2017-05-30 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-30-Hancitor-infection-with-ZLoader.pcap.zip 12.7 MB (12,661,044 bytes)
- 2017-05-30-Hancitor-infection-with-ZLoader.pcap (13,200,366 bytes)
- 2017-05-30-Hancitor-malspam-6-examples.zip 17.3 kB (17,306 bytes)
- 2017-05-30-Hancitor-malspam-1501-UTC.eml (13,938 bytes)
- 2017-05-30-Hancitor-malspam-1505-UTC.eml (13,907 bytes)
- 2017-05-30-Hancitor-malspam-1554-UTC.eml (13,935 bytes)
- 2017-05-30-Hancitor-malspam-1602-UTC.eml (13,946 bytes)
- 2017-05-30-Hancitor-malspam-1611-UTC.eml (13,943 bytes)
- 2017-05-30-Hancitor-malspam-1612-UTC.eml (13,936 bytes)
- 2017-05-30-malware-from-Hancitor-infection.zip 238.5 kB (238,523 bytes)
- BN315C.tmp (176,640 bytes)
- Fedex_invoice_yahoo.doc (184,832 bytes)
NOTES:
- Saw two tweets about this activity. One was from @james_inthe_box here, and one was from @peterkruse here.
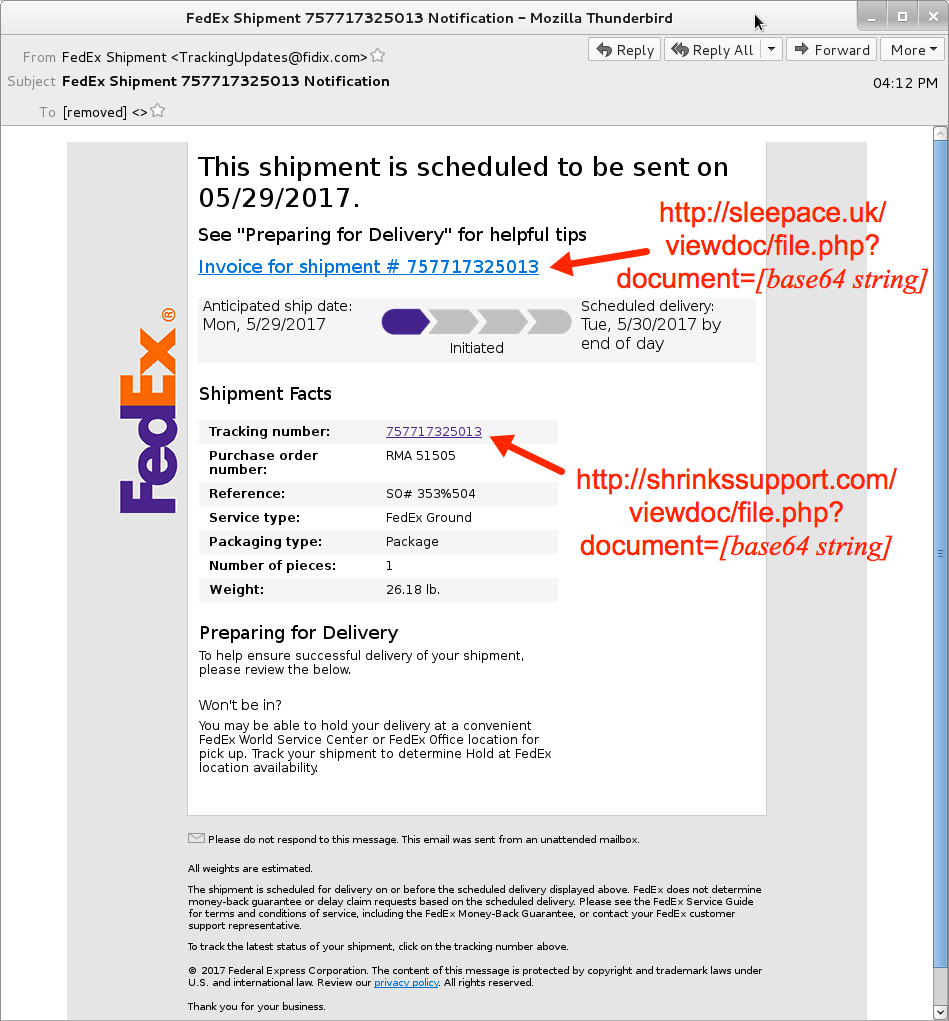
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date: Tuesday 2017-05-30 as early as 15:01 UTC through at least 16:12 UTC
- From: "FedEx Shipment" <TrackingUpdates@fidix[.]com>
- Subject: FedEx Shipment 754154562476 Notification
- Subject: FedEx Shipment 783606525076 Notification
- Subject: FedEx Shipment 713510261570 Notification
- Subject: FedEx Shipment 735302540030 Notification
- Subject: FedEx Shipment 747130050208 Notification
- Subject: FedEx Shipment 757717325013 Notification
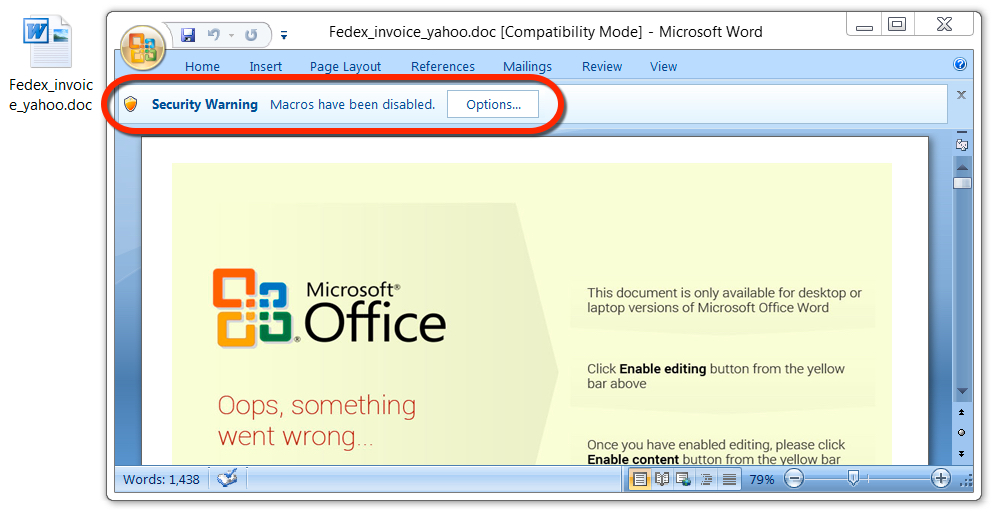
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
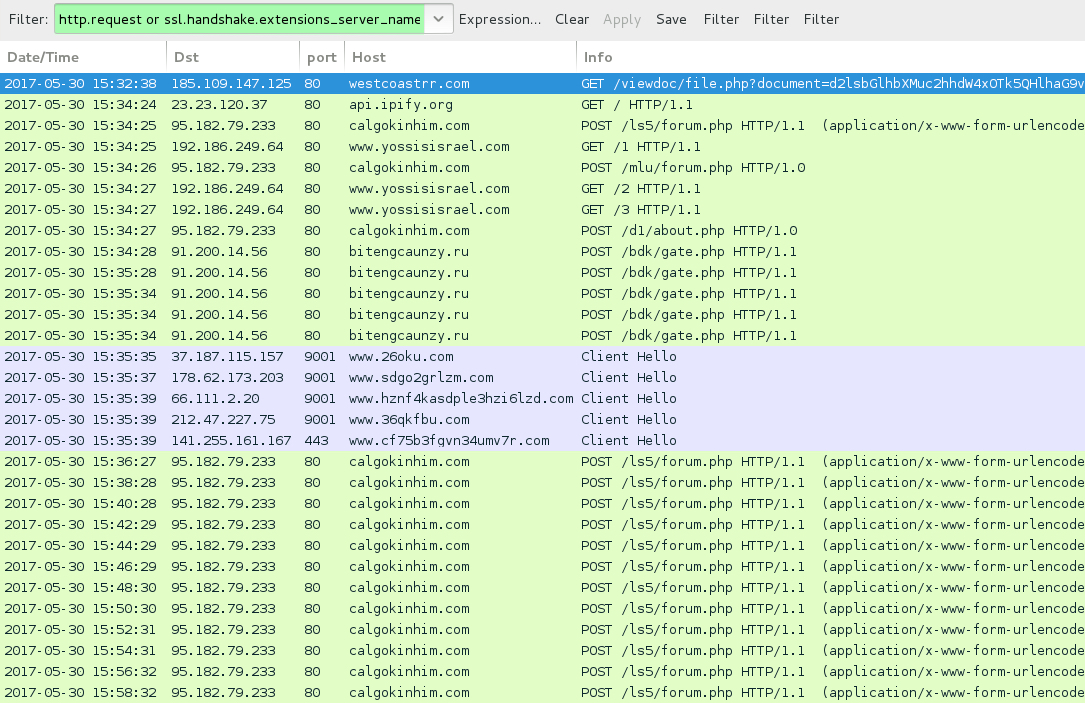
