2017-05-17 - EITEST HOEFLERTEXT POPUPS SEND SPORA RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 22017-05-17-EITest-HoeflerText-popups-send-Spora-ransomware-3-pcaps.zip 408.1 kB (408,110 bytes)
- 2017-05-17-1st-run-EITest-HoeflerText-popup-sends-Spora-ransomware.pcap (371,305 bytes)
- 2017-05-17-2nd-run-EITest-HoeflerText-popup-sends-Spora-ransomware.pcap (347,065 bytes)
,- 2017-05-17-3rd-run-EITest-HoeflerText-popup-sends-Spora-ransomware.pcap (372,941 bytes)
- 2017-05-17-EITest-HoeflerText-popups-and-Spora-ransomware-files.zip 370.6 kB (370,637 bytes)
- 2017-05-17-1st-run-page-from-intothebluefishing_com-with-injected-EITest-script-for-HoeflerText-popup.txt (128,363 bytes)
- 2017-05-17-1st-run-Font_Chrome.exe (187,904 bytes)
- 2017-05-17-2nd-run-page-from-intothebluefishing_com-with-injected-EITest-script-for-HoeflerText-popup.txt (128,364 bytes)
- 2017-05-17-2nd-run-Font_Chrome.exe (184,320 bytes)
- 2017-05-17-3rd-run-page-from-intothebluefishing_com-with-injected-EITest-script-for-HoeflerText-popup.txt (128,337 bytes)
- 2017-05-17-3rd-run-Font_Chrome.exe (184,320 bytes)
- HELP_Xkj1VYCu.html.txt (68 bytes)
NOTES:
- My thanks to @malwrhunterteam for contacting me about the recent changes in Spora.
- My thanks to also @killamjr who tweeted about the compromised website used in this traffic (link).
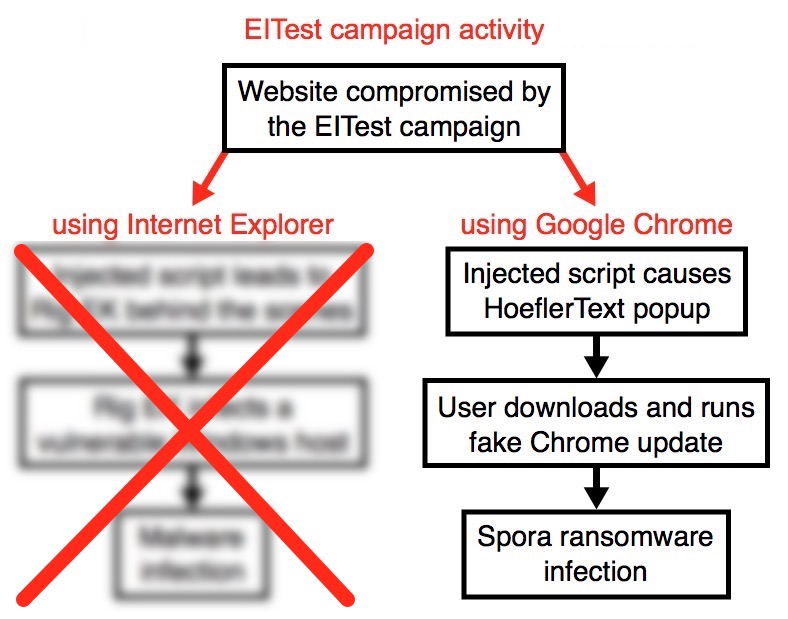
Shown above: Not seeing any Rig EK from the EITest campaign, but we're still seeing HoeflerText popups.
