2017-05-10 - "BLANK SLATE" CAMPAIGN PUSHES CERBER RANSOMWARE OR GLOBEIMPOSTER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-10-Blank-Slate-campaign-7-pcaps.zip 1.6 MB (1,647,425 bytes)
- 2017-05-10-Blank-Slate-malspam-tracker.csv.zip 1.7 kB (1,729 bytes)
- 22017-05-10-Blank-Slate-emails-and-associated-ransomware-samples.zip 1.8 MB (1,847,463 bytes)
BACKGROUND:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
TODAY'S NOTES:
- Seeing some GlobeImposter ransomware along with the usual Cerber ransomware from this campaign.
- Only seeing zipped .js files as attachments so far this week.
EMAILS
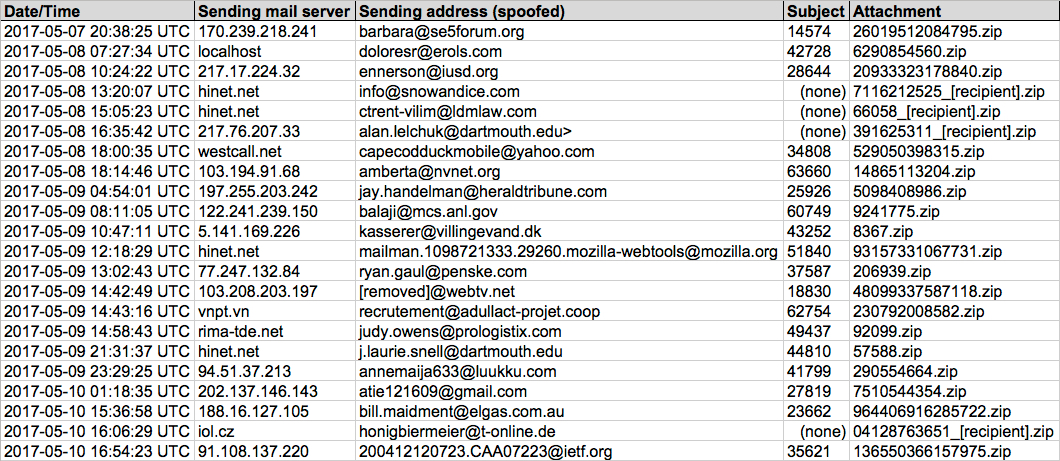
Shown above: Screenshot of spreadsheet tracker (1 of 3).
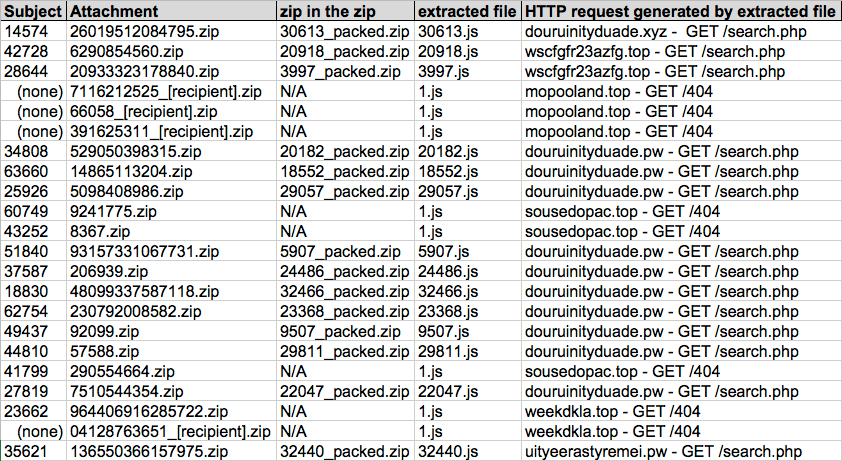
Shown above: Screenshot of spreadsheet tracker (2 of 3).