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- 185.109.147[.]125 port 80 - agaagents[.]com - GET /viewdoc/file.php?document=[base64 string]
- 185.109.147[.]125 port 80 - compshrinks[.]com - GET /viewdoc/file.php?document=[base64 string]
- 185.109.147[.]125 port 80 - shrinkssupport[.]com - GET /viewdoc/file.php?document=[base64 string]
- 185.109.147[.]125 port 80 - sleepace[.]uk - GET /viewdoc/file.php?document=[base64 string]
- 185.109.147[.]125 port 80 - WESTCOASTRR[.]COM - GET /viewdoc/file.php?document=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- Fedex_invoice_[recipient's email domain, minus the suffix].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 95.182.79[.]233 port 80 - calgokinhim[.]com - POST /ls5/forum.php
- 95.182.79[.]233 port 80 - calgokinhim[.]com - POST /mlu/forum.php
- 95.182.79[.]233 port 80 - calgokinhim[.]com - POST /d1/about.php
- 192.186.249[.]64 port 80 - www.yossisisrael[.]com - GET /1
- 192.186.249[.]64 port 80 - www.yossisisrael[.]com - GET /2
- 192.186.249[.]64 port 80 - www.yossisisrael[.]com - GET /3
- 91.200.14[.]56 port 80 - bitengcaunzy[.]ru - POST /bdk/gate.php
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 4ffbdd599dd5aa09f8c3f7e3db0b3c169ba38106db6192a59194e79ef60f957b
File name: Fedex_invoice_yahoo.doc
File size: 184,832 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 3a2f6291ceaee6be499e0a84d7fe931005e425fd21d25448fe5e38cc1fc37b81
File location: C:\Users\[username]\AppData\Local\Temp\BN315C.tmp
File size: 176,640 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
