2017-04-26 - MOLE RANSOMWARE AND KOVTER INFECTIONS FROM EMAILS IMPERSONATING USPS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-26-Mole-ransomware-and-Kovter-infections-3-pcaps.zip 922.5 kB (922,459 bytes)
- 2017-04-26-USPS-themed-malspam-tracker.csv.zip 3.3 kB (3,344 bytes)
- 2017-04-26-USPS-themed-emails-and-associated-malware.zip 1.2 MB (1,206,318 bytes)
BACKGROUND ON THIS CAMPAIGN:
- My in-depth write-up on this campaign is at: Mole Ransomware: How One Malicious Spam Campaign Quickly Increased Complexity and Changed Tactics
- 2017-04-11 - Internet Storm Center (ISC) InfoSec Forums: Malspam on 2017-04-11 pushes yet another ransomware variant
- 2017-04-12 - BleepingComputer: Mole Ransomware Distributed Through Fake online Word Docs
NOTES FOR TODAY:
- The last time I looked into this, it was "Parking Service" malspam.
- Today, we're back to USPS-themed malspam linking to fake Word Online sites for zipped .js files disguised as Office plugins.
- Each downloaded zip archive is a different file name and a different file hash (same with the extracted .js files).
- I only saw Mole ransomware (exe1.exe) and Kovter (exe2.exe) as the follow-up malware today.
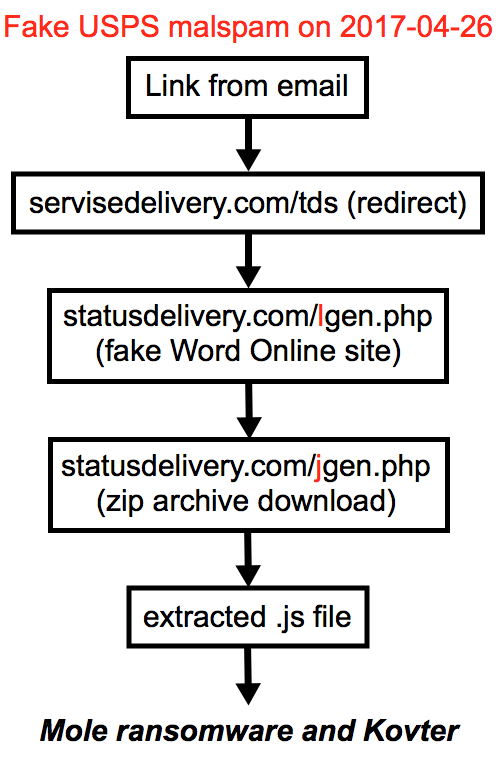
Shown above: Flowchart for this infection traffic.
EMAILS
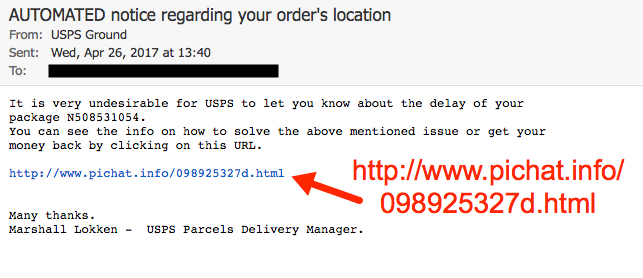
Shown above: Screenshot of one of the emails seen today.