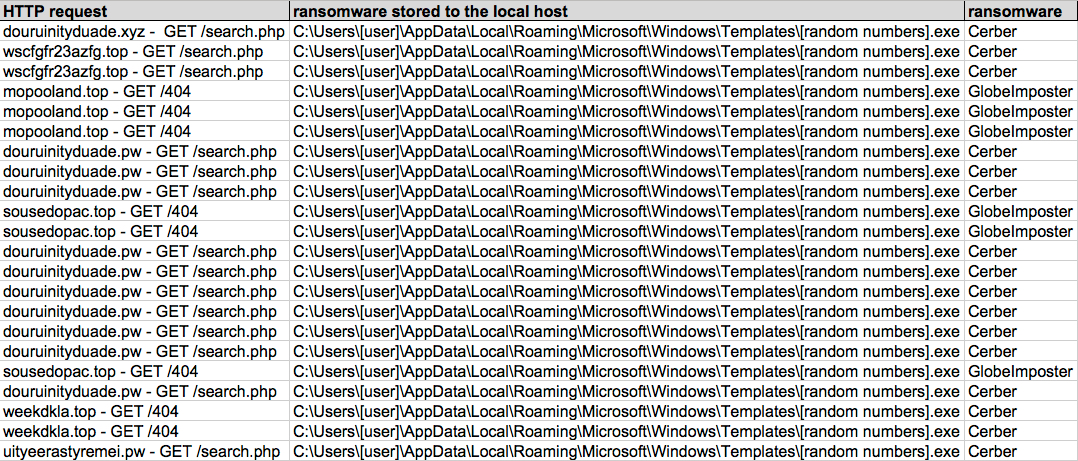
Shown above: Screenshot of spreadsheet tracker (3 of 3).
TRAFFIC
URLS GENERATED BY THE EXTRACTED FILES:
- 47.91.76[.]69 port 80 - mopooland[.]top - GET /404
- 47.91.76[.]69 port 80 - sousedopac[.]top - GET /404
- 47.91.76[.]69 port 80 - weekdkla[.]top - GET /404
- 47.91.89[.]227 port 80 - douruinityduade[.]pw - GET /search.php
- 47.91.89[.]227 port 80 - douruinityduade[.]xyz - GET /search.php
- 47.91.89[.]227 port 80 - uityeerastyremei[.]pw - GET /search.php
- 47.91.89[.]227 port 80 - wscfgfr23azfg[.]top - GET /search.php
CERBER RANSOMWARE POST-INFECTION TRAFFIC:
- 94.21.172[.]0 - 94.21.172[.]31 (94.21.172[.]0/27) UDP port 6893
- 94.22.172[.]0 - 94.22.172[.]31 (94.22.172[.]0/27) UDP port 6893
- 94.23.172[.]0 - 94.23.175[.]255 (94.23.172[.]0/22) UDP port 6893
- 45.35.183[.]221 port 80 - p27dokhpz2n7nvgr.1hkjl3[.]top - HTTP traffic for Cerber decryption instructions on 2017-05-00
- 45.35.183[.]221 port 80 - p27dokhpz2n7nvgr.1eetmp[.]top - HTTP traffic for Cerber decryption instructions on 2017-05-09
- 89.238.181[.]75 port 80 - p27dokhpz2n7nvgr.1jyhqc[.]top - HTTP traffic for Cerber decryption instructions on 2017-05-10
GLOBEIMPOSTER RANSOMWARE POST-INFECTION TRAFFIC:
- None
SHA256 HASHES
ZIP ARCHIVES:
- 29e7ff4c502b99d5bbe8d315cee8db328b40e6d84c771ba6db535c13272a0938 - 8367.zip
- f0e053f6cf3adc4ddb20daf382a71a369721bfd08b668fd7eae75698b01c73e6 - 57588.zip
- ff98f0b0e09ea3f02c7f79c851b2b7322fd4cc6f78557eae9f7c0b9b834298a6 - 66058_[recipient].zip
