2017-06-13 - JAFF RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-13-Jaff-ransomware-infection-traffic.pcap.zip 15.6 kB (15,642 bytes)
- 2017-06-13-malspam-tracker-for-Jaff-ransomware.csv.zip 1.3 kB (1,266 bytes)
- 2017-06-13-Jaff-ransomware-emails-and-malware.zip 474.4 kB (474,438 bytes)
SOME TWEETS OR BLOG POSTS ABOUT TODAY'S #JAFF #RANSOMWARE MALSPAM:
- @peterkruse: Several active #Jaff #Ransomware C&C servers now hosted at: AS132203, Singapore Tencent Cloud Computing (beijing) Co. Ltd. (link)
- @tmmalanalyst: Jun-13,2017(JST). MalSpam attached ZIP file -> zip -> wsf. Infected #Jaff #ransomware. (link)
EMAILS
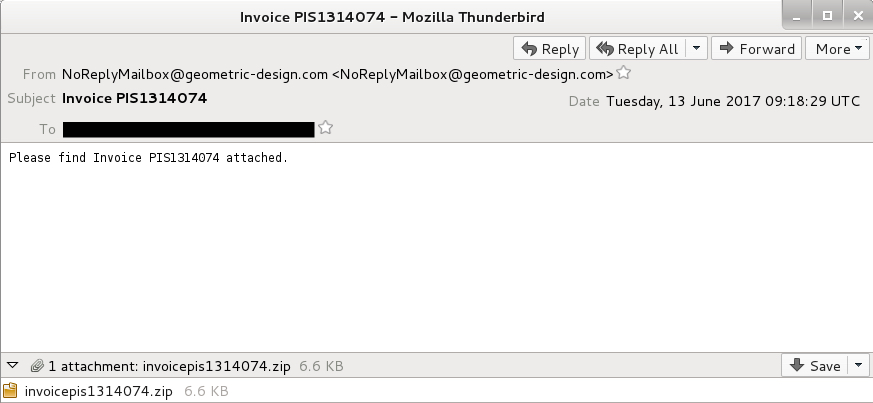
Shown above: An example of the emails.
10 EXAMPLES:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME -- ZIP IN THE ZIP -- EXTRACTED .WSF FILE
- 2017-06-13 09:18:29 UTC -- NoReplyMailbox@geometric-design[.]com -- Invoice PIS1314074 -- invoicepis1314074.zip -- JPS8FFO1.zip -- JPS8FFO1.wsf
- 2017-06-13 09:38:17 UTC -- NoReplyMailbox@najmi[.]de -- Invoice PIS6680000 -- invoicepis6680000.zip -- OOJVFMYO2.zip -- OOJVFMYO2.wsf
- 2017-06-13 10:52:21 UTC -- NoReplyMailbox@karimlounes[.]com -- Invoice PIS5416591 -- invoicepis5416591.zip -- AXQ4CXPA.zip -- AXQ4CXPA.wsf
- 2017-06-13 12:32:24 UTC -- NoReplyMailbox@proteralabs[.]com -- Invoice PIS2233669 -- invoicepis2233669.zip -- FTOZTGYDZ.zip -- FTOZTGYDZ.wsf
- 2017-06-13 13:11:16 UTC -- NoReplyMailbox@coljohnt[.]com -- Invoice PIS2511038 -- invoicepis2511038.zip -- N82QC77I.zip -- N82QC77I.wsf
- 2017-06-13 13:16:07 UTC -- NoReplyMailbox@atomacon[.]org -- Invoice PIS1695072 -- invoicepis1695072.zip -- OEOOWNGE.zip -- OEOOWNGE.wsf
- 2017-06-13 13:29:52 UTC -- NoReplyMailbox@spedders.worldonline[.]co[.]uk -- Invoice PIS0413254 -- invoicepis0413254.zip -- JODUBWOOW.zip -- JODUBWOOW.wsf
- 2017-06-13 14:30:29 UTC -- NoReplyMailbox@lidercontab[.]com -- Invoice PIS2436728 -- invoicepis2436728.zip -- MTSUQM4J.zip -- MTSUQM4J.wsf
- 2017-06-13 15:13:59 UTC -- NoReplyMailbox@tornadowristbands[.]com -- Invoice PIS9587975 -- invoicepis9587975.zip -- HF4YIDIIL.zip -- HF4YIDIIL.wsf
