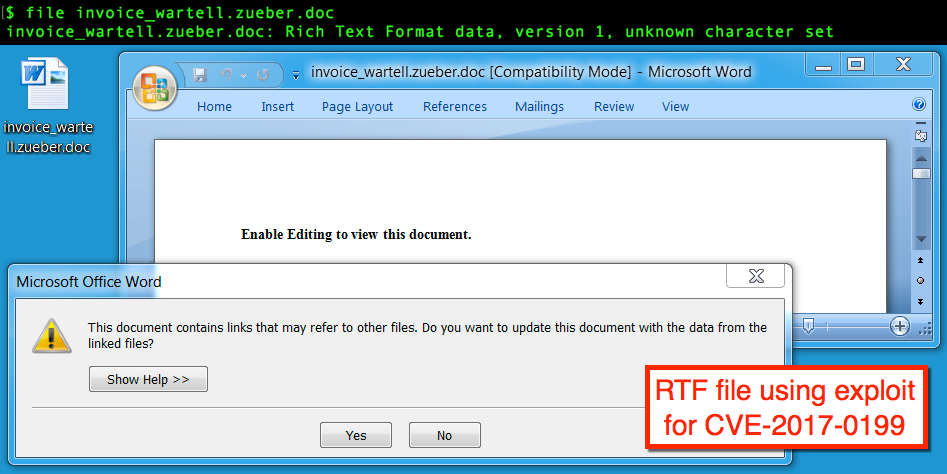
Shown above: Malicious RTF document from link in the malspam.
TRAFFIC
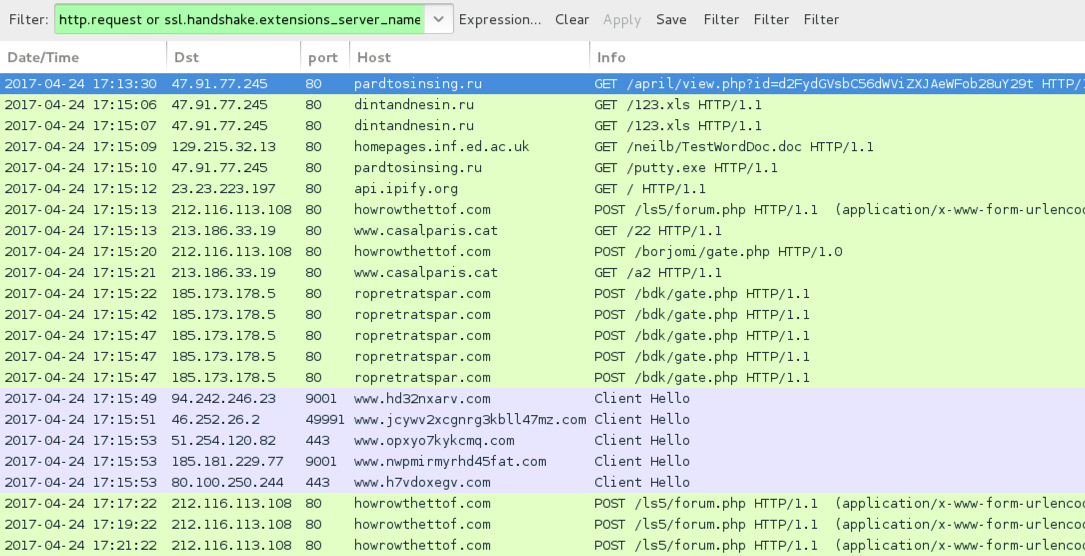
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUEST FOR THE RTF DOCUMENT:
- 47.91.77[.]245 port 80 - dintandnesin[.]ru - GET /april/view.php?id=[base64 string]
- 47.91.77[.]245 port 80 - pardtosinsing[.]ru - GET /april/view.php?id=[base64 string]
POST-INFECTION TRAFFIC:
- 47.91.77[.]245 port 80 - pardtosinsing[.]ru - GET /putty.exe
- 47.91.77[.]245 port 80 - dintandnesin[.]ru - GET /123.xls
- 129.215.32[.]13 port 80 - homepages.inf.ed[.]ac[.]uk - GET /neilb/TestWordDoc.doc
- 212.116.113[.]108 port 80 - howrowthettof[.]com - POST /ls5/forum.php
- 212.116.113[.]108 port 80 - howrowthettof[.]com - POST /borjomi/gate.php
- 213.186.33[.]19 port 80 - www.casalparis[.]cat - GET /22
- 213.186.33[.]19 port 80 - www.casalparis[.]cat - GET /a2
- 185.173.178[.]5 port 80 - ropretratspar[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
RTF DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 2644d5522d7f5f652f7df68f216269a98e0c8039ca63ed0796e921123846a3fe
File location: invoice_wartell.zueber.doc
File description: Malicious RTF document designed to exploit vulnerability for CVE-2017-0199
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: 7dcbb4e490ee52c01e7838288c799981eaab47131b9f3dc21d349b8eac7545d4
File location: C:\Users\[username]\AppData\Roaming\25667.exe
File description: Hancitor binary (downloaded at putty.exe)
- SHA256 hash: efdb74e025abe504eb160e7ff359da8582a9ee6b376ce402c5be7287b8d2293c
File location: C:\Users\[username]\AppData\Local\Temp\BNC476.tmp
File description: DELoader/ZLoader
Click here to return to the main page.