DATES/TIMES:
- Wednesday 2017-04-26 as early as 12:28 UTC through at least 21:54 UTC
EXAMPLES OF SENDING ADDRESSES (ALL SPOOFED):
- "USPS Express Delivery" <henohe32@caverntours[.]com>
- "USPS Express Delivery" <kafweh515171@audioactivesound[.]com>
- "USPS Express Delivery" <lai82@impresos-gdl[.]com>
- "USPS Express Delivery" <sesaifud45660083@tangentindia[.]com>
- "USPS Express Delivery" <viyhye183@kcn[.]jp>
- "USPS Express Delivery" <vyjaqpu3707847@winebox[.]com>
- "USPS Express Delivery" <xokfiuf15355858@bariartesanias[.]com[.]ar>
- "USPS Ground Support" <ginutro7@pan-americana[.]com>
- "USPS Ground Support" <heuyj77035@annebonthuis[.]nl>
- "USPS Ground Support" <ppus053130@asante[.]org>
- "USPS Ground Support" <yreiwvgo05@lancasterchambersc[.]com>
- "USPS Ground" <bftany5074720@nationalpeening[.]com>
- "USPS Ground" <pyuijuwx03637@vividdragon[.]com>
- "USPS Ground" <rae86462653@roviba[.]com>
- "USPS Ground" <uhonatom64@hkduroparts[.]com>
- "USPS Ground" <wpyvehel0435183@martyfriedel[.]com>
- "USPS Ground" <wysk7615566@ccwest[.]com>
- "USPS Home Delivery" <ztqwyhov8670001@themcsgroup[.]com>
- "USPS International" <einw2840584@coreheatingandplumbing[.]co[.]uk>
- "USPS International" <obziuda01010226@emailsend[.]com[.]au>
- "USPS International" <unyyy47534@wmusic[.]com[.]cn>
- "USPS Parcels Delivery" <gragro6666344@taxatienieuws[.]nl>
- "USPS Parcels Delivery" <qis32113374@austindevelopments[.]com[.]au>
- "USPS Parcels Delivery" <xnzckreg26778165@nebo[.]edu>
- "USPS Priority Delivery" <aj0@arvakinsurancegroup[.]com>
- "USPS Priority Delivery" <ebipc68814@sodahub[.]in>
- "USPS Priority Parcels" <ihpuod25880856@fengshui-gateway[.]com>
- "USPS Priority Parcels" <oofaoirx24660673@oakleafproperties[.]com>
- "USPS Priority Parcels" <zgqyzip46533540@auth0rity[.]com>
- "USPS Priority" <gmtimgok26405527@cei[.]org>
- "USPS Priority" <gukoldv52771@marlinchemical[.]net>
- "USPS Priority" <maknoat50@villageacupunctureandmassage[.]com>
- "USPS Priority" <tea01227@dutchmanwoodworks[.]com>
- "USPS SameDay" <igaraki785@cpd.ci.concord[.]ca[.]us>
- "USPS SameDay" <oejjouut6583@russquackenbush[.]com>
- "USPS Station Management" <iujhahzd87632020@seafaring[.]ru>
- "USPS Station Management" <pujoqeys4@leydinfreyer[.]com[.]au>
- "USPS Support Management" <rnfynmrk1068052@blumentur[.]com[.]br>
- "USPS Support Management" <yhu024517@ssheladia[.]com>
- "USPS Support" <bigafith33784567@yeweyih[.]com[.]tw>
- "USPS Support" <lyxrinyt06306284@energy-store[.]it>
- "USPS Support" <p1470@exidasp[.]ca>
