2017-05-12 - "BLANK SLATE" CAMPAIGN CONTINUES PUSHING CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-12-Cerber-ransomware-from-Blank-Slate-campaign-2-pcaps.zip kB ( bytes)
- 2017-05-12-Blank-Slate-malspam-tracker.csv.zip 0.9 kB (882 bytes)
- 2017-05-12-Blank-Slate-emails-and-Cerber-ransomware.zip kB ( bytes)
BACKGROUND:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
TODAY'S NOTES:
- Just the usual Cerber ransomware from this campaign.
- Only saw zipped .js files as attachments so far this week.
EMAILS
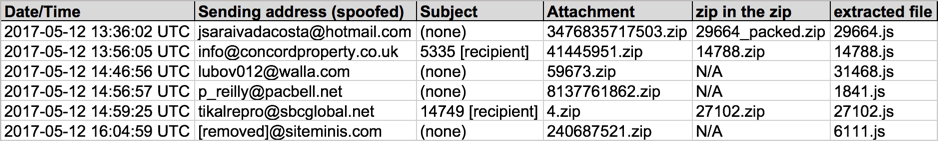
Shown above: Screenshot of spreadsheet tracker (1 of 2).
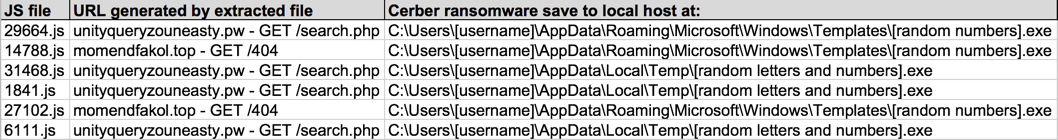
Shown above: Screenshot of spreadsheet tracker (2 of 2).
TRAFFIC
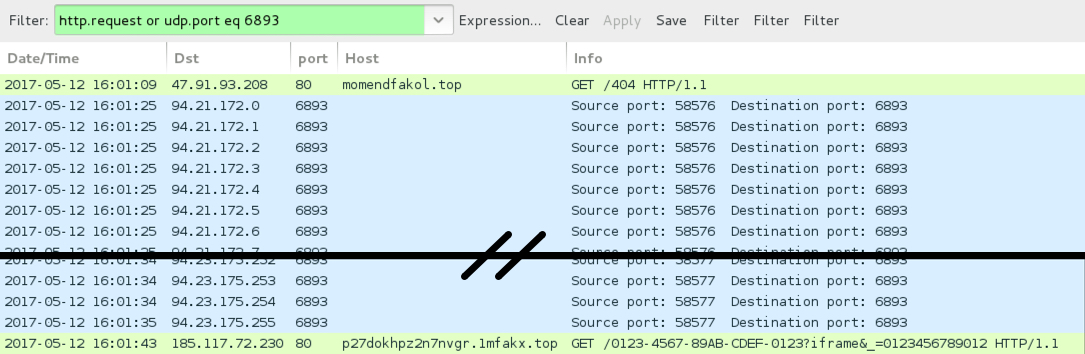
Shown above: Traffic from an infection filtered in Wireshark.
