2017-05-11 - JUMPING ON THE JAFF RANSOMWARE BANDWAGON
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-11-Jaff-ransomware-infection-from-phinamco_com.pcap.zip 140.6 kB (140,625 bytes)
- 2017-05-11-Jaff-ransomware-malspam-tracker.csv.zip 1.9 kB (1,898 bytes)
- 2017-05-11-Jaff-ransomware-emails-and-malware.zip 3.9 MB (3,860,396 bytes)
NOTES:
- Seems like everyone and their mother has posted information about the new Jaff ransomware that appeared today. I'm just jumping on the bandwagon.
- It's distributed through the same type of malspam we've seen before with PDF attachments --> embedded Word documents (with malicious macros) --> follow-up malware.
EMAILS
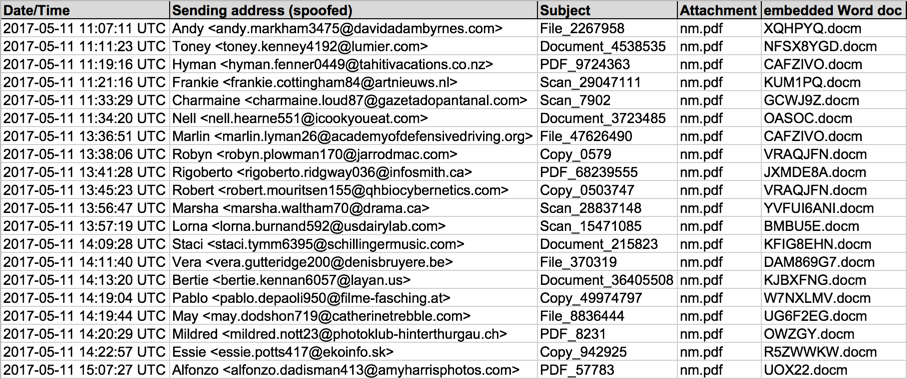
Shown above: Screenshot of spreadsheet tracker.
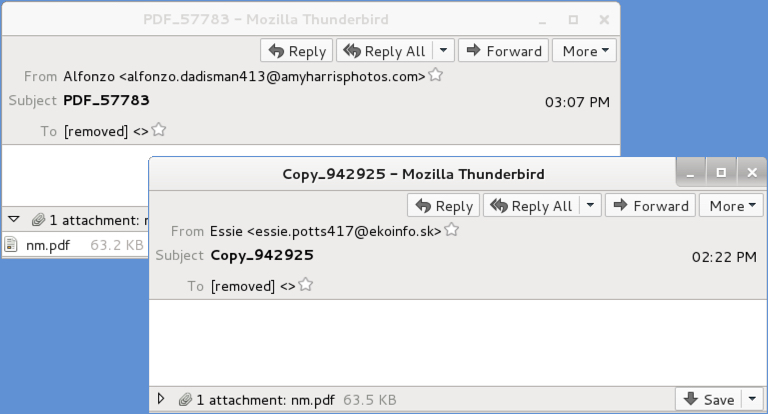
Shown above: Two examples of these emails.
DATES/TIMES:
- Thursday 2017-05-11 as early as 11:17 UTC through at least 15:07 UTC
EXAMPLES OF SENDING ADDRESSESS (ALL SPOOFED):
- From: Alfonzo <alfonzo.dadisman413@amyharrisphotos[.]com>
- From: Andy <andy.markham3475@davidadambyrnes[.]com>
- From: Bertie <bertie.kennan6057@layan[.]us>
- From: Charmaine <charmaine.loud87@gazetadopantanal[.]com>
- From: Essie <essie.potts417@ekoinfo[.]sk>
- From: Frankie <frankie.cottingham84@artnieuws[.]nl>
- From: Hyman <hyman.fenner0449@tahitivacations[.]co[.]nz>
- From: Lorna <lorna.burnand592@usdairylab[.]com>
- From: Marlin <marlin.lyman26@academyofdefensivedriving[.]org>
