2017-06-01 - ZEUS PANDA BANKER INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-01-Zeus-Panda-Banker-infection-traffic.pcap.zip 3.4 MB (3,400,817 bytes)
- 2017-06-01-Zeus-Panda-Banker-infection-traffic.pcap (3,978,012 bytes)
- 2017-06-01-malware-from-Zeus-Panda-Banker-infection.zip 388.4 kB (388,402 bytes)
- TPD64730435.zip (26,605 bytes)
- Traffic_Police_Department - Parking_Ticket_Information.doc (68,096 bytes)
- suchka.exe (188,417 bytes)
- upd59213af8.exe (299,008 bytes)
NOTES:
- This Zeus Panda Banker infection originated from a wave of parking ticket-themed malspam using links to Google Docs URLs that host zip archives containing Word documents.
- The Word documents have macros that, if enabled, attempt to download and install Zeus Panda Banker.
- My sincere hanks to the person who emailed me information about this wave of malspam. You know who you are!
- The emails are signed "Sincerely, Traffic Police."
Shown above: This is how I like traffic police... Brash and sassy.
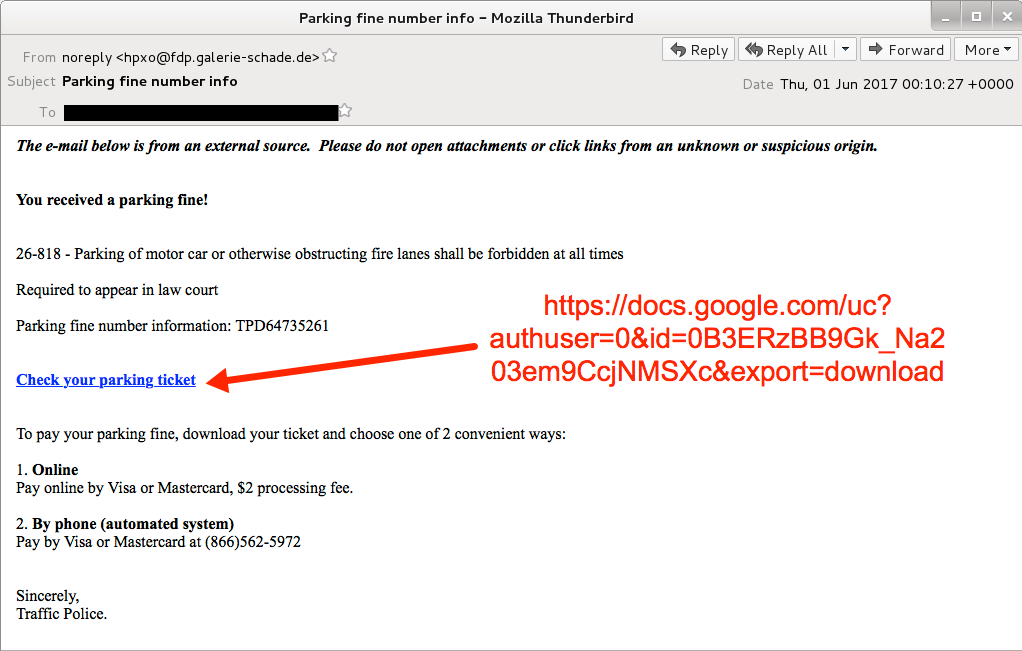
Shown above: Screen shot from one of the emails.
