2017-05-02 - KEEPING IT 100: "BLANK SLATE" CAMPAIGN STARTS PUSHING MORDOR RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-02-Blank-Slate-campaign-9-pcaps.zip 2.1 MB (2,132,187 bytes)
- 2017-05-02-Blank-Slate-malspam-tracker.csv.zip 5.1 kB (5,134 bytes)
- 2017-05-02-Blank-Slate-emails-and-associated-ransomware.zip 3.1 MB (3,117,577 bytes)
BACKGROUND:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
TODAY'S NOTES:
- How am I "Keeing it 100"? Today's post has 100 emails by this campaign from 2017-04-28 through 2017-05-02.
- In the past few hours before I made this blog post, the Blank Slate campaign started pushing Mordor ransomware instead of Cerber ransomware.
- More information on Mordor ransomware can be found here.
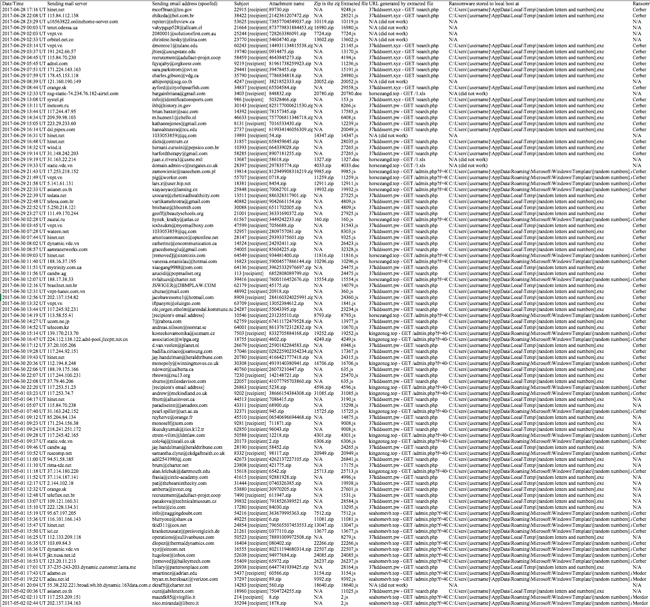
Shown above: Keeping it 100 means too many entries in the spreadsheet for a good screenshot.
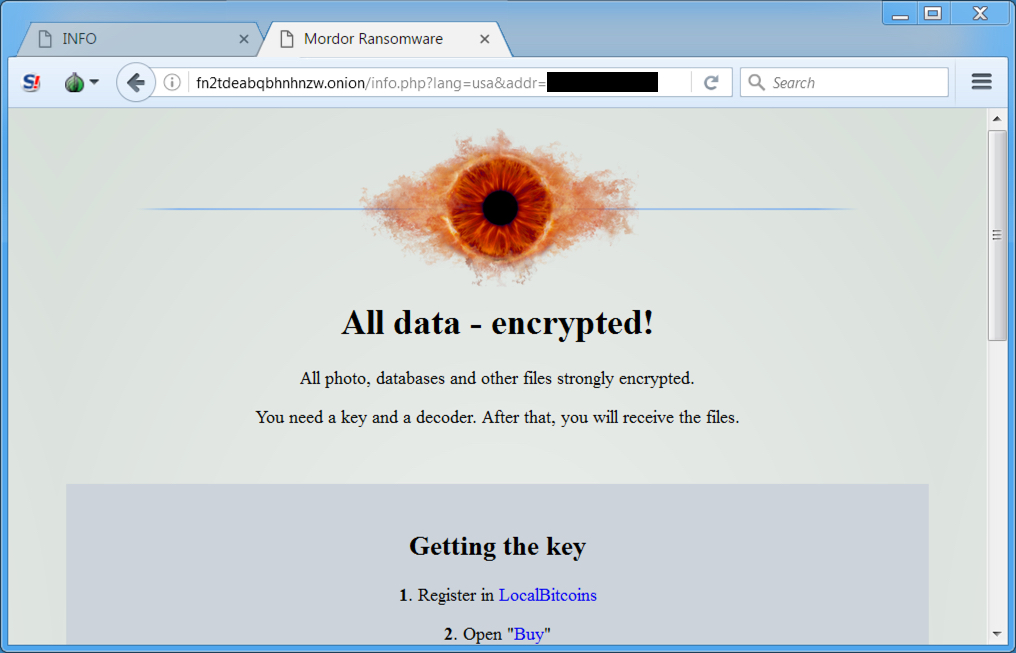
Shown above: Mordor ransomware description instructions (image 1 of 2).