- From: Marsha <marsha.waltham70@drama[.]ca>
- From: May <may.dodshon719@catherinetrebble[.]com>
- From: Mildred <mildred.nott23@photoklub-hinterthurgau[.]ch>
- From: Nell <nell.hearne551@icookyoueat[.]com>
- From: Pablo <pablo.depaoli950@filme-fasching[.]at>
- From: Rigoberto <rigoberto.ridgway036@infosmith[.]ca>
- From: Robert <robert.mouritsen155@qhbiocybernetics[.]com>
- From: Robyn <robyn.plowman170@jarrodmac[.]com>
- From: Staci <staci.tymm6395@schillingermusic[.]com>
- From: Toney <toney.kenney4192@lumier[.]com>
- From: Vera <vera.gutteridge200@denisbruyere[.]be>
EXAMPLES OF SUBJECT LINES:
- Subject: Copy_0503747
- Subject: Copy_0579
- Subject: Copy_49974797
- Subject: Copy_942925
- Subject: Document_215823
- Subject: Document_36405508
- Subject: Document_3723485
- Subject: Document_4538535
- Subject: File_2267958
- Subject: File_370319
- Subject: File_47626490
- Subject: File_8836444
- Subject: PDF_57783
- Subject: PDF_68239555
- Subject: PDF_8231
- Subject: PDF_9724363
- Subject: Scan_15471085
- Subject: Scan_28837148
- Subject: Scan_29047111
- Subject: Scan_7902
FILE NAME FOR ALL ATTACHMENTS:
- nm.pdf [File attributes: PDF document, version 1.4]
MALWARE
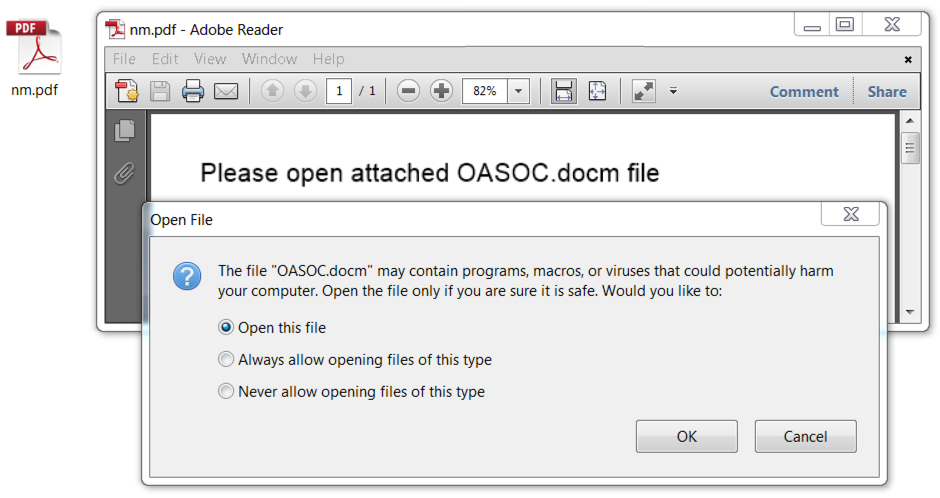
Shown above: Opening the nm.pdf file provides a malicious Word document with macros.
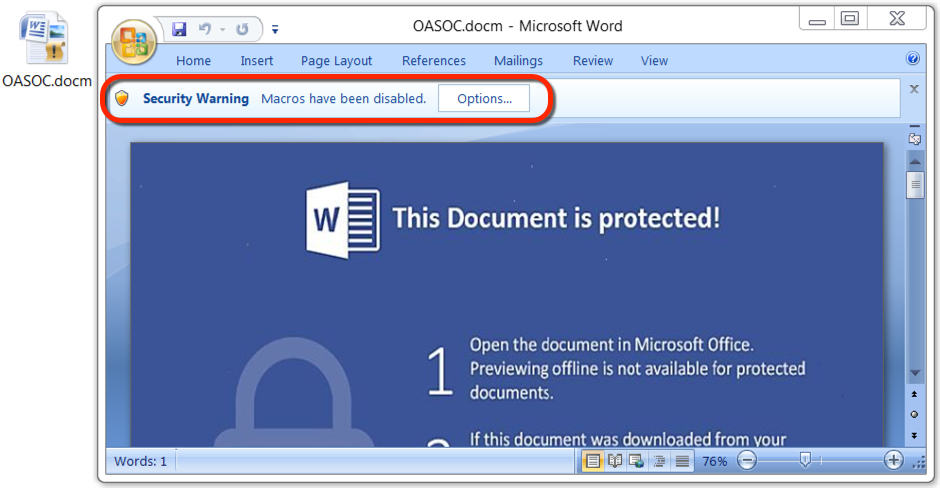
Shown above: Macros from the embedded Word documents are designed to infect a Windows host with malware.
