2017-06-12 - URSNIF INFECTION FROM JAPANESE MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-12-Ursnif-infection-traffic.pcap.zip 307.9 kB (307,897 bytes)
- 2017-06-12-Ursnif-infection-traffic.pcap (349,173 bytes)
- 2017-06-12-malware-from-Ursnif-infection.zip 311.7 kB (311,708 bytes)
- emd.exe (306,688 bytes)
- の請求書2.xls (45,056 bytes)
NOTES:
- Big thanks to @tmmalanalyst who keeps a close eye on these waves of Ursnif malspam (link for today's tweet).
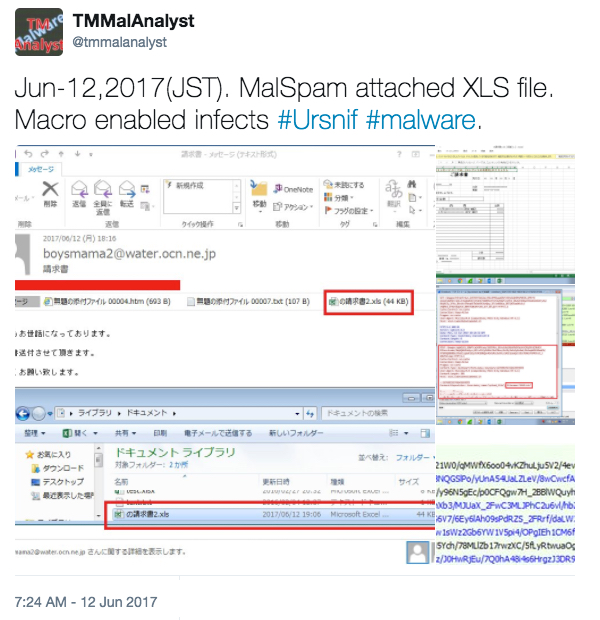
Shown above: Tweet from @tmmalanalyst.
EMAILS
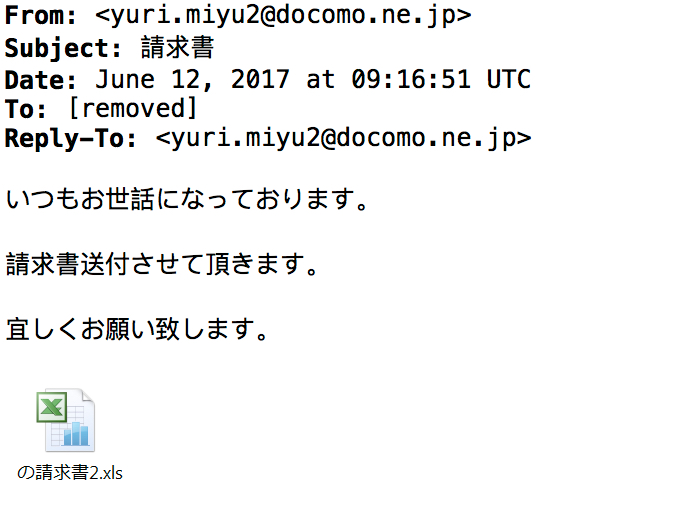
Shown above: Screen shot from the email.
EMAIL HEADERS:
- Date: Monday 2017-06-12 as early as 08:45 UTC through at least 09:16 UTC
- From: <aiuta-tmc.0611@jk9.so-net[.]ne[.]jp>
- From: <katsuy0s-10.dec.97@wonder.ocn[.]ne[.]jp>
- From: <media110@k.vodafone[.]ne[.]jp>
- From: <mkaraki.cbr250rr_cb1.ek9999@sakai.jcom[.]co[.]jp>
- From: <sophiaxah@eonet[.]ne[.]jp>
- From: <tetsulinlinlin@outlook[.]jp>
- From: <yuri.miyu2@sakai.jcom[.]co[.]jp>
- Subject: 請求書
- Attachment: の請求書2.xls
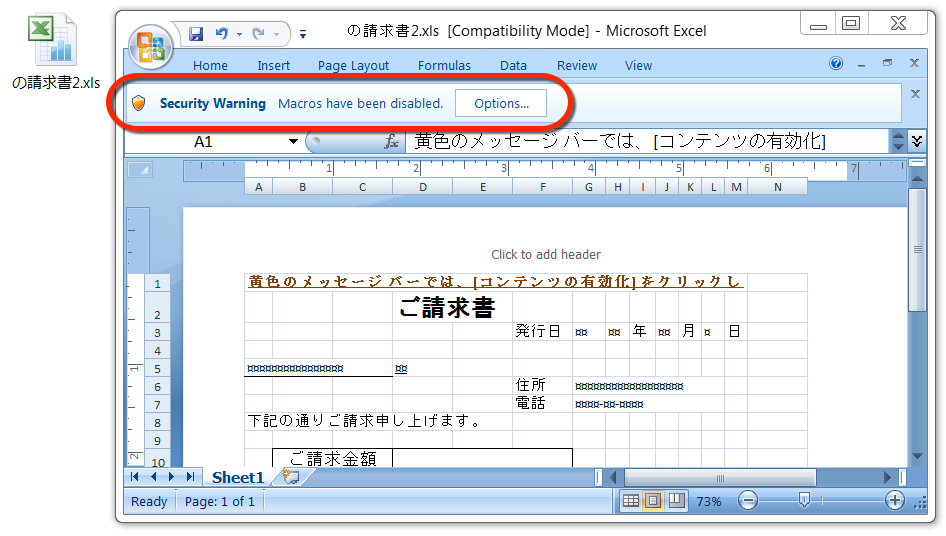
Shown above: Malicious Excel spreadsheet from the malspam.
