2017-05-30 - RIG EK SENDS KOVTER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-30-Rig-EK-sends-Kovter-2-pcaps.zip 1.2 MB (1,158,477 bytes)
- 2017-05-30-Rig-EK-sends-Kovter-1st-run.pcap (680,294 bytes)
- 2017-05-30-Rig-EK-sends-Kovter-2nd-run.pcap (794,493 bytes)
- 2017-05-30-Rig-EK-and-Kovter-malware-and-artifacts.zip 788.6 kB (788,576 bytes)
- 2017-05-30-Rig-EK-artifact-o32.tmp-both-runs.txt (1,141 bytes)
- 2017-05-30-Rig-EK-flash-exploit-both-runs.swf (14,851 bytes)
- 2017-05-30-Rig-EK-landing-page-1st-run.txt (119,209 bytes)
- 2017-05-30-Rig-EK-landing-page-2nd-run.txt (119,022 bytes)
- 2017-05-30-Rig-EK-payload-Kovter-1st-run.exe (384,070 bytes)
- 2017-05-30-Rig-EK-payload-Kovter-2nd-run.exe (388,213 bytes)
NOTES:
- The initial URL in these pcaps is the final HTTP GET request in a probable malvertising chain of events leading to Rig EK.
- The same type of Kovter malware payload sent by this Rig EK was also seen from EITest Rig EK earlier today.
TRAFFIC
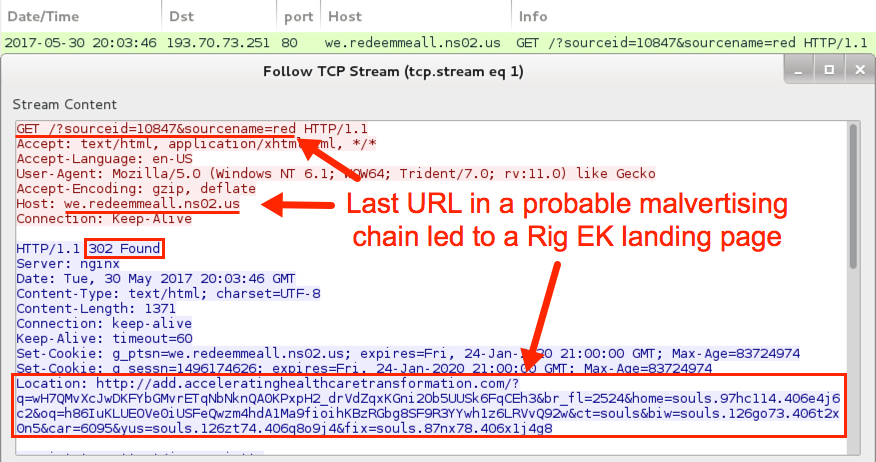
Shown above: Redirect to Rig EK.
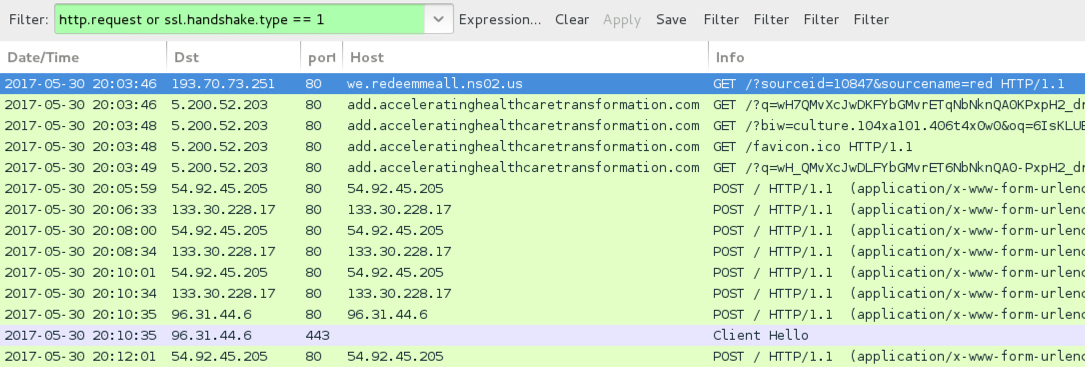
Shown above: Traffic from the 1st run filtered in Wireshark.
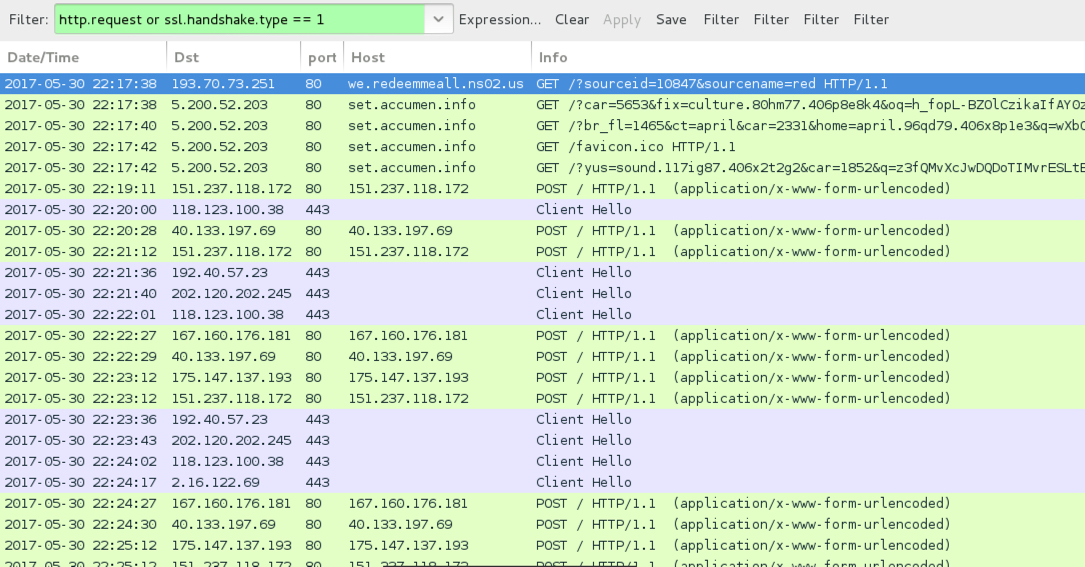
Shown above: Traffic from the 2nd run filtered in Wireshark.
