2017-06-22 - LOCKY RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-22-Locky-ransomware-infection-traffic.pcap.zip 312.2 kB (312,236 bytes)
- 2017-06-22-Locky-ransomware-malspam-tracker.csv.zip 2.1 kB (2,075 bytes)
- 2017-06-22-Locky-ransomware-emails-and-malware.zip 3.3 MB (3,301,499 bytes)
EMAILS
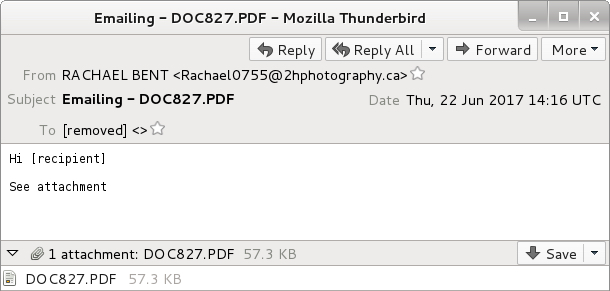
Shown above: An example of the emails.
20 EXAMPLES:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME (PDF) -- EMBEDDED .DOCM FILE
- 2017-06-22 11:12:25 UTC -- JOYCE GURR <Joyce4382@acmarmediagroup[.]com> -- Emailing - DOC787.PDF -- DOC787.PDF -- 000270630709.docm
- 2017-06-22 11:14:19 UTC -- HANNAH NICOLSON <Hannah6956@tecnolab-ba[.]com[.]br> -- Emailing - PDF806.PDF -- PDF806.PDF -- 000248089012.docm
- 2017-06-22 11:15:33 UTC -- MORGAN COOMBE <Morgan6045@magato[.]ru> -- Emailing - DOC199.PDF -- DOC199.PDF -- 000248089012.docm
- 2017-06-22 11:15:34 UTC -- KRISTEN MASSENGILL <Kristen0038@integratedphysio[.]net> -- Emailing - DOC999.PDF -- DOC999.PDF -- 000518024662.docm
- 2017-06-22 11:15:55 UTC -- ESTER LITTLEFAIR <Ester5226@edgeentertainment[.]se> -- Emailing - PDF064.PDF -- PDF064.PDF -- 000455383454.docm
- 2017-06-22 11:15:58 UTC -- ADRIENNE PEAKE <Adrienne3129@thebusinessjoint[.]com> -- Emailing - DOC514.PDF -- DOC514.PDF -- 000455383454.docm
- 2017-06-22 11:16:24 UTC -- LENORE RICHARDSON <Lenore5792@clocksoffracing[.]com> -- Emailing - DOC787.PDF -- DOC787.PDF -- 000455383454.docm
- 2017-06-22 11:17:11 UTC -- WILLIE BRADFIELD <Willie5496@efpotterappraisal[.]com> -- Emailing - DOC441.PDF -- DOC441.PDF -- 000890651955.docm
- 2017-06-22 11:17:38 UTC -- LEIF NOTT <Leif9322@lansay[.]com[.]br> -- Emailing - PDF537.PDF -- PDF537.PDF -- 000890651955.docm
