2017-04-26 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-26-Hancitor-infection-with-ZLoader.pcap.zip 12.9 MB (12,890,646 bytes)
- 2017-04-26-Hancitor-infection-with-ZLoader.pcap (13,425,601 bytes)
- 2017-04-26-Hancitor-malspam-5-examples.zip 5.7 kB (5,700 bytes)
- 2017-04-26-Hancitor-malspam-144836-UTC.eml (1,603 bytes)
- 2017-04-26-Hancitor-malspam-150705-UTC.eml (1,601 bytes)
- 2017-04-26-Hancitor-malspam-155750-UTC.eml (1,626 bytes)
- 2017-04-26-Hancitor-malspam-170648-UTC.eml (1,559 bytes)
- 2017-04-26-Hancitor-malspam-171002-UTC.eml (1,601 bytes)
- 2017-04-26-malware-from-Hancitor-infection.zip 247.6 kB (247,597 bytes)
- ADP_Invoice_gerald.simpson.doc (207,360 bytes)
- BN673A.tmp (158,720 bytes)
NOTES:
- Yesterday, the Hancitor campaign stopped using RTF documents with a .doc extension to exploit CVE-2017-0199.
- Since then, the actors behind this campaign have gone back to using Word documents with malicious macros.
- @James_inthe_box started a Twitter discussion about today's activity here.
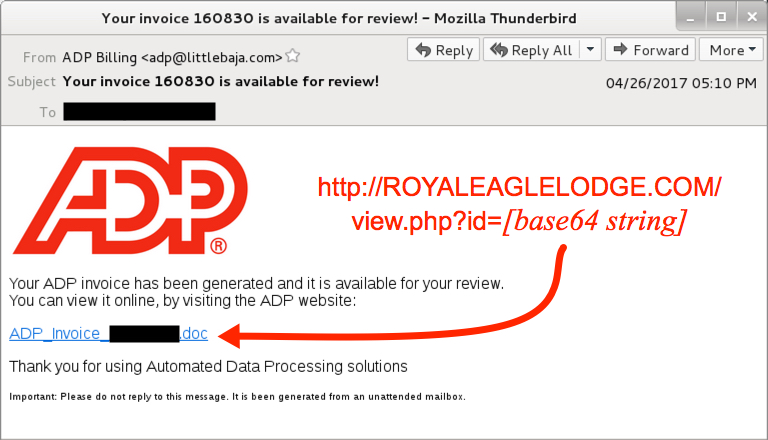
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2017-04-26 as early as 14:48 UTC through at least 17:10 UTC
- From: (spoofed) "ADP Billing" <adp@lamantiaproduce[.]com>
- From: (spoofed) "ADP Billing" <adp@littlebaja[.]com>
- From: (spoofed) "ADP Billing" <adp@orchardridgecc[.]com>
- Subject: Your invoice 160830 is available for review!
- Subject: Your invoice 380131 is available for review!
- Subject: Your invoice 538322 is available for review!
- Subject: Your invoice 581742 is available for review!
- Subject: Your invoice 776534 is available for review!
