2017-06-01 - JAFF RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-01-Jaff-ransomware-infection-traffic.pcap.zip 213.4 kB (213,391 bytes)
- 2017-06-01-Jaff-ransomware-malspam-tracker.csv.zip 0.8 kB (837 bytes)
- 2017-06-01-Jaff-ransomware-emails-and-malware.zip 823.0 kB (823,019 bytes)
NOTES:
- More information on this campaign can be found at: https://isc.sans.edu/forums/diary/Jaff+ransomware+gets+a+makeover/22446/
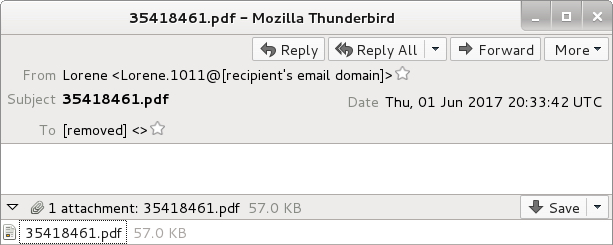
Shown above: An example of the emails.
4 EMAIL EXAMPLES:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT
- 2017-06-01 20:33:42 UTC -- "Lorene" <Lorene.1011@[recipient's email domain]> -- 35418461.pdf
- 2017-06-01 20:36:36 UTC -- "Marcos" <Marcos.7077@[recipient's email domain]> -- 77586054.pdf
- 2017-06-01 20:39:17 UTC -- "Ana" <Ana.0770@[recipient's email domain]> -- 79443215.pdf
- 2017-06-01 21:04:17 UTC -- "Jami" <Jami.3269@[recipient's email domain]> -- 41021119.pdf
MALWARE
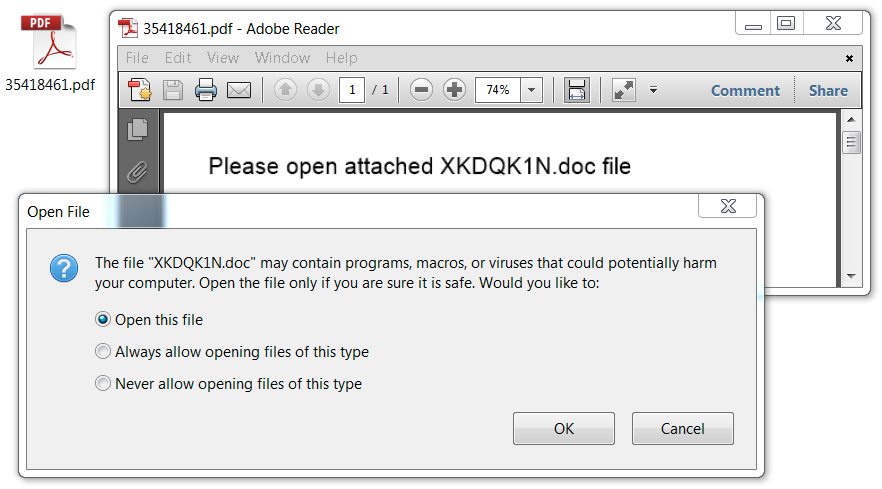
Shown above: As usual, the PDF attachment contains an embedded Word document with malicious macros.