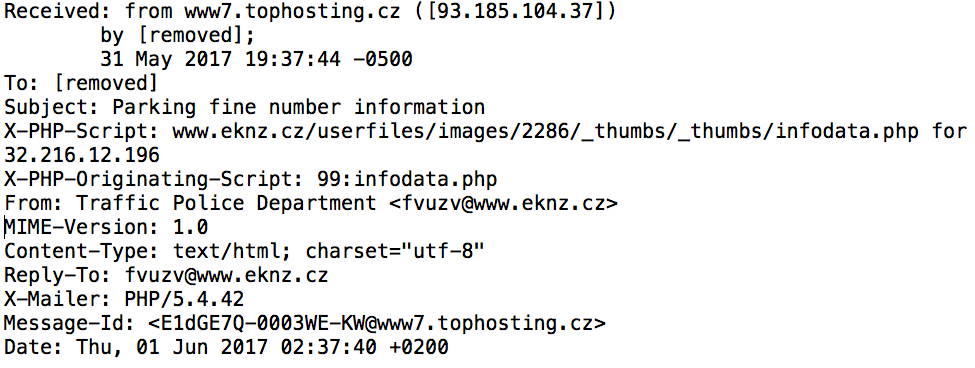
Shown above: Example of email headers (1 of 2).
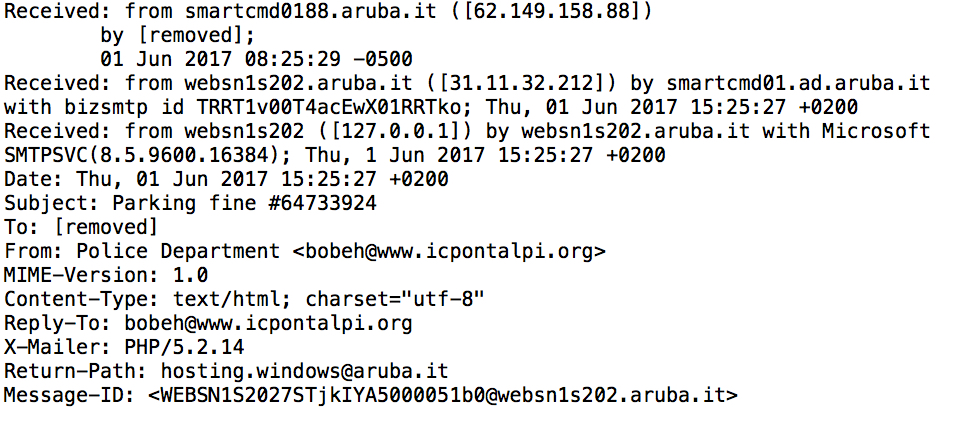
Shown above: Example of email headers (2 of 2).
EMAIL HEADERS:
- Date: As early as Wendesday 2017-05-31 at 22:57 UTC through at least Thursday 2017-06-01 at 14:15 UTC
- Subject: Parking fine number info
- Subject: Parking fine number information
- Subject: Parking fine #64731962
- Subject: Parking fine #64732133
- Subject: Parking fine #64732399
- Subject: Parking fine #64733708
- Subject: Parking fine #64733752
- Subject: Parking fine #64733924
- Subject: Parking fine #64733997
- Subject: Parking fine #64734291
- Subject: Parking fine #64734709
- Subject: Parking fine #64735028
- Subject: Parking fine #64735308
- Subject: Parking fine #64735557
- Subject: Parking fine #64736451
- Subject: Parking fine #64737103
- Subject: Parking fine #64737716
- Subject: Parking fine #64739852
- Subject: Parking ticket
- From: 150730@linwebng13.hostingspace[.]pro
- From: 559274@pemlinng025.blacknight[.]com
- From: absalarm.dk@linux9.unoeuro[.]com
- From: apache@mc1.molalla[.]net
- From: bobeh@www.icpontalpi[.]org
- From: crownsol@chewbacca.zuver[.]net[.]au
- From: dmktmx@as1r2051.servwingu[.]mx
- From: dwfcz@tutor360[.]it
- From: from-okinawa@sv155.xserver[.]jp
- From: fvuzv@www.eknz[.]cz
- From: garsia94__garsia94tbgettru__rq@rauf3.beget[.]ru
- From: lilkana@sv007.rocketnet[.]jp
- From: lubpz@armazem398[.]com[.]br
- From: nsvps_brainwave@ps406045.dreamhostps[.]com
- From: rbagroltd@hestia-la.thewebhostserver[.]com
- From: techadvi@cp10-jhb.za-dns[.]com
- From: thomas.a.weber@t-online[.]de
MALWARE
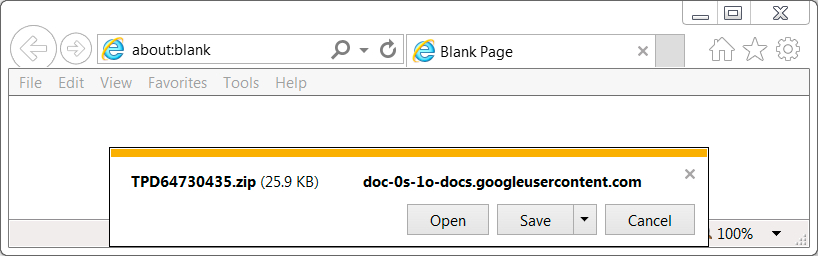
Shown above: Downloading the zip archive from a link in one of the emails to Google Docs.
