2017-05-25 - JAFF RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-25-Jaff-ransomware-traffic.pcap.zip 172.2 kB (172,152 bytes)
- 2017-05-25-Jaff-ransomware-malspam-tracker.csv.zip 0.8 kB (807 bytes)
- 2017-05-25-Jaff-ransomware-emails-and-malware.zip 858.1 kB (858,132 bytes)
NOTES:
- More information on this campaign can be found at: https://isc.sans.edu/forums/diary/Jaff+ransomware+gets+a+makeover/22446/
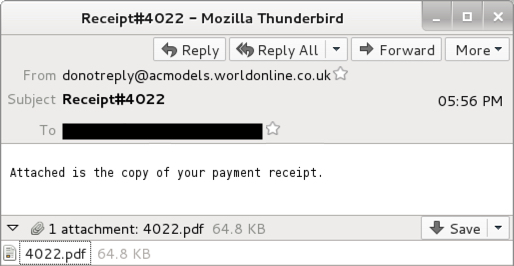
Shown above: An example of the emails.
4 EMAIL EXAMPLES:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME
- 2017-05-25 12:28:25 UTC -- donotreply@corepartners[.]co[.]uk -- Receipt_74332 -- 74332.pdf
- 2017-05-25 12:35:12 UTC -- donotreply@aero-media[.]co[.]uk -- Receipt#4163 -- 4163.pdf
- 2017-05-25 12:56:43 UTC -- donotreply@cukierman[.]com[.]br -- Payment 2317 -- 2317.pdf
- 2017-05-25 17:56:09 UTC -- donotreply@acmodels.worldonline[.]co[.]uk -- Receipt#4022 -- 4022.pdf
MALWARE
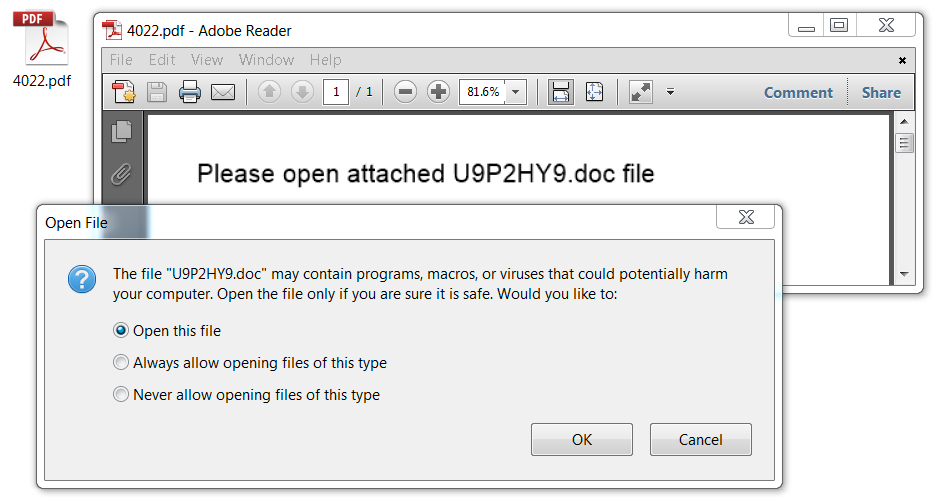
Shown above: As usual, the PDF attachment contains an embedded Word document with malicious macros.