- "USPS Support" <ybuozwga0047@acme-atlanta[.]com>
- "USPS TechConnect" <eeupuaj58468604@stjoanhershey[.]org>
- "USPS TechConnect" <iwwj34280@byington[.]net>
- "USPS TechConnect" <ovwooud87864426@grandrapidssolargard[.]com>
EXAMPLES OF SUBJECT LINES:
- ATTENTION REQUIRED: PROBLEMS WITH YOUR ITEM
- AUTOMATED letter: moneyback info
- AUTOMATED notice regarding your order's location
- AUTOMATED notification concerning your shipment's location
- AUTOMATED USPS EMAIL CONCERNING YOUR SHIPMENT
- AUTOMATED USPS OFFICIAL LETTER REGARDING YOUR PARCEL
- AUTOMATIC notification: moneyback info
- AUTOMATIC USPS EMAIL IN REGARDS TO YOUR ORDER
- AUTOMATIC USPS OFFICIAL LETTER IN REGARDS TO YOUR PARCEL
- IMMEDIATE ACTION REQUIRED: your parcel's been postponed
- IMMEDIATE ATTENTION NEEDED: your shipment's been delayed
- IMPORTANT USPS MONEYBACK INFO
- IMPORTANT USPS MONEYBACK INFO CONCERNING YOUR ITEM
- IMPORTANT USPS system letter
- IMPORTANT: notice of delay of your package
- IMPORTANT: notice of delay of your parcel
- Major problems reported to the USPS support team
- Official letter from USPS support team
- Official notice from USPS support team
- Official notification concerning your item
- Official notification in regards to your package
- OFFICIAL USPS customer support letter
- OFFICIAL USPS MONEYBACK INFORMATION
- Official USPS notification in regards to your order
- OFFICIAL USPS REFUND INFORMATION
- PROMPT ACTION REQUIRED: your order's been postponed
- PROMPT ATTENTION NEEDED: your item's been delayed
- PROMPT ATTENTION NEEDED: your shipment's been postponed
- There has been an issue with your order
- There has been an issue with your shipment
- There's been an issue with your package
- URGENT: notification of delay of your order
- URGENT: notification of delay of your package
- USPS customer support letter: your package has been delayed
- USPS customer support team notification: your parcel has been postponed
- USPS official notice: big trouble with your order
- USPS official notification: serious problems with your shipment
- USPS OFFICIAL STATEMENT regarding your item
- USPS support notice: your shipment has been delayed
- USPS support statement: your shipment has been delayed
- USPS USER IMPORANT NEW INFORMATION IN REGARDS TO YOUR SHIPMENT
- WARNING: INFO ON A IMPENDING REFUND
- WARNING: you are legally obliged to review the status of your item
- WARNING: you are required to check the status of your shipment
TRAFFIC
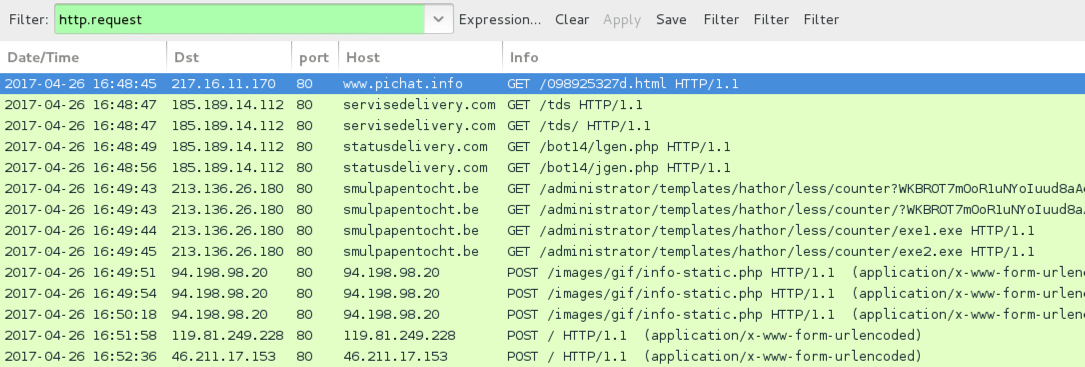
Shown above: Traffic from an infection filtered in Wireshark.