- 2017-06-13 15:22:53 UTC -- NoReplyMailbox@benjaminandbanks[.]com -- Invoice PIS8938690 -- invoicepis8938690.zip -- B9UHRNO5.zip -- B9UHRNO5.wsf
MALWARE
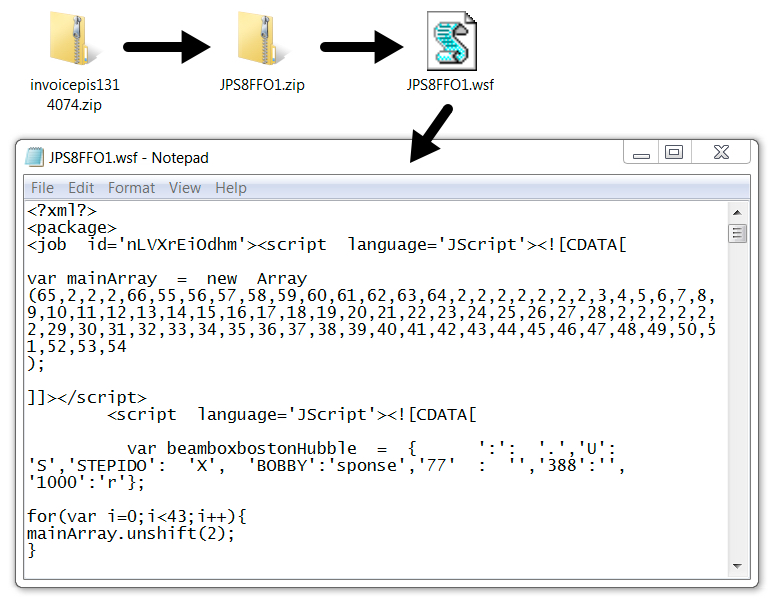
Shown above: An example of the malware attached to the malspam.
SHA256 HASHES FOR THE ZIP ATTACHMENTS:
- 6643ae22814b118da4af55b365d62ba5c032b66e9717cde499c4e578d6fe3aa7 - invoicepis0413254.zip
- 8be825e2a658d5c23bf434cf4b52fd6c7d6b8ff7184274622b4fd1178e72d738 - invoicepis1314074.zip
- b8fce962dea3d0f76f020bc89402b69df272ed81569bdd302ace4ff4a054e0ac - invoicepis1695072.zip
- 7f7423a76c055116f55a424fb5fa03069a63db3d06b764bba057bb9678e95a32 - invoicepis2233669.zip
- b808ab2a7be1c153fb3511c5dff97a9cd1c645628933c545edf91001af52bdfe - invoicepis2436728.zip
- 5bc0649ae27083ba74eddd3d9f98cd1d1733cb1c1a5a1790f0fa979c0604db38 - invoicepis2511038.zip
- 62ff866da9576e2b178f6385465c45f4773ce37fcae0c101865d71d1c4500ea3 - invoicepis5416591.zip
- 0daffeae3bba397f66565872c0a97f436f23deac3e5d1ee1eb76d67006e1956e - invoicepis6680000.zip
- 51d30e6b11a2a1b0e963644d50bb43fc4ba58e4f5864c0999a69ad7001256b28 - invoicepis8938690.zip
- ff788450fff963c894cdc4eb909e7b59a2a4896c325d44164ccc9acc93122c00 - invoicepis9587975.zip
SHA256 HASHES FOR THE EXTRACTED .WSF FILES:
- 78559cb2823bcc6652ce6d5b9b4049b8b3a1147373d310f820ce6a943d107f9b - AXQ4CXPA.wsf
- 88fedc4d8bae75ff479f279d32c347b9fc46db34aad8548322e8b343b5f1f36d - B9UHRNO5.wsf
- 00055a1a81ca4522d0c849843dd82482beb0c0a11e077eab92ce29500e699ab5 - FTOZTGYDZ.wsf
- cf8236b8f144ccb425d031d2cf00aaedba438718eccf878ddf52c23c56c8ae2a - HF4YIDIIL.wsf
- e6e83f833b75e15437611c0b3ba0ff074861f47641e9807b9fd80cfcedc535e0 - JODUBWOOW.wsf
- 3bca60bc39b2477fe678c5ae42d3d9b3e6a4c841005e513544f18d82b5808fdd - JPS8FFO1.wsf
- 67cf8484de51cc971cea3b83abc6a1faf4eee5bed13fd1278a6c94382be8027e - MTSUQM4J.wsf
- be22ebcc446ca3c537256f14ae114bf4e2e2a131e8bbc153d6605a0e089493a9 - N82QC77I.wsf
- 07e014544fa7c3f6553dfb8ad82e0c83c7bbab5f60558fa3f64a70ea0d7cc1f1 - OEOOWNGE.wsf