TRAFFIC
- 173.255.128[.]189 port 80 - www.intothebluefishing[.]com - GET / [compromised website]
- 176.223.207[.]41 port 80 - clinicalpsychology.psiedu.ubbcluj[.]ro - GET /who.php [URL to download Spora ransomware]
- 190.115.19[.]190 port 80 - 190.115.19[.]190 - GET / [redirect from decryption instructions HTML file dropped to infected host]
- 190.115.19[.]190 port 80 - spora[.]biz - GET / [The domain to decrypt your encrypted files]
MALWARE
SPORA RANSOMWARE SAMPLE 1 OF 3:
- SHA256 hash: b4f085f6d2fcb419ed28bc6f4836c842bb251eb6c00cfa8099ebcef905e51a9c
File size: 187,904 bytes
File name: Font_Chrome.exe
SPORA RANSOMWARE SAMPLE 2 OF 3:
- SHA256 hash: e28dca64178f43907eda9f04823066769ab233bc1b0719aab9d7c90b7451dd7a
File size: 184,320 bytes
File name: Font_Chrome.exe
SPORA RANSOMWARE SAMPLE 3 OF 3:
- SHA256 hash: 5a58e4a4910fbbb8092af231cba2e7cf9f9c0acf6ec88ccb7e0566fcf7b03415
File size: 184,320 bytes
File name: Font_Chrome.exe
IMAGES
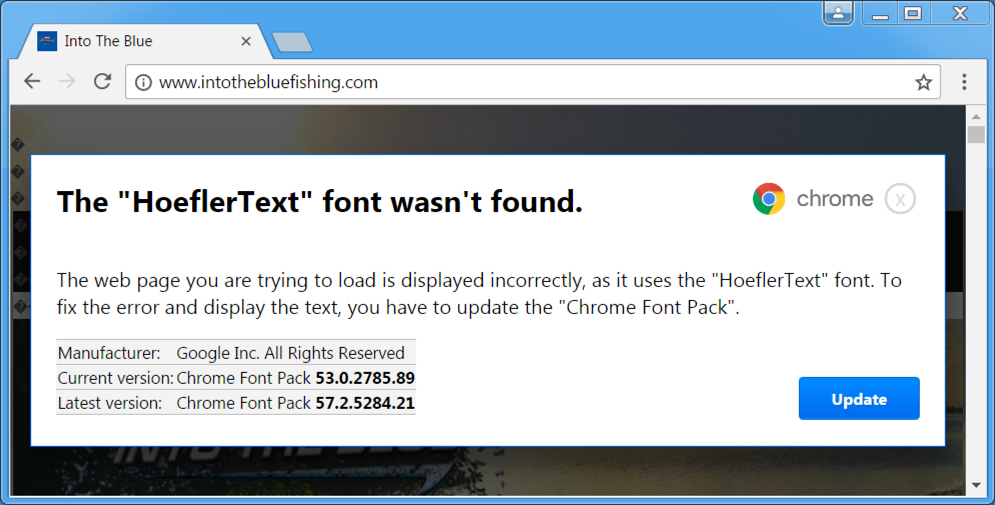
Shown above: HoflerText popup from compromised website when viewing in Chrome.
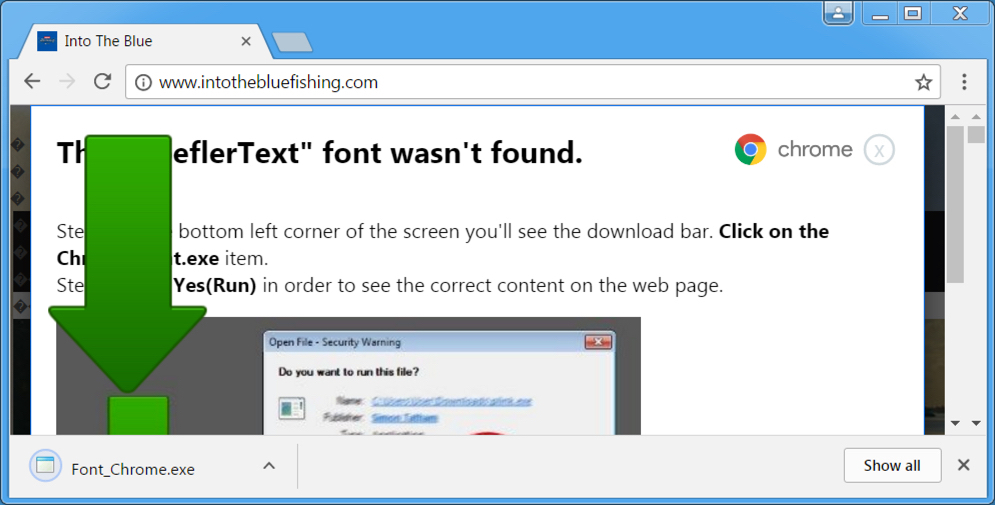
Shown above: Downloading Font_Chrome.exe (which is actually Spora ransomware).
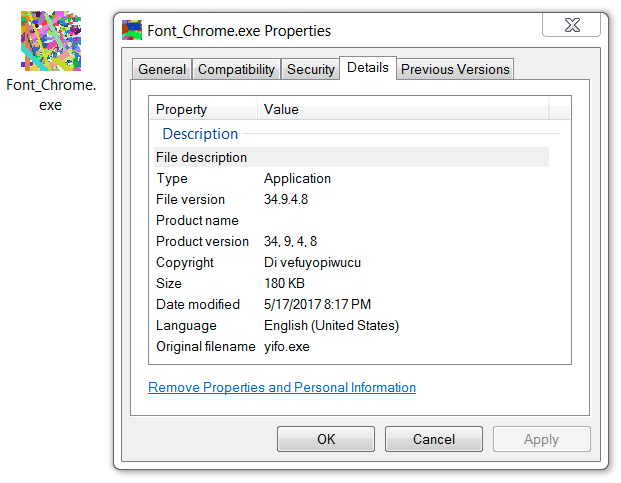
Shown above: Here's some metadata on the Spora ransomware binary.