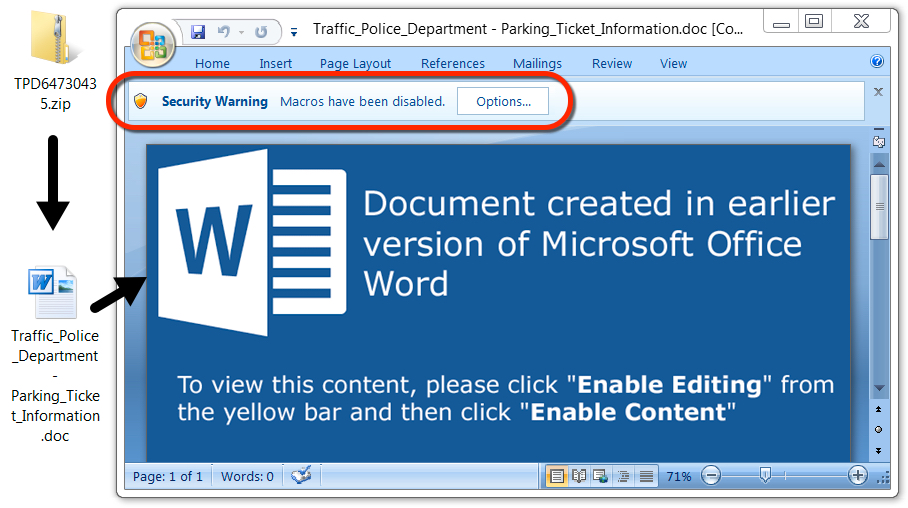
Shown above: The zip archive contained a Word document with malicious macros.
ZIP ARCHIVE DOWNLOADED FROM GOOGLE DOCS LINK IN ONE OF THE EMAILS:
- SHA256 hash: 75c9cea38806c0a04aa498b9732a04e1da77091353a68e6b4edfc868d7edeb0c
File size: 26,605 bytes
File name: TPD64730435.zip
WORD DOCUMENT EXTRACTED FROM ZIP ARCHIVE:
- SHA256 hash: 68feb6fb94c52220c2238674ba8232e7b7b1233728fc34707ccde3cb8318f993
File size: 68,096 bytes
File name: Traffic_Police_Department - Parking_Ticket_Information.doc
FILE DOWNLOADED BY THE WORD MACROS:
- SHA256 hash: 520e78f7c5f55de70c15031db0c2aad2a3708fcceb5198c24628d497093c4ae0
File size: 188,417 bytes
File location: C:\Users\[username]\AppData\Local\Temp\suchka.exe
FOLLOW-UP MALWARE NOTED AFTER THE INITIAL INFECTION:
- SHA256 hash: 00fa65c8fced0abfab3f544801014a349f7d960819d8d79c47abe090bd75ccfc
File size: 299,008 bytes
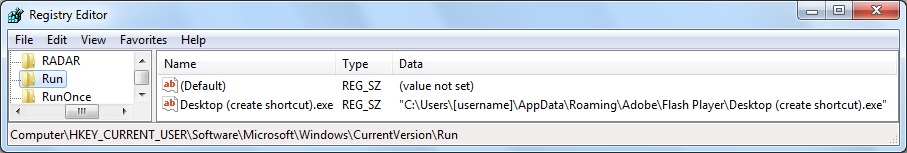
File location: C:\Users\[username]\AppData\Local\Temp\upd59213af8.exe
File location: C:\Users\[username]\AppData\Roaming\Adobe\Flash Player\Desktop (create shortcut).exe
Shown above: Follow-up malware made persistent on the infected host.