SHA256 HASHES OF PDF FILES ATTACHED TO THESE EMAILS:
- 0a265c366932405a3247508a1a1a65241681e9d698acf31c828f0b6c68a04be0 - nm.pdf
- 1100f0d5e11ef9177c6b45b58999f86a2f1451668721ae6b2e73135cf3e487c8 - nm.pdf
- 235b8bf934ba5a562a7f47e8f622092ef6492bab644eb9a0b63f1aa9cb685d84 - nm.pdf
- 3028117d9773d4f978abd6ac6d14f17593e69297efec757104c4098ea5ad1768 - nm.pdf
- 358a6decd42df41c0234e5f14f5ad572e4da50ee030b8a9569821f4ffb6c8cd3 - nm.pdf
- 372adf1cdf70c716da09c5b2aa2ab1f3d48a6e3d1a7a969eb847d6562e0e0a3b - nm.pdf
- 3b7cd88cf3acb5e617b5bfdaab43413e96147393dc6fae264a8ca361381344c9 - nm.pdf
- 3e4bd555d5eb34cf3b79d21ab7788c9cf3c6be3eccff48655c265e31dceaf599 - nm.pdf
- 47e81d1de081e4e435bdbdd0df2857055fffdf749ddf7c1bb1f2e0040241724f - nm.pdf
- 57bfe19f9615f026765825689cdc26725f4f24f23123bdcc35aeddbdc5274fc4 - nm.pdf
- 6c4c5a1500a014aba0b5a01193abe9dd22c960028fa77ab9f3f8a678ad42dd03 - nm.pdf
- 8a3070bf1c86dfa86650e717c2d466f62ff253f28797a42bff819ed17571cbb0 - nm.pdf
- ac5c2c47c4cf28ee8336a51ed33eec40ef76b7990691f23eade0b240cd61c40b - nm.pdf
- ad454b174bc2d2903fc3063da2c918daf9c2bb9ffa1e13f6db42ad82f549cefe - nm.pdf
- b0f475e09e82891cbcd6c2a823000161191ea6d899f9d610f508ab26dee59584 - nm.pdf
- c3cf407f5c6269d79aef3f2e8bcf296a325fa067aa1af3f44c6e53189f66e111 - nm.pdf
- eb41eb3aa7d96ceebefa633cb519fae84ca66dd434cf3303576e9aff86a02f61 - nm.pdf
- f712e08b8020c5a0615a0f128ea9a891d2d45deafe7446c11f9227bd77dd28b3 - nm.pdf
SHA256 HASHES OF MALICIOUS WORD DOCUMENTS EMBEDDED IN THE ABOVE PDF FILES:
- 1b33cc35011ddee5766342ba26f9964712f6531c6c057138890e36a58404d5b0 - OASOC.docm
- 20c7800aa15b5d378ff3b39e9c901dc68a12489a4a1800a6ec9b59f16ba1bafc - VRAQJFN.docm
- 219485c2dd60f9cb70a1c787802551f77e6cb1b421568372d425ffa49772fca8 - UG6F2EG.docm
- 29c027a3386083974b6dbf51d1e0c2e3f89b78c44bda350a543af4c5a813f456 - R5ZWWKW.docm
- 2efcffff5c144f8397da3df815f15145a0600a85a612ede9e0ae6846b7bf5388 - KJBXFNG.docm
- 4792532defb4431aa399f649a3e443a62f062e4a99458c7ee240c2ae5d6716f4 - DAM869G7.docm
- 517b9cb82b4d4e7e8af5ec96cc832bcd0ec6d1203bc8046c8e3d546e3b283e65 - NFSX8YGD.docm
- 59959df33f904f32046e4f79830f574862e8fe9edae75f88f91064bebb5f4d8c - UOX22.docm
