2017-06-05 - DRIDEX INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-05-Dridex-infection-traffic.pcap.zip 72.9 kB (72,896 bytes)
- 2017-06-05-Dridex-malspam-tracker.csv.zip 1.1 kB (1,073 bytes)
- 2017-06-05-Dridex-malware-and-artifacts.zip 966.6 kB (966,558 bytes)
OTHER REPORTS ON TODAY'S DRIDEX ACTIVITY WITH MORE INDICATORS AT:
- Dynamoo's Blog: Malware spam: "John Miller Limited" / "Invoice"
- My Online Security: Spoofed John Miller invoice pretending to come from somebody named Holmes delivers Dridex banking Trojan
EMAILS
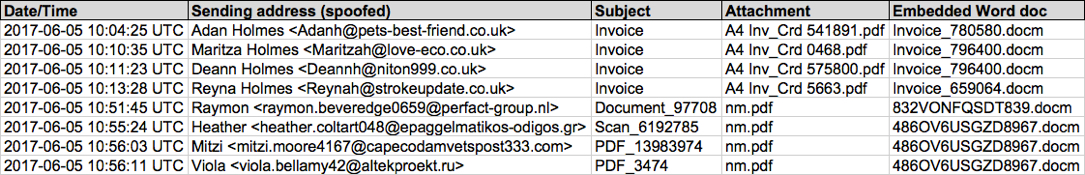
Shown above: Spreadsheet on the 8 emails I collected.
MALWARE
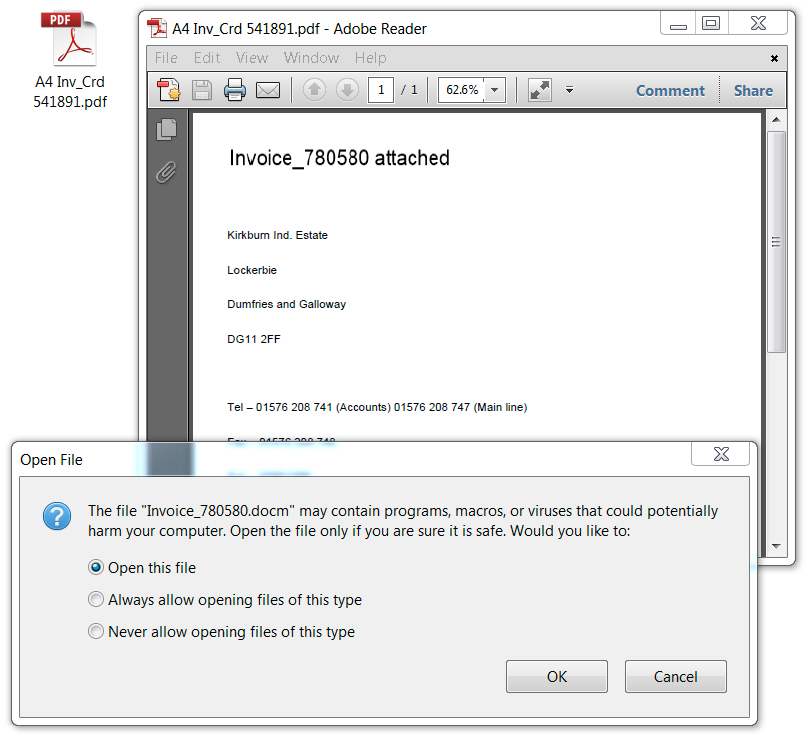
Shown above: As usual, the PDF attachment contains an embedded Word document with malicious macros.
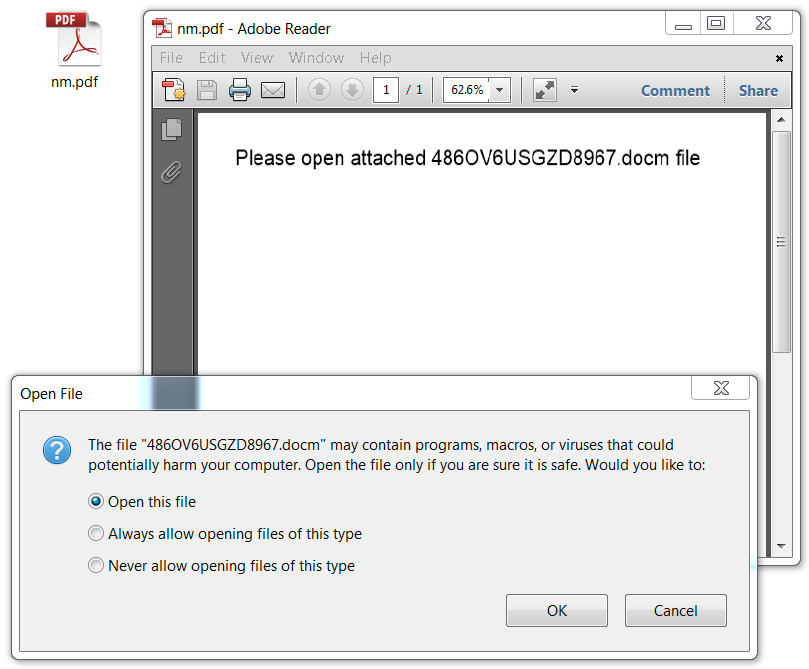
Shown above: Another shot of the PDF attachment from the second wave.
