2017-06-15 - RIG EK (HOOKADS AND SEAMLESS CAMPAIGNS)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-15-Rig-EK-six-pcaps.zip 7.2 MB (7,235,888 bytes)
- 2017-06-15-1st-run-Seamless-Rig-EK-sends-Ramnit.pcap (993,395 bytes)
- 2017-06-15-2nd-run-Seamless-Rig-EK-sends-Ramnit.pcap (880,020 bytes)
- 2017-06-15-3rd-run-Hookads-Rig-EK-sends-Dreambot.pcap (609,685 bytes)
- 2017-06-15-4th-run-Hookads-Rig-EK-sends-Dreambot.pcap (370,858 bytes)
- 2017-06-15-5th-run-Hookads-Rig-EK-sends-Dreambot.pcap (4,029,509 bytes)
- 2017-06-15-6th-run-Seamless-Rig-EK-sends-Ramnit.pcap (870,270 bytes)
- 2017-06-15-Rig-EK-artifacts-and-malware.zip 677.9 kB (677,920 bytes)
- 2017-06-15-1st-run-Rig-EK-landing-page.txt (121,845 bytes)
- 2017-06-15-2nd-run-Rig-EK-landing-page.txt (121,645 bytes)
- 2017-06-15-3rd-run-Rig-EK-landing-page.txt (61,241 bytes)
- 2017-06-15-4th-run-Rig-EK-landing-page.txt (121,599 bytes)
- 2017-06-15-5th-run-Rig-EK-landing-page.txt (61,001 bytes)
- 2017-06-15-6th-run-Rig-EK-landing-page.txt (60,940 bytes)
- 2017-06-15-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-06-15-Rig-EK-artifact-OTTYUADAF.txt (1,137 bytes)
- 2017-06-15-Rig-EK-flash-exploit-first-3-runs.swf (16,299 bytes)
- 2017-06-15-Rig-EK-flash-exploit-last-3-runs.swf (16,299 bytes)
- 2017-06-15-HookAds-Rig-EK-payload-Dreambot.exe (251,392 bytes)
- 2017-06-15-Seamless-Rig-EK-payload-Ramnit.exe (249,864 bytes)
BACKGROUND ON THE CAMPAIGNS:
- 2016-11-01 - Malwarebytes Blog: The HookAds malvertising campaign (link)
TRAFFIC
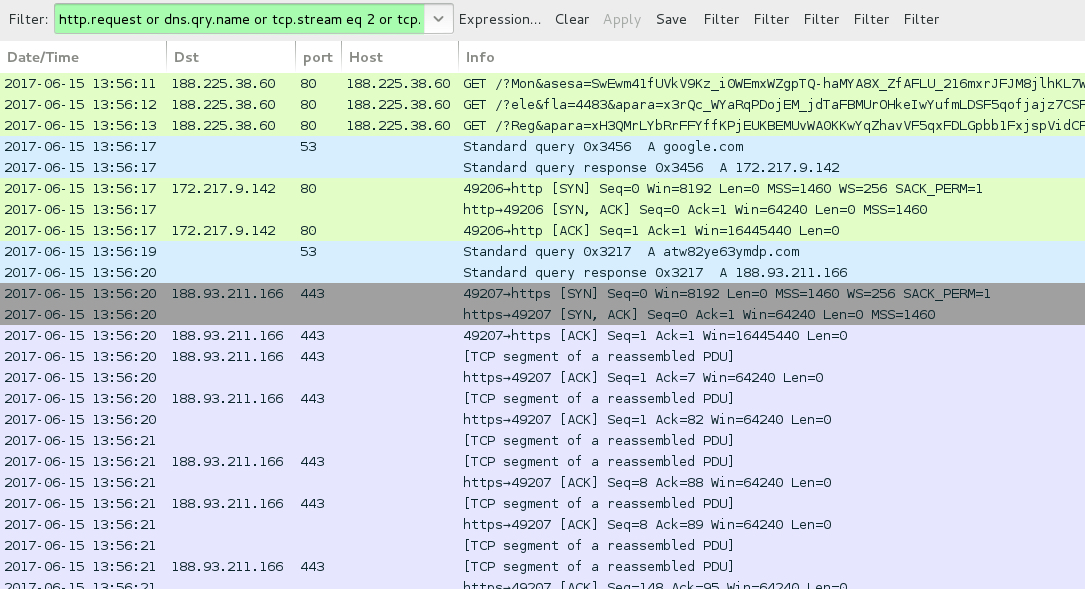
Shown above: Traffic from one of the Seamless campaign infections filtered in Wireshark.