LINKS FROM THE EMAILS:
- www.apui95[.]org - GET /download/lsf/53904208ab.html
- www.arcoglass[.]net - GET /3f60caba08.html
- www.ashnoortex.quantapress[.]com - GET /55351bbf17.html
- www.autumnmoon[.]ca - GET /wp-content/423fd4e375.html
- www.avukatiarama[.]com - GET /wp-content/uploads/2017/04/2f8d830cb0.html
- www.bgbaligatraveldiary[.]com - GET /wp-content/uploads/1f91a1c9ee.html
- www.bondhucomputers[.]com - GET /wp-content/uploads/9b759cb904.html
- www.cisportstherapy[.]com - GET /wp-content/53904208ab.html
- www.crmgestao[.]com[.]br - GET /wp-content/themes/converio/02186564fe.html
- www.develop[.]com[.]vc - GET /wp-content/themes/develop/fa7651d6c6.html
- www.fancytiehtx[.]com - GET /wp-content/plugins/wraper/91039cc1b6.html
- www.felixsolis[.]mobi - GET /2a48c06f46.html
- www.focalpointbdg[.]com - GET /wp-content/plugins/278498c41a.html
- www.forkliftlastik[.]org - GET /wp-content/themes/minimize/9b759cb904.html
- www.gonzalez-santiago[.]com - GET /photog/05bd94a5e0.html
- www.imtsus[.]com - GET /wp-content/plugins/wp-blog/2a48c06f46.html
- www.informatica-ag[.]it - GET /wp-content/uploads/58de0d46db.html
- www.kardeslermobilyaizmir[.]com - GET /2a48c06f46.html
- www.laboratorioweb[.]net - GET /wp-content/9b759cb904.html
- www.latifekuskay[.]com - GET /wp-content/plugins/b670991e46.html
- www.nti-rechten[.]nl - GET /wp-content/uploads/2017/04/c75ab8fb60.html
- www.pankajevents[.]com - GET /wp-content/plugins/wraper/3f60caba08.html
- www.pichat[.]info - GET /098925327d.html
- www.sailingmonea[.]com - GET /wp-content/uploads/62fd619f6e.html
- www.shenzhen-mro[.]com - GET /modules/mod_ariimageslidersa/c5f6be8373.html
- www.sotex[.]de - GET /0659cc424a.html
- www.spaziosportsrl[.]com - GET /wp-content/themes/sketch/2f8d830cb0.html
- www.teapotcollector[.]org - GET /wp-content/plugins/wraper/a4b3cada4b.html