- 59be1462a0d8fe2dcb88f6174e9d671bba7d8969a46dc5f566e006acec4df671 - YVFUI6ANI.docm
- 641b2ad3d345b97a8c92d152bb3f9b4b8a98af41ce3d1a9454fb804cce8f26dc - W7NXLMV.docm
- 6d31108908dc891f1c784831acfc69c5da65d982d8928da5ccfd0b15351aa3db - KUM1PQ.docm
- 6e7ff200d849d8594ddb72d4840daefa78d0d025f28d26c6c96f2eaccfba19ba - GCWJ9Z.docm
- 713e492aa212eb265de9dfc1d615dd57940aa3bde5293aef15165da027e28d3c - OWZGY.docm
- 7c550b82d112e065890a8e7efe862832b32cfeeb4f6a9ce85151525147a7cb9d - JXMDE8A.docm
- 9e441538b51c24f8f1e32411a52b58c1aaf6a591e96b5a17eebd3550da185baf - CAFZIVO.docm
- aa576e4bd47c41c783a20b41920601bfe092dd10ec262917e50b363eb132f958 - KFIG8EHN.docm
- b6c2f3466a76a56d0e0a373130e6f147fa1e11a0faa9f146d3418b4c477fc7ea - BMBU5E.docm
- c20562703066886685e5980ebc9f94499f9a152e628777f15592e4092348b9e8 - XQHPYQ.docm
JAFF RANSOMWARE SAMPLE DOWNLOADED BY ONE OF THE WORD DOCUMENTS:
- SHA256 hash: 1be07198c324c9732d4e2676945ec021eeacd78775aea2100f49ca0483d3f901
- File size: 155,648 bytes
- File location: C:\Users\[username]\AppData\Loca\Temp\pitupi20.exe
TRAFFIC
URLS FROM THE WORD MACROS TO DOWNLOAD JAFF RANSOMWARE:
- 5hdnnd74fffrottd[.]com - GET /af/f87346b
- babil117[.]com - GET /f87346b
- boaevents[.]com - GET /f87346b
- byydei74fg43ff4f[.]net - GET /af/f87346b
- easysupport[.]us - GET /f87346b
- edluke[.]com - GET /f87346b
- julian-g[.]ro - GET /f87346b
- phinamco[.]com - GET /f87346b
- takanashi[.]jp - GET /f87346b
- techno-kar[.]ru - GET /f87346b
- tending[.]info - GET /f87346b
- tiskr[.]com - GET /f87346b
- trans-atm[.]com - GET /f87346b
- trialinsider[.]com - GET /f87346b
- vscard[.]net - GET /f87346b
- wipersdirect[.]com - GET /f87346b
JAFF RANSOMWARE POST-INFECTION TRAFFIC:
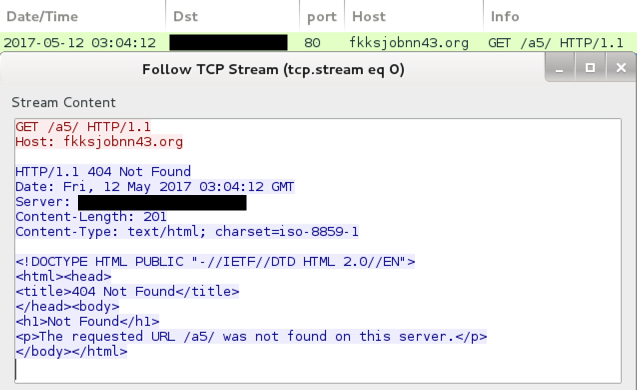
- ???? port 80 - fkksjobnn43[.]org - GET /a5/
- rktazuzi7hbln7sy[.]onion - Tor domain for Jaff Decryptor
fkksjobnn43[.]org didn't resolve in DNS, so I edited the Windows hosts file to generate an HTTP request to a web server I control.
IMAGES
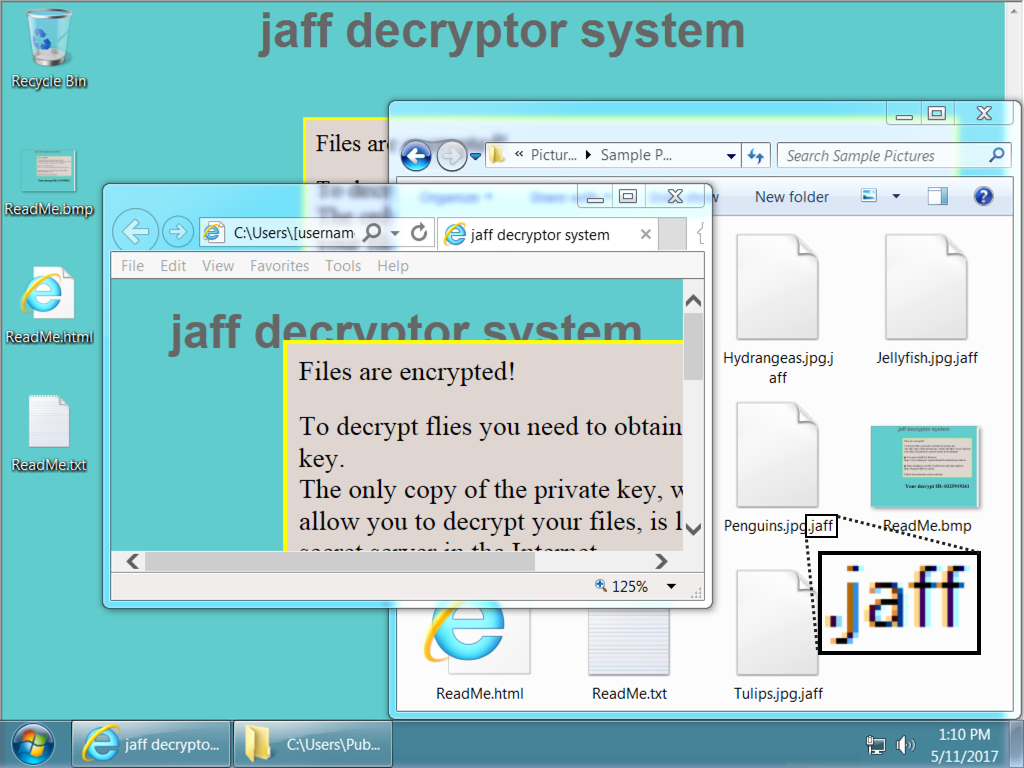
Shown above: Desktop of an infected Windows host.