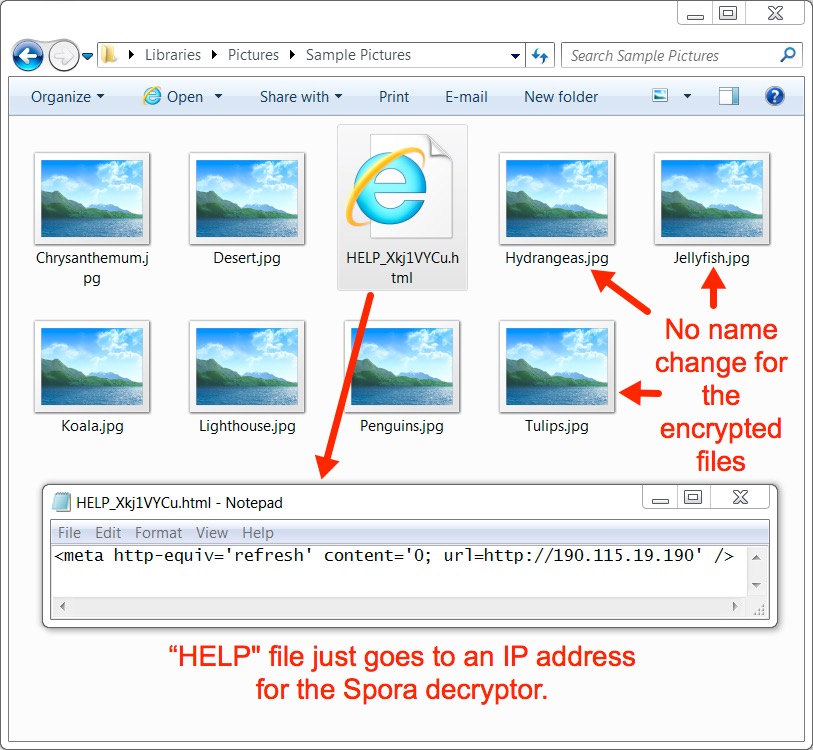
Shown above: The decryption instructions HELP_Xkj1VYCu.html only had one line that redirected to an IP address.
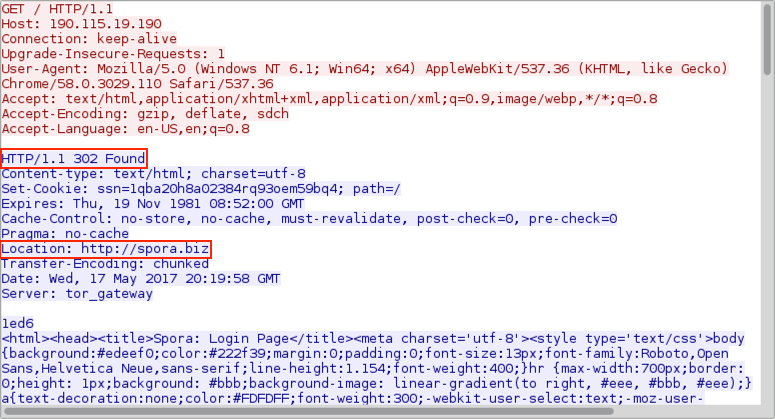
Shown above: The IP address redirects (or is) the Spora[.]biz decryptor site.
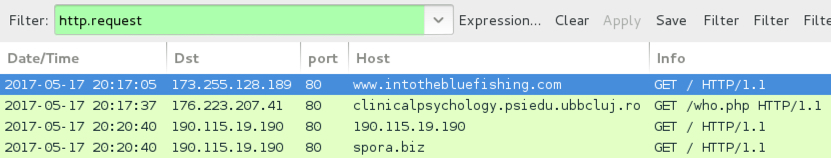
Shown above: Traffic from the infection filtered in Wireshark.
