2017-05-31 - LUMINOSITY RAT
ASSOCIATED FILES:
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
- 2017-05-31-Luminosity-RAT-traffic.pcap.zip 726.6 kB (726,628 bytes)
- 2017-05-31-Luminosity-RAT-traffic.pcap (862,006 bytes)
- 22017-05-31-Luminosity-RAT-malware.zip 1.7 MB (1,693,290 bytes)
- RFQ-1.exe (885,760 bytes)
- RFQ-1.zip (845,938 bytes)
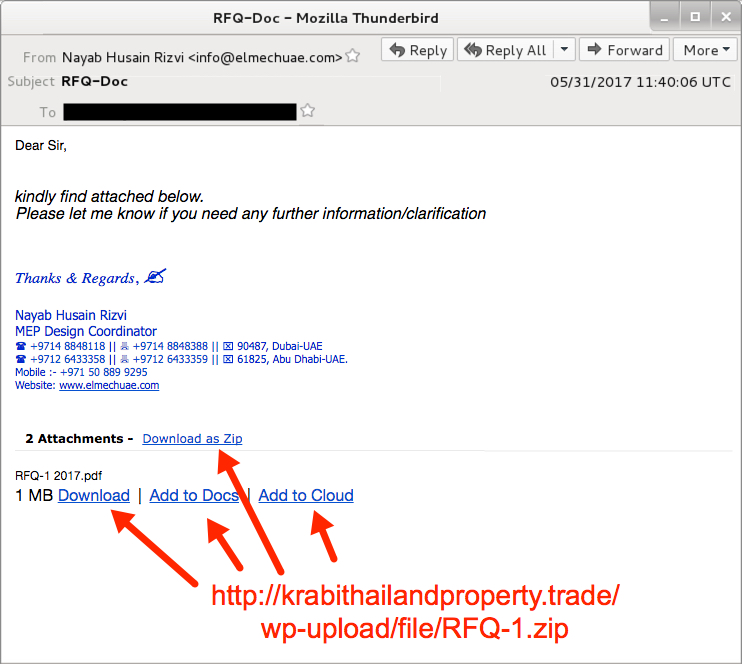
Shown above: Screenshot of the email.
EMAIL HEADERS:
Received: from [10.98.149[.]95] (unknown [197.210.25[.]103]);
by [removed]
Wed, 31 May 2017 14:40:21 +0300 (EEST)
Date: Thu, 01 Jun 2017 00:40:06 -0700
From: "Nayab Husain Rizvi" <info@elmechuae[.]com>
Subject: RFQ-Doc
MIME-Version: 1.0
TRAFFIC
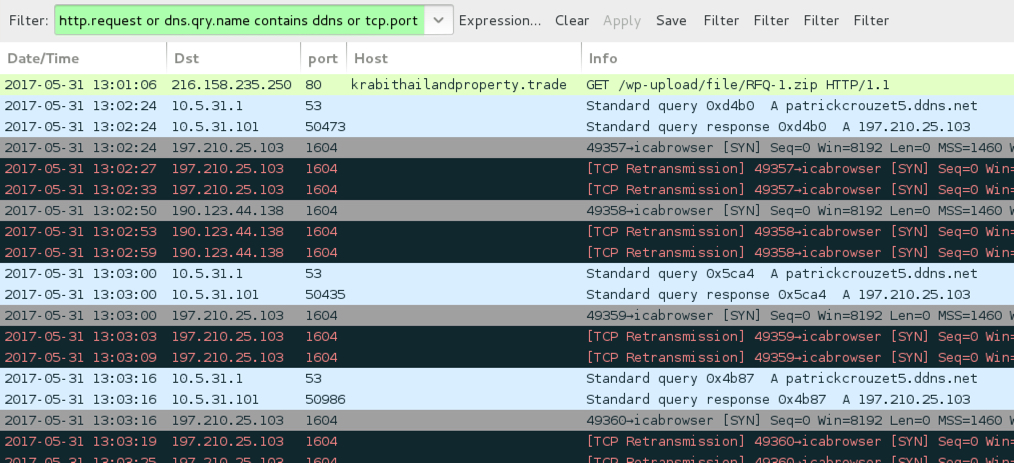
Shown above: Pcap of the traffic filtered in Wireshark.