- 2017-06-22 11:17:49 UTC -- CHASITY STREETER <Chasity3864@kirbywoods[.]com> -- Emailing - DOC702.PDF -- DOC702.PDF -- 000890651955.docm
- 2017-06-22 11:18:09 UTC -- LEIGH BLACKSTOCK <Leigh3122@forestcart[.]com> -- Emailing - PDF666.PDF -- PDF666.PDF -- 000731715784.docm
- 2017-06-22 11:19:31 UTC -- JERE FAWSETT <Jere1463@brooklinedemocrats[.]org> -- Emailing - PDF832.PDF -- PDF832.PDF -- 000812220195.docm
- 2017-06-22 11:19:34 UTC -- HOWARD OF HAINAULT <Howard1979@click2limos[.]com> -- Emailing - PDF603.PDF -- PDF603.PDF -- 000812220195.docm
- 2017-06-22 11:20:04 UTC -- LUISA RIDDOCK <Luisa7638@kofix[.]nl> -- Emailing - PDF394.PDF -- PDF394.PDF -- 000904155375.docm
- 2017-06-22 11:47:39 UTC -- AUBREY WHITING <Aubrey5405@headofficebybjorn[.]com> -- Emailing - DOC134.PDF -- DOC134.PDF -- 000639752201.docm
- 2017-06-22 11:50:11 UTC -- SIMONE CAMERON <Simone5537@rotechelectrical[.]com> -- Emailing - DOC935.PDF -- DOC935.PDF -- 00091882312.docm
- 2017-06-22 14:07:48 UTC -- ELOY WINDRIDGE <Eloy3302@mo-gerzat[.]fr> -- Emailing - DOC998.PDF -- DOC998.PDF -- 000862862990.docm
- 2017-06-22 14:14:15 UTC -- KERRI SHEPPARD <Kerri8171@hart-comm[.]com> -- Emailing - PDF974.PDF -- PDF974.PDF -- 000261712564.docm
- 2017-06-22 14:14:51 UTC -- ALFRED AKISTER <Alfred2203@robertlarin[.]com> -- Emailing - PDF836.PDF -- PDF836.PDF -- 00091882312.docm
- 2017-06-22 14:16:05 UTC -- RACHAEL BENT <Rachael0755@2hphotography[.]ca> -- Emailing - DOC827.PDF -- DOC827.PDF -- 000205740858.docm
MALWARE
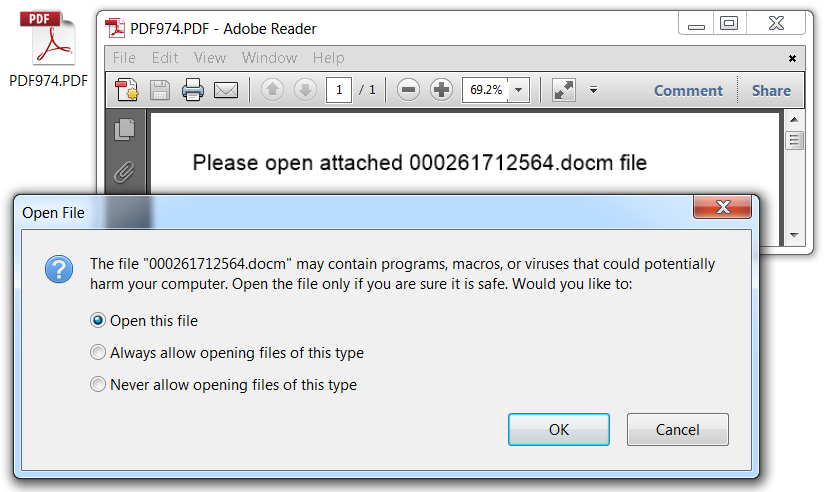
Shown above: An example of the PDF files attached to the malspam.