- 4d581ef9c463ab6496d340335cec683833794b2efb1edde70a3c63726bcd008c - OOJVFMYO2.wsf
RANSOMWARE RETRIEVED FROM INFECTED HOST:
- SHA256 hash: 001268d7fad7806705b3710ccc8cfffb2c2cfb830a273d7a0f87a5fa6422b9f5
File size: 174,592 bytes
File description: Windows EXE for Jaff ransomware
TRAFFIC
URLS FROM THE .WSF FILES TO DOWNLOAD JAFF RANSOMWARE:
- 16892[.]net - GET /984hvxd?[short string of characters]
- 78tguyc876wwirglmltm[.]net - GET /af/984hvxd?[short string of characters]
- aarontax[.]com - GET /984hvxd?[short string of characters]
- abyzon[.]com - GET /984hvxd?[short string of characters]
- careermag[.]in - GET /984hvxd?[short string of characters]
- ciiltire[.]com - GET /984hvxd?[short string of characters]
- cinema-strasbourg[.]com - GET /984hvxd?[short string of characters]
- e67tfgc4uybfbnfmd[.]org - GET /af/984hvxd?[short string of characters]
- makkahhaj[.]com - GET /984hvxd?[short string of characters]
- mseconsultant[.]com - GET /984hvxd?[short string of characters]
- oscarbenson[.]com - GET /984hvxd?[short string of characters]
- qiyuner[.]com - GET /984hvxd?[short string of characters]
- scjjh[.]cn - GET /984hvxd?[short string of characters]
- sock[.]lt - GET /984hvxd?[short string of characters]
- speedgrow[.]com - GET /984hvxd?[short string of characters]
- yes2malaysia[.]com - GET /984hvxd?[short string of characters]
- zabandan[.]com - GET /984hvxd?[short string of characters]
- zebtex[.]com - GET /984hvxd?[short string of characters]
JAFF RANSOMWARE POST-INFECTION TRAFFIC:
- 119.28.98.205 port 80 - hv7verjdhfbvdd44f[.]info - GET /a5/
- rktazuzi7hbln7sy[.]onion - Tor domain for Jaff Decryptor [same Decryptor domain since Jaff first appeared on 2017-05-11]
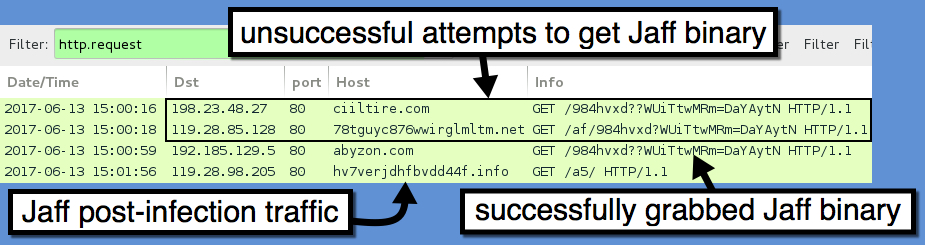
Shown above: Traffic from the infection filtered in Wireshark.
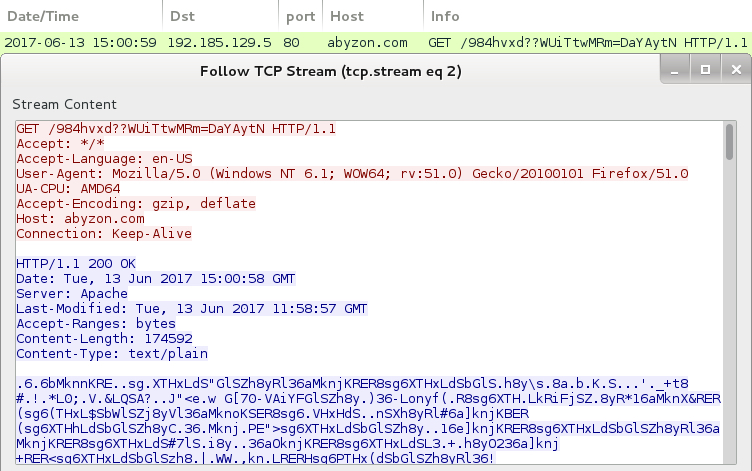
Shown above: HTTP request for the Jaff ransomware.
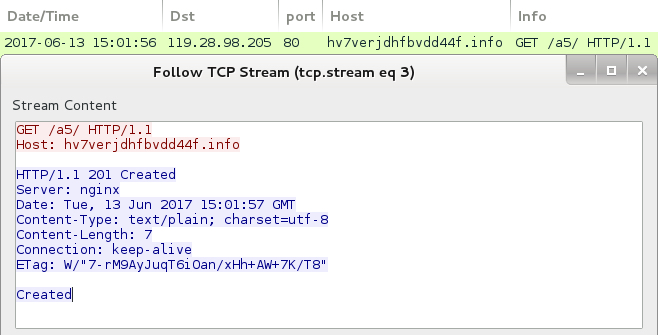
Shown above: Post-infection traffic from the infected Windows host.