REDIRECT AND RIG EK:
- 193.70.73[.]251 port 80 - we.redeemmeall.ns02.us - GET /?sourceid=10847&sourcename=red [final URL of a malvertising chain]
- 5.200.52[.]203 port 80 - add.acceleratinghealthcaretransformation[.]com - Rig EK (1st run)
- 5.200.52[.]203 port 80 - set.accumen[.]info - Rig EK (2nd run)
- 81.177.141[.]40 port 80 - add.akselegance[.]com - Rig EK (impromptu 3rd run)
KOVTER POST-INFECTION TRAFFIC - 1ST RUN:
- 54.92.45[.]205 port 80 - 54.92.45[.]205 - POST /
- 96.31.44[.]6 port 80 - 96.31.44[.]6 - POST /
- 133.30.228[.]17 port 80 - 133.30.228[.]17 - POST /
- 96.31.44[.]6 port 443 - HTTPS/SSL/TLS traffic
- Various IP addresses on TCP ports 443 and 8080 - Attempted TCP connections
KOVTER POST-INFECTION TRAFFIC - 2ND RUN:
- 40.133.197[.]69 port 80 - 40.133.197[.]69 - POST /
- 151.237.118[.]172 port 80 - 151.237.118[.]172 - POST /
- 167.160.176[.]181 port 80 - 167.160.176[.]181 - POST /
- 175.147.137[.]193 port 80 - 175.147.137[.]193 - POST /
- 2.16.122[.]69 port 443 - HTTPS/SSL/TLS traffic
- 118.123.100[.]38 port 443 - HTTPS/SSL/TLS traffic
- 192.40.57[.]23 port 443 - HTTPS/SSL/TLS traffic
- 202.120.202[.]245 port 443 - HTTPS/SSL/TLS traffic
- 76.8.251[.]242 port 2025 - HTTPS/SSL/TLS traffic
- 202.120.202[.]245 port 4343 - HTTPS/SSL/TLS traffic
- Various IP addresses on TCP ports 443 and 8080 - Attempted TCP connections
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: 8f43aec2986d0705134b6b4af7e745ade1dd48897b95dc7e3844520fa8f9cd18
- File size: 14,851 bytes
- File description: Rig EK Flash exploit seen on Tuesday 2017-05-30
MALWARE PAYLOAD (KOVTER) - 1ST RUN:
- SHA256 hash: d58e284f53366f2545816878942dafc3a0a14a1ab5d7abaeaf028d3ac80acfd8
- File size: 384,070 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\[random numbers and letters].exe
MALWARE PAYLOAD (KOVTER) - 2ND RUN:
- SHA256 hash: 57e90c503ffd9f990d892063b626527898952a0e7a95d4656e8439f63f7caf72
- File size: 388,213 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\[random numbers and letters].exe
OTHER IMAGES
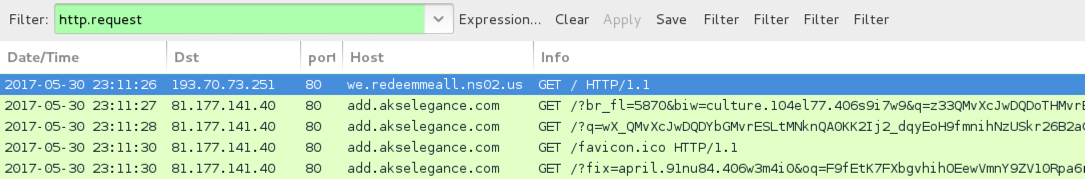
Shown above: A 3rd run proved I only needed the domain name, not the full URL to get Rig EK.
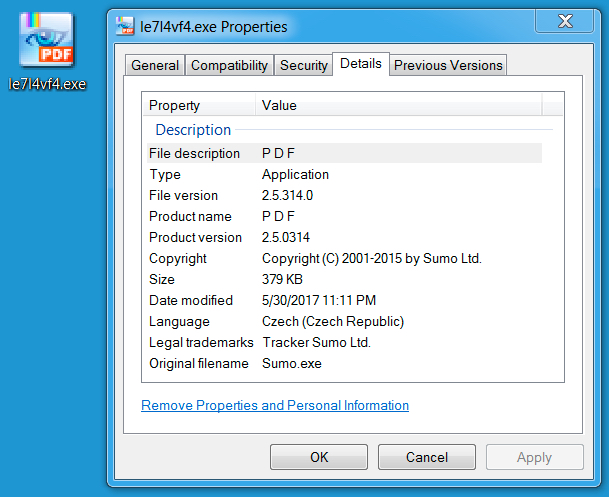
Shown above: Metadata for both Kovter payloads.
Click here to return to the main page.