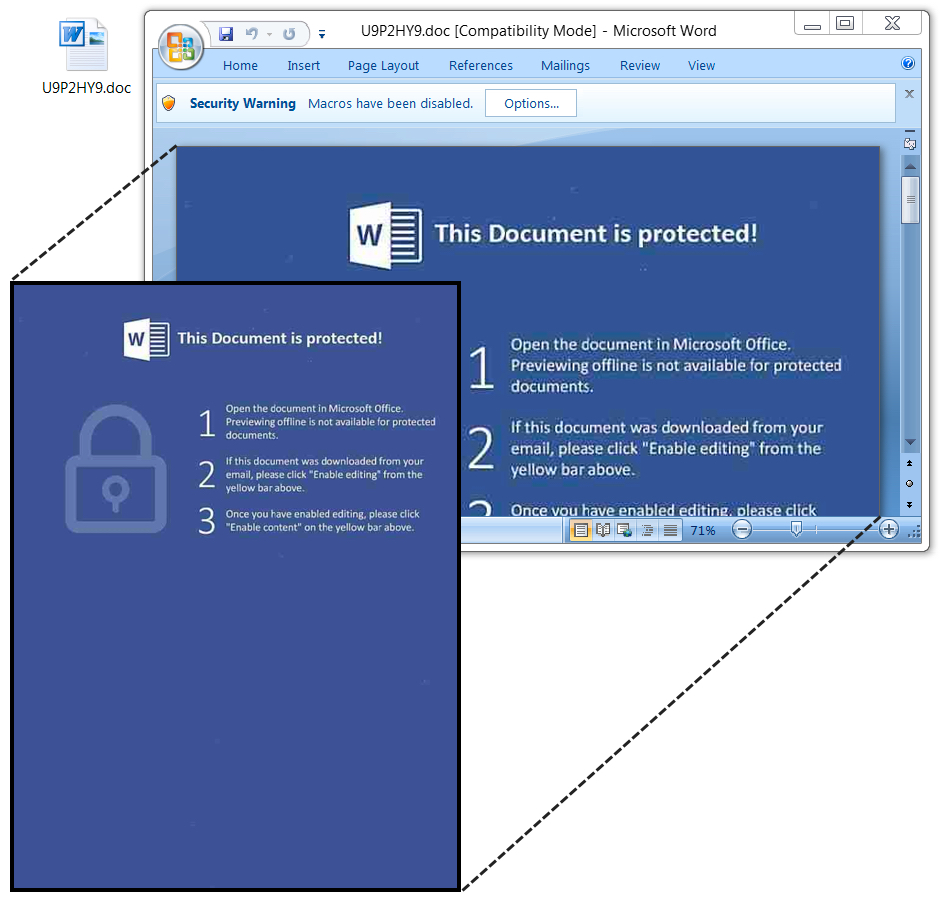
Shown above: No marks today in the bottom half of the images in these Word documents.
SHA256 HASHES FOR THE PDF ATTACHMENTS:
- 0237ae2520a441751b224d56aa776ba3758d07073b5164c5174ea2e4990f8462 - 4163.pdf
- 0d33a0f086710c812794dc20c6057d422c74c582b6bb737b3c3ade0fd369c801 - 2317.pdf
- 454d5ec8cac7915ab1b02852007d28a65a5076fbc28e5b6ffbb6bca290596a9e - 4022.pdf
- 4f332611fe30a155fcd73aff87135035436196acbb8ccf219efdc8a3c3b7ae14 - 74332.pdf
SHA256 HASHES FOR THE EMBEDDED WORD DOCUMENTS:
- 549acec1f738a40d4097ba096ff2827bc76481b3f4dd73ef0fab437eb476be29 - U9P2HY9.doc
- 8abb70a36f99ee613f65535aeaaf28a3d0e79df7129110f4f9ef50833f664354 - NCVH2PL.doc
- 9383ade91f05af3f350831ac76ba218e42fc033964753e6db71c0fded5b0b832 - WXEVIR.doc
- c47090ad7c20f9cafee4e162985f6a2d8b60c4e3b3327d532e70a167b8a1a9e8 - W2X2PEW.doc
JAFF RANSOMWARE SAMPLE:
- SHA256 hash: 2cc1d8edc318e0e09aad6afbc48999980f8e39e54734bca4c1a95c7b5db39569
File size: 217,088 bytes
File location: C:\Users\[username]\AppData\Local\Temp\bruhadson8.exe
TRAFFIC
URLS FROM THE WORD MACROS TO DOWNLOAD JAFF RANSOMWARE:
- better57toiuydof[.]net - GET /af/TrfHn4
- blackstoneconsultants[.]com - GET /TrfHn4
- derossigroup[.]it - GET /TrfHn4
- dianagaertner[.]com - GET /TrfHn4
- hunter[.]cz - GET /TrfHn4
- youtoolgrabeertorse[.]org - GET /af/TrfHn4
JAFF RANSOMWARE POST-INFECTION TRAFFIC:
- 34.225.214[.]20 port 80 dorobratiohdtyszxwk[.]com - GET /a5/
- rktazuzi7hbln7sy[.]onion - Tor domain for Jaff Decryptor (same as the last few times)
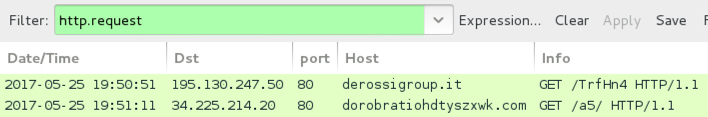
Traffic from the infection filtered in Wireshark.
