2017-05-01 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-01-Hancitor-infection-with-ZLoader.pcap.zip 392.9 kB (392,908 bytes)
- 2017-05-01-Hancitor-infection-with-ZLoader.pcap (537,762 bytes)
- 2017-05-01-Hancitor-malspam-4-examples.zip 4.0 kB (4,001 bytes)
- 2017-05-01-Hancitor-malspam-1609-UTC.eml (995 bytes)
- 2017-05-01-Hancitor-malspam-1611-UTC.eml (1,072 bytes)
- 2017-05-01-Hancitor-malspam-1654-UTC.eml (1,055 bytes)
- 2017-05-01-Hancitor-malspam-1658-UTC.eml (1,047 bytes)
- 2017-05-01-malware-from-Hancitor-infection.zip 270.7 kB (270,675 bytes)
- BNED2B.tmp (187,904 bytes)
- Ringcentral_Fax_Invoice_willie.dinkman.doc (244,736 bytes)
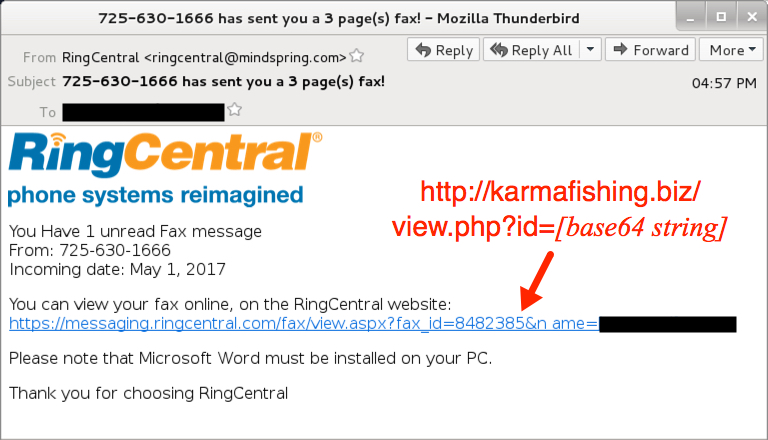
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2017-05-01 as early as 16:09 UTC through at least 16:58 UTC
- From: (spoofed) "RingCentral" <ringcentral@mindspring[.]com>
- Subject: 725-630-1772 has sent you a 3 page(s) fax!
- Subject: 725-630-1666 has sent you a 3 page(s) fax!
- Subject: 725-630-2772 has sent you a 3 page(s) fax!
- Subject: 725-630-5125 has sent you a 3 page(s) fax!
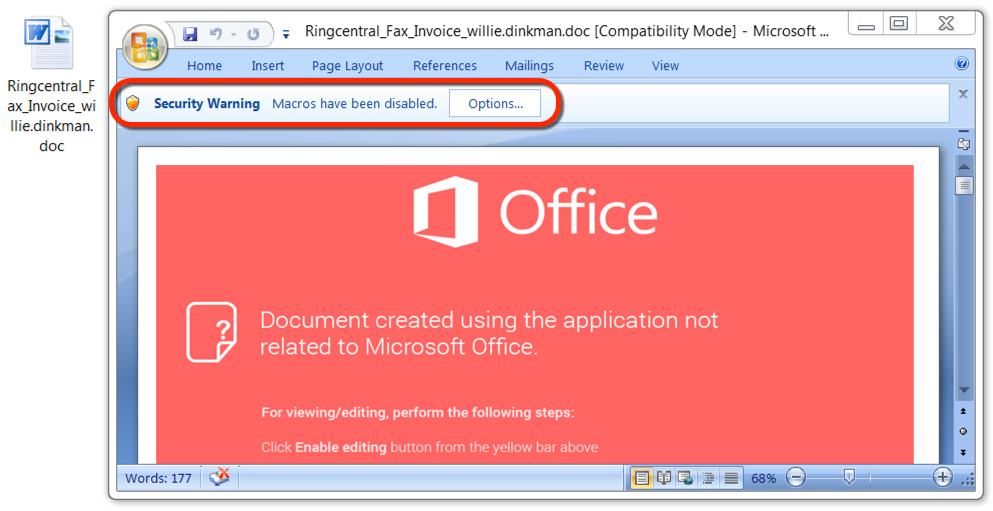
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
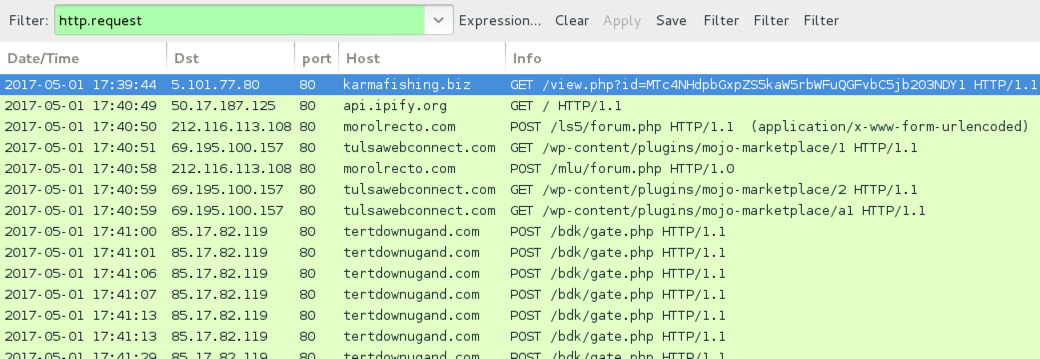
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUEST FOR THE WORD DOCUMENT:
- 5.101.77[.]80 port 80 - dhvoilfieldservices[.]com - GET /view.php?id=[base64 string]
- 5.101.77[.]80 port 80 - karmafishing[.]biz - GET /view.php?id=[base64 string]
POST-INFECTION TRAFFIC:
- 212.116.113[.]108 port 80 - morolrecto[.]com - POST /ls5/forum.php
- 212.116.113[.]108 port 80 - morolrecto[.]com - POST /mlu/forum.php
- 69.195.100[.]157 port 80 - tulsawebconnect[.]com - GET /wp-content/plugins/mojo-marketplace/1
- 69.195.100[.]157 port 80 - tulsawebconnect[.]com - GET /wp-content/plugins/mojo-marketplace/2
- 69.195.100[.]157 port 80 - tulsawebconnect[.]com - GGET /wp-content/plugins/mojo-marketplace/a1
- 85.17.82[.]119 port 80 - tertdownugand[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 6a58cbbd0b5f47bd53c50260fdcd0a0e3b75b5109fa86278d961eb5d4e17fc13
File name: Ringcentral_Fax_Invoice_willie.dinkman.doc
File size: 244,736 bytes
File description: Hancitor maldoc
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: a573430c2c69e9b1d19667062bc75905f5ad5e2b8ee67baa14586b6b1624e319
File location: C:\Users\[username]\AppData\Local\Temp\BNED2B.tmp
File size: 187,904 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