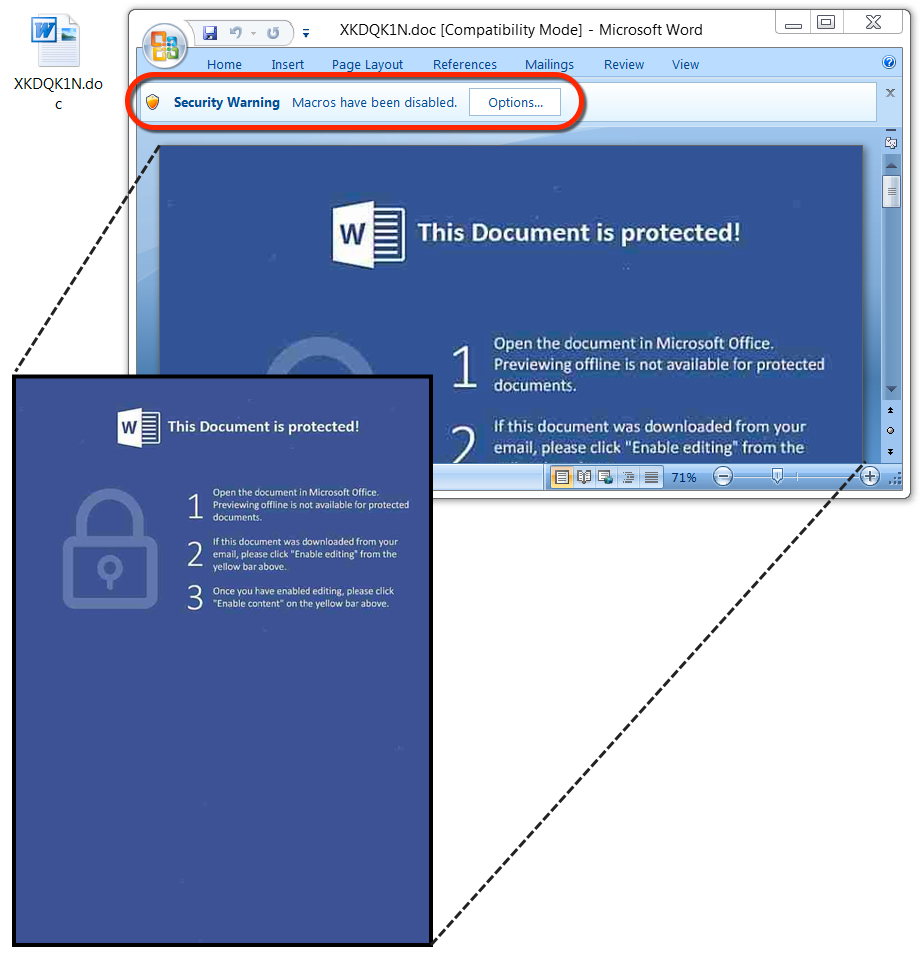
Shown above: No marks today in the bottom half of the images in these Word documents.
SHA256 HASHES FOR THE PDF ATTACHMENTS:
- 2ac01c6385135cc695abdf4e9e34d7618a7e0b81285e1f3123df54a9572982fd - 79443215.pdf
- 753550a1aa18b506693af9e1dd3af81de174cd88e820a7c87e9a8474456d3deb - 77586054.pdf
- 7cf89ac46a7bfcb8657c8b7bfa9f39c5396ec62ef9e86416f4780138c72e9040 - 41021119.pdf
- 81ef38b0fb7c395c05f593847074021743b4b2a4b1b45478e25cf64194a67aef - 35418461.pdf
SHA256 HASHES FOR THE EMBEDDED WORD DOCUMENTS:
- 5db77f4e40f002917e99670f23976d883e67b17cffbba0b5801328b6c49c81f8 - YLRZLH.doc
- 830de9a72c138440482d0b7049f8d1a4de4906574043e721cd7d1487f2de2100 - XKDQK1N.doc
- 990ec28dd5d11e294910e2ed1e7bae6cc57272af402d6bf7bd3db9fd5dc89c3a - FXCHG1Y.doc
- b4304a0346bae39f2e158d2ad404f8b45aba2640fd903b26c5d6ca07ea9611ff - YVQEG23K.doc
JAFF RANSOMWARE SAMPLE:
- SHA256 hash: 824901dd0b1660f00c3406cb888118c8a10f66e3258b5020f7ea289434618b13
File size: 251,904 bytes
File location: C:\Users\[username]\AppData\Local\Temp\bruhadson8.exe
TRAFFIC
URLS FROM THE WORD MACROS TO DOWNLOAD JAFF RANSOMWARE:
- dsopro[.]com - GET /7rvmnb
- fabriquekorea[.]com - GET /7rvmnb
- katoconsulting[.]ro - GET /7rvmnb
- newserniggrofg[.]net - GET /af/7rvmnb
- praktikum-marketing[.]de - GET /7rvmnb
- resevesssetornument[.]com - GET /af/7rvmnb
- tasfirin-ustasi[.]net - GET /7rvmnb
- theexcelconsultant[.]com - GET /7rvmnb
JAFF RANSOMWARE POST-INFECTION TRAFFIC:
- 5.101.66[.]85 port 80 whoisfoxxrobiouy[.]net - GET /a5/
- rktazuzi7hbln7sy[.]onion - Tor domain for Jaff Decryptor (same as the last few times)
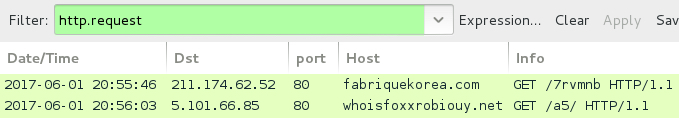
Shown above: Traffic from the infection filtered in Wireshark.
