2017-06-02 - DRIDEX INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-02-Dridex-infection-traffic.pcap.zip 435 kB (434,708 bytes)
- 2017-06-02-Dridex-malspam-tracker.csv.zip 1.4 kB (1,414 bytes)
- 2017-06-02-Dridex-emails-and-malware.zip 3.0 MB (3,007,958 bytes)
NOTES:
- From 2017-05-11 through yesterday, this type of malspam from the Necurs botnet was pushing Jaff ransomware.
- Today, it's pushing Dridex.
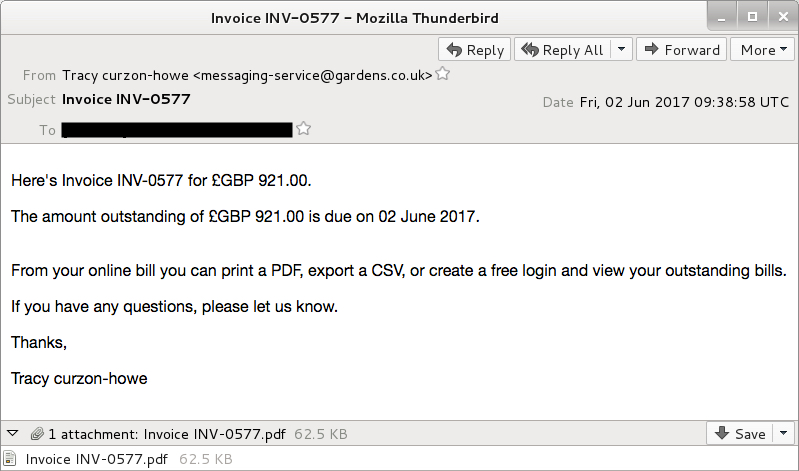
Shown above: An example of emails from the first wave.
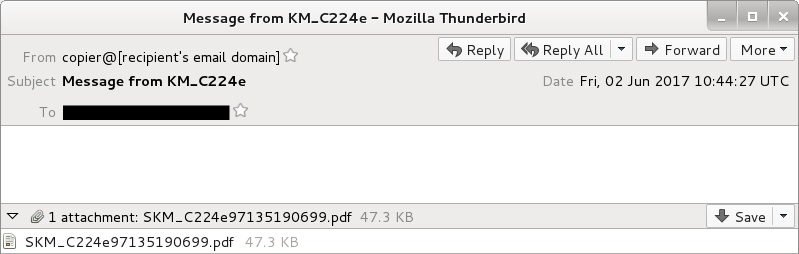
Shown above: An example of emails from the second wave.
14 EMAIL EXAMPLES:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME
- 2017-06-02 09:31:08 UTC -- Jocelyn kelland <messaging-service@southstarcomputers[.]co[.]uk> -- Invoice INV-0771 -- Invoice INV-0771.pdf
- 2017-06-02 09:36:47 UTC -- Willis lagerstom <messaging-service@jordanholidays[.]co[.]uk> -- Invoice INV-0151 -- Invoice INV-0151.pdf
- 2017-06-02 09:37:37 UTC -- Valarie marquet <messaging-service@n6drains[.]co[.]uk> -- Invoice INV-0007 -- Invoice INV-0007.pdf
- 2017-06-02 09:40:08 UTC -- Kelli clowes <messaging-service@tatlersrestaurant[.]co[.]uk> -- Invoice INV-0416 -- Invoice INV-0416.pdf
- 2017-06-02 09:40:28 UTC -- Hattie coggan? <messaging-service@gazandvic.worldonline[.]co[.]uk> -- Invoice INV-0578 -- Invoice INV-0578.pdf
- 2017-06-02 09:41:25 UTC -- Spencer de insula <messaging-service@familieswork[.]co[.]uk> -- Invoice INV-0373 -- Invoice INV-0373.pdf
- 2017-06-02 09:51:56 UTC -- Jame cholmley <messaging-service@geb1.worldonline[.]co[.]uk> -- Invoice INV-0948 -- Invoice INV-0948.pdf
- 2017-06-02 10:06:38 UTC -- copier@[recipient's email domain] -- Message from KM_C224e -- SKM_C224e27127577722.pdf
- 2017-06-02 10:08:08 UTC -- copier@[recipient's email domain] -- Message from KM_C224e -- SKM_C224e85088058540.pdf