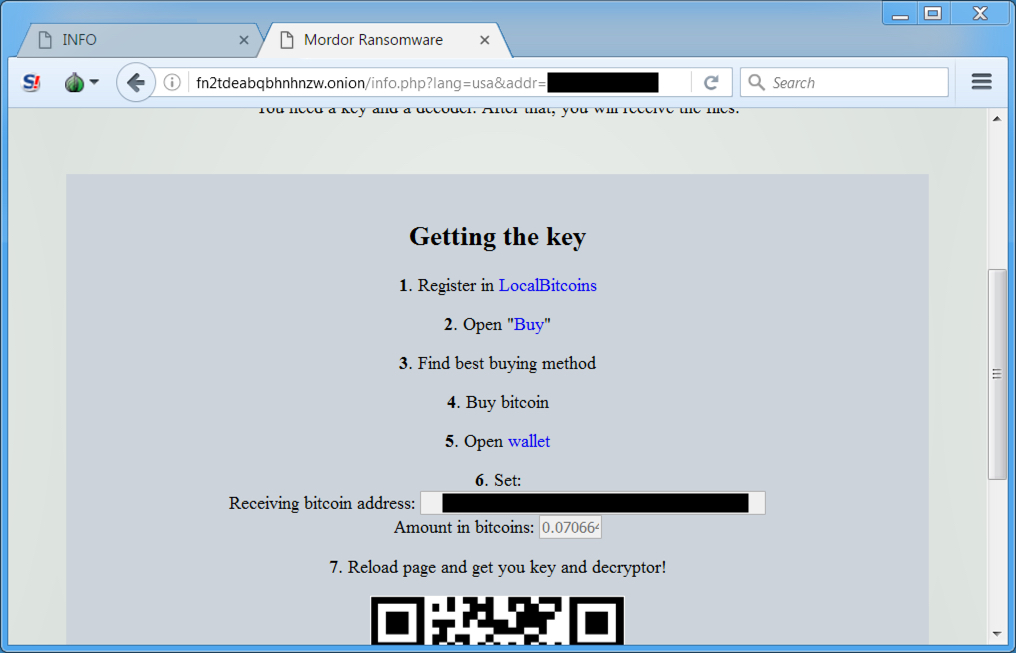
Shown above: Mordor ransomware description instructions (image 2 of 2).
TRAFFIC
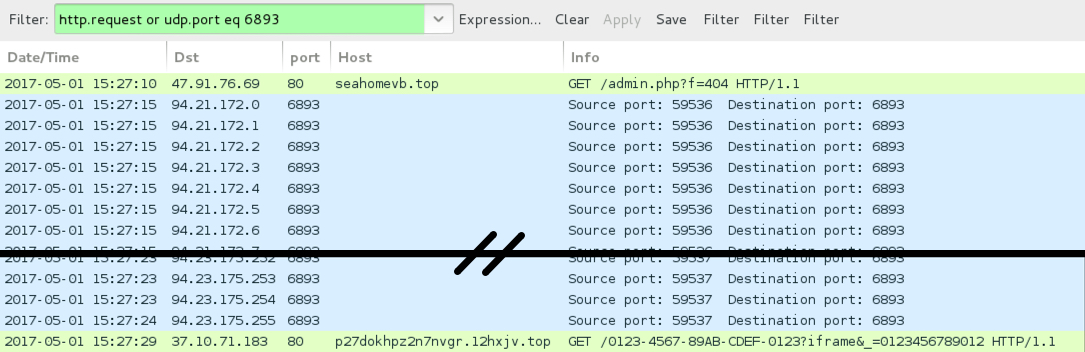
Shown above: Domain from Blank Slate campaign sending Cerber ransomware.
