2017-05-22 - JAFF RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-22-Jaff-ransomware-traffic.pcap.zip 147.3 kB (147,259 bytes)
- 2017-05-22-Jaff-ransomware-malspam-tracker.csv.zip 1.5 kB (1,462 bytes)
- 2017-05-22-Jaff-ransomware-emails-and-malware.zip 2.4 MB (2,427,044 bytes)
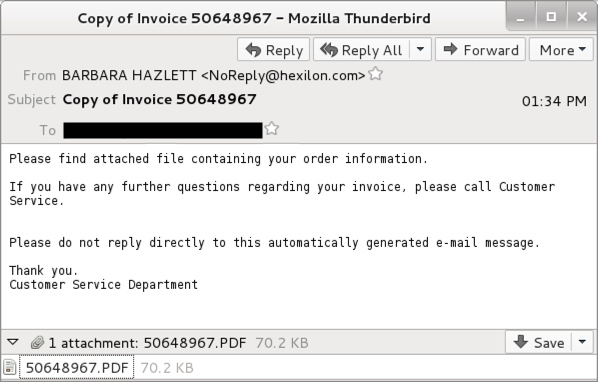
Shown above: An example of the emails.
12 EMAIL EXAMPLES:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME
- 2017-05-22 13:34:31 UTC -- BARBARA HAZLETT <NoReply@hexilon[.]com> -- Copy of Invoice 50648967 -- 50648967.PDF
- 2017-05-22 13:42:35 UTC -- BARTON HENDON <NoReply@noriet[.]pl> -- Copy of Invoice 96259119 -- 96259119.PDF
- 2017-05-22 13:49:43 UTC -- JAVIER SALTER <NoReply@jmclutherie[.]com> -- Copy of Invoice 58159387 -- 58159387.PDF
- 2017-05-22 13:54:02 UTC -- IRMA CLARK <NoReply@emotionalclarity[.]co[.]uk> -- Copy of Invoice 14017976 -- 14017976.PDF
- 2017-05-22 14:09:25 UTC -- MONA HOUNDSOME <NoReply@MathFileFolderGames[.]com> -- Copy of Invoice 05346468 -- 05346468.PDF
- 2017-05-22 14:35:59 UTC -- MAVIS HOWARD <NoReply@tezziessignshop[.]com> -- Copy of Invoice 64647384 -- 64647384.PDF
- 2017-05-22 14:45:46 UTC -- ALANA MACALISTER <NoReply@elecomptrade[.]com> -- Copy of Invoice 21397165 -- 21397165.PDF
- 2017-05-22 14:54:29 UTC -- ERIKA OF ROUMANIA <NoReply@inetobchod[.]cz> -- Copy of Invoice 85354849 -- 85354849.PDF
- 2017-05-22 14:58:43 UTC -- 1DEANA MINTAS <NoReply@racesalinaspeedway[.]com> -- Copy of Invoice 93059018 -- 93059018.PDF
- 2017-05-22 15:29:14 UTC -- SHELLEY MARKHAM <NoReply@cancianpavimenti[.]it> -- Copy of Invoice 87325061 -- 87325061.PDF
- 2017-05-22 15:59:26 UTC -- Minnie Gerry <gerry.darwin7234@hzndj[.]com> -- Document_9483142 -- nm.pdf
- 2017-05-22 15:59:50 UTC -- Minnie <minnie.sye17@greenvalleyelks[.]org> -- PDF_9807 -- nm.pdf
MALWARE
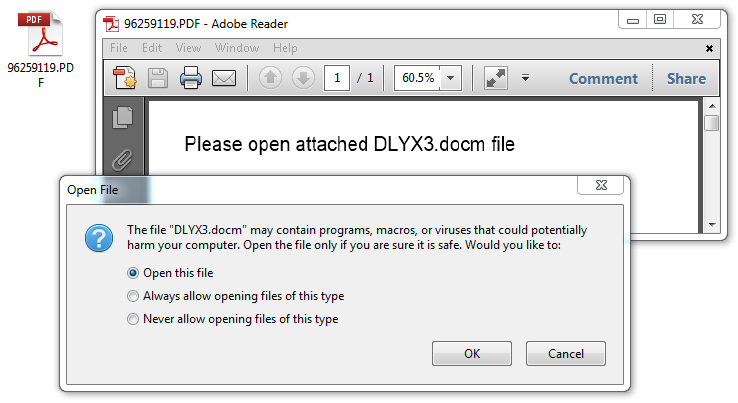
Shown above: As usual, the PDF attachment contains an embedded Word document with malicious macros.
