2017-05-10 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-10-Hancitor-infection-with-ZLoader.pcap.zip 12.9 MB (12,904,318 bytes)
- 2017-05-10-Hancitor-infection-with-ZLoader.pcap (13,413,872 bytes)
- 2017-05-10-Hancitor-malspam-3-examples.zip 4.8 kB (4,793 bytes)
- 2017-05-10-Hancitor-malspam-1435-UTC.eml (800 bytes)
- 2017-05-10-Hancitor-malspam-1456-UTC.eml (156,66 bytes)
- 2017-05-10-Hancitor-malspam-1457-UTC.eml (769 bytes)
- 2017-05-10-malware-from-Hancitor-infection.zip 93.4 kB (93,364 bytes)
- WEXInc_subpoena_Reggie.Standsford.doc (160,256 bytes)
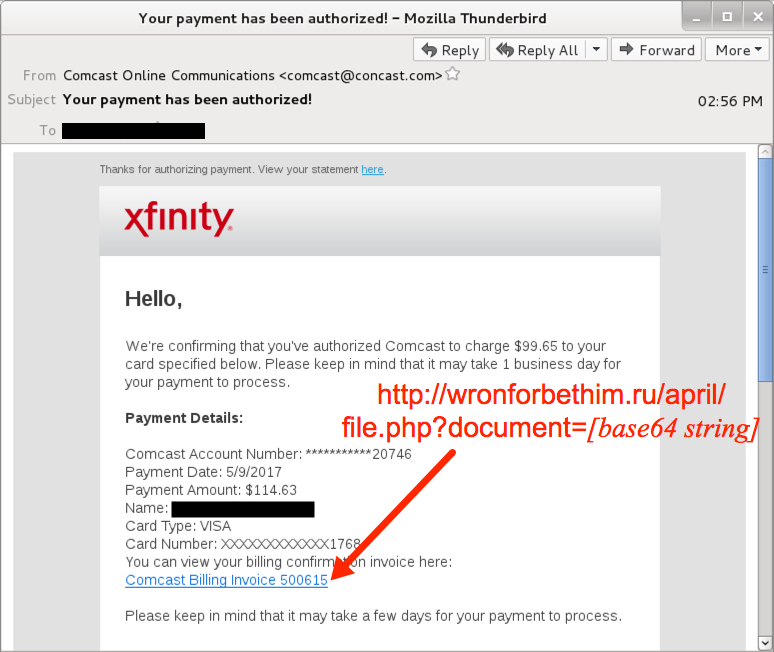
Shown above: Screen shot from one of the fake Comcast emails.
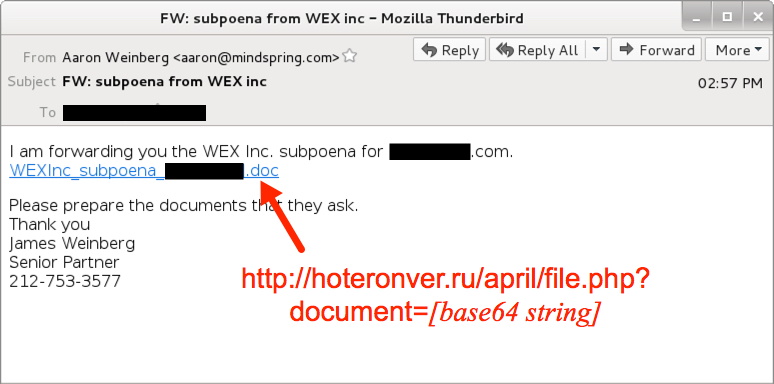
Shown above: Screen shot from one of the fake subpoena emails.
EMAIL HEADERS:
- Date: Wednesday 2017-05-10
- Subject: FW: subpoena from WEX inc
- From: "Aaron Weinberg" <aaron@mindspring[.]com>
- Subject: Your payment has been authorized!