- 2017-06-02 10:12:02 UTC -- copier@[recipient's email domain] -- Message from KM_C224e -- SKM_C224e33730651761.pdf
- 2017-06-02 10:12:21 UTC -- copier@[recipient's email domain] -- Message from KM_C224e -- SKM_C224e47704213294.pdf
- 2017-06-02 10:13:17 UTC -- copier@[recipient's email domain] -- Message from KM_C224e -- SKM_C224e31729375367.pdf
- 2017-06-02 10:13:34 UTC -- copier@[recipient's email domain] -- Message from KM_C224e -- SKM_C224e24647053158.pdf
- 2017-06-02 10:44:27 UTC -- copier@[recipient's email domain] -- Message from KM_C224e -- SKM_C224e97135190699.pdf
MALWARE
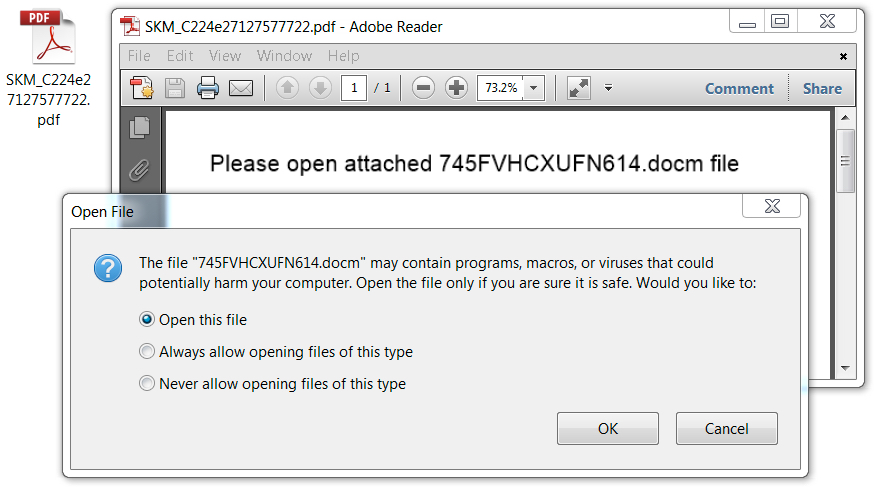
Shown above: As usual, the PDF attachment contains an embedded Word document with malicious macros.
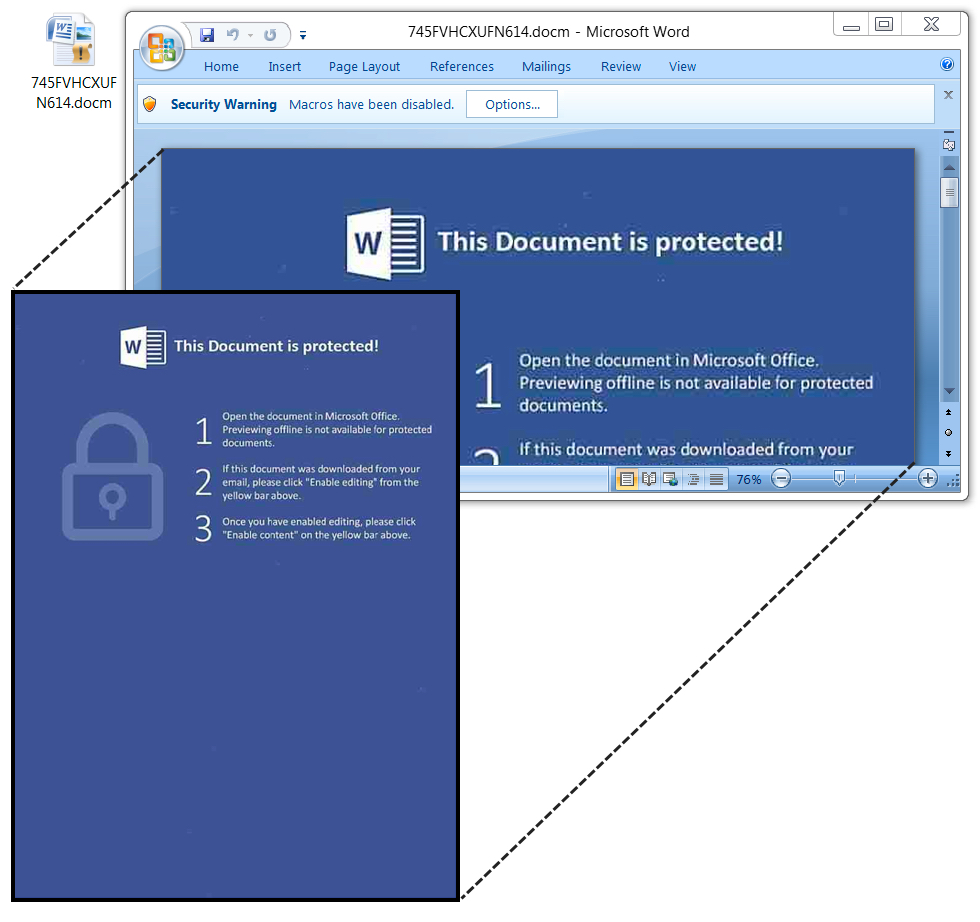
Shown above: The malicious Word document.
SHA256 HASHES FOR THE PDF ATTACHMENTS:
- cd0223374553dd88ef8a7e74866e8b24e9a531603c4b88d208da82b4ea8200e3 - Invoice INV-0007.pdf
- 11b249fa0d3079a978e7642a7079443a165cfe45ab6e1623b6fac8c6f51cb868 - Invoice INV-0151.pdf
- eaafb7d9c7cdb094930dfcaee17b722658153ebece944e8169ee32598f17834c - Invoice INV-0373.pdf
- b53bd04d4e65ecdcb29cd2ec5946a1b374da2fcfce2b40df8794d1d68f231b65 - Invoice INV-0416.pdf
- 546a787a4f7df13720f89afde13623fbe21d65267e4178b2c395c43c1fcd2c7e - Invoice INV-0578.pdf
- 377757b54790ef841def258c1f7f8580e7aa49813ecc5390a485b7a1c3029296 - Invoice INV-0771.pdf
- 1a7d9cd1b454d372d6afa9438879cbe98a5da52a801bd2385dcb1255fccfc37d - Invoice INV-0948.pdf
- 311be869af4bc6a7aaacd6e848cfb66a5844ea2b14bb29d0efa2b6cf3ccd99ca - SKM_C224e24647053158.pdf
- 377757b54790ef841def258c1f7f8580e7aa49813ecc5390a485b7a1c3029296 - SKM_C224e27127577722.pdf
- 311be869af4bc6a7aaacd6e848cfb66a5844ea2b14bb29d0efa2b6cf3ccd99ca - SKM_C224e31729375367.pdf
- a543eacf9634b3c105d63b0f71823c8b4b281a57e44283c301c0caad3b697ca4 - SKM_C224e33730651761.pdf
