2017-05-04 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-04-Hancitor-infection-with-ZLoader.pcap.zip 11.0 MB (10,960,848 bytes)
- 2017-05-04-Hancitor-infection-with-ZLoader.pcap (11,646,696 bytes)
- 2017-05-04-Hancitor-malspam-6-examples.zip 7.8 kB (7,798 bytes)
- 2017-05-04-Hancitor-malspam-1559-UTC.eml (2,785 bytes)
- 2017-05-04-Hancitor-malspam-1600-UTC.eml (2,786 bytes)
- 2017-05-04-Hancitor-malspam-1623-UTC.eml (2,757 bytes)
- 2017-05-04-Hancitor-malspam-1705-UTC.eml (2,733 bytes)
- 2017-05-04-Hancitor-malspam-2032-UTC.eml (2,732 bytes)
- 2017-05-04-Hancitor-malspam-2034-UTC.eml (2,732 bytes)
- 2017-05-04-malware-from-Hancitor-infection.zip 247.5 kB (247,475 bytes)
- BND7B8.tmp (194,560 bytes)
- USPS_glen.fendale.doc (190,464 bytes)
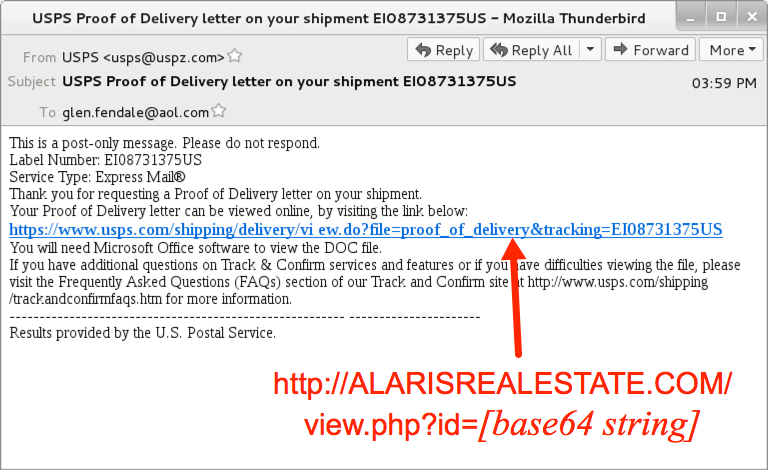
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date/Time: Thursday 2017-05-04 as early as 15:59 UTC through at least 20:34 UTC
- From: (spoofed) "USPS" <usps@uspz[.]com>
- Subject: USPS Proof of Delivery letter on your shipment EI00474731US
- Subject: USPS Proof of Delivery letter on your shipment EI02553212US
- Subject: USPS Proof of Delivery letter on your shipment EI08731375US
- Subject: USPS Proof of Delivery letter on your shipment EI18266375US
- Subject: USPS Proof of Delivery letter on your shipment EI25088368US
- Subject: USPS Proof of Delivery letter on your shipment EI28338016US
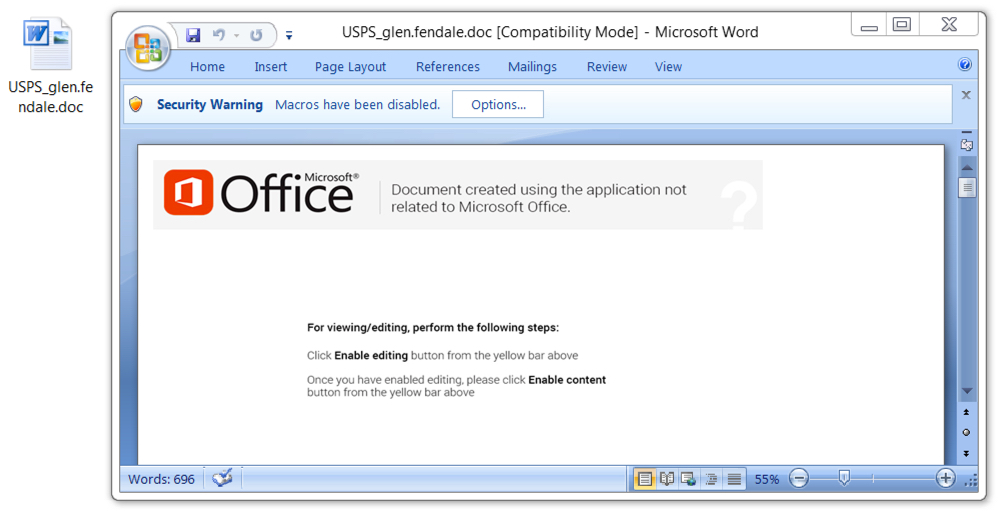
