2017-05-31 - HANCITOR INFECTION WITH ZLOADER
ASSOCIATED FILES:
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
- 2017-05-31-Hancitor-infection-with-ZLoader.pcap.zip 13.7 MB (13,656,337 bytes)
- 2017-05-31-Hancitor-infection-with-ZLoader.pcap (14,566,953 bytes)
- 22017-05-31-Hancitor-malspam-3-examples.zip 4.5 kB (4,525 bytes)
- 2017-05-31-Hancitor-malspam-1547-UTC.eml (3,860 bytes)
- 2017-05-31-Hancitor-malspam-1558-UTC.eml (3,863 bytes)
- 2017-05-31-Hancitor-malspam-1612-UTC.eml (3,855 bytes)
- 2017-05-31-malware-from-Hancitor-infection.zip 288.2 kB (288,177 bytes)
- BNF842.tmp (190,464 bytes)
- USPS_invoice_yahoo.doc (269,312 bytes)
NOTES:
- Other indicators can be found from a tweet by @james_inthe_box here.
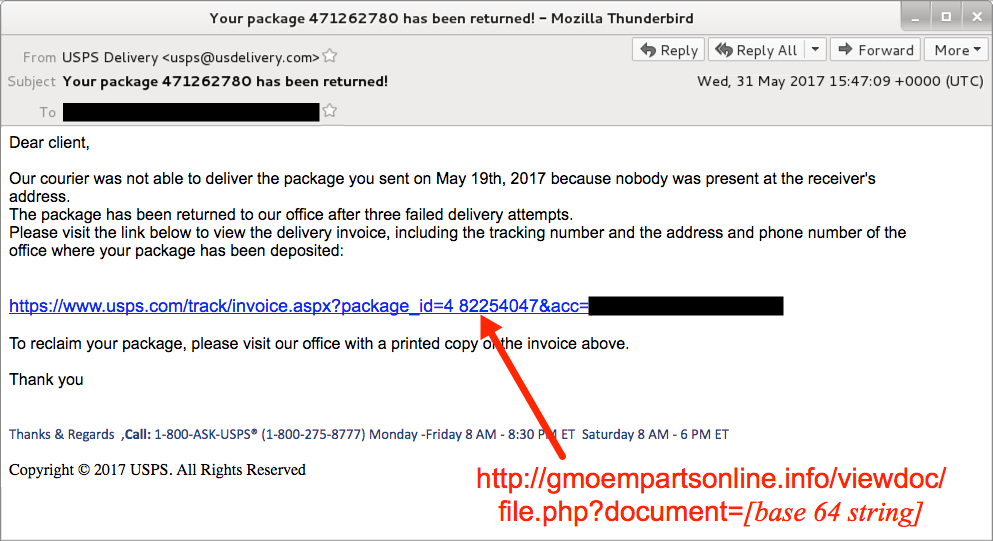
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date: Wednesday 2017-05-31 as early as 15:47 UTC through at least 16:12 UTC
- From: "USPS Delivery" <usps@usdelivery[.]com>
- Subject: Your package 471262780 has been returned!
- Subject: Your package 482254047 has been returned!
- Subject: Your package 776322486 has been returned!
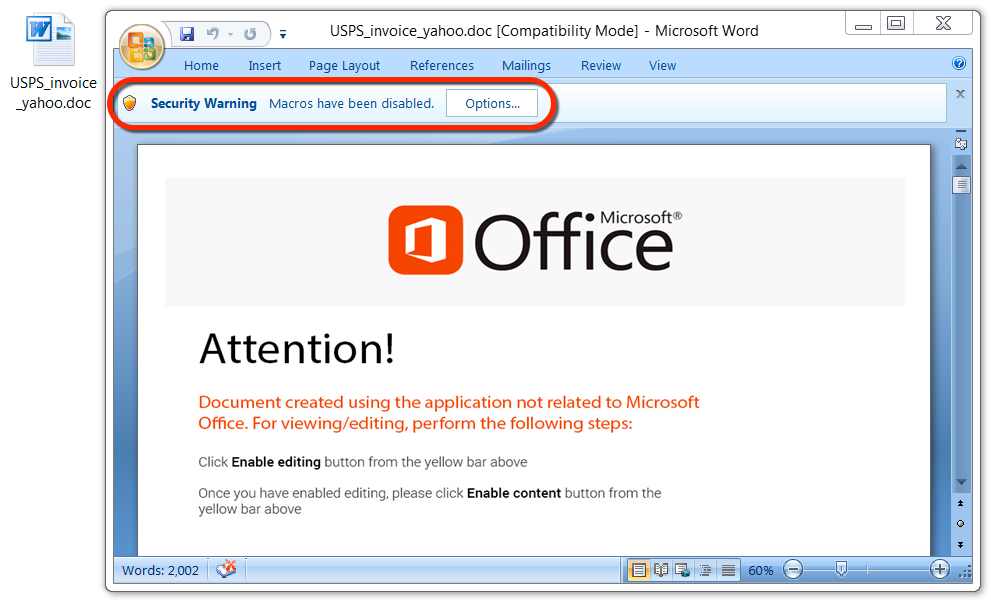
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
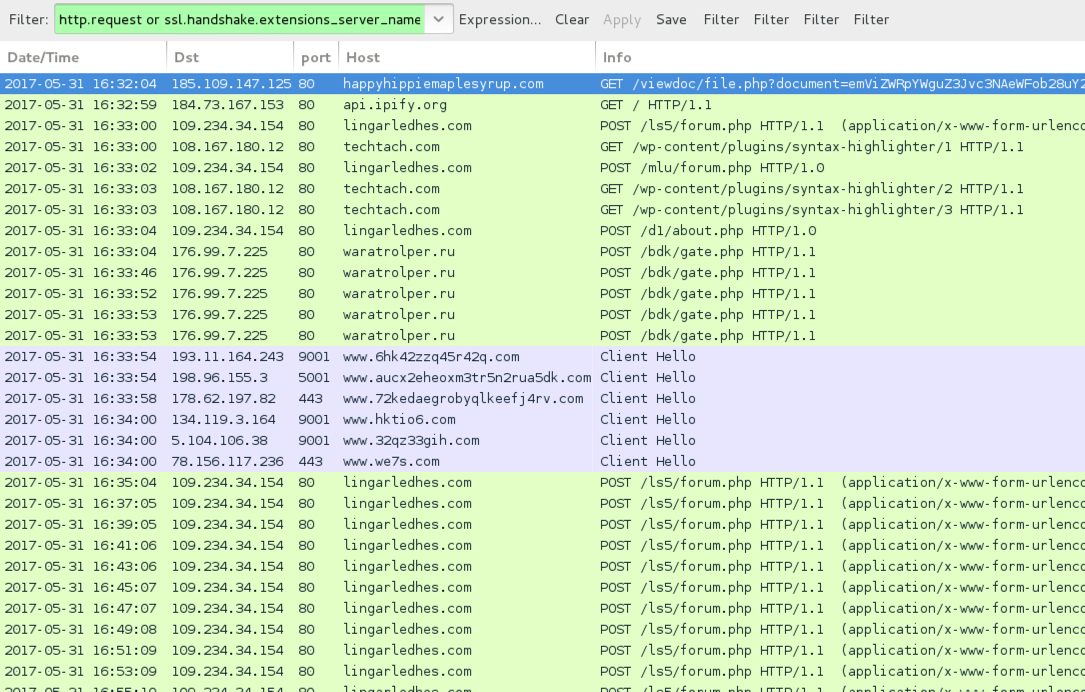
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- 185.109.147[.]125 port 80 - gmoempartsonline[.]info - GET /viewdoc/file.php?document=[base64 string]