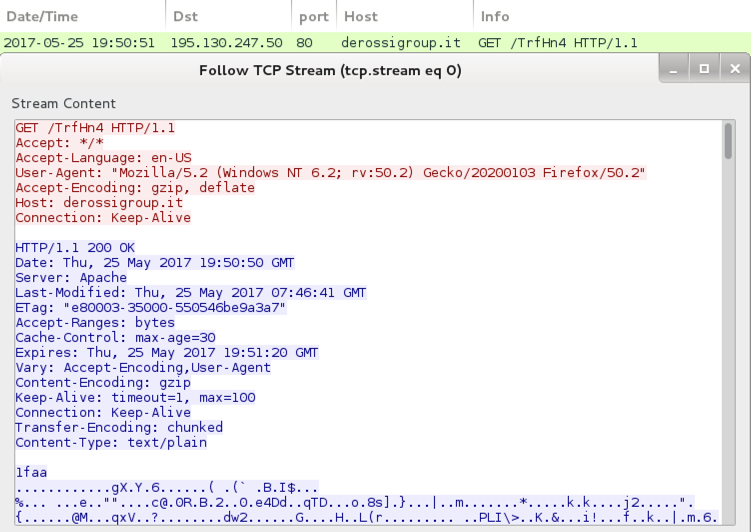
HTTP request for Jaff ransomware.
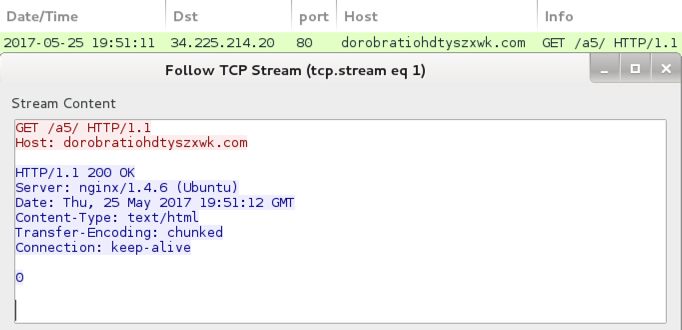
Post-infection traffic from the infected Windows host.