IMAGES
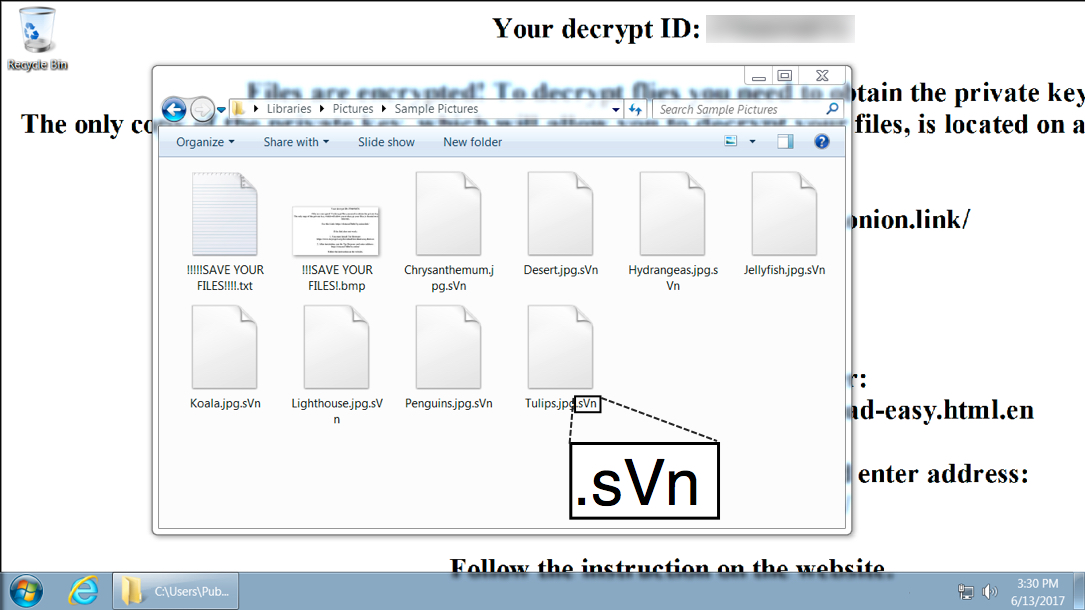
Shown above: Desktop of an infected Windows host.
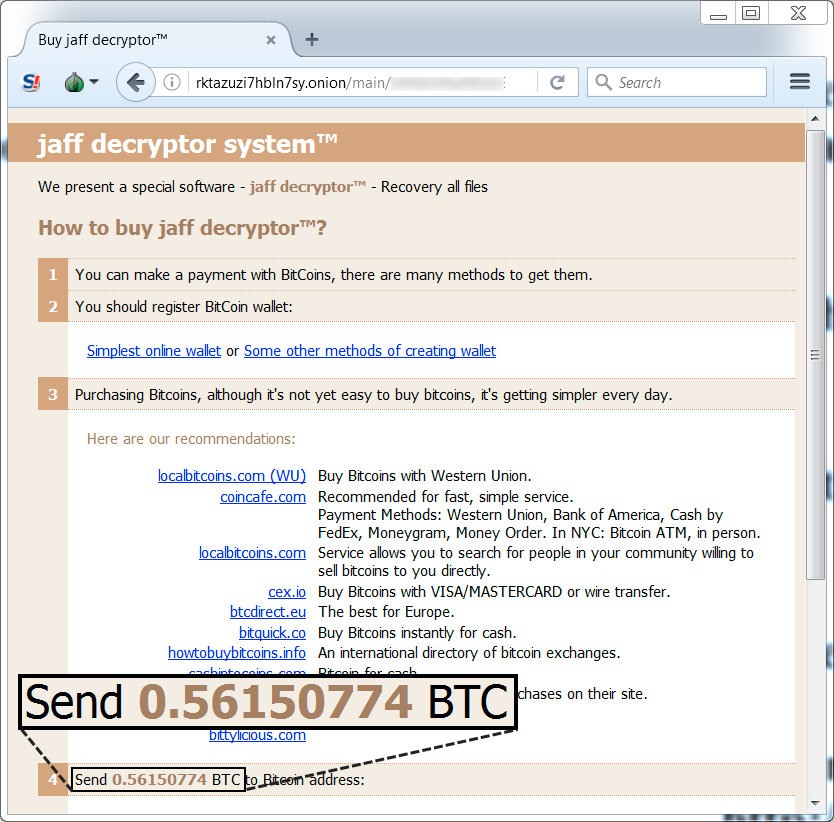
Shown above: Going to the Jaff Decryptor.
Click here to return to the main page.