ASSOCIATED DOMAINS
- 216.158.235[.]250 port 80 - krabithailandproperty[.]trade - GET /wp-upload/file/RFQ-1.zip [link from the email to download the zip archive]
- 197.210.25[.]103 1604 - patrickcrouzet5.ddns[.]net - post-infection attempted TCP connections
- 190.123.44[.]138 port 1604 - post-infection attempted TCP connections
MALWARE
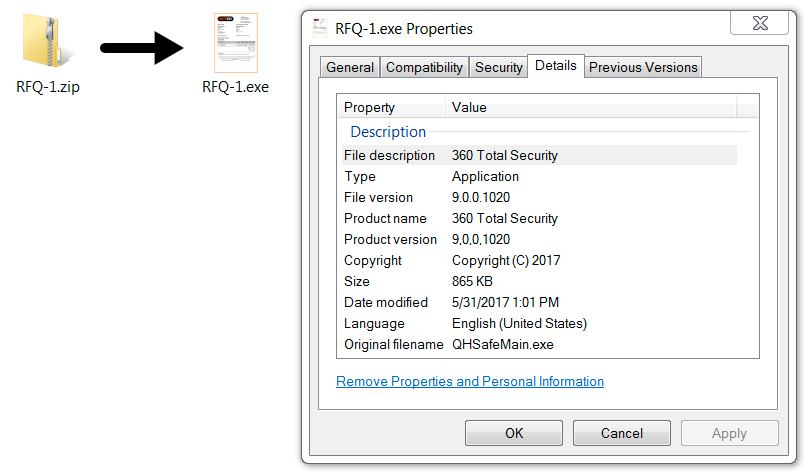
Shown above: ZIP archive and its contents.
DOWNLOADED ZIP FILE:
- SHA256 hash: 0789f957d8725decc8aad4fa572b696e542362d4b70353e2222fe20844f0f71b
- File size: 845,938 bytes
- File name: RFQ-1.zip
EXTRACTED MALWARE (LUMINOSITY RAT):
- SHA256 hash: 4b9b87441ef44b226d170b760103ff694a7374805e26202822250154d3206994
- File size: 885,760 bytes
- File name: RFQ-1.exe
IMAGES
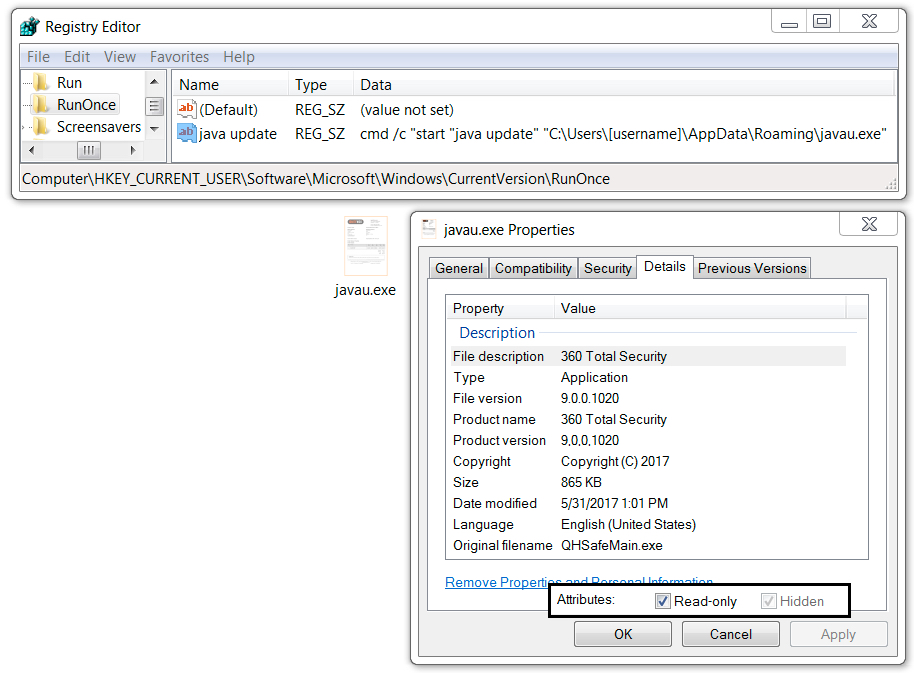
Shown above: Luminosity RAT made persistent on the infected host.
