2017-06-08 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-08-Hancitor-infection-with-ZLoader.pcap.zip 8.3 MB (8,253,203 bytes)
- 2017-06-08-Hancitor-malspam-traffic.pcap (8,831,992 bytes)
- 2017-06-08-Hancitor-malspam-5-examples.zip 7.4 kB (7,415 bytes)
- 2017-06-08-Hancitor-malspam-1520-UTC.eml (3,613 bytes)
- 2017-06-08-Hancitor-malspam-1529-UTC.eml (3,613 bytes)
- 2017-06-08-Hancitor-malspam-1549-UTC.eml (3,616 bytes)
- 2017-06-08-Hancitor-malspam-1644-UTC.eml (3,607 bytes)
- 2017-06-08-Hancitor-malspam-1650-UTC.eml (3,602 bytes)
- 2017-06-08-malware-from-Hancitor-infection.zip 253.6 kB (253,556 bytes)
- BN730D.tmp (202,752 bytes)
- Payment_Invoice_yahoo.doc (199,168 bytes)
SOME TWITTER ACCOUNTS THAT TWEETED ABOUT TODAY'S #HANCITOR MALSPAM:
EMAILS
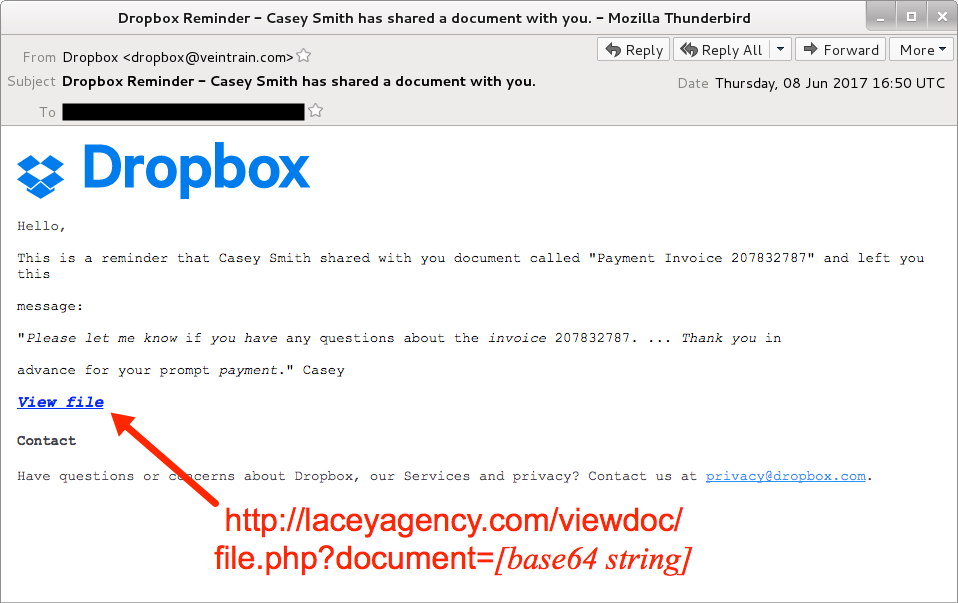
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date: Thursday 2017-06-08 as early as 15:20 UTC through at least 16:50 UTC
- From: "Dropbox" <dropbox@veintrain[.]com>
- Subject: Dropbox Reminder - Casey Smith has shared a document with you.
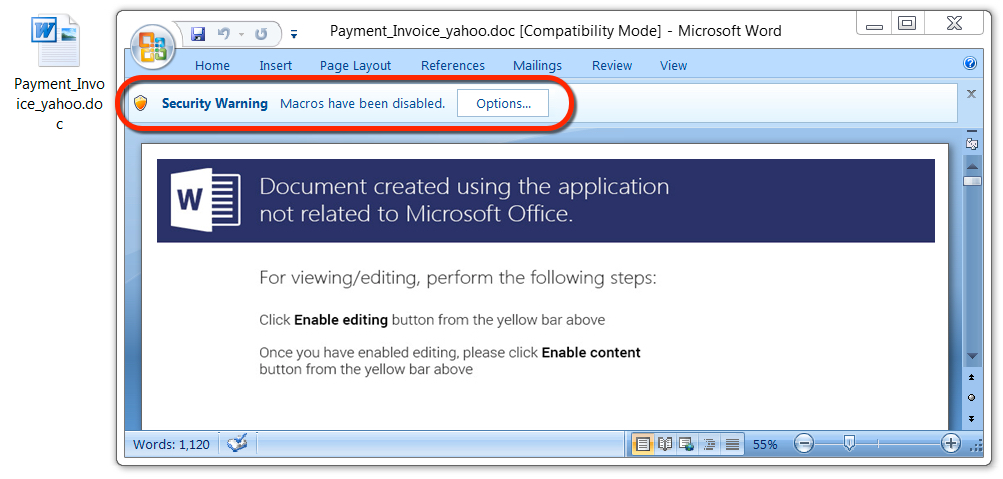
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
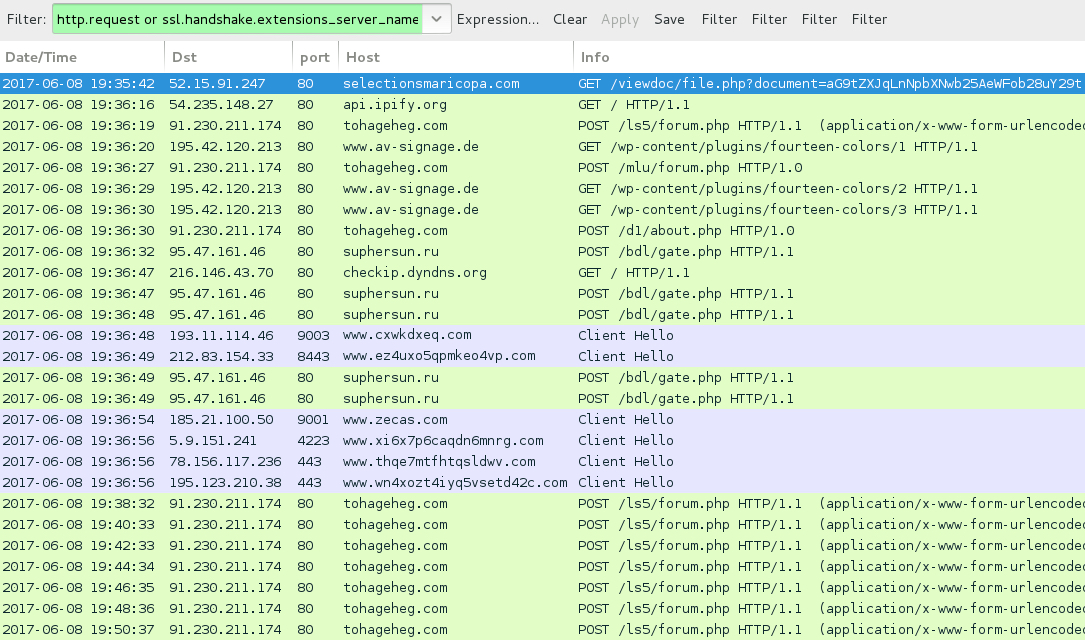
Shown above: Traffic from the infection filtered in Wireshark.
HTTP REQUESTS FOR THE WORD DOCUMENT:
- 52.15.91[.]247 port 80 - brri[.]in - GET /viewdoc/file.php?document=[base64 string]
- 52.15.91[.]247 port 80 - bucksinvestmentgroup[.]com - GET /viewdoc/file.php?document=[base64 string]
- 52.15.91[.]247 port 80 - BUCKSREALESTATECENTER[.]COM - GET /viewdoc/file.php?document=[base64 string]
- 184.168.221[.]51 port 80 - gottliebfamilypartnership[.]com - GET /viewdoc/file.php?document=[base64 string]
- 184.168.221[.]30 port 80 - laceyagency[.]com - GET /viewdoc/file.php?document=[base64 string]