- From: "Comcast Online Communications" <comcast@concast[.]com>
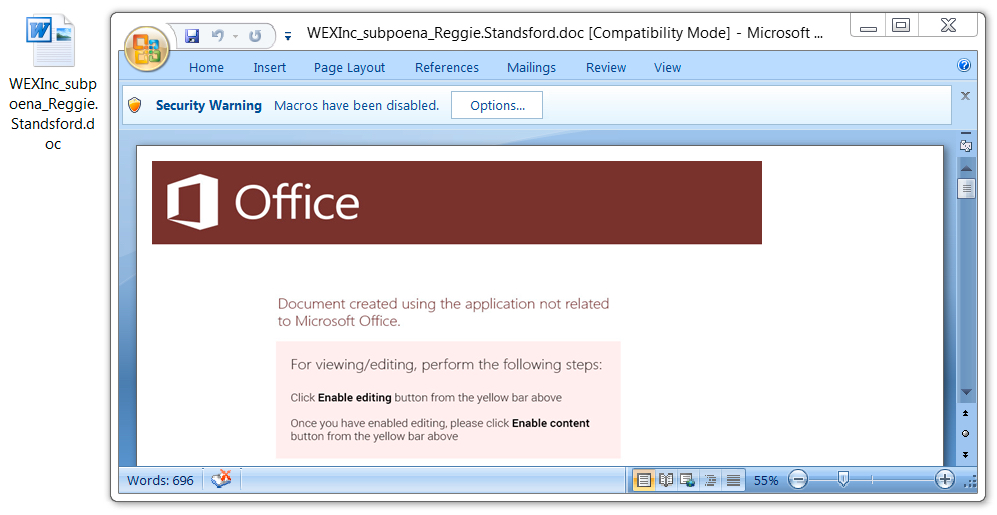
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
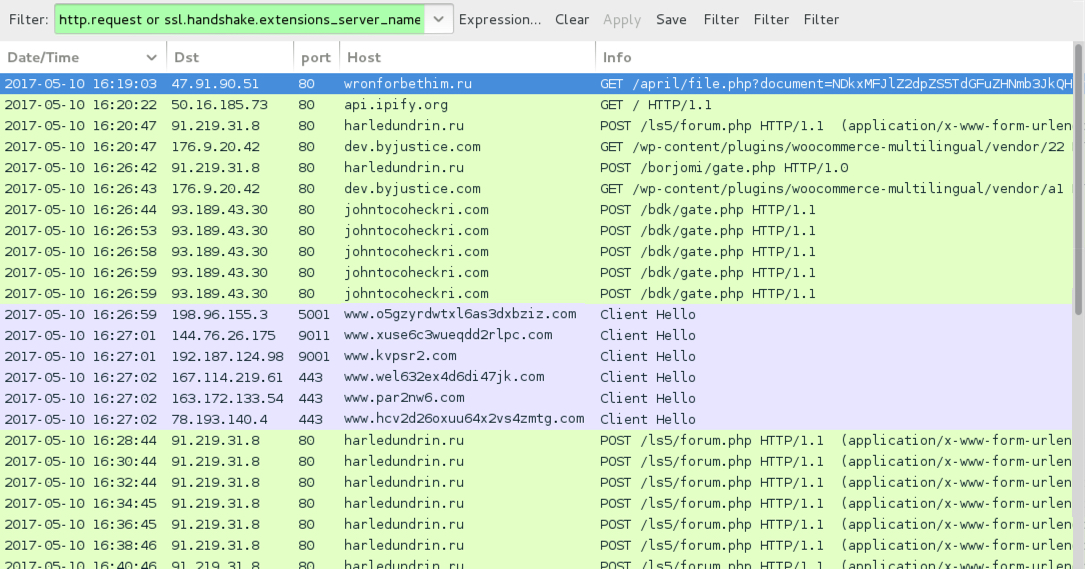
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- 47.91.90[.]51 port 80 - wronforbethim[.]ru - GET /april/file.php?document=[base64 string]
- 47.91.90[.]51 port 80 - hoteronver[.]ru - GET /april/file.php?document=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- WEXInc_subpoena_[username].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 91.219.31[.]8 port 80 - harledundrin[.]ru - POST /ls5/forum.php
- 91.219.31[.]8 port 80 - harledundrin[.]ru - POST /borjomi/gate.php
- 176.9.20[.]42 port 80 - dev.byjustice[.]com - GET /wp-content/plugins/woocommerce-multilingual/vendor/22
- 176.9.20[.]42 port 80 - dev.byjustice[.]com - GET /wp-content/plugins/woocommerce-multilingual/vendor/a1
- 93.189.43[.]30 port 80 - johntocoheckri[.]com - POST /bdk/gate.php
- 77.73.68[.]159 port 80 - ledderofort[.]com - attempted TCP connection but no response from the server
- 185.175.158[.]242 port 80 - repandranre[.]ru - attempted TCP connection but no response from the server
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 7f1bc132a6567c4a7d0c8de1c7ae29004203edc9d2f542220833fe0ea06da91c
File name: WEXInc_subpoena_Reggie.Standsford.doc
File size: 160,256 bytes
File description: Hancitor maldoc
Click here to return to the main page.