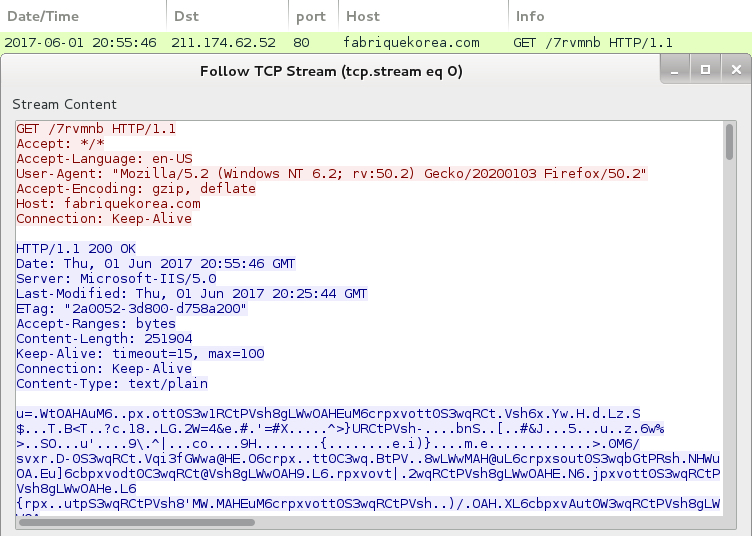
Shown above: HTTP request for the Jaff ransomware.
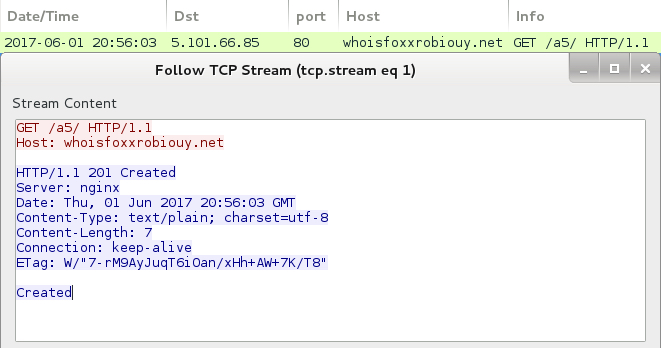
Shown above: Post-infection traffic from the infected Windows host.
