2017-06-21 - RIG EK SENDS BUNITU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-21-Rig-EK-sends-Bunitu.pcap.zip 274 kB (273,571 bytes)
- 2017-06-21-Rig-EK-sends-Bunitu.pcap (294,060 bytes)
- 2017-06-21-Rig-EK-artifacts-and-malware.zip 253.1 kB (253,105 bytes)
- 2017-06-21-Rig-EK-flash-exploit.swf (16,299 bytes)
- 2017-06-21-Rig-EK-landing-page.txt (121,339 bytes)
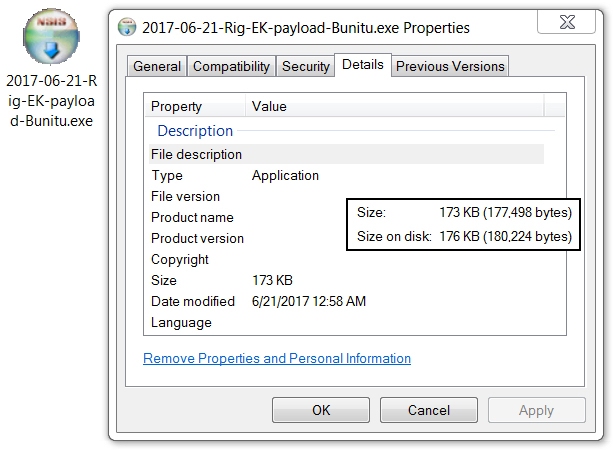
- 2017-06-21-Rig-EK-payload-Bunitu.exe (177,498 bytes)
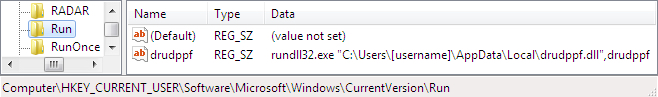
- 2017-06-21-post-infection-artifact-drudppf.dll (13,312 bytes)
OTHER NOTES:
- This traffic has the same characteristics as I saw on 2017-05-09 (same type of redirect, same type of payload).
TRAFFIC
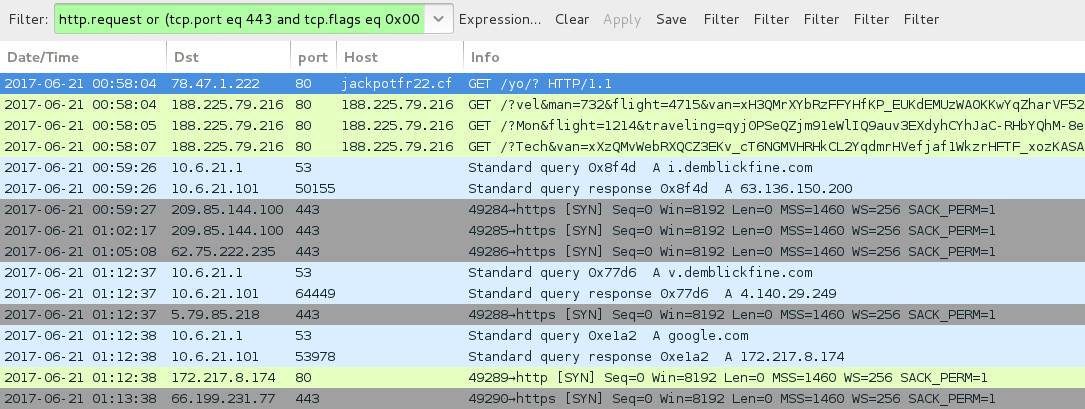
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 78.47.1[.222 port 80 - jackpotfr22[.]cf - GET /yo/? [gate to Rig EK]
- 188.225.79[.]216 port 80 - 188.225.79[.]216 - Rig EK
- 5.79.85[.]218 port 443 - Post-infection Bunitu traffic (encrypted but not HTTPS/SSL/TLS)
- 62.75.222[.]235 port 443 - Post-infection Bunitu traffic (encrypted but not HTTPS/SSL/TLS)
- 66.199.231[.]77 port 443 - Post-infection Bunitu traffic (encrypted but not HTTPS/SSL/TLS)
- 209.85.144[.]100 port 443 - Post-infection Bunitu traffic (encrypted but not HTTPS/SSL/TLS)
- DNS query for i.demblickfine[.]com - resolved to 63.136.150[.]200 but no follow-up traffic
- DNS query for v.demblickfine[.]com - resolved to 4.140.29[.]249 but no follow-up traffic
- google[.]com - Post-infection check by infected host - follow-up TCP connection but no HTTP traffic
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 892b3990a09bb3391c5a1a591d9908a0e77db7385addc2c38cfcb32db265a970
File size: 16,299 bytes
File description: Rig EK flash exploit on 2017-06-21 (1st and 2nd runs)
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: e7049140f7f07a48406a7de2e3a08fc8759af9f94de533210e99f69c34bc27aa
File size: 177,498 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File description: Rig EK payload of Bunitu on 2017-06-21
Shown above: The malware payload (re-named for today's malware archive).
- SHA256 hash: 951d15d83264c1ffd387fd871d3f0776e0016b00bc353e17c6911562da6e2169
File size: 13,312 bytes
File location: C:\Users\[username]\AppData\Local\drudppf.dll
File description: Post-infection artifact
Shown above: Windows registry update for persistence.
Click here to return to the main page.