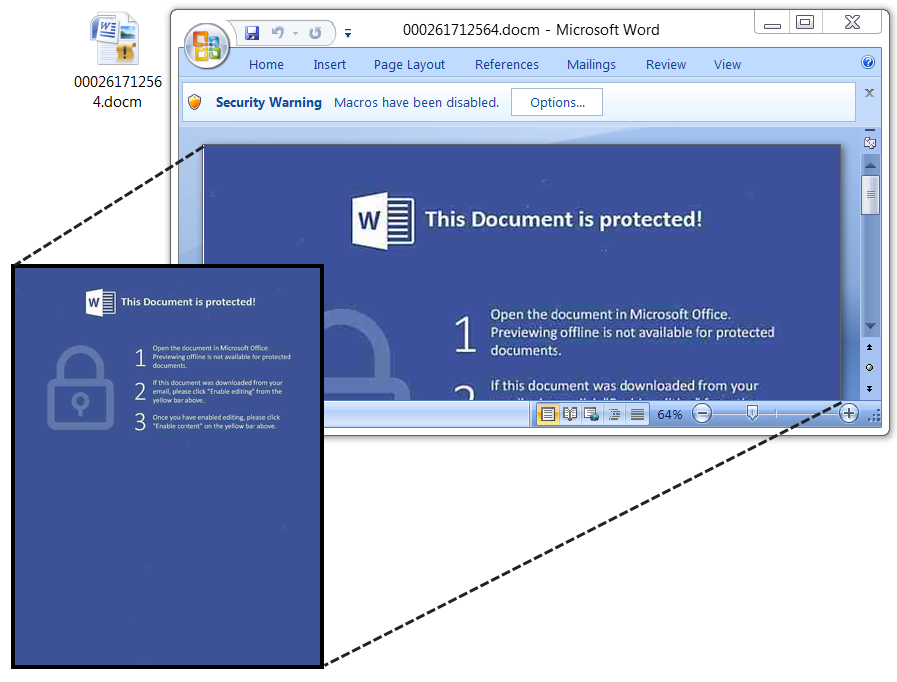
Shown above: An example of the embedded Word documents seen when opening the PDF files.
SHA256 HASHES FOR THE PDF ATTACHMENTS:
- 27de13b9f57d2ec30bb0b90cd7d470818f026b0049af81f96210ad6d731b0f95 - PDF603.PDF and PDF832.PDF
- 402d345db262cbf8e25382487feb52be1631d0e5c2e815e201964fb2c3905882 - PDF836.PDF and PDF974.PDF
- 48e52822ddba1ec2b3f634c159f0dc1ccfd193b22d2d8c8794ab699bdb299a87 - DOC134.PDF
- 50098a3edc1b67e6debe23a143e2d24ac67536b4ee3a1506798c0177b123d579 - DOC441.PDF, DOC702.PDF, and PDF537.PDF
- 6d36f5c7cb4b43318c100c9f070da0e35670984224bc6cc2c5dfe471dc86bfd7 - DOC999.PDF
- 73b0097b6f4bb031e9a8bdd75ae4559310c9e335d15ea4418c690d8cca5687f3 - DOC998.PDF
- 7e6f3aad2d1d70dc7a9cabc6e42e91a578ecc7d7ee8b2e8895d88171b31eb2dc - DOC827.PDF
- 9f0c6e6d630b6e12b7b34f858e6746ff6f686f3a4f67fd77510143ed1f778d6d - DOC935.PDF
- a4c4f44741d3f74e9072b23abb7c08c8661c4e30a67859eb94ba16c74fc44006 - DOC199.PDF and PDF806.PDF
- a912588520a6aeece0382126b4c93f42cd31b0ca93f6a1bc5495d4ad2effe7c0 - PDF666.PDF
- b36b17be1eea01c00322cd5ccb6a3106f9558c48eb8a0961d36e545a52c5360e - PDF394.PDF
- ce038868832f30bf52cfae8094fee50a381401d30654286c55b6434c4d1950d5 - DOC204.PDF
- f880cd4bfadc2092484abbc6da106d5a91daeab12f7ce983ea3114a1a0686af2 - DOC514.PDF, DOC787.PDF, and PDF064.PDF
SHA256 HASHES FOR THE EXTRACTED .DOCM FILES:
- 1bbe76d89604c0a235538fca4b420f49be876e489a4c6fae95c14ce1f925a994 - 000812220195.docm
- 4536363e33f1312b217596cd126e9143d6c265e89f85add19ffa8cba8db0af90 - 000639752201.docm
- 55bdadc62ae8cac9b1b106b86798d98cfa24cbeac5ab5240a06bfbb4d3a7af4a - 000248089012.docm
- 64ff88edc478747b24b9fba8b99d06652914294117fc3e9e7aa5744a62ed8074 - 000455383454.docm
- 735d5262c3af811499ba5f85d77294cbab90daf723c0fde035a6e9c522fcc257 - 000261712564.docm
- a120b68d1195dffe21a9a68b6a4f2ea8840d584b1bc5f0c8cd50a5b6d8d8ccd0 - 00091882312.docm
- ada1f5f6f46a225a6ca1f42bfdae8441536a810b929f925f20939bbe5b95b44b - 000205740858.docm