IMAGES
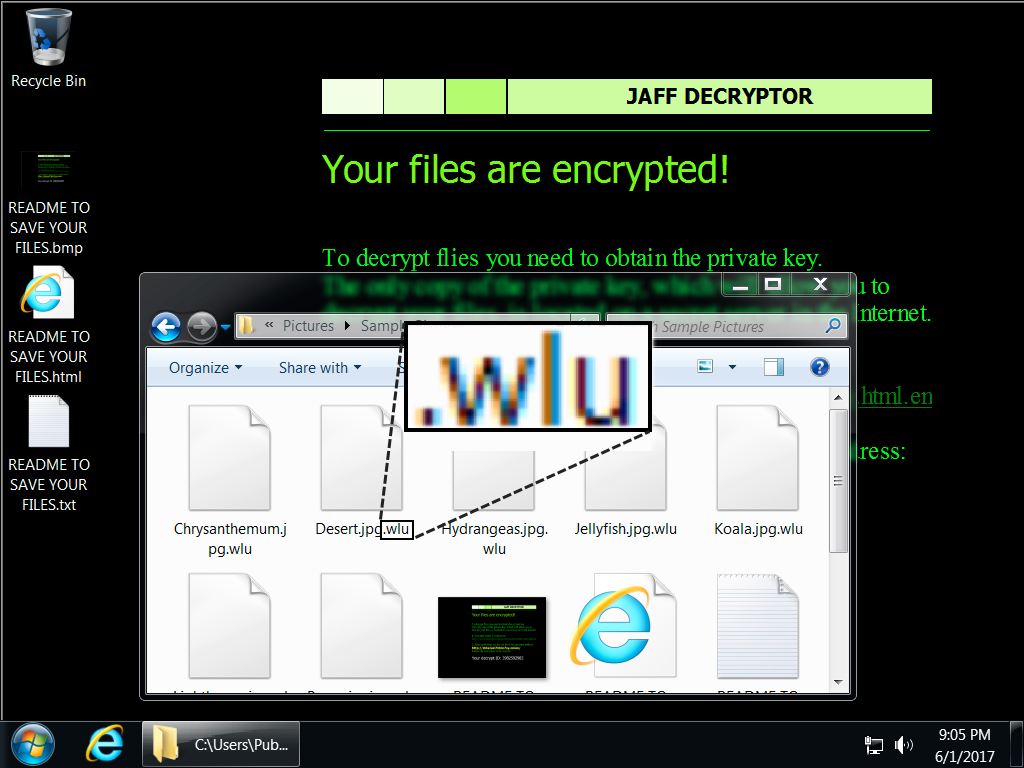
Shown above: Desktop of an infected Windows host.
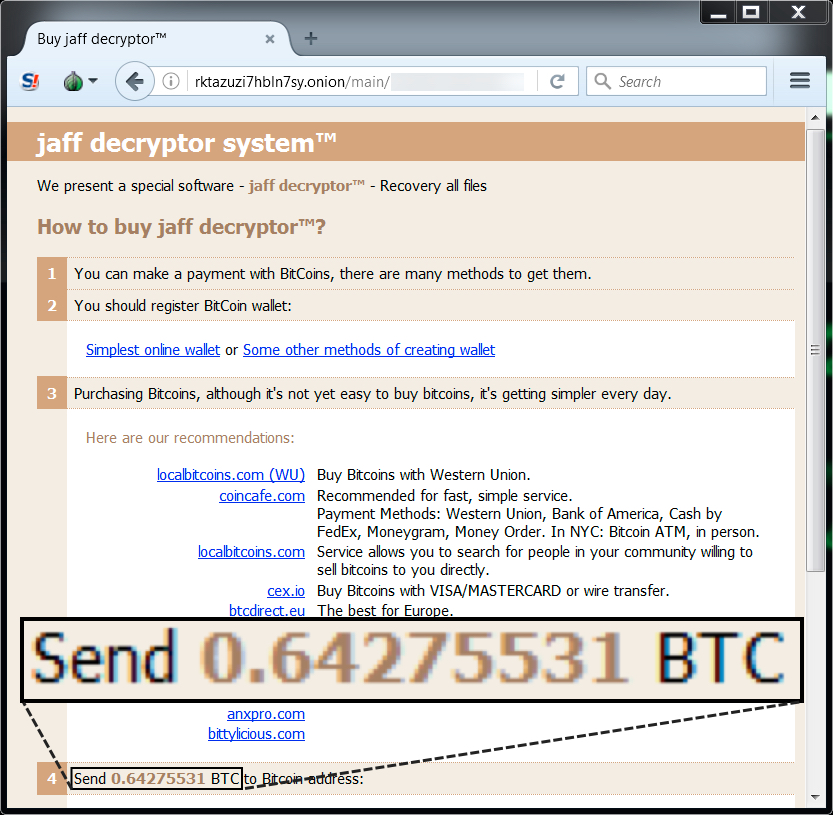
Shown above: Going to the Jaff Decryptor.
Click here to return to the main page.
