2017-06-20 - RIG EK FROM HOOKADS CAMPAIGN SENDS DREAMBOT & CHTHONIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-20-HookAds-Rig-EK-two-pcaps.zip 5.2 MB (5,232,207 bytes)
- 2017-06-20-1st-run-HookAds-Rig-EK-sends-Dreambot-and-Chthonic.pcap (1,888,062 bytes)
- 2017-06-20-2nd-run-HookAds-Rig-EK-sends-Dreambot.pcap (3,694,234 bytes)
- 2017-06-20-HookAds-Rig-EK-artifacts-and-malware.zip 501.8 kB (501,759 bytes)
- 2017-06-20-1st-and-2nd-runs-HookAds-Rig-EK-payload-Dreambot.exe (218,624 bytes)
- 2017-06-20-1st-and-2nd-runs-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-06-20-1st-and-2nd-runs-Rig-EK-flash-exploit.swf (16,299 bytes)
- 2017-06-20-1st-run-HookAds-Rig-EK-payload-Chthonic.exe (351,232 bytes)
- 2017-06-20-1st-run-Rig-EK-landing-page.txt (121,380 bytes)
- 2017-06-20-2nd-run-Rig-EK-landing-page.txt (121,419 bytes)
BACKGROUND ON THE HOOKADS CAMPAIGN:
- 2016-11-01 - Malwarebytes Blog: The HookAds malvertising campaign (link)
OTHER NOTES:
- The first run has two instances of Rig EK from the HookAds campaign.
- The first run also has two different payloads: Dreambot and Chthonic
- No post-infection was seen from Dreambot in the first run.
TRAFFIC
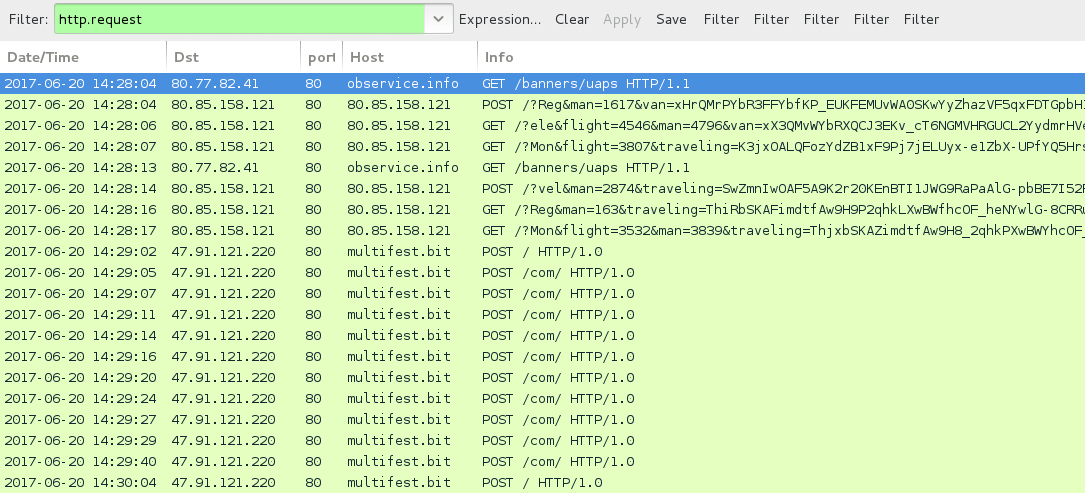
Shown above: Traffic from the 1st run filtered in Wireshark.
