2017-05-04 - DECIMAL IP CAMPAIGN USES FAKE ADOBE FLASH PLAYER SITE TO SEND SMOKE LOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-04-Decimal-IP-campaign-2-pcaps.zip 715.5 kB (715,454 bytes)
- 2017-04-25-Smoke-Loader-post-infection-traffic.pcap (330,328 bytes)
- 2017-05-04-fake-Adobe-Flash-player-site.pcap (1,066,302 bytes)
- 2017-05-04-Decimal-IP-campaign-malware.zip 51.3 kB (51,257 bytes)
- flashplayer24pp_id_install.exe (148,992 bytes)
NOTES:
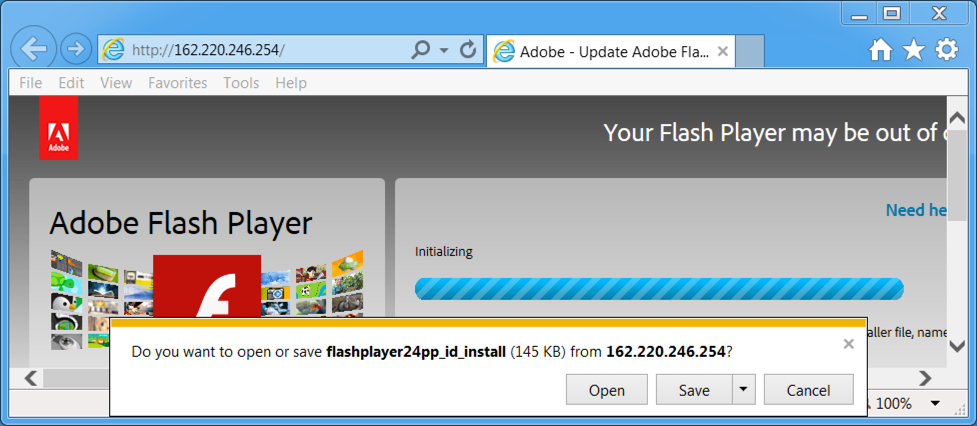
- Saw a fake Adobe Flash site send Smoke Loader (disguised as a Flash Player installer) on 2017-05-04, but the sample had already been submitted to VirusTotal on 2017-04-25.
- URLs associated with the Decimal IP campaign had been leading to Rig EK, but they are now redirecting to a fake Flash Player installer page.
- It seems to be the same Smoke Loader from this campaign today as we saw from Decimal IP Rig EK last week.
Shown above: Using the Decimal IP URL from Zerophage blog post about the Decimal IP campaign.
TRAFFIC
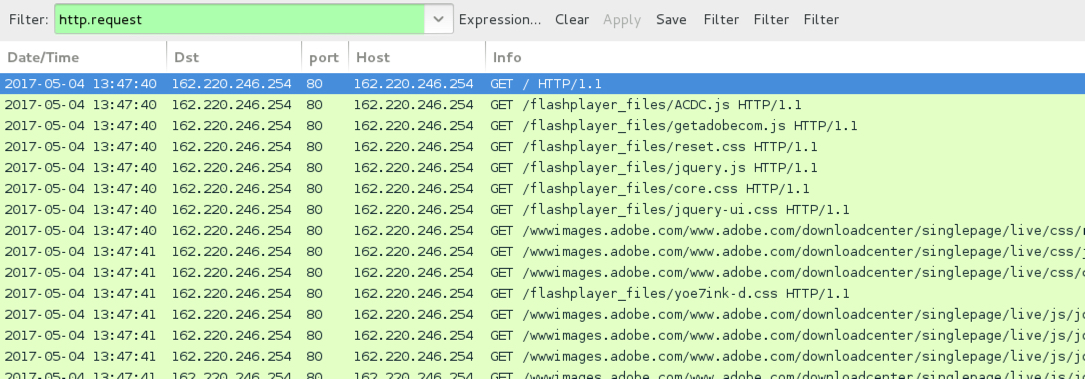
Shown above: Traffic from the fake Flash Player site filtered in Wireshark.