- c048209e3fe1c6119c3dc729800f9d0850d186c7c00cc403d104761571821aa8 - 000862862990.docm
- c3d6cac91b2b4b5ddd5d2ca035215e0ee33228f01083cde80545a58d7e47bfe1 - 000518024662.docm
- d9154bda586ad98049374105f20be6bbedd278e6fc3296836a40ee44866f804e - 000904155375.docm
- dcbf50e60f17f3c72ad84fb5f434bcea9ba6b2630075737fbefdde52a8af7797 - 000890651955.docm
- de5441ddffb488777e73e59c9c1ac30827def0eef5b6334d1d0eb66532cdae3c - 000731715784.docm
- e19a94667e12dd445f68fcd4d21e8b1abc8431052f8bfb22449ab3589a2b10cb - 000270630709.docm
MALWARE RETRIEVED FROM INFECTED HOST:
- SHA256 hash: 858632df961a6d355abfe7eb090c96156d2206e9171ef07ef1857f016bf737c4
File size: 311,808 bytes
File location: C:\Users\[username]\AppData\Local\Temp\proshuto8.exe
File description: Windows executable for Locky ransomware
TRAFFIC
URLS FROM THE WORD MACROS FILES TO DOWNLOAD LOCKY:
- 1time[.]nl - GET /7gyjgg5r6
- asathlon[.]it - GET /7gyjgg5r6
- asman.railsplayground[.]net - GET /7gyjgg5r6
- autobluelite[.]com - GET /7gyjgg5r6
- blitzacademy[.]in - GET /7gyjgg5r6
- brontorittoozzo[.]com - GET /af/7gyjgg5r6
- chocolatesbazaar[.]com - GET /7gyjgg5r6
- ddplgroup[.]com - GET /7gyjgg5r6
- i-school-tutor[.]com - GET /7gyjgg5r6
- itbouquet[.]com - GET /7gyjgg5r6
- malamalamak9[.]net - GET /7gyjgg5r6
- melakatropical[.]com - GET /7gyjgg5r6
- micolon[.]com - GET /7gyjgg5r6
- obluelite[.]com - GET /7gyjgg5r6
- partyangel.in - GET /7gyjgg5r6
- randomessstioprottoy[.]net - GET /af/7gyjgg5r6
- skyfling[.]com - GET /7gyjgg5r6
- techno-me[.]com - GET /7gyjgg5r6
- tyastudio[.]com - GET /7gyjgg5r6
- unitedtanga[.]com - GET /7gyjgg5r6
- www.losangelesrelocationservices[.]net - GET /7gyjgg5r6
LOCKY POST-INFECTION TRAFFIC:
- 185.115.140[.]170 port 80 - 185.115[.]140.170 - GET /checkupdate
- g46mbrrzpfszonuk[.]onion - Tor domain for Locky decryptor
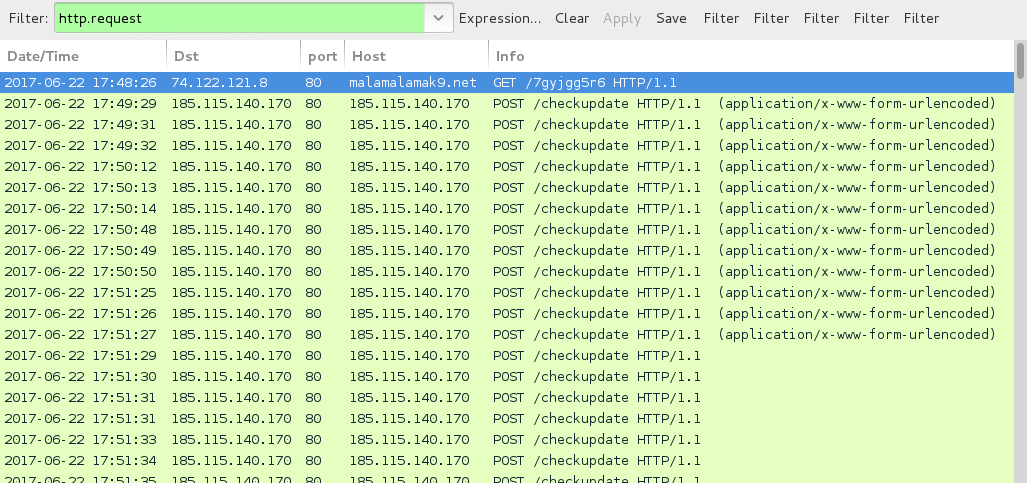
Shown above: Traffic from the infection filtered in Wireshark.