- 6f829b86da3bc9ceda839274b39cd730dd4affa9b694300ac62a94a370a4806c - 92099.zip
- b040c8757deef20f61667066b0c932451b39382fad63f0c4d0c72cbfafd0999a - 206939.zip
- 0b0aab38b8dbdab5fe377f492c137444e35eaaafd975818f177d539f9c7eee08 - 9241775.zip
- 1561a03bb781015743305e75a5aa4b3d6ff58daa2b293fa0918a41283e333a3c - 290554664.zip
- ff98f0b0e09ea3f02c7f79c851b2b7322fd4cc6f78557eae9f7c0b9b834298a6 - 391625311_[recipient].zip
- 397f840a2c2204fdd20c1766c562a9846680e68cd8f1ce4b74269ea8a83d22ea - 5098408986.zip
- 10e85b0b6f88a7aca12dc8381dd9c009b49a82d2920286a56019f2c16b0fb9a3 - 6290854560.zip
- f41334f00e8392481de41b29459ae993705c9e45bcc919a9bb0142e0749ddf2b - 7510544354.zip
- ff98f0b0e09ea3f02c7f79c851b2b7322fd4cc6f78557eae9f7c0b9b834298a6 - 7116212525_[recipient].zip
- 8718674c38e7be05b581af99663d27041c57caef88040ccc90300f278d05bd07 - 04128763651_[recipient].zip
- e1d3a33301a94568db86741a23d204d82afb78be01fde557059d7899720f2b63 - 14865113204.zip
- 5b8596c824987658115e42f8d0a31240f7893af3af306202dd21c6119a67189b - 230792008582.zip
- 5a513948360ef9d4e8c48ced5d3f109bb83a9c224fd327126e04cde36a28a1db - 529050398315.zip
- 448fc784571983e8b5dd84fe4d5784ed8974d8b6e5589b0f412245d60797aab5 - 20933323178840.zip
- 7d7c1993257b8f40d31a1c4e4e992ba13140152cfbf7d4a8d31e520dd22a2c00 - 26019512084795.zip
- b8388cf31b0eac4ba610283d45b85cf1c58f47d1bdd3dfb2b6952b1f4217334f - 48099337587118.zip
- ea5a26e97938d18f01b10e1cae5b7c278682a10c99fe33c6fa87f07f2c51fea0 - 93157331067731.zip