- 185.109.147[.]125 port 80 - GOINTROLLIN[.]COM - GET /viewdoc/file.php?document=[base64 string]
- 185.109.147[.]125 port 80 - happyhippiemaplesyrup[.]com - GET /viewdoc/file.php?document=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- USPS_invoice_[recipient's email domain, minus the suffix].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 109.234.34[.]154 port 80 - lingarledhes[.]com - POST /ls5/forum.php
- 109.234.34[.]154 port 80 - lingarledhes[.]com - POST /mlu/forum.php
- 109.234.34[.]154 port 80 - lingarledhes[.]com - POST /d1/about.php
- 108.167.180[.]12 port 80 - techtach[.]com - GET /wp-content/plugins/syntax-highlighter/1
- 108.167.180[.]12 port 80 - techtach[.]com - GET /wp-content/plugins/syntax-highlighter/2
- 108.167.180[.]12 port 80 - techtach[.]com - GET /wp-content/plugins/syntax-highlighter/3
- 176.99.7[.]225 port 80 - waratrolper[.]ru - POST /bdk/gate.php
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 90bc91b499514874902cd442324f1f81347ed351dd60212c3ac238f419f755f4
File name: USPS_invoice_yahoo.doc
File size: 269,312 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 346b7d73c5a1b3700e922525e29579fa4bfeff942921bac4ae0bcb5ba856e262
File location: C:\Users\[username]\AppData\Local\Temp\BNF842.tmp
File size: 190,464 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