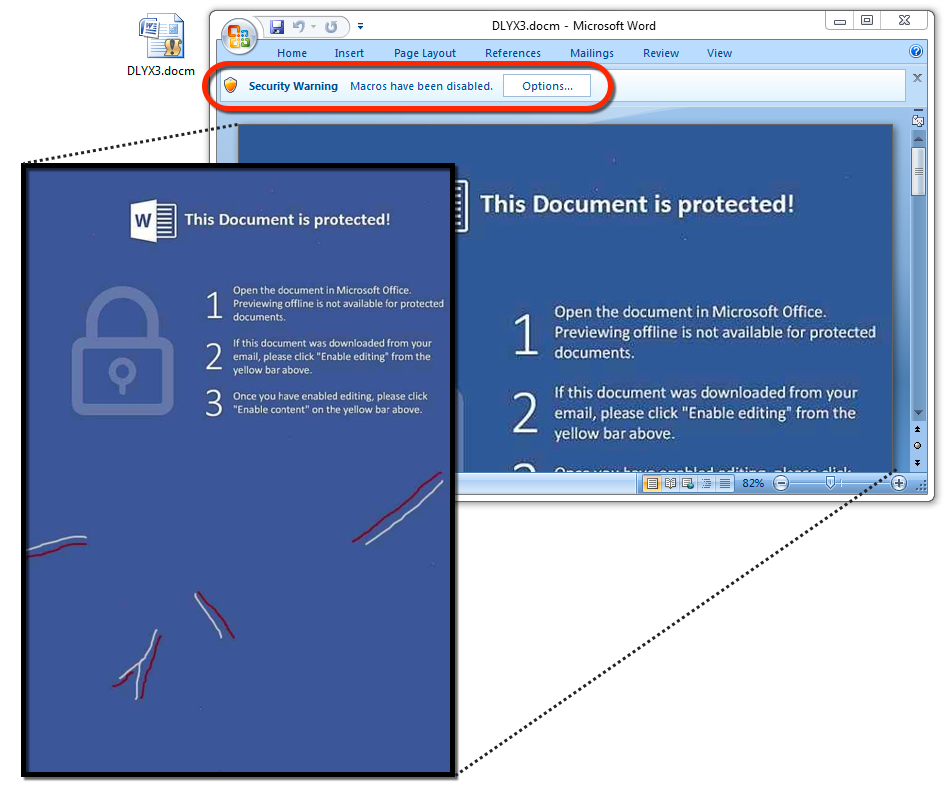
Shown above: Started noticing marks in the bottom half of the images in these Word documents.
SHA256 HASHES FOR THE PDF ATTACHMENTS:
- 10321320369049daf9e10a898d44d489c5c1eba376c4ee9144257e2285634aa8
- 11f02f894bd5773bf5a6b6da6336881d30f525f16bfc938c42d6e305de6b2f46
- 476d6c030f56b9727abd5da5322efb08063a50e6b71562fb40eb779b1d3689ff
- 4967779ed93e178ad3e5d895a434f4866f77ddc3df9e9f3c0c69d9c6419835d6
- 6df458c9e52d9b104f8419a5bdfe320730b07642af007972b0fa72200e4949ad
- 7b007efc9a703bbaeebd9bc443efb9f8c6300c3f1480a040a81a2120dc5c97cb
- 7cd7a975ac42b409d97161c5fb3e100552bc5c2eaeb6e196b45e2a55c5086b17
- 9e31d8584c3d281bb264e6cccd38eb25ec8d1b7a11af85b2e42c335a06c78bfd
- d36aa76aa38e01bdc5d1ce3c83bffb402e0b8e7ff5200e79ca700864ac9abdee
- e08a6331873d1aea6d6ec8178d550a56a98895fb268c430948af9bc1098a9762
- e1aab160d59b83a9b62dc2609c2d55b7f07387f4b84041c18efe068e05f9b9dd
SHA256 HASHES FOR THE EMBEDDED WORD DOCUMENTS:
- 2fe146a9b8857e4c8fb8feb41952ec58c7bfc2c4c8fba2ac3c8bce28ce8bd468 - DLYX3.docm
- 43c96848e38431c5b9d90622808733cfe011e6b1a04b0c8f5e4e50a205ea95f9 - LOASWA.docm
- 5406916f81e8c20f61d0ff8f3242642d6d04ffb0c0c2d351bfd166aa3b62a44b - VWJEPFUGN.docm
- 56db9d583df62c240576b372e0ddfaadd8adb2e40d0af974d8b7cd33bc06443a - VNNCTVG.docm
- 8f04b9cd61543f8211285cd72f3a73d55cc2035da5e9abd44ec82f6a6b820ba6 - XJ3ZKWN.docm
- a358fb67469ea758d100fe42423b6b8c1085b47efa701e441fc20af11dc9d307 - BMUC3LI.docm
- a5563ae47b4aefdc8ce88dc82bd920446abdd7bcdf9c0c0196ee534aeebd2c5b - HMFQD7F.docm