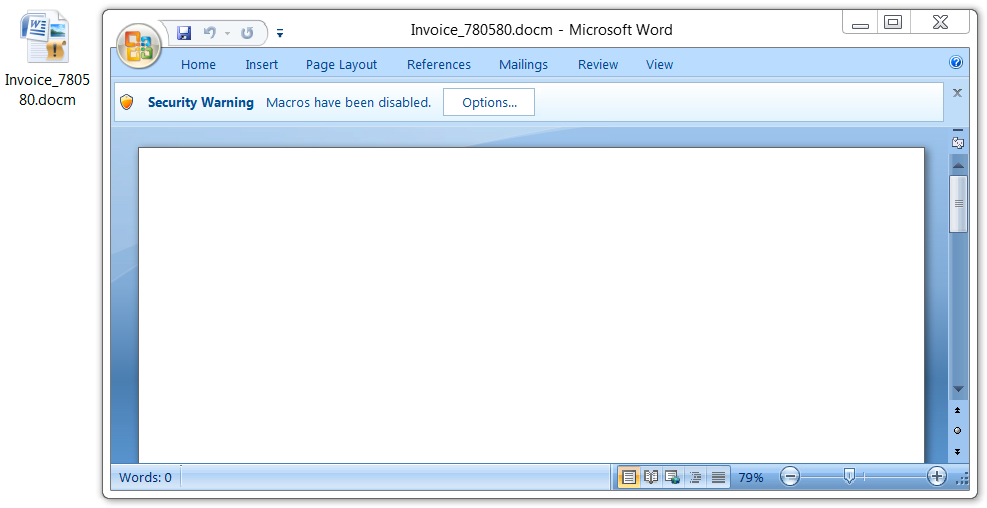
Shown above: No picture or instructions this time. Just a blank Word document with macros.
SHA256 HASHES FOR THE PDF ATTACHMENTS:
- 0e3adf0314c28862e2ebbb80e985734afef46f41155891b31d75d095aa2d2e24
- 2793481cba97250c877ab15789ce851c7da360ca9a5602a2f86fdef8e842471d
- 2ba45f9e37a6db042f1b6492e2b92eb2decaa8b0b18508affa79f72c2a51bf04
- 7a11a65f347bbfb2c6865b90e1373cfdf4085468864953ec59d7412512256d36
- b2fc044e9e49f5c539d13705548b0adf822d5a5f431c61f083cc2c59ba08aac9
SHA256 HASHES FOR THE EMBEDDED WORD DOCUMENTS:
- 011bf13d75adfd98c1e60aec9e3470be4e89f9c56263e511ab30aa2c69f132c2
- 564be1d40296c09cd7247fbd396158d9bcad443f2bd627f53a7e3672fffa361e
- b865826fdd7ef22cb5621f92d9391fbacfe10e9c75402b571e1484597d25b49c
- bdb3b5081a31d6b10a2602af6aee5c4eaa3722c17b4d5c90b4874968454c9654
- df2bc524fafb759eae77e3053c6f7d7dacdf6b5be43048d9c849529d749c61f7
FILES RETRIEVED FROM INFECTED HOST:
- SHA256 hash: c7dc1e2d1dbda6e287675160f1e96f6514b8a6f10017a1e4b76c7591c3785e97
File size: 118.784 bytes
File location: C:\User\[username]\AppData\Local\Temp\miniramon8.exe
File description: Windows EXE for Dridex
TRAFFIC
URLS FROM THE WORD MACROS TO DOWNLOAD DRIDEX:
- multielectricos[.]com - GET /8yfh4gfff
- newserniggrofg[.]net - GET /af/8yfh4gfff
- resevesssetornument[.]com - GET /af/8yfh4gfff
- salonpalmareal[.]com - GET /8yfh4gfff
- select-hire[.]com - GET /8yfh4gfff
- sukko-diona[.]ru - GET /8yfh4gfff
- ymcaonline[.]net - GET /8yfh4gfff
- zhongjianbao[.]com - GET /8yfh4gfff
DRIDEX POST-INFECTION TRAFFIC:
- 46.101.154[.]177 port 4743 - SSL/TLS traffic
- 85.214.126[.]182 port 4743 - SSL/TLS traffic
- 89.110.157[.]78 port 4743 - SSL/TLS traffic
Click here to return to the main page.