TRAFFIC
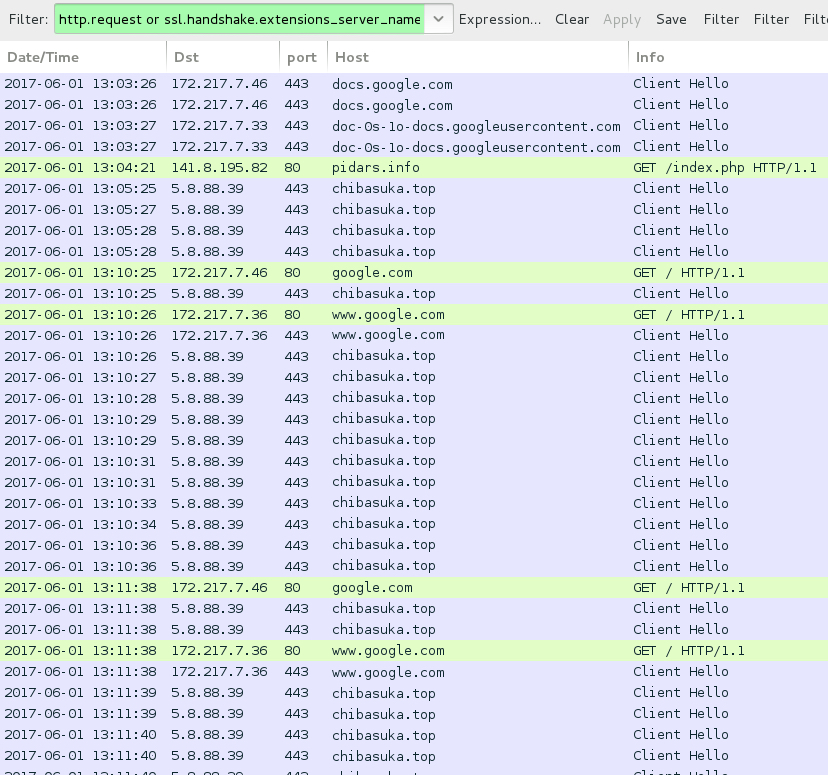
Shown above: Traffic from the infection filtered in Wireshark.
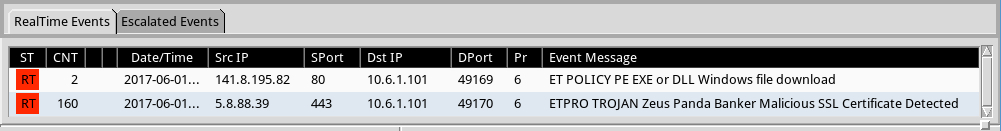
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil and tcpreplay on Security Onion.
ASSOCIATED DOMAINS:
- docs.google[.]com - GET /uc?authuser=0&id=0B3ERzBB9Gk_Na203em9CcjNMSXc&export=download [HTTPS request for the initial zip archive]
- 141.8.195[.]82 port 80 - pidars[.]info - GET /index.php [HTTP request for the malware binary]
- 5.8.88[.]39 port 443 - chibasuka[.]top - HTTPS/SSL/TLS traffic [several connections]
- google[.]com - GET / [Connectivity check by the infected host]
Click here to return to the main page.