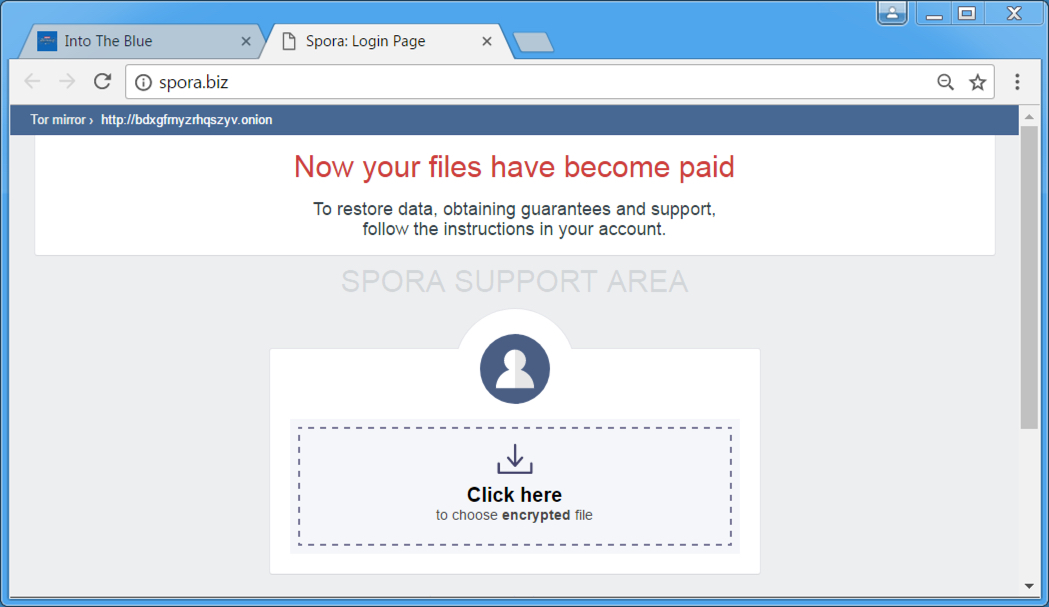
Shown above: Initial Spora decryptor screen at Spora[.]biz.
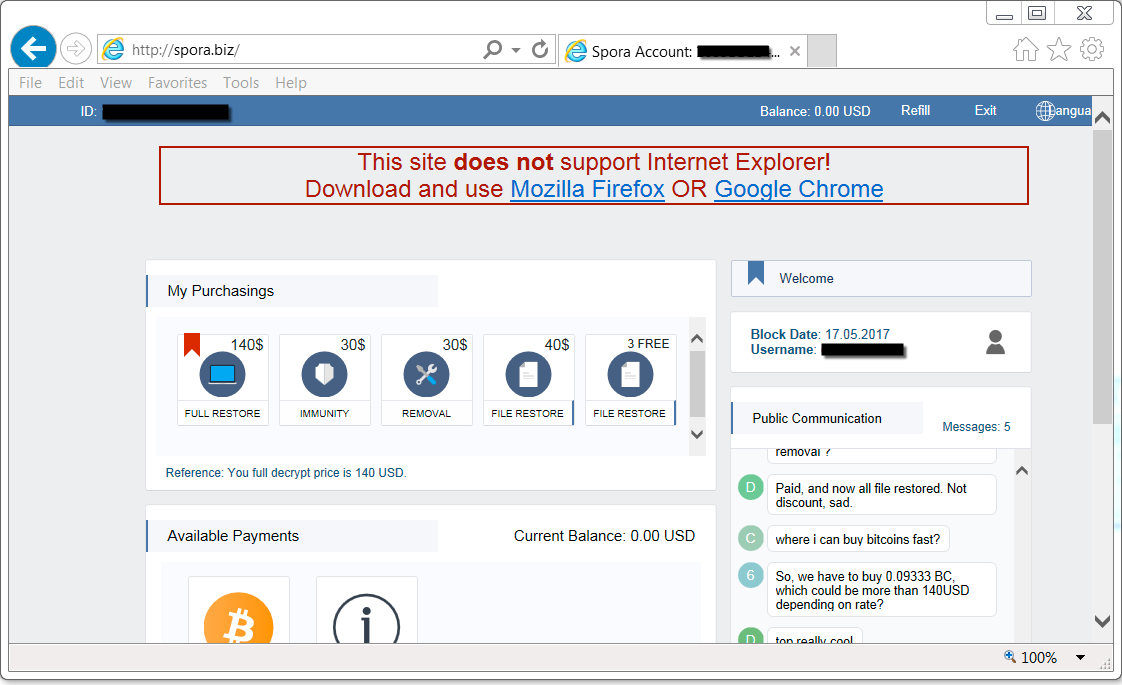
Shown above: After you drag and drop an encrypted file to the previous screen, you'll get the Spora decryptor page.
Click here to return to the main page.