FAKE ADOBE FLASH PLAYER SITE AND DOWNLOAD URL FOR SMOKELOADER ON 2017-05-04:
- 162.220.246[.]254 port 80 - 162.220.246[.]254 - GET /
- 162.220.246[.]254 port 80 - 162.220.246[.]254 - GET /flashplayer24pp_id_install.exe?dl=1
POST-INFECTION TRAFFIC FROM SAME SMOKELOADER SAMPLE ON 2017-04-25:
- www.bing[.]com - GET /
- support.microsoft[.]com - POST /kb/2600211
- go.microsoft[.]com - POST /fwlink/?LinkId=120337
- www.microsoft[.]com - GET /
- www.adobe[.]com - POST /
- msdn.microsoft[.]com - GET /vstudio
- 195.154.72[.]149 port 80 - aoids03wkde38[.]us - POST /
FILE HASHES
FAKE FLASH PLAYER INSTALLER (SMOKE LOADER):
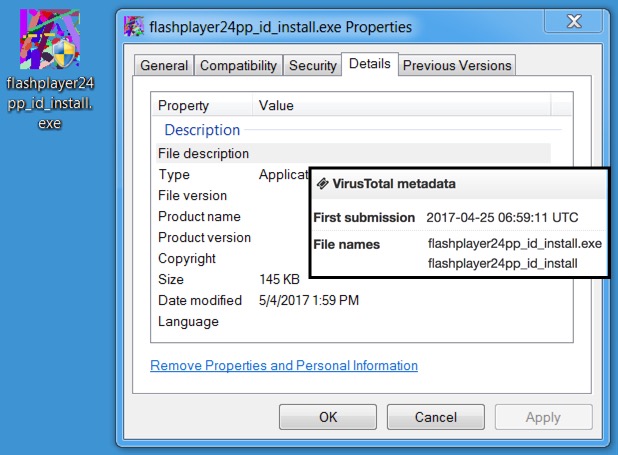
- SHA256 hash: b1ac30b73b959603bb2c42f97bab6ca48f5a953a1fcb50bacb06f0eb5e2402c7
File name: flashplayer24pp_id_install or flashplayer24pp_id_install.exe
File size: 148,992 bytes
Shown above: Smoke Loader sample from 2017-05-04 was around as early as 2017-04-25.
IMAGES
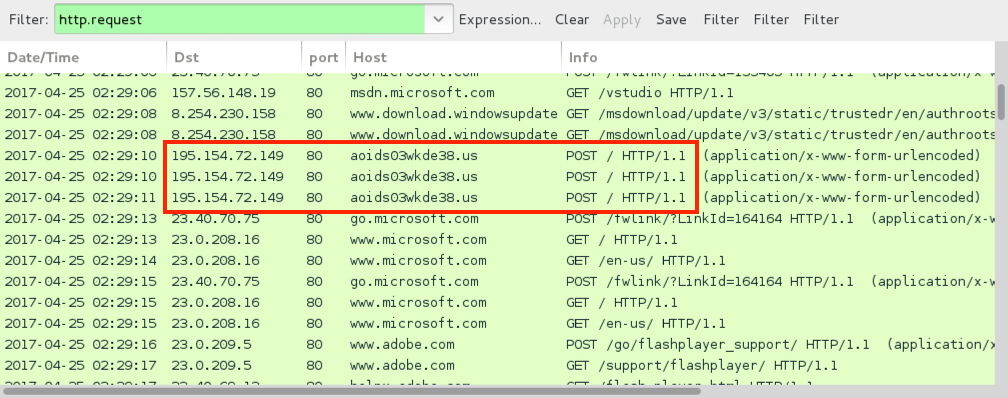
Shown above: Post-infection traffic caused by the Smoke Loader sample from a pcap dated 2017-04-25.
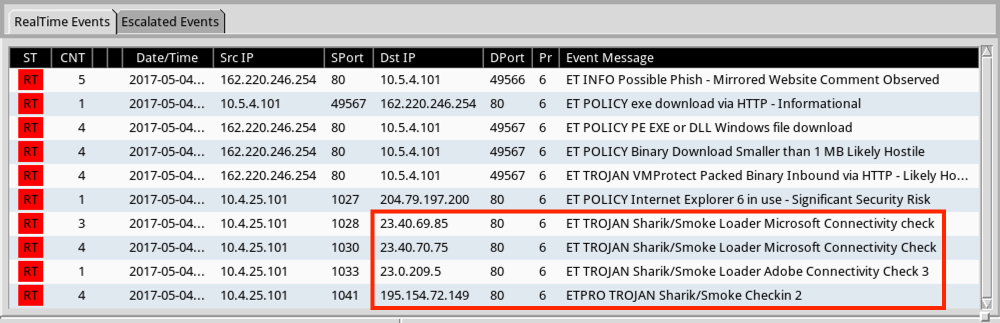
Shown above: Some alerts on both pcaps from the Emerging Threats and ETPRO rulesets using Sguil and tcpreplay on Security Onion.
Click here to return to the main page.