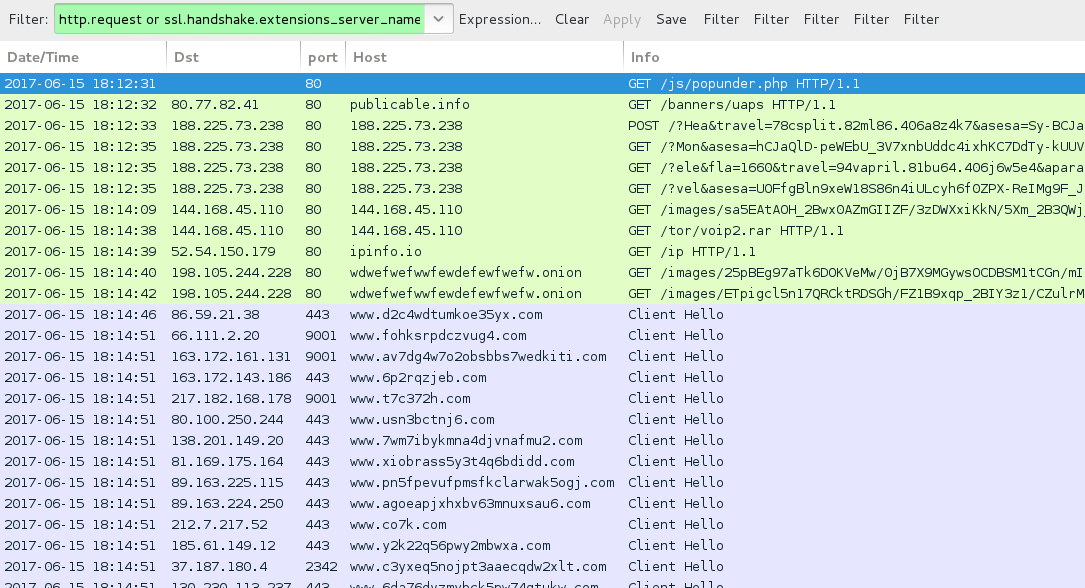
Shown above: Traffic from one of the HookAds campaign infections filtered in Wireshark.
ASSOCIATED DOMAINS:
- [ip address redacted] port 80 - [domain redacted] - GET [URL redacted] - Seamless redirect
- [ip address redacted] port 80 - [domain redacted] - GET /js/popunder.php - URL from site leading to HookAds redirect
- 80.77.82[.]41 port 80 - promose[.]info - GET /banners/uaps - HookAds redirect (1 of 2)
- 80.77.82[.]41 port 80 - publicable[.]info - GET /banners/uaps - HookAds redirect (2 of 2)
- 188.225.38[.]60 port 80 - 188.225.38[.]60 - Rig EK (1st run)
- 188.225.73[.]238 port 80 - 188.225.73[.]238 - Rig EK (2nd through 6th runs)
- google.com - Ramnit post-infection connectivity check (dns and TCP connection but no actual HTTP taffic)
- 188.93.211[.]166 port 443 - atw82ye63ymdp[.]com - Ramnit post-infection traffic (encrypted)
- 144.168.45[.]110 port 80 - 144.168.45[.]110 - GET /images/[long string of characters].avi - Dreambot post-infection traffic
- 144.168.45[.]110 port 80 - 144.168.45[.]110 - GET /tor/voip2.rar - Dreambot post-infection traffic
- ipinfo[.]io - GET /ip - Dreambot post-infection location check
- 198.105.244[.]228 port 80 - wdwefwefwwfewdefewfwefw[.]onion - GET /images/[long string of characters].jpeg - Dreambot post-infection traffic
- 198.105.244[.]228 port 80 - wdwefwefwwfewdefewfwefw[.]onion - GET /images/[long string of characters].gif - Dreambot post-infection traffic
- various IP addresses on various ports - various domains - Dreambot post-infection Tor traffic
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 5834d95ebd3c93b0e629a43affec651a3a9c3c5e3c430c37deef5608da0d8110
File size: 16,299 bytes
File description: Rig EK flash exploit on 2017-06-15 (1 of 2)
- SHA256 hash: 14e6a9025e7a268c33c98a6343179efc723a3fca80093f8c4ab58cf4d7c38798
File size: 16,299 bytes
File description: Rig EK flash exploit on 2017-06-15 (2 of 2)
MALWARE RETRIEVED FROM THE INFECTED HOSTS:
- SHA256 hash: ca293693efbe0dca2b152e632fc8df70212994f00c471dc994034e53b6364dae
File size: 251,392 bytes
File description: Rig EK payload from Hookads campaign on 2017-06-15 - Dreambot
- SHA256 hash: de5c83e00f7bd1422fbe1317180efe0645c865a3b7e67f512e7cd425fb728cb6
File size: 249,864 bytes
File description: Rig EK payload from Seamless campaign on 2017-06-15 - Ramnit
Click here to return to the main page.