- www.trikolkysmile[.]cz - GET /css/67ed877d86.html
- www.uiccoin[.]org - GET /9c1dfb513b.html
REDIRECT:
- 185.189.14[.]112 port 80 - servisedelivery[.]com - GET /tds
- 185.189.14[.]112 port 80 - servisedelivery[.]com - GET /tds/
FAKE WORD ONLINE SITE:
- 185.189.14[.]112 port 80 - statusdelivery[.]com - GET /bot14/lgen.php
- 185.189.14[.]112 port 80 - statusdelivery[.]com - GET /bot14/jgen.php
PARTIALS URLS FROM THE .JS FILES FOR ADDITIONAL MALWARE:
- atrium-nieruchomosci[.]pl - GET /js/js/jscalendar-1.0/lang/counter
- js-electronics[.]be - GET /tmp/yoo_venture_j25/warp/libraries/counter
- lecamorariu[.]ro - GET /counter
- protectie-electromagnetica[.]ro - GET /wp-content/themes/twentythirteen/languages/counter
- smulpapentocht[.]be - GET /administrator/templates/hathor/less/counter
MOLE RANSOMWARE POST-INFECTION TRAFFIC:
- 94.198.98[.]20 port 80 - 94.198.98[.]20 - GET /images/gif/info-static.php
EMAIL ADDRESSES FROM THE MOLE RANSOMWARE DECRYPTION INSTRUCTIONS:
- A�u�g�u�s�t�S�t�e�e�n�@�w�r�i�t�e�m�e�[.]�c�o�m�
- �a�u�g�u�s�t�s�t�e�e�n�@�i�n�d�i�a�[.]�c�o�m�
SOME OF THE KOVTER POST-INFECTION TRAFFIC:
- 46.211.17[.]153 port 80 - 46.211.17[.]153 - POST /
- 119.81.249[.]228 port 80 - 119.81.249[.]228 - POST /
- 185.199.177[.]90 port 80 - 185.199.177[.]90 - POST /
- 23.73.153[.]97 port 443 - HTTPS (TLSv1.2) traffic
- various IP addresses over port 443 and 8080 - Attempted TCP connections
MALWARE
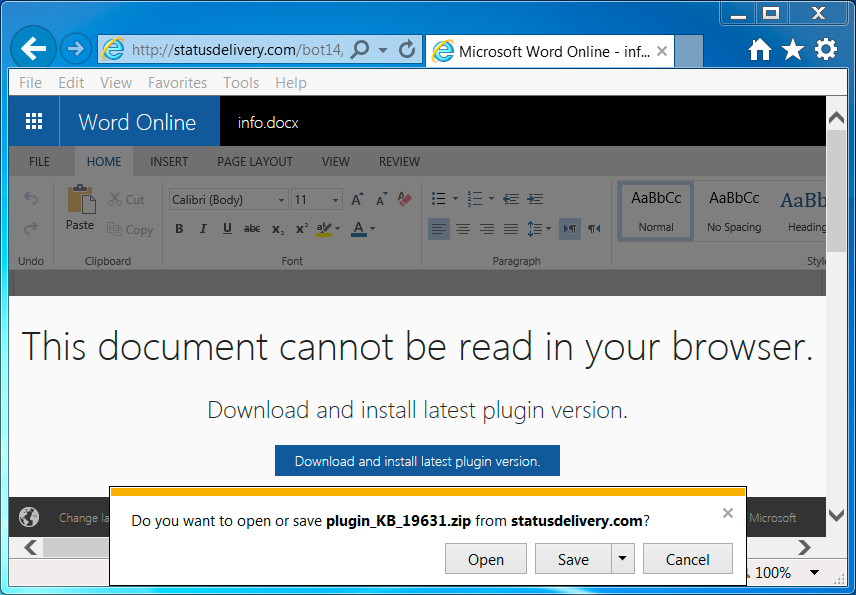
Shown above: Zip archive disguised as an Office plugin downloaded from today's fake Word Online page.
Shown above: Each downloaded zip archive contains a .js file.
SAMPLES OF ZIP ARCHIVES DOWNLOADED FROM THE FAKE WORD ONLINE SITE:
- 31e56d6c14ce7c080b892d121268f30f5c37501773c82ec21fd25963b98d8238 - plugin_KB_47092.zip