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
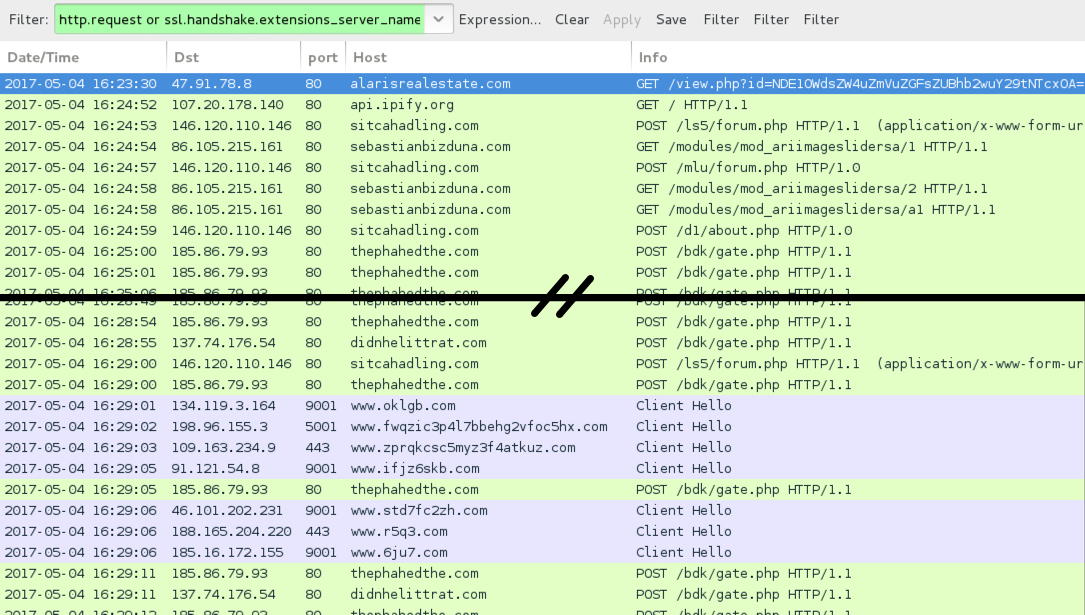
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUEST FOR THE WORD DOCUMENT:
- 47.91.78[.]8 port 80 - ALARISREALESTATE[.]COM - GET /view.php?id=[base64 string]
- 47.91.78[.]8 port 80 - LAZYJPRINTINGSERVICES[.]COM - GET /view.php?id=[base64 string]
POST-INFECTION TRAFFIC:
- 146.120.110[.]146 port 80 - sitcahadling[.]com - POST /ls5/forum.php
- 146.120.110[.]146 port 80 - sitcahadling[.]com - POST /mlu/forum.php
- 146.120.110[.]146 port 80 - sitcahadling[.]com - POST /d1/about.php
- 86.105.215[.]161 port 80 - sebastianbizduna[.]com - GET /modules/mod_ariimageslidersa/1
- 86.105.215[.]161 port 80 - sebastianbizduna[.]com - GET /modules/mod_ariimageslidersa/2
- 86.105.215[.]161 port 80 - sebastianbizduna[.]com - GET /modules/mod_ariimageslidersa/a1
- 185.86.79[.]93 port 80 - thephahedthe[.]com - POST /bdk/gate.php
- 137.74.176[.]54 port 80 - didnhelittrat[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 8b31cbf818c17fe3778124c102c8d74d14ffdc41fc5548bff5b861e2720a8e68
File name: USPS_glen.fendale.doc
File size: 190,464 bytes
File description: Hancitor maldoc
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: 19d54c76c0d887ff607ea8eef0c59237e26dc9df54a96d4c8b957fbbb21f3bb9
File location: C:\Users\[username]\AppData\Local\Temp\BND7B8.tmp
File size: 194,560 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