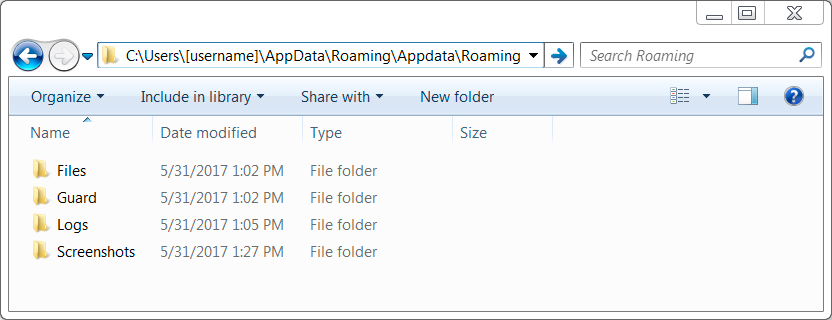
Shown above: Directories created to hold data stolen by the malware.
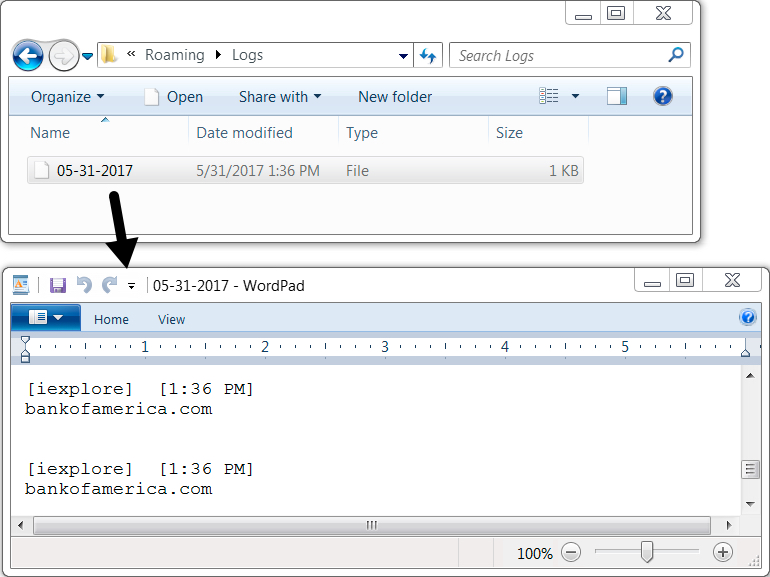
Shown above: Log of user activity from the infected host.
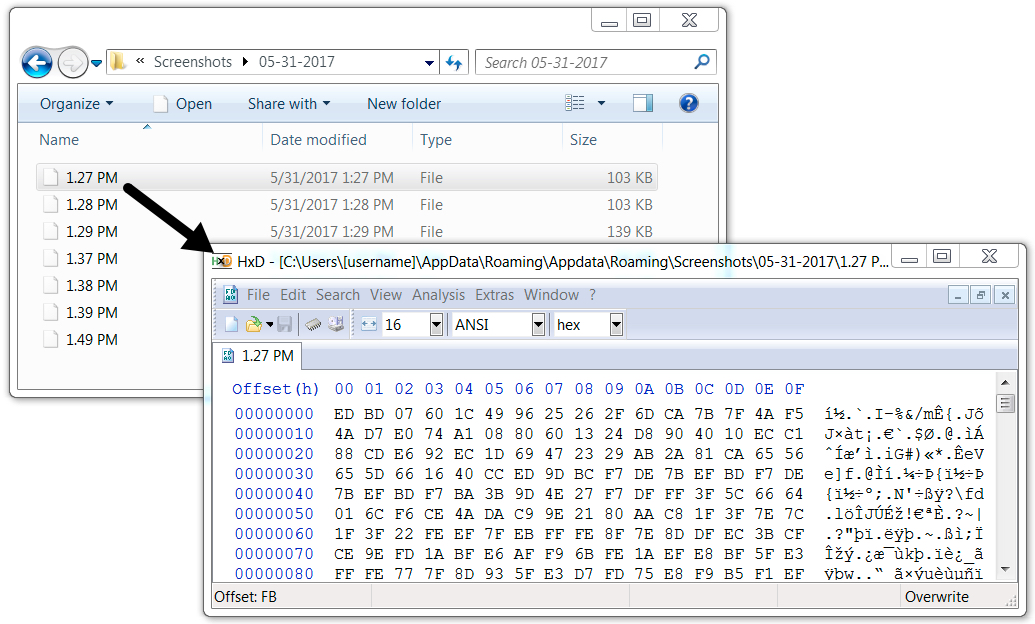
Shown above: Screenshots stored in some sort of encoded format on the infected host.
Click here to return to the main page.