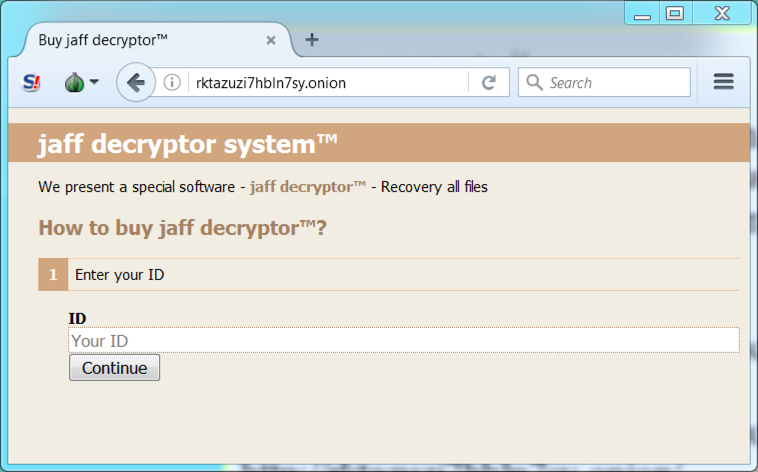
Shown above: Going to the Jaff Decryptor. Why is "jaff decryptor" in lower-case letters?
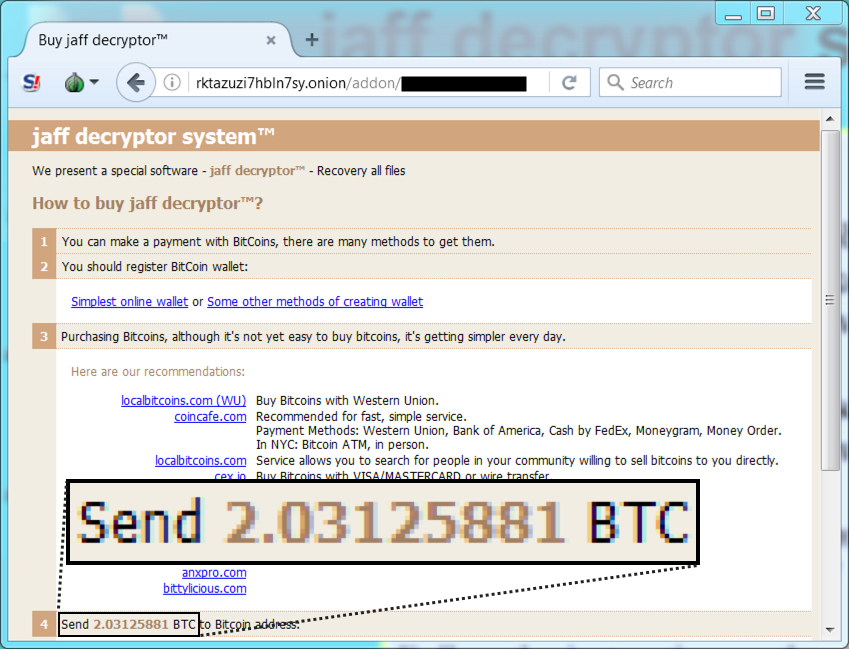
Shown above: Wonder what the exchange rate was when they calculated the bitcoin amount for their ransom.
Click here to return to the main page.