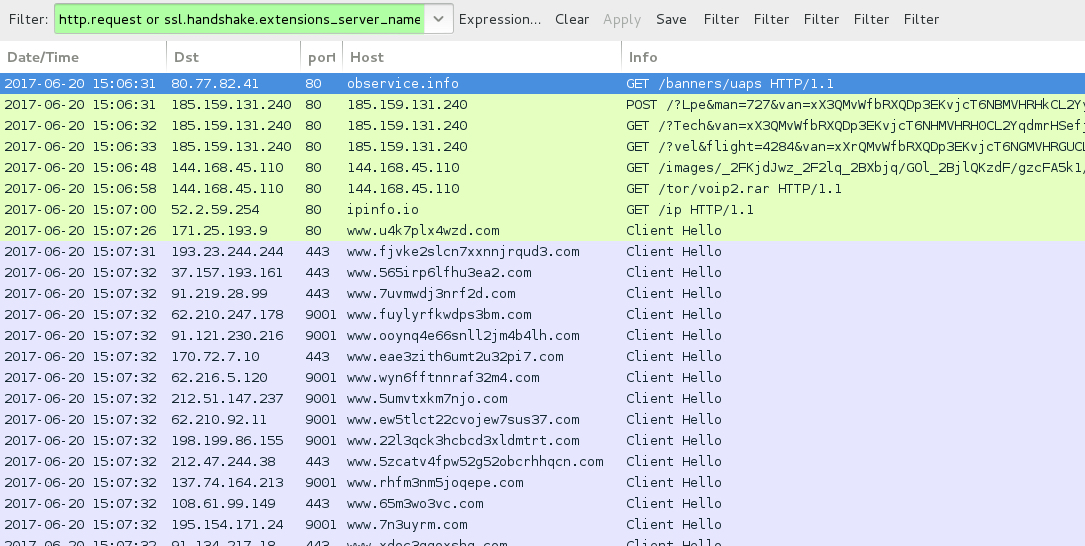
Shown above: Traffic from the 2nd run filtered in Wireshark.
ASSOCIATED DOMAINS:
- 80.77.82[.]41 port 80 - observice[.]info - GET /banners/uaps [HookAds redirect]
- 80.85.158[.]121 port 80 - 80.85.158[.]121 - Rig EK (1st run)
- 185.159.131[.]240 port 80 - 185.159.131[.]240 - Rig EK (2nd run)
- 47.91.121[.]220 port 80 - multifest[.]bit - POST / [Chthonic post-infection traffic]
- 47.91.121[.]220 port 80 - multifest[.]bit - POST /com/ [Chthonic post-infection traffic]
- 52.174.55[.]168 port 53 - DNS queries for multifest[.]bit [Chthonic post-infection traffic]
- 51.255.48[.]78 port 53 - DNS queries for A multifest[.]bit [Chthonic post-infection traffic]
- 144.168.45[.]110 port 80 - 144.168.45[.]110 - GET /images/[long string of characters].avi - [Dreambot post-infection traffic]
- 144.168.45[.]110 port 80 - 144.168.45[.]110 - GET /tor/voip2.rar - [Dreambot post-infection traffic]
- ipinfo[.]io - GET /ip - [Dreambot post-infection location check]
- DNS query for wdwefwefwwfewdefewfwefw[.]onion - did not resolve - [Dreambot post-infection location check]
- Various IP addresses various ports - Tor traffic - [Dreambot post-infection]
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 892b3990a09bb3391c5a1a591d9908a0e77db7385addc2c38cfcb32db265a970
File size: 16,299 bytes
File description: Rig EK flash exploit on 2017-06-20 (1st and 2nd runs)
MALWARE RETRIEVED FROM THE INFECTED HOSTS:
- SHA256 hash: 1fd7b6b244cbcac394452f540ef373fd5bfaa402273b29252f06edf2fd0432b7
File size: 218,624 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File description: HookAds campaign Rig EK payload of Dreambot on 2017-06-20 (1st and 2nd runs) - Dreambot
- SHA256 hash: 192c3580b679a1c4e82f428e85d098d9b866676073d083b1eb312ead8d01ca39
File size: 351,232 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File description: HookAds campaign Rig EK payload of Chthonic on 2017-06-20 (1st run) - Dreambot
Click here to return to the main page.