URLS GENERATED BY THE EXTRACTED FILES:
- 47.91.89[.]227 port 80 - unityqueryzouneasty[.]pw - GET /search.php
- 47.91.93[.]208 port 80 - momendfakol[.]top - GET /404
CERBER POST-INFECTION TRAFFIC:
- 94.21.172[.]0 - 94.21.172[.]31 (94.21.172[.]0/27) UDP port 6893
- 94.22.172[.]0 - 94.22.172[.]31 (94.22.172[.]0/27) UDP port 6893
- 94.23.172[.]0 - 94.23.175[.]255 (94.23.172[.]0/22) UDP port 6893
- 185.117.72[.]230 port 80 - p27dokhpz2n7nvgr.1mfakx[.]top - HTTP traffic for Cerber ransomware decryption instructions on 2017-05-12
SHA256 HASHES
ZIP ARCHIVES:
- 1707eda8de95b2f773a01b5d2c1bcd7a03b290a185a5d026734c8e32f6d68b75 - 4.zip
- d4d75f900fee0eeeed4e817367949f7403f107befc3df1a012c07369dc9fb460 - 59673.zip
- ba9f2bf001b9eab33b95ef0b4c57b3bd6ba84163f5010d07e4375acf577d53f8 - 41445951.zip
- d5611fb05817ebb4bccb83558a2f4f2e78274b67905f1b17f57773c2dbd0ee4d - 240687521.zip
- 653ec70da8b32d351e8b0282a3ff2ebd2227b45d396c1858063ef2938f75756c - 8137761862.zip
- 80cab22eab63ffb0e13a99c7d3c31fd989e569473e2ad7d487b025c5de6b7bd2 - 3476835717503.zip
EXTRACTED .JS FILES:
- 77473815f67a6ad11628a8f60f3d7f0aae1b8b8068f48b3c78f4eb50e950cda2 - 1841.js
- 232705cc7660f921e29f71dce856e14ca1bc838cc769a93c7fe55892a865cbc2 - 6111.js
- 1ea2c117483e174d9204b949355e1f8cbdbe306fd566a890471e96ddfaabef1a - 14788.js
- 8dba6237418b36ca79d5565a5bd2b442c0d9678f65209528edd00e3b021ab41b - 27102.js
- 47eae379577aa642f9840d6a260d32847b8b81cde7ebcd01e381202049658676 - 29664.js
- 6fd69b8f79f4284da6f0f9adb1e095f2da1ffc9e5c60b7abe33960291ff70609 - 31468.js
CERBER RANSOMWARE SAMPLES:
- SHA256 hash: 67f49ece27415c9646ddf5aa3037d67e28b2252d0d2c577e7e89c5ec2154b0bc
File size: 426,666 bytes
File description: Cerber from momendfakol[.]top on 2017-05-12
- SHA256 hash: cf262a9236eaf5230c219845823f36fd8c8e8b77ba882c34ce38a5087539cf71
File size: 479,913 bytes
File description: Cerber from unityqueryzouneasty[.]pw on 2017-05-12
IMAGES
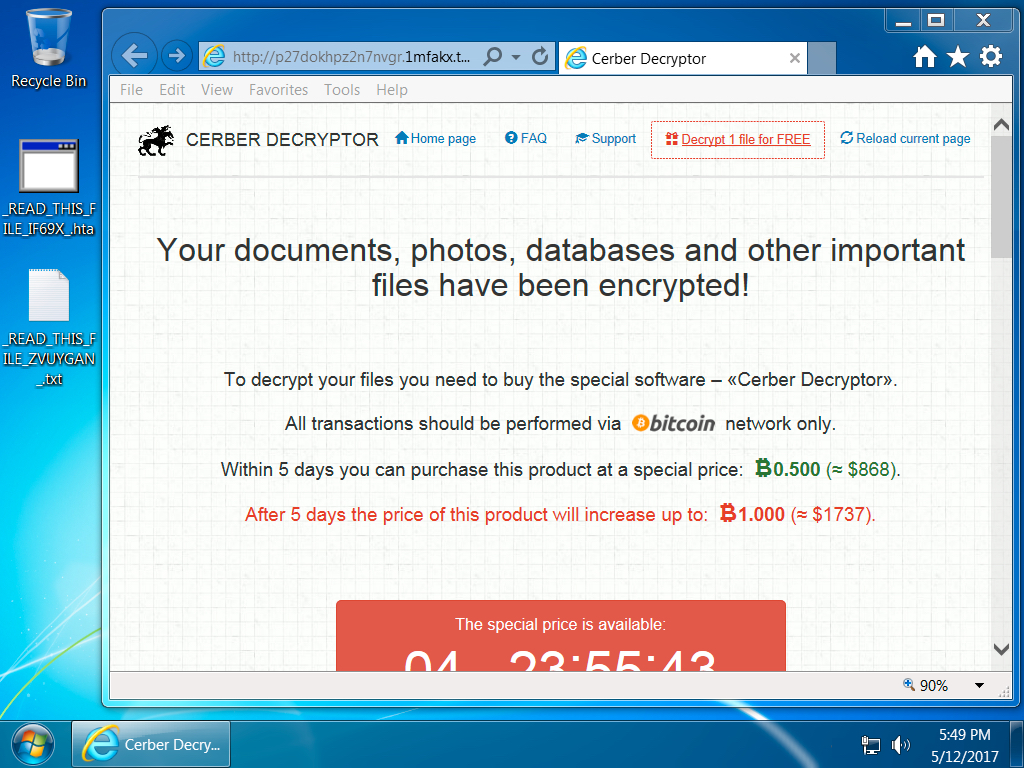
Shown above: Desktop of a Windows host infected with one of today's Cerber ransomware samples.
Click here to return to the main page.
