2017-06-08 - INFOSTEALER INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-08-Brazil-infostealer-infection-traffic.pcap.zip 8.7 MB (8,705,420 bytes)
- 2017-06-08-Brazil-infostealer-infection-traffic.pcap (9,261,121 bytes)
- 2017-06-08-Brazil-email-and-infostealer-malware.zip 10.8 MB (10,790,408 bytes)
- 2017-06-07-Brazil-malspam-1740-UTC.eml (2,148 bytes)
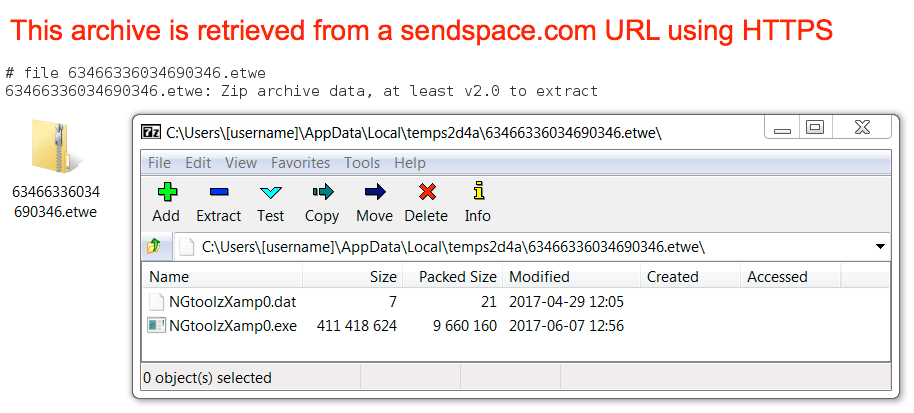
- 63466336034690346.etwe (9,660,419 bytes)
- Iptu-_-2017.zip (1,126,288 bytes)
EMAILS
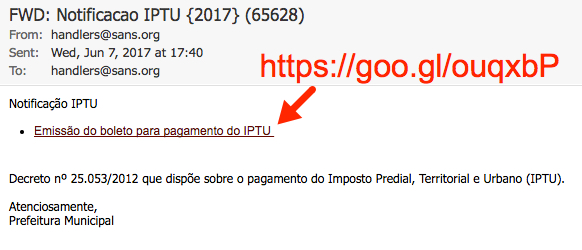
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date: Wednesday 2017-06-07 at 17:40 UTC
- Sending mail server: lasvegas-nv-datacenter.serverpoint[.]com (216.108.237[.]107)
- Message ID header: <20170607174004.32A9C2C74A0@lasvegas-nv-datacenter.serverpoint[.]com>
- Sending address: [spoofed: recipient's email address]
- Subject: FWD: Notificacao IPTU {2017} (65628)
INITIAL MALWARE
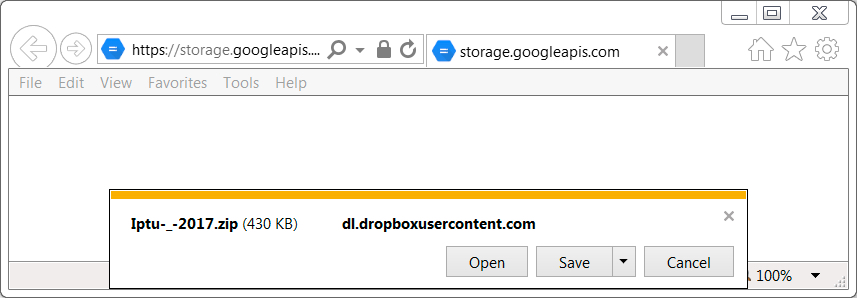
Shown above: Clicking link from the email redirects to a Dropbox URL for a zip archive.
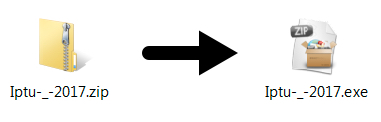
Shown above: Contents of the zip archive.
