2017-05-16 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-16-Hancitor-infection-with-ZLoader.pcap.zip 11.8 MB (11,831,623 bytes)
- 2017-05-16-Hancitor-infection-with-ZLoader.pcap (12,783,182 bytes)
- 2017-05-16-Hancitor-malspam-2-examples.zip 2.5 kB (2,546 bytes)
- 2017-05-16-Hancitor-malspam-182526-UTC.eml (2,082 bytes)
- 2017-05-16-Hancitor-malspam-184711-UTC.eml (2,076 bytes)
- 2017-05-16-malware-from-Hancitor-infection.zip 256.2 kB (256,158 bytes)
- BNE3C9.tmp (207,872 bytes)
- UPS_Label_harold.smithee.doc (204,800 bytes)
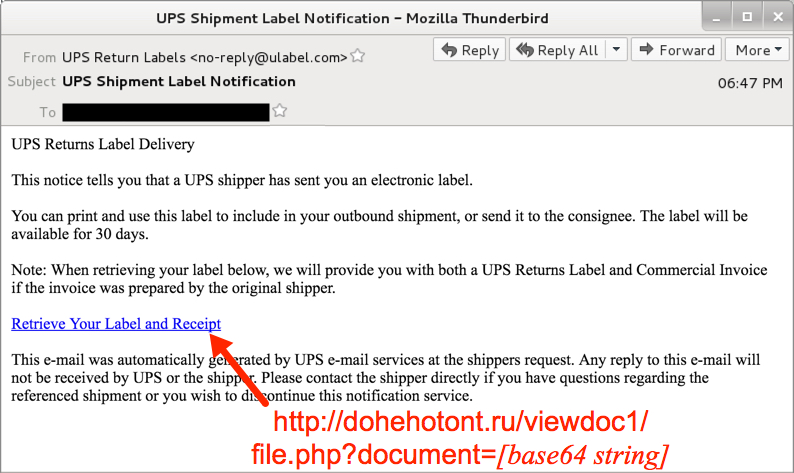
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date: Tuesday 2017-05-16
- Subject: UPS Shipment Label Notification
- From: "UPS Return Labels" <no-reply@ulabel[.]com>
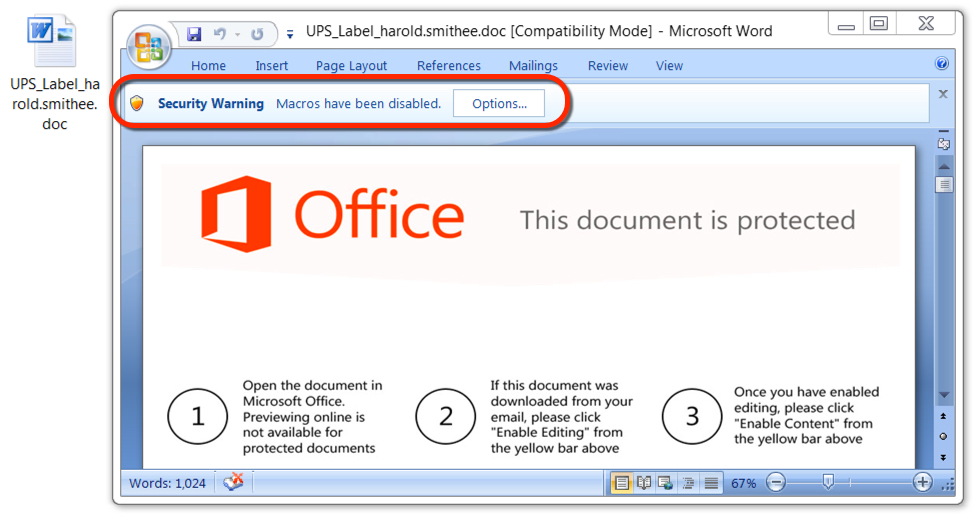
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
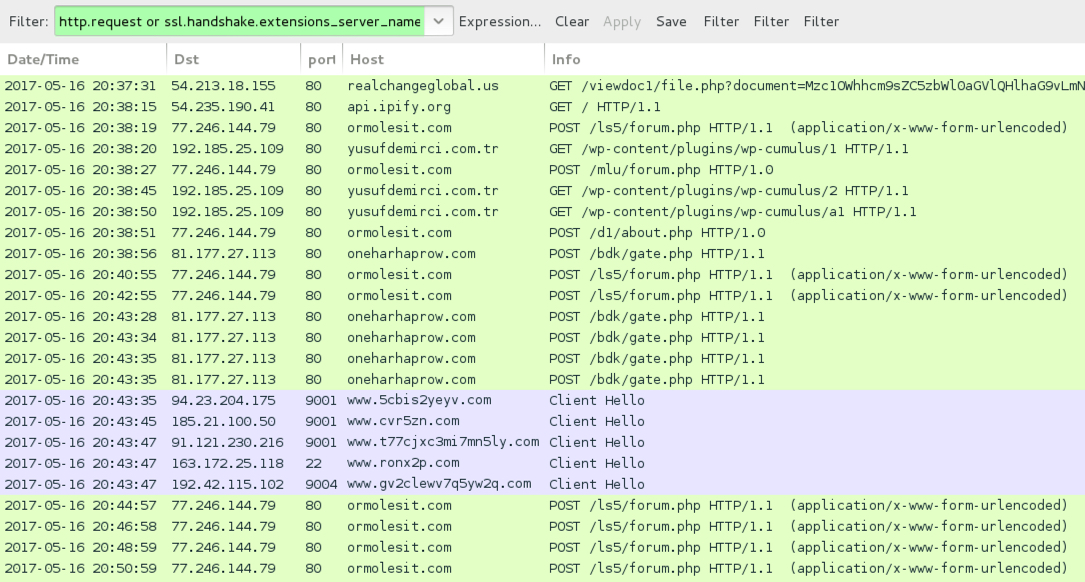
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- 54.213.18[.]155 port 80 - REALCHANGEGLOBAL[.]US - GET /viewdoc1/file.php?document=[base64 string]
- 54.213.18[.]155 port 80 - dohehotont[.]ru - GET /viewdoc1/file.php?document=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- UPS_Label_[username].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 77.246.144[.]79 port 80 - ormolesit[.]com - POST /ls5/forum.php
- 77.246.144[.]79 port 80 - ormolesit[.]com - POST /mlu/forum.php
- 77.246.144[.]79 port 80 - ormolesit[.]com - POST /d1/about.php
- 192.185.25[.]109 port 80 - yusufdemirci[.]com[.]tr - GET /wp-content/plugins/wp-cumulus/1
- 192.185.25[.]109 port 80 - yusufdemirci[.]com[.]tr - GET /wp-content/plugins/wp-cumulus/2
- 192.185.25[.]109 port 80 - yusufdemirci[.]com[.]tr - GET /wp-content/plugins/wp-cumulus/a1
- 81.177.27[.]113 port 80 - oneharhaprow[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 1014b0191af345644fb1d079438aeeefd33b54a4119f7f26d76b1b2c294cca61
File name: UPS_Label_harold.smithee.doc
File size: 204,800 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 19352237f417ba7e63855fbdfcd42084f92848a16138b9db555f076dab741c57
File location: C:\Users\[username]\AppData\Local\Temp\BNE3C9.tmp
File size: 207,872 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