- 5278a3a1ce4f2ffb6edf5cc6a1cb6b56477f8e87d7e151998b45b1d6ff685a19 - plugin_KB_57676.zip
- e0818a03a897f47113970e21b575f9725eac608b1dc4eda4f3470ea3d25f8199 - plugin_KB_66614.zip
- d405a7811ce8341c258fabf05da6d88a9b204b9b9c47bedbefe40a318d0f5d8e - plugin_KB_72013.zip
- f69b69ac673ffee8473950360e8296d855cb75f6d6ab00cde5d0c4c58c6b7c8c - plugin_KB_81638.zip
- 49b9050e71aa65568e99125bc40abd5984382db5d39dcd55a2409664ca948999 - plugin_KB_89567.zip
- 1e5aac17ab222e7351b08fd95503839414e75f80ea318212950f81a8c826cba8 - plugin_KB_92384.zip
.JS FILES EXTRACTED FROM THE ABOVE ZIP ARCHIVES:
- 0f6ec40363f669ff8c2a040cea7519f3d2ec44d30549ae8824e84781173dca25 - plugin_KB_47092.js
- 5d94ed7fc42411bc5f807ec869800533ad718bafb93c5942cbf7766dacf8a29e - plugin_KB_57676.js
- 7ee8913af927d70ef84e1ffb8a132cf554e04a388900ba733f651eb685bf8a17 - plugin_KB_66614.js
- 8dce263108614871fd3f6a799279c1da7e7d26ef1544183976dd692b86da5c6c - plugin_KB_72013.js
- 8e61d88a02736abb8e1ba76d80f12ba68bb4e4e914be8c5049b0358e3a31e2e9 - plugin_KB_81638.js
- 14ea062ca146ed50b89faf437bb801367788e95857f73c92c5fbada47525fda4 - plugin_KB_89567.js
- 94aaf6ff9192056b6177531b391ea00a701ee8fbb35ba26946ca8710d1eb9c13 - plugin_KB_92384.js
SAMPLES OF MALWARE DOWNLOADED BY THE .JS FILES:
- 0a3c26a388e6ede8e08a33ddc3c9aece079d5d6c752854e16d216e134ed3d357 - exe1.exe - Mole ransomware
- f9babd5f229b59221245ac36506c4524ff7ee362a8d5c126004ace4035f53918 - exe1.exe - Mole ransomware
- 1ba0eeecd16eb7e3a7753f5fb93e95e13de6fc42de684bb7eaf0b6dfe4d94278 - exe2.exe - Kovter
- acef8f1ccc857e4bb97ae80fcec4b1f50c76c6888a030ece66c9d53ebebbcde7 - exe2.exe - Kovter
- dc46009d1a33ba4ad8272f3e13b226825cdcb70ba4b3d20ae7e054e0a8adbf1d - exe2.exe - Kovter
IMAGES
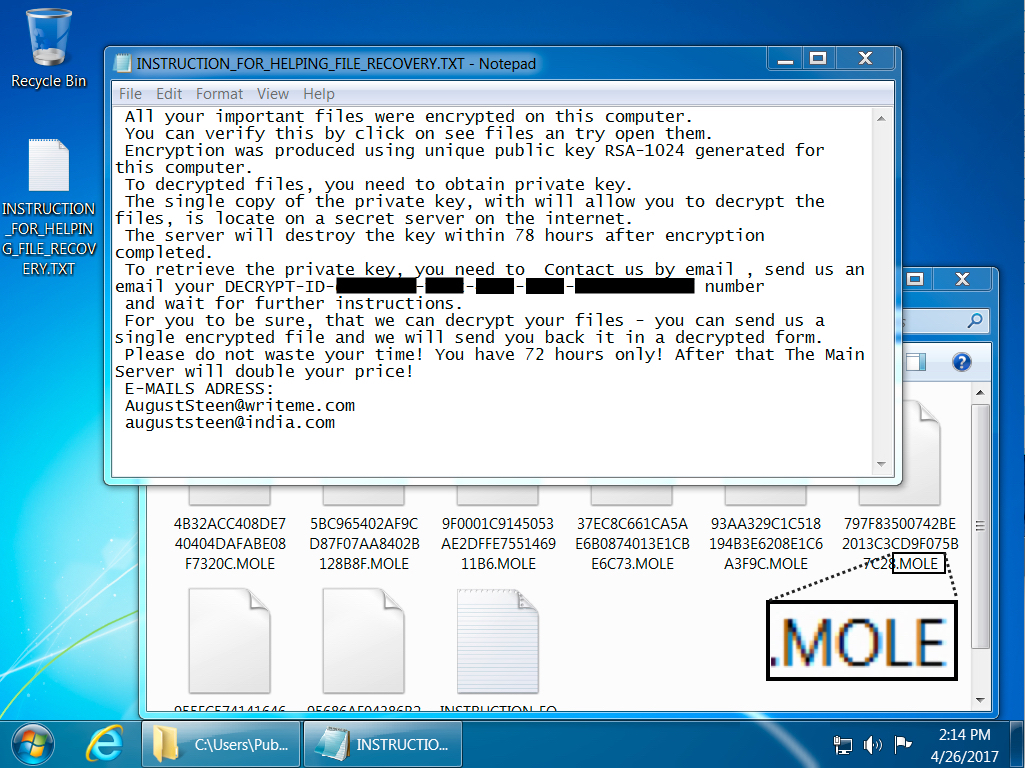
Shown above: Screenshot of an infected Windows desktop.
Click here to return to the main page.