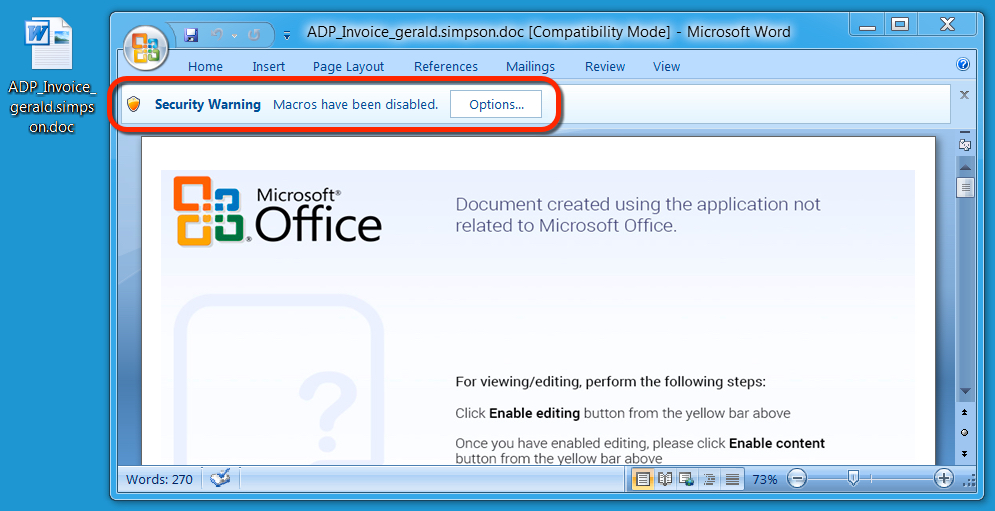
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
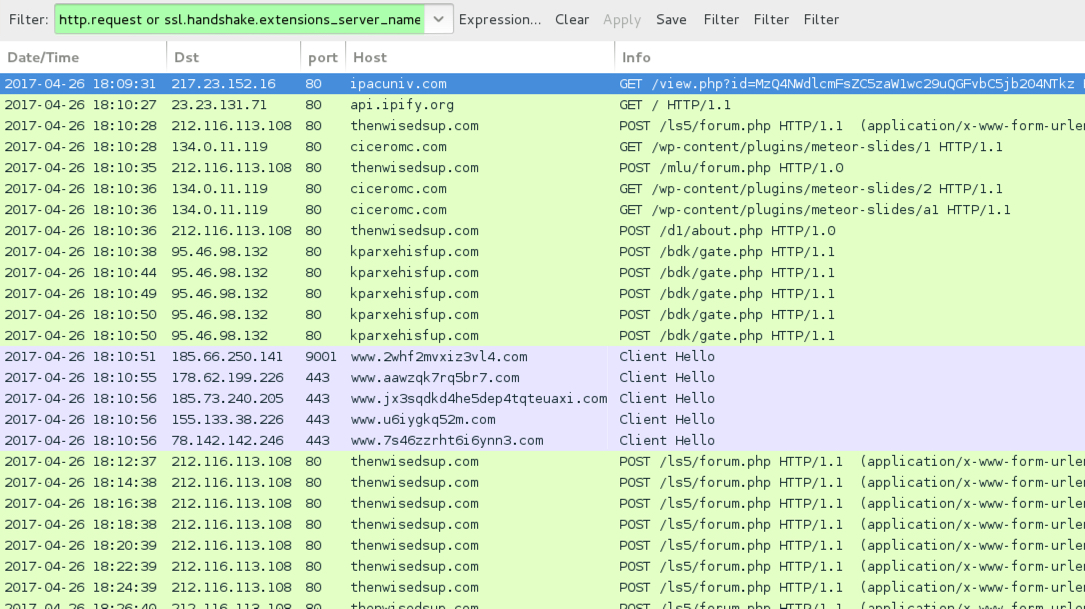
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUEST FOR THE WORD DOCUMENT:
- 217.23.152[.]16 port 80 - IPACUNIV[.]COM - GET /view.php?id=[base64 string]
- 217.23.152[.]16 port 80 - LORIBYDESYGN[.]NET - GET /view.php?id=[base64 string]
- 217.23.152[.]16 port 80 - ROYALEAGLELODGE[.]COM - GET /view.php?id=[base64 string]
- 217.23.152[.]16 port 80 - sparxdynamix[.]co[.]uk - GET /view.php?id=[base64 string]
- 217.23.152[.]16 port 80 - withedtwilrit[.]ru - GET /view.php?id=[base64 string]
POST-INFECTION TRAFFIC:
- 212.116.113[.]108 port 80 - thenwisedsup[.]com - POST /ls5/forum.php
- 212.116.113[.]108 port 80 - thenwisedsup[.]com - POST /mlu/forum.php
- 212.116.113[.]108 port 80 - thenwisedsup[.]com - POST /d1/about.php
- 134.0.11[.]119 port 80 - ciceromc[.]com - GET /wp-content/plugins/meteor-slides/1
- 134.0.11[.]119 port 80 - ciceromc[.]com - GET /wp-content/plugins/meteor-slides/2
- 134.0.11[.]119 port 80 - ciceromc[.]com - GGET /wp-content/plugins/meteor-slides/a1
- 95.46.98[.]132 port 80 - kparxehisfup[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 36daf8bb54231f6777cc81bd223cbc5b55948b9bc69cb8d3999b4931be9a7c61
File name: ADP_Invoice_gerald.simpson.doc
File size: 207,360 bytes
File description: Hancitor maldoc
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: d2bd34c6ffa969c3b347d4b3016b7d0610f65ec3346e4fe442589ebe2c37981d
File location: C:\Users\[username]\AppData\Local\Temp\BN673A.tmp
File size: 158,720 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