IMAGES
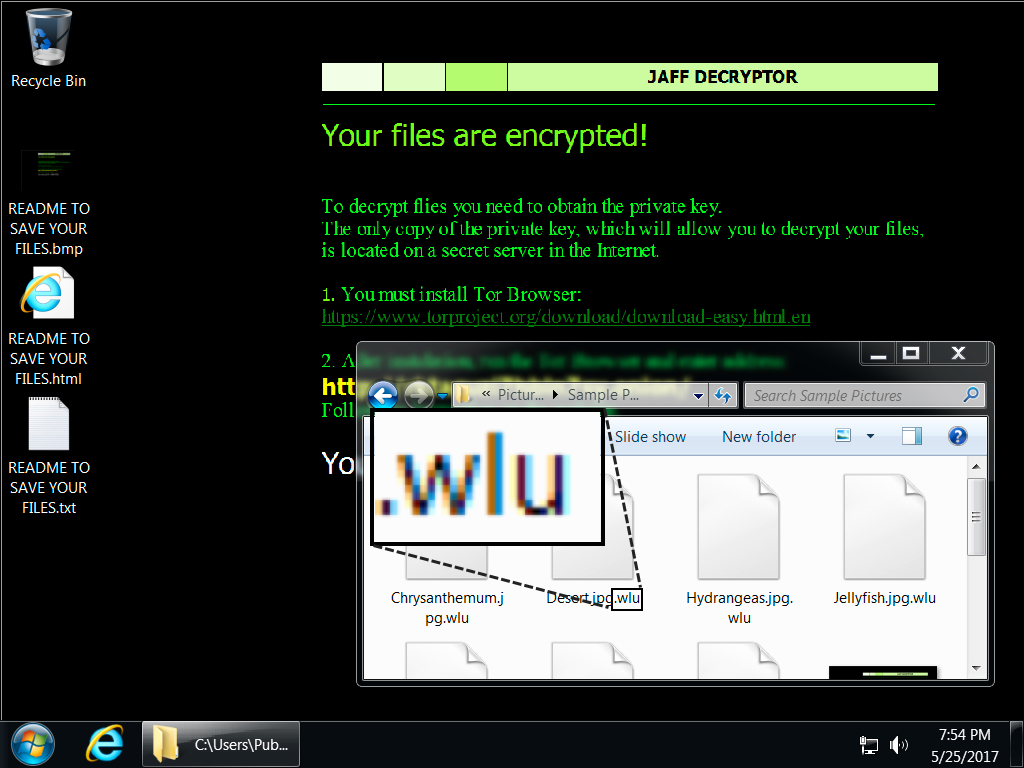
Shown above: Desktop of an infected Windows host.
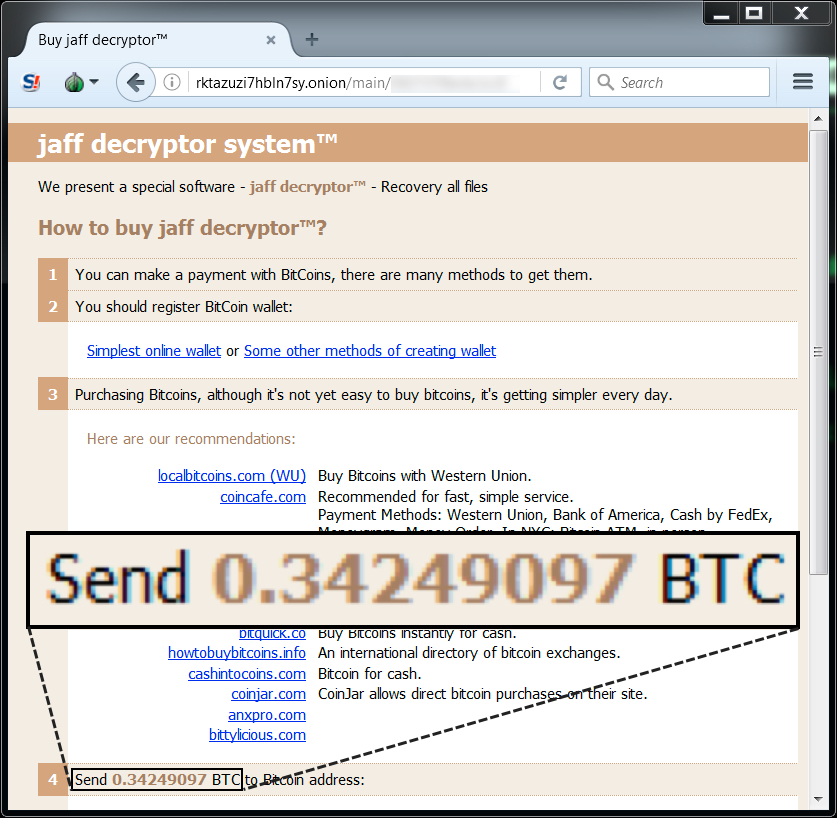
Shown above: Going to the Jaff Decryptor.
Click here to return to the main page.
