2017-06-12 - HAWKEYE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-12-Hawkeye-infection-traffic.pcap.zip 600.1 kB (600,094 bytes)
- 2017-06-12-Hawkeye-infection-traffic.pcap (712,789 bytes)
- 2017-06-12-email-and-malware-from-Hawkeye-infection.zip 904.3 kB (904,323 bytes)
- 2017-06-12-Hawkeye-malspam.eml (253,322 bytes)
- Payment2017.doc (180,224 bytes)
- 2017-06-12-Hawkeye-malware.exe (661,480 bytes)
EMAILS
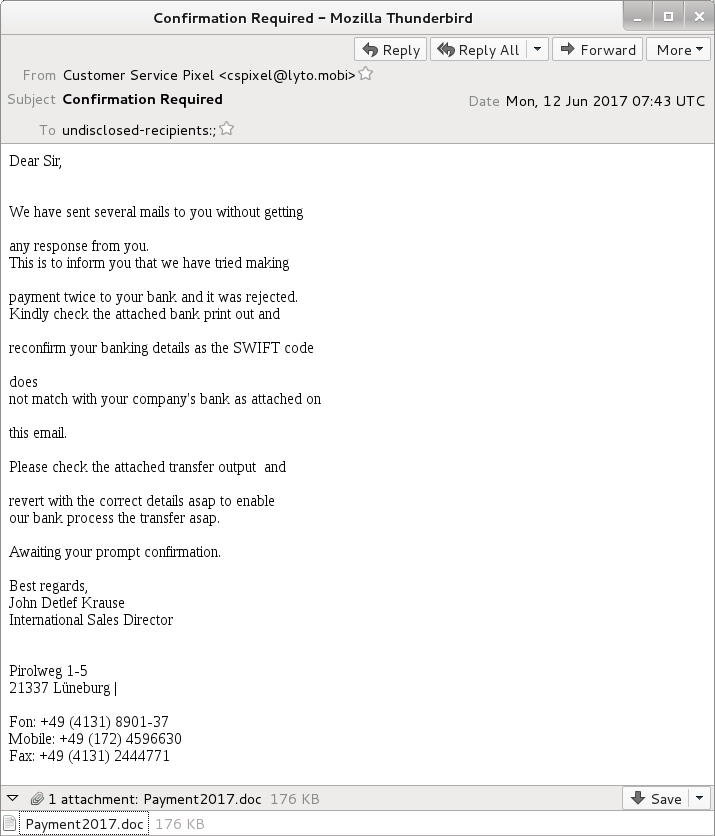
Shown above: Screen shot from the email.
EMAIL HEADERS:
- Date: Monday 2017-06-12 at 07:43 UTC
- From: Customer Service Pixel <cspixel@lyto[.]mobi>
- Subject: Confirmation Required
- Attachment: Payment2017.doc
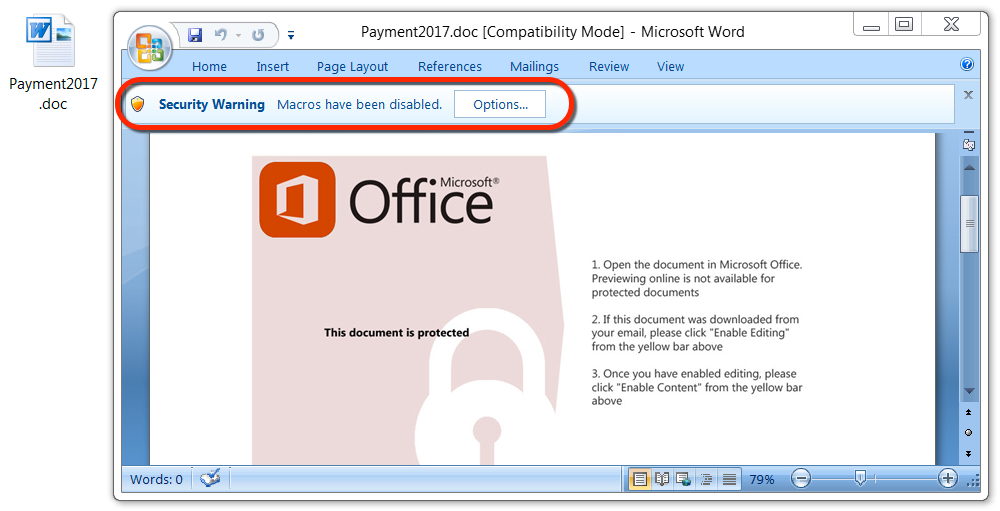
Shown above: Malicious Word document from the malspam.
TRAFFIC
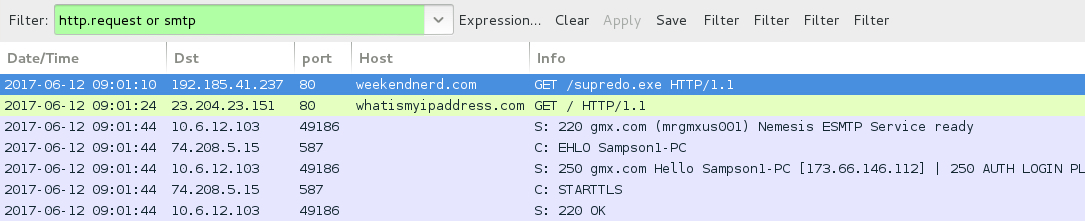
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 192.185.41[.]237 port 80 - weekendnerd[.]com - GET /supredo.exe [HTTP request for Hawkeye malware after enabling macros on the Word document]
- whatismyipaddress[.]com - Post-infection location check
- port 587 - smtp.mail[.]com - Hawkeye data exfiltration email sent from the infected host via encrypted SMTP
FILE HASHES
WORD DOCUMENT FROM THE EMAIL:
- SHA256 hash: 1ad96e21f18c6c337e75d05d632ea020e409921784249a919f945056d30b1e0c
File size: 180,224 bytes
File name: Payment2017.doc
FOLLOW-UP MALWARE (HAWKEYE):
- SHA256 hash: f5f915bab2da6d58e9c07823cd89594f631425a041cd2e642b5f1a64ca23203e
File size: 661,480 bytes
HTTP request: weekendnerd[.]com/supredo.exe
Location on the infected Windows host: C:\Users\[username]\AppData\Roaming\Cpudlls.exe
Click here to return to the main page.