- 5fefc595155fd79022cc772503f994d5b144e8a933ac95ea15fe1d58c5088e50 - SKM_C224e47704213294.pdf
- 2e3768b4c924e0826c928afb1c2664be99b32bcde80a688464f6546ea9181fdb - SKM_C224e85088058540.pdf
- 21638d2d5b29a22d627a05b82e87b670aca216c93d5513015e33d6a476abb1e9 - SKM_C224e97135190699.pdf
SHA256 HASHES FOR THE EMBEDDED WORD DOCUMENTS:
- bb2e4d6d92c3863d7a7a867cbaca6807c8cec713e67f866e280d26525434e897 - 111DJV54NRB118.docm
- b08d15ffedade365ae8a5c9eefa273714bdc02b5bcd8903ccd3cfb5f42936ce4 - 307AKH56YVU512.docm
- 49aa6809b45720d0cb0f90eb79bca70af66acf11ff62cfc70266b55954ef7459 - 381DKNVX6TT814.docm
- 1fd5764500ff4e06cf332571c2b51ac0352c2df2228abd842816f0a7024806f9 - 513IF28PILG272.docm
- 7abef7558692083009f0e763fe591a20268e62c8a35f88a17dee9c4b57b69900 - 610ASHHEIXYH688.docm
- 42151ca743c29fd64d927d2cee9cafa7e67609aaa7f1ec29390bd481fab56079 - 651X2WTXGJM419.docm
- 9f5541acd2d0ba325de21763aa5eac78dcdb6afbd7790532a0d9697d398bec83 - 656NVMPNEQM829.docm
- d79d3fe06f91a0b4974cf4346e62624deb1c8f47634eb60a7e16b7fd086fcbdb - 745FVHCXUFN614.docm
- 153b01882dafadd73f73d3343a583b981b01e6ad12cf74418b251296bf537da9 - 783PNCDQX7893.docm
- 2ee58f175bc8ebe984fed80a333bfc7d66b439a1158e8a2d3f950485acf47f7e - 806M6QN9PXB210.docm
- d32f40221b575a31d9eb627c01e5cc97e5337fb16621dd152e1d2aa34730142e - 810FY6KLZEW4739.docm
- ddd20e67c4b959054b8fe69ffd719ff235e909bf651d026208802eb4d6887154 - 869X5YEUYBV798.docm
FILES RETRIEVED FROM INFECTED HOST:
- SHA256 hash: ffb6cf0788bc9fef9314085cf23fbdf87bfde9c3b78f014d5fd3e76d769cc82c
File size: 135,168 bytes
File location: C:\User\[username]\AppData\Local\Temp\miniramon8.exe
File description: Dridex
- SHA256 hash: b938375b07461535976dcbf316d3587faafdbeedfd6efe70752f27373188bd25
File size: 192 bytes
File location: C:\User\[username]\AppData\Local\Temp\OF6.cmd
File type: Batch file
- SHA256 hash: 80c10ee5f21f92f89cbc293a59d2fd4c01c7958aacad15642558db700943fa22