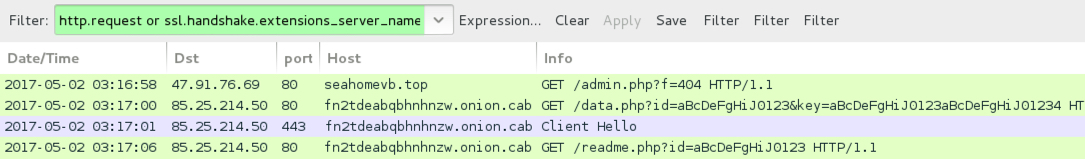
Shown above: Same domain from Blank Slate campaign sending Mordor ransomware a few hours later.
URLS GENERATED BY THE EXTRACTED FILES:
- 51.15.77[.]124 port 80 - 37kddsserrt[.]pw - GET /search.php
- 51.15.77[.]124 port 80 - 37kddsserrt[.]xyz - GET /search.php
- 31.41.44[.]59 port 80 - horsezangd[.]top - GET /1.xls [Word docs trying to exploit CVE-2017-0199]
- 31.41.44[.]59 port 80 - horsezangd[.]top - GET /admin.php?f=404
- 47.91.76[.]69 port 80 - kingzoneg[.]top - GET /admin.php?f=404
- 47.91.76[.]69 port 80 - seahomevb[.]top - GET /admin.php?f=404
CERBER POST-INFECTION TRAFFIC:
- 94.21.172[.]0 - 94.21.172.31 (94.21.172[.]0/27) UDP port 6893
- 94.22.172[.]0 - 94.22.172.31 (94.22.172[.]0/27) UDP port 6893
- 94.23.172[.]0 - 94.23.175.255 (94.23.172[.]0/22) UDP port 6893
- 37.10.71[.]183 port 80 - p27dokhpz2n7nvgr.12hxjv[.]top
MORDOR POST-INFECTION TRAFFIC:
- 85.25.214[.]50 port 80 - fn2tdeabqbhnhnzw[.]onion[.]cab - HTTP traffic
- 85.25.214[.]50 port 443 - fn2tdeabqbhnhnzw[.]onion[.]cab - HTTPS/SSL/TLS traffic
SHA256 HASHES
ATTACHED ZIP ARCHIVES AND EXTRACTED .JS FILES:
- Too many to mention
EXTRACTED RTF FILES DESIGNED TO EXPLOIT CVE-2017-0199:
- 83b435bb1349e8676f671505c4850ef2be1dbc4da27adf246c8452553096a5ea - 1327.doc
- 5be2c27d9ad2bf91b8263273e992744e074fcce7767643bd9bab8c05622583c0 - 20780.doc
- 74616a15e77b58e1dc6fac225865fb0fdd6470e76bbf358260317cba44ee9636 - 4033.doc
RANSOMWARE SAMPLES:
- SHA256 hash: 7f2335466ecca7be6888f92b5ba260780ce0a38039ceb54ac99b0485b3b086de
File description: Cerber ransomware from 37kddsserrt[.]pw and 37kddsserrt.xyz on 2017-04-29
- SHA256 hash: 3c858a40d94d1c9ba1b3d9d637b295eaa48f491dc24eb2e43f964cac518270fb
File description: Cerber ransomware from 37kddsserrt[.]pw and horsezangd[.]top on 2017-04-29
- SHA256 hash: dd24b0eb3b2126683c961731244ccee63e0b25c26186811da33be0d7ff1f98c3
File description: Cerber ransomware from kingzoned[.]top on 2017-04-30
- SHA256 hash: f853d76ad14ffec2779706a9861d79ba37d5ebb7c494b88d735330d571caa54d
File description: Cerber ransomware from kingzoned[.]top and seahomevb[.]top on 2017-05-01
- SHA256 hash: 15d5f8faf33a50a973ec36f70c69459c3bdcac27b929a6a76d5a9dac50e4cc27
File description: Mordor ransomware from seahomevb[.]top on 2017-05-01
- SHA256 hash: 0b58b14a4f500314414bb793aacd00336a454f3543e0c126a86544f823aabbfa
File description: Mordor ransomware from seahomevb[.]top on 2017-05-02
Click here to return to the main page.