- 52.15.91[.]247 port 80 - nhphomes[.]com - GET /viewdoc/file.php?document=[base64 string]
- 52.15.91[.]247 port 80 - PILOTCLUBLIFELINE[.]COM - GET /viewdoc/file.php?document=[base64 string]
- 52.15.91[.]247 port 80 - SAFELIFESENIORSC[.]COM - GET /viewdoc/file.php?document=[base64 string]
- 52.15.91[.]247 port 80 - scottshelp[.]com - GET /viewdoc/file.php?document=[base64 string]
- 52.15.91[.]247 port 80 - selectionsmaricopa[.]com - GET /viewdoc/file.php?document=[base64 string]
NAME FOR THE MALICIOUS WORD DOCUMENTS:
- Payment_Invoice_[recipient's email domain, minus the suffix].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 91.230.211[.]174 port 80 - tohageheg[.]com - POST /ls5/forum.php
- 91.230.211[.]174 port 80 - tohageheg[.]com - POST /mlu/forum.php
- 91.230.211[.]174 port 80 - tohageheg[.]com - POST /d1/about.php
- 195.42.120[.]213 port 80 - www.av-signage[.]de - GET /wp-content/plugins/fourteen-colors/1
- 195.42.120[.]213 port 80 - www.av-signage[.]de - GET /wp-content/plugins/fourteen-colors/2
- 195.42.120[.]213 port 80 - www.av-signage[.]de - GET /wp-content/plugins/fourteen-colors/3
- 95.47.161[.]46 port 80 - suphersun[.]ru - POST /bdl/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
OTHER INDICATORS FROM @CHEAPBYTE AND @JAMES_INTHE_BOX:
- 185.173.178[.]177 port 80 - downdintwiltit[.]ru - POST /ls5/forum.php
- 91.230.211[.]174 port 80 - lonemoning[.]ru - POST /ls5/forum.php
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 1c7f4150670158ab16e475f3641739d5adc40e191a64167f14c8c152be7fda82
File name: Payment_Invoice_yahoo.doc
File size: 199,168 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: d9ebab1937abaad9bafbffbc4d434a034bbef141a78a22b200f7da1f026f4ad1
File location: C:\Users\[username]\AppData\Local\Temp\BN730D.tmp
File size: 202,752 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