- b657ee84e4358187091ae49dbecade191418624d0ec1958524fc9d2740b0d623 - WBLYJOFBR.docm
- cbd9fc0ee67a1edd2511773cb013d2db55f4f42c15b1fe37b417bf096ca7f029 - HC5TMRFS.docm
- cc18fd9d51b01cd3dc5f6a07403a933baa8ec648e0b65835bf10a8efdc583217 - LXC9UU.docm
- f3a3299f3ff1e51b5d52c99c78df7a6a585c1a2686a8468a3dfacde9a6fe6b4e - SOBFSGAUV.docm
JAFF RANSOMWARE SAMPLE:
- SHA256 hash: 3105bf7916ab2e8bdf32f9a4f798c358b4d18da11bcc16f8f063c4b9c200f8b4
File size: 184,320 bytes
File location: C:\Users\[username]\AppData\Local\Temp\buzinat8.exe
TRAFFIC
URLS FROM THE WORD MACROS TO DOWNLOAD JAFF RANSOMWARE:
- brotexxshferrogd[.]net - GET /af/jhg6fgh
- datadunyasi[.]com - GET /jhg6fgh
- dewatch[.]de - GET /jhg6fgh
- electua[.]org - GET /jhg6fgh
- essensworld[.]cz - GET /jhg6fgh
- everstruct[.]com[.]au - GET /jhg6fgh
- f1toh1[.]com - GET /jhg6fgh
- herrossoidffr6644qa[.]top - GET /af/jhg6fgh
- joesrv[.]com - GET /jhg6fgh
- knowyourmarketing[.]com - GET /jhg6fgh
- pattumalamatha[.]com - GET /jhg6fgh
- primary-ls[.]ru - GET /jhg6fgh
- tayangfood[.]com - GET /jhg6fgh
- tipografia[.]by - GET /jhg6fgh
- way2lab[.]com - GET /jhg6fg
JAFF RANSOMWARE POST-INFECTION TRAFFIC:
- 217.29.63[.]199 port 80 trollitrancessions[.]net - GET /a5/
- rktazuzi7hbln7sy[.]onion - Tor domain for Jaff Decryptor (same as the last few times)
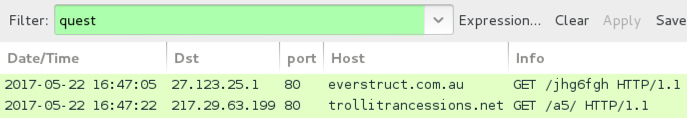
Traffic from the infection filtered in Wireshark.
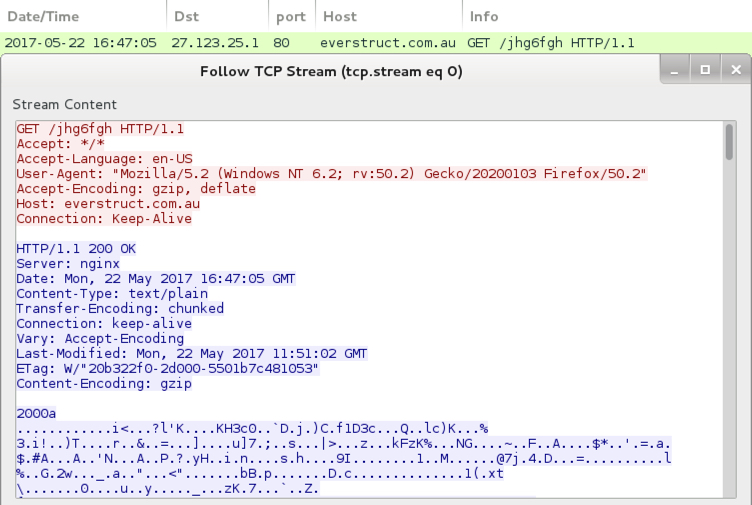
HTTP request for the Jaff ransomware.
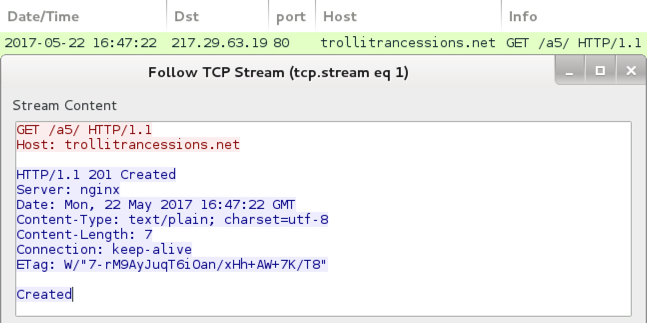
Post-infection traffic from the infected Windows host.