- 25bac4e2b43a7903bb1ab36ab414f66cffe0c92fdd781005dad587d31ec0d324 - 136550366157975.zip
- 5895c5c93d6e9359edd20bac9e4a11c6f15b32e2a54959ee689792e3d2dd7b34 - 964406916285722.zip
EXTRACTED .JS FILES:
- 00b8d9e7b4f98abd2b4b67802fcd7be88e87ebd57870ed5a10aee1a8541b8917 - 1.js
- 6a629b363769bc75e07205784ceaa307e8decb0f823bf051bd3556a90f6704df - 1.js
- 90c458ba3d094ad4c3d84d6ed124f74f4940265d790210e84e53fb53b12b5660 - 1.js
- a5dde2575b4037454b0c6e92a6bfe4bd429cd1e4834b22d79b929c2f9fa4d2ad - 1.js
- bcba0e37b9b27b7632a7ad6f45243144c0afcf385d8154d66a6b637137cf0752 - 1.js
- fcbba7bd0cf7e1be027ec1e11b61a7e52634b4fce6d7be6aa3a1941c0295be2f - 1.js
- b09a30233dad22763e261bf083e2f6acda057a73d171a21c92b6e70af555adca - 3997.js
- 29670a559616fd54d113e37bc2067177d4c8fce2ae2f33515d81e5d3b185aee2 - 5907.js
- 2049506d3aea7215f44b80e1e49579028322b957f2c99170c3816a748dc423e1 - 9507.js
- 5c283845068026962dd6baec7e36186138fa2ebe80bfb1a62ad053728ca1bb56 - 18552.js
- 1531d95ff858dc77ba5556a2f4fed505d8283307e7af66053e0a4966500dd191 - 20182.js
- 8e7bb472110e97816952d4f5d3876d2de6974e730f4ee9dc193ac8cc32bef056 - 20918.js
- d64763aa3f1ecb0eb36dbb93dcbfafacc4d31331c49f8e2c12918f0724fcdfe5 - 22047.js
- 2c1fca046e79f87134f7cc83795d09fce6a3672f2a80c75d73fcf6f5ffe99184 - 23368.js
- d0980aacc8ea9d02992885c5b253f632d2b0db060832f43f571e8ace8aaa43b2 - 24486.js
- 05d025cf6617f4047e098064129428f26cfd95847ad0eb483595ad41f7c1eefb - 29057.js
- b1b5b3bef09f55186d37e0fa9629aefec8a857ac99fe8c5da587dfbb86c67aee - 29811.js