File size: 776,192 bytes
File location: C:\Users\[username]\AppData\Roaming\4AXMka1\calc.exe
File description: appears to be a copy of legitimate Microsoft file calc.exe
- SHA256 hash: b39797252e05301fa28a94811b105f5ea7d6e6be066ffc71be9a25baf543b862
File size: 348,160 bytes
File location: C:\Users\[username]\AppData\Roaming\4AXMka1\UxTheme.dll
File description: Likely Dridex DLL side-loaded by above calc.exe file
WINDOWS REGISTRY ENTRY ON THE INFECTED HOST:
- Registry key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Value name: Msgqwid
Value type: REG_SZ
Value Data: C:\Users\[username]\AppData\Roaming\4AXMka1\calc.exe
TRAFFIC
URLS FROM THE WORD MACROS TO DOWNLOAD DRIDEX:
- eselink[.]com[.]my - GET /hH60bd
- lanphuong[.]vn - GET /hH60bd
- lordheals[.]com - GET /hH60bd
- meiyizixun[.]com - GET /hH60bd
- midiconcept[.]com - GET /hH60bd
- mountmary[.]ca - GET /hH60bd
- newserniggrofg[.]net - GET /af/hH60bd
- orhangazitur[.]com - GET /hH60bd
- resevesssetornument[.]com - GET /af/hH60bd
- shrideva[.]co[.]in - GET /hH60bd
- strassensammler[.]de - GET /hH60bd
- systemalu[.]com - GET /hH60bd
- yoyogi[.]com[.]au - GET /hH60bd
- zvezda-k[.]ru - GET /hH60bd
DRIDEX POST-INFECTION TRAFFIC:
- 147.32.5[.]111 port 8043 - SSL/TLS traffic
- 200.119.46[.]10 port 443 - SSL/TLS traffic
- 203.206.230[.]127 port 443 - SSL/TLS traffic
- 80.229.36[.]165 port 443 - attempted TCP connection (no response from the server)
- 81.170.50[.]252 port 443 - attempted TCP connection (no response from the server)
- 94.226.67[.]55 port 443 - attempted TCP connection (no response from the server)
- 185.141.25[.]23 port 443 - attempted TCP connection (no response from the server)
- 216.165.249[.]150 port 443 - attempted TCP connection (no response from the server)
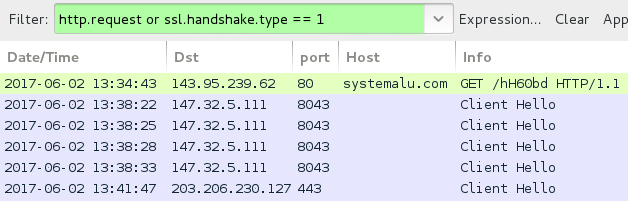
Shown above: Traffic from the infection filtered in Wireshark.