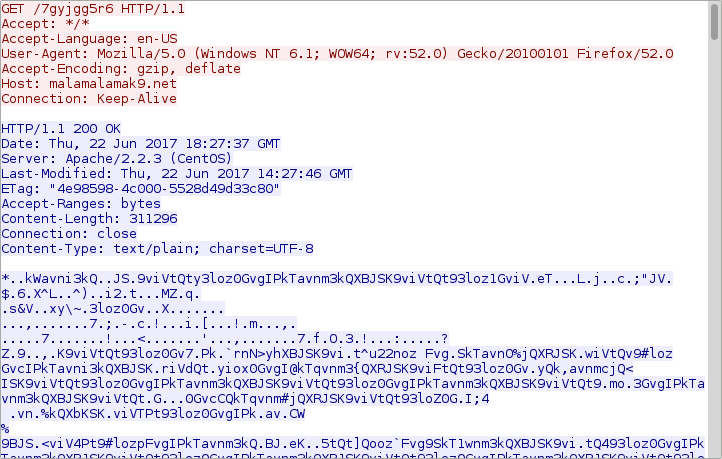
Shown above: HTTP GET request for the Locky ransomware binary.
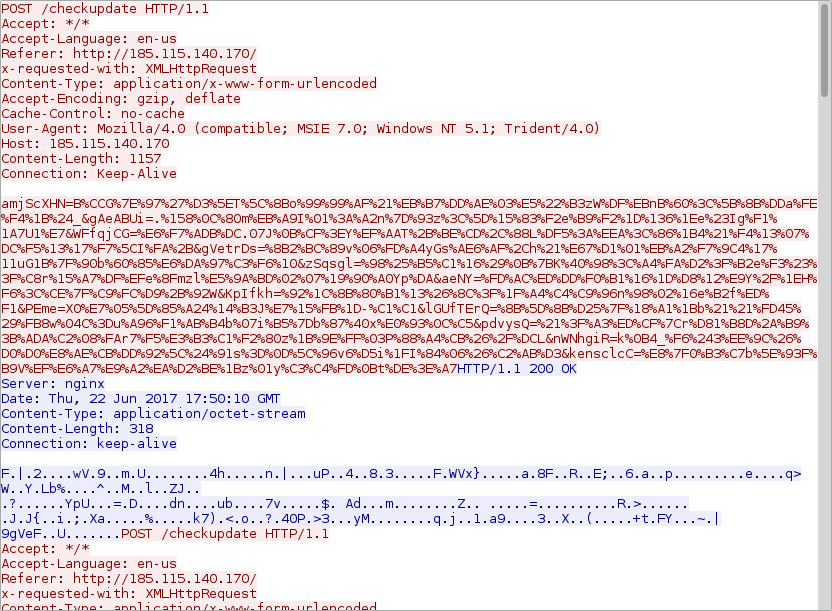
Shown above: Post-infection callback from the infected host.