IMAGES
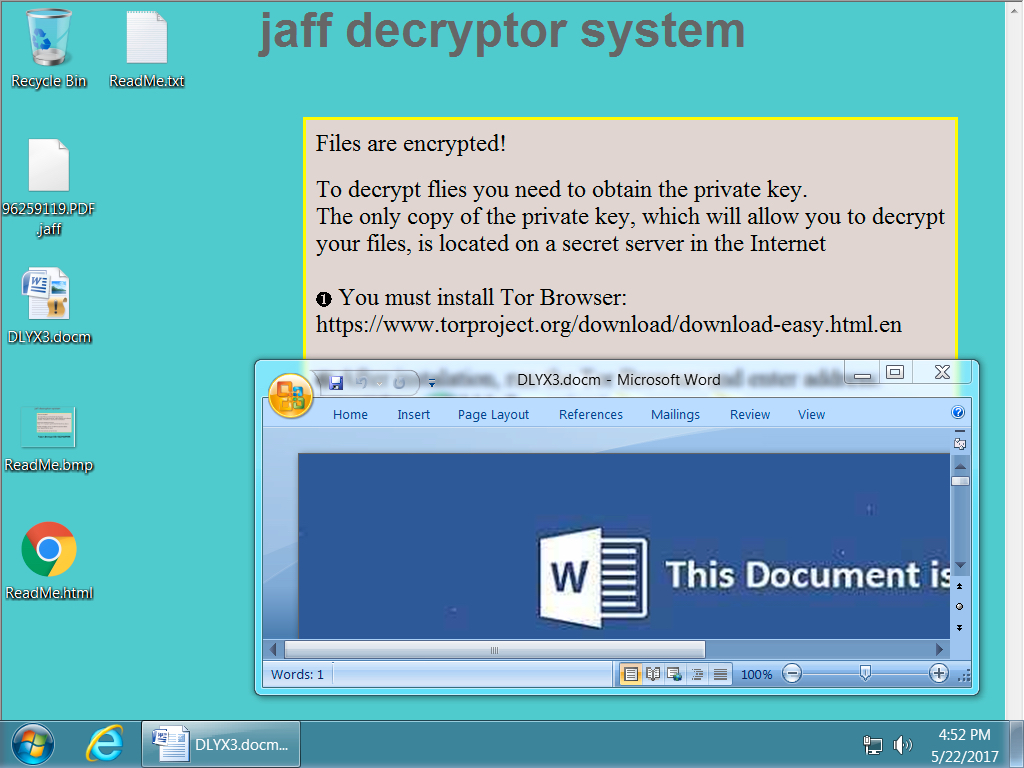
Shown above: Desktop of an infected Windows host.
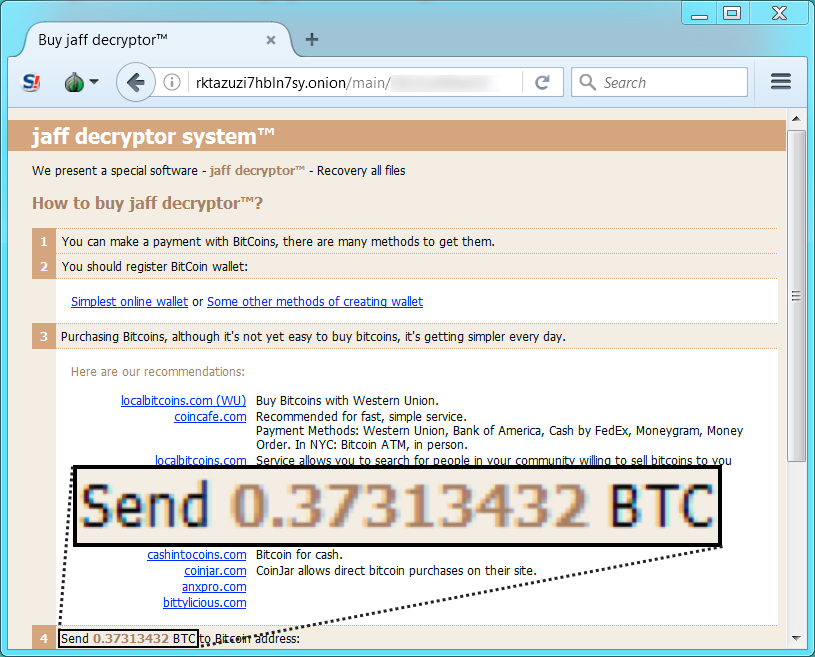
Shown above: Going to the Jaff Decryptor.
Click here to return to the main page.