TRAFFIC
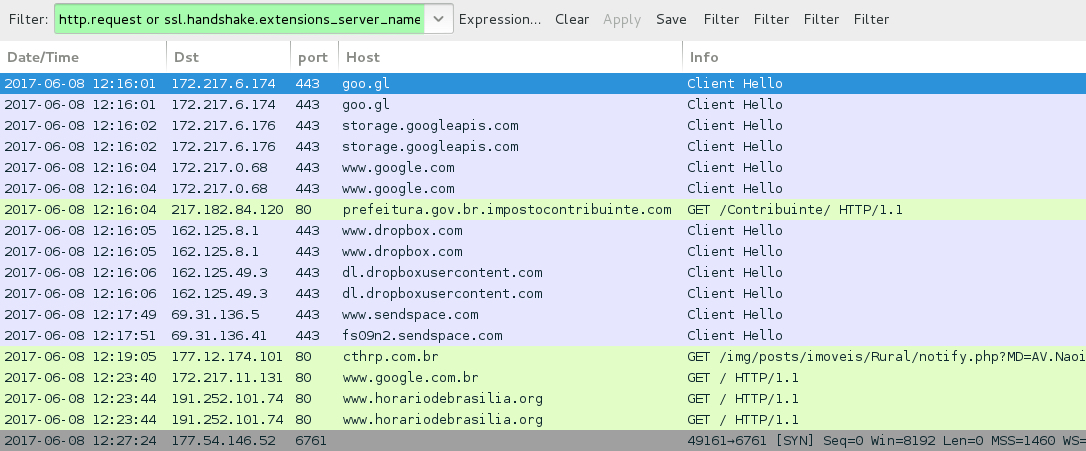
Shown above: Traffic from the infection filtered in Wireshark.
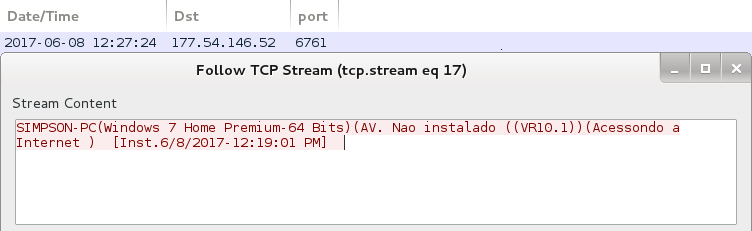
Shown above: Some of the post-infection traffic.
ASSOCIATED DOMAINS AND URLS:
- goo[.]gl - GET /ouqxbP [HTTPS traffic]
- storage.googleapis[.]com - GET /contribuinte/2via.html [HTTPS traffic]
- 217.182.84[.]120 port 80 - prefeitura[.]gov[.]br.impostocontribuinte[.]com - GET /Contribuinte/
- www.dropbox[.]com - GET /s/fe62ltwktduo2dg/Iptu-_-2017.zip?dl=1 [HTTPS URL for initial malware]
- www.sendspace[.]com - unknown URL [HTTPS traffic]
- fs09n2.sendspace[.]com - unknown URL [HTTPS traffic for follow-up malware]
- 177.12.174[.]101 port 80 - cthrp[.]com[.]br - callback traffic/check-in
- 191.252.101[.]74 port 80 - www.horariodebrasilia[.]org - GET / [connectivity check?]
- 177.54.146[.]52 port 6761 - hinv8cwfrkp.ddns[.]net - callback traffic, not encrypted
FILE HASHES
ZIP ARCHIVE AFTER CLICKING LINK FROM THE EMAIL:
- SHA256 hash: fd345c6cc9bbb17c8852f6fcdf9e9561d2d676c21abc1e4aec51b3d1c5a337e5
File size: 1,126,288 bytes
File name: Iptu-_-2017.zip
FILE EXTRACTED FROM THE ZIP ARCHIVE:
- SHA256 hash: bb38ee84fa3be8a1690e1a16420d0580abc3704b987065ec14e601c22e62c4f4
File size: 1,126,288 bytes
File name: Iptu-_-2017.exe
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: b4b6210013bd25880e31f5300cc51f2e99c2e7cfb5b13438d419b35fd744a888
File size: 9,660,419 bytes
File location: C:\Users\[username]\AppData\Local\temps2d4a\63466336034690346.etwe
File description: Zip archive - deleted after files are extracted
Shown above: Zip archive downloaded during the infection.
- SHA256 hash: d4cbf49c16febf85c3e5ef7b8d496f0be15989bbf8e54e1e25c4335d2e95ad9b
File size: 411,418,624 bytes
File location: C:\Users\[username]\AppData\Local\temps2d4a\NGtoolzXamp0.exe
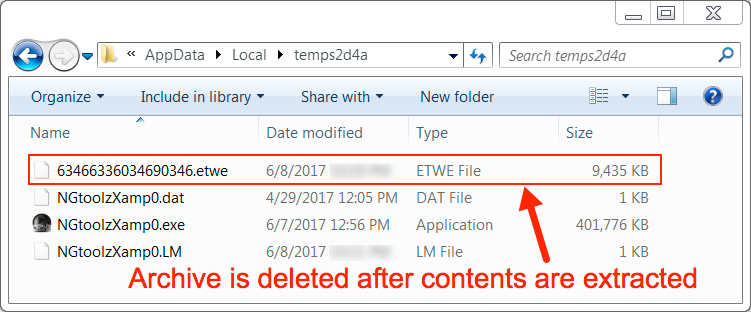
Shown above: Files noted on the infected host.
Click here to return to the main page.