TRAFFIC
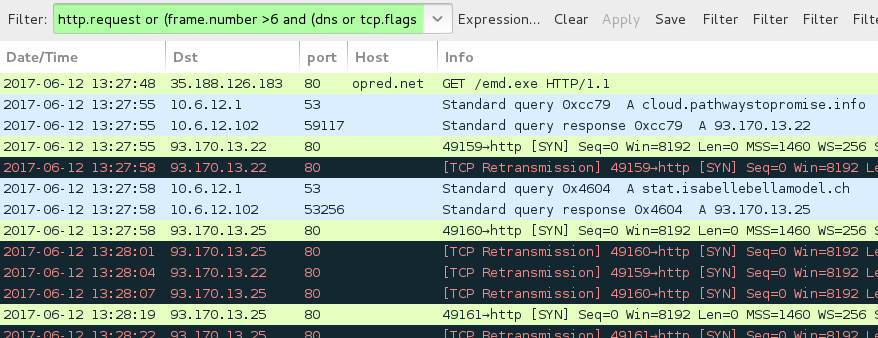
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 35.188.126[.]183 port 80 - opred[.]net - GET /emd.exe [HTTP request for Ursnif binary after enabling macros on the Excel spreadsheet]
- 93.170.13[.]22 port 80 - cloud.pathwaystopromise[.]info - Ursnif post-infection callback
- 93.170.13[.]25 port 80 - stat.isabellebellamodel[.]ch - Ursnif post-infection callback
- NOTE: Unlike @tmmalanalyst, I never got a TCP connection for the post-infection traffic. See images in @tmmalanalyst's tweet for more details on the post-infection traffic.
FILE HASHES
EXCEL SPREADSHEET FROM THE EMAIL:
- SHA256 hash: a82024fbe5d6be2049d9d36c050202cac59078808f531d161419fee46cdab017
File size: 45,056 bytes
File name: の請求書2.xls
URSNIF MALWARE:
- SHA256 hash: 38e0e29d154165a0966dce4aed6d464b4c8f461f19d08e8e726a6d795302a2c2
File size: 306,688 bytes
HTTP request: opred[.]net/emd.exe
Location on the infected Windows host: C:\Users\[username]\AppData\Roaming\Microsoft\Consutil\api-prop.exe
IMAGES
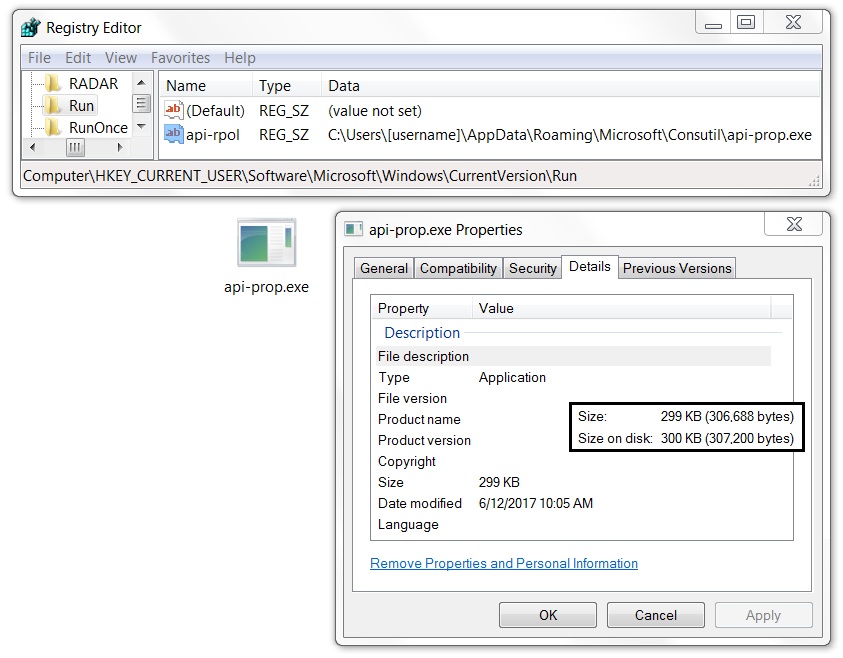
Shown above: Updated Windows registry for malware persistence.
Click here to return to the main page.