IMAGES
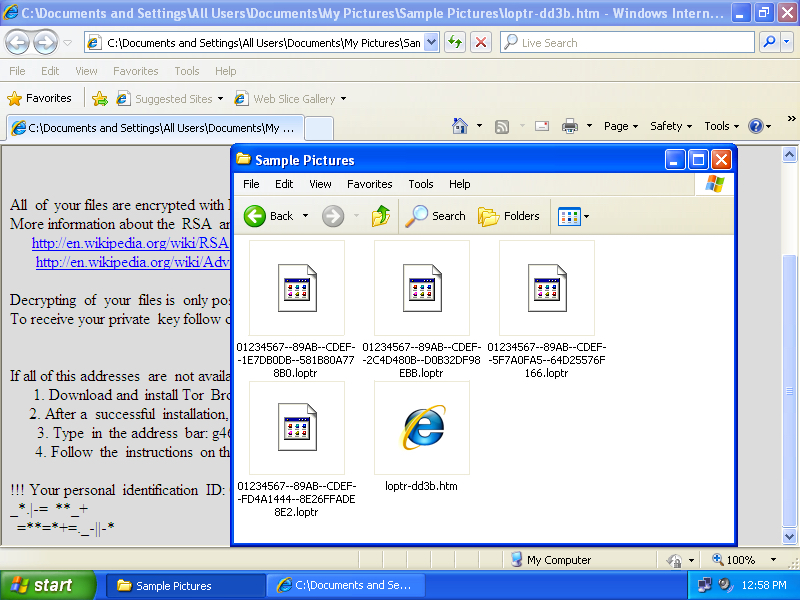
Shown above: Encrypted files have .loptr as the file extension.
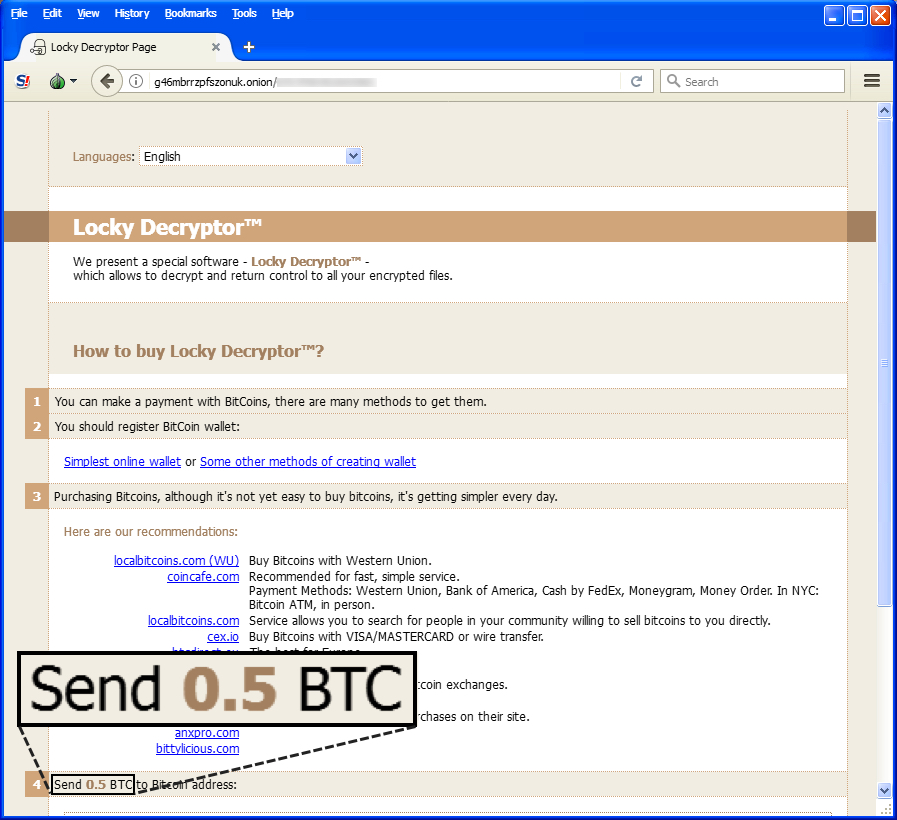
Shown above: Screen shot of the Locky decryptor asking 0.5 bitcoin for the ransom payment.
Click here to return to the main page.