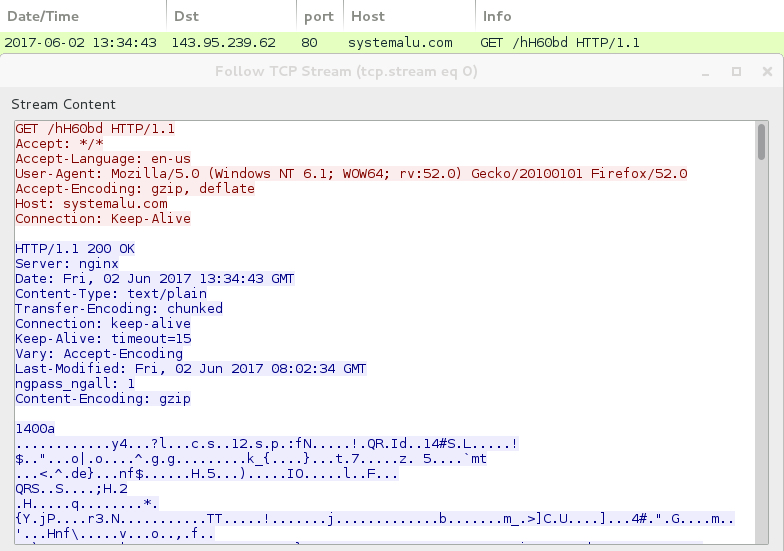
Shown above: HTTP request for the Dridex EXE.
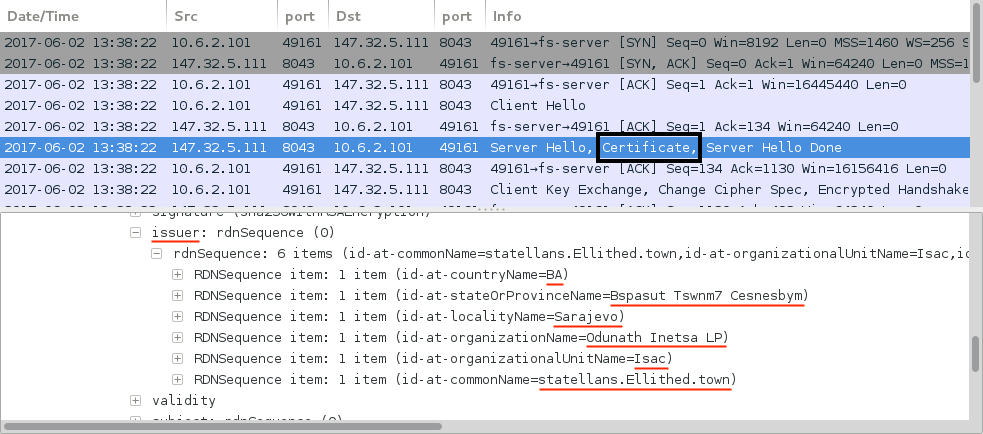
Shown above: SSL/TLS certificate data associated with Dridex.
Click here to return to the main page.