- ce78439627595fb5205db1381b52317d9f7919c7025a7c1bec0046f9359d8f31 - 30613.js
- 50b82794905433b8212a9e693881455cb1f847816adc0819c7db0d607f8702a5 - 32440.js
- 2c1fca046e79f87134f7cc83795d09fce6a3672f2a80c75d73fcf6f5ffe99184 - 32466.js
RANSOMWARE SAMPLES:
- SHA256 hash: a414dfab03e91901378329d1dfb7c13e76b745ffd1e00a6457533860af1c11fd
File description: Cerber ransomware from douruinityduade[.]xyz on 2017-05-08
- SHA256 hash: 5c7c5bd5fa9084851bc5247963ada63a3312c2211d7498d3a78673c9334f4e86
File description: Cerber ransomware from douruinityduade[.]pw on 2017-05-09
- SHA256 hash: 0c212918fb29d3388e3f59e7908dbc9d9eb29756423a057c7b7da6792c6be73d
File description: Cerber ransomware from wscfgfr23azfg[.]top on 2017-05-09
- SHA256 hash: 0edc1cf02ce8889de673d15d3809e6fab7f8e43838bea6a6ec524f493f00ce1e
File description: GlobeImposter ransomware from mopooland[.]top on 2017-05-09 and sousedopac[.]top on 2017-05-10
- SHA256 hash: b3b654c619859a65f0861a801686f74d834945d714a3d9afcbc9c88b2fe84740
File description: Cerber ransomware from uityeerastyremei[.]pw on 2017-05-10
- SHA256 hash: dad7dd3fddfc23f7eed6bfd9d88eb1ffff155b4c812886957c9f3229df6adc0e
File description: Cerber ransomware from weekdkla[.]top on 2017-05-10
IMAGES
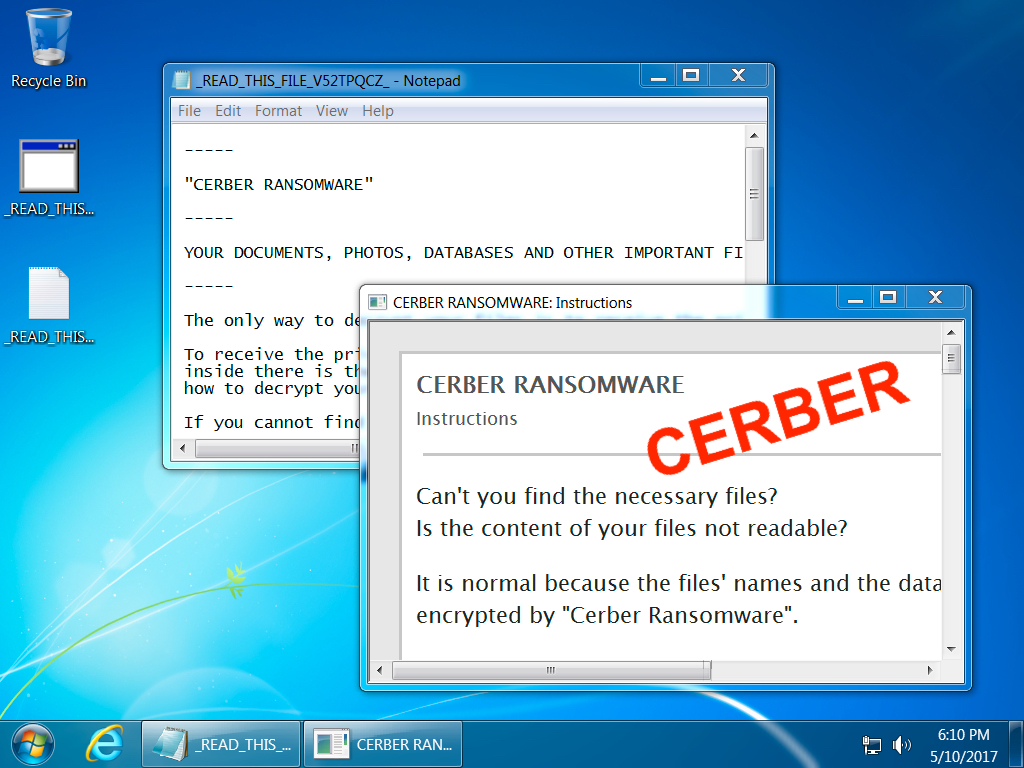
Shown above: Desktop of a Windows host infected with Cerber ransomware
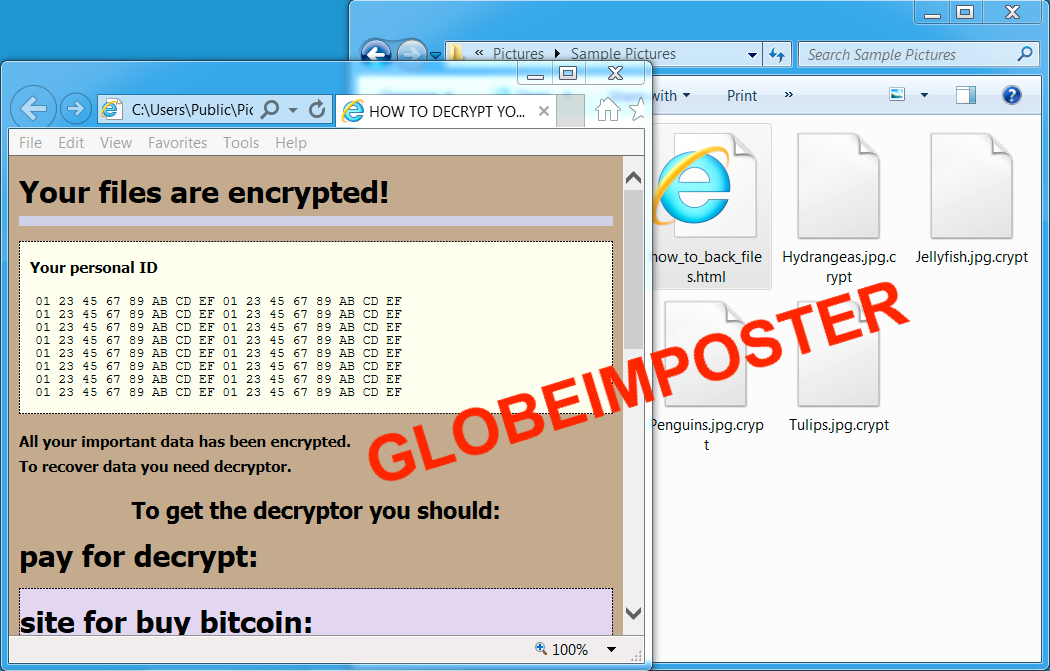
Shown above: A Windows host infected with GlobeImposter ransomware
Click here to return